Managing Physical Security Devices: Feeling Stuck in the Stone Age?
As organizations have become heavily dependent on IP cameras, access control panels, and other connected devices for their physical security, it has become increasingly important to operationally manage those devices properly.
But while the operational management of physical security devices is more crucial now than ever before, the massive and growing fleets and the complexity of the physical security ecosystem makes managing them a serious challenge. As a result, achieving a mature approach to managing physical security devices is a major process that takes time. Developing that maturity as an organization involves taking significant and careful steps to keep moving along the continuum towards enterprise-ready physical security.
To shed light on how to make that journey effectively, we at SecuriThings have created a five-step maturity model for physical security. By completing a quick self-assessment, you can find out how far your organization has come in its approach to operationally managing its physical security devices. Even more importantly, you can get valuable guidance to help you keep improving.
This post will provide a quick overview of the maturity model. For a deeper understanding, we invite you to check out our new eBook, Optimizing Physical Security Device Management: A Comprehensive Maturity Model.
The goal: enterprise-ready physical security
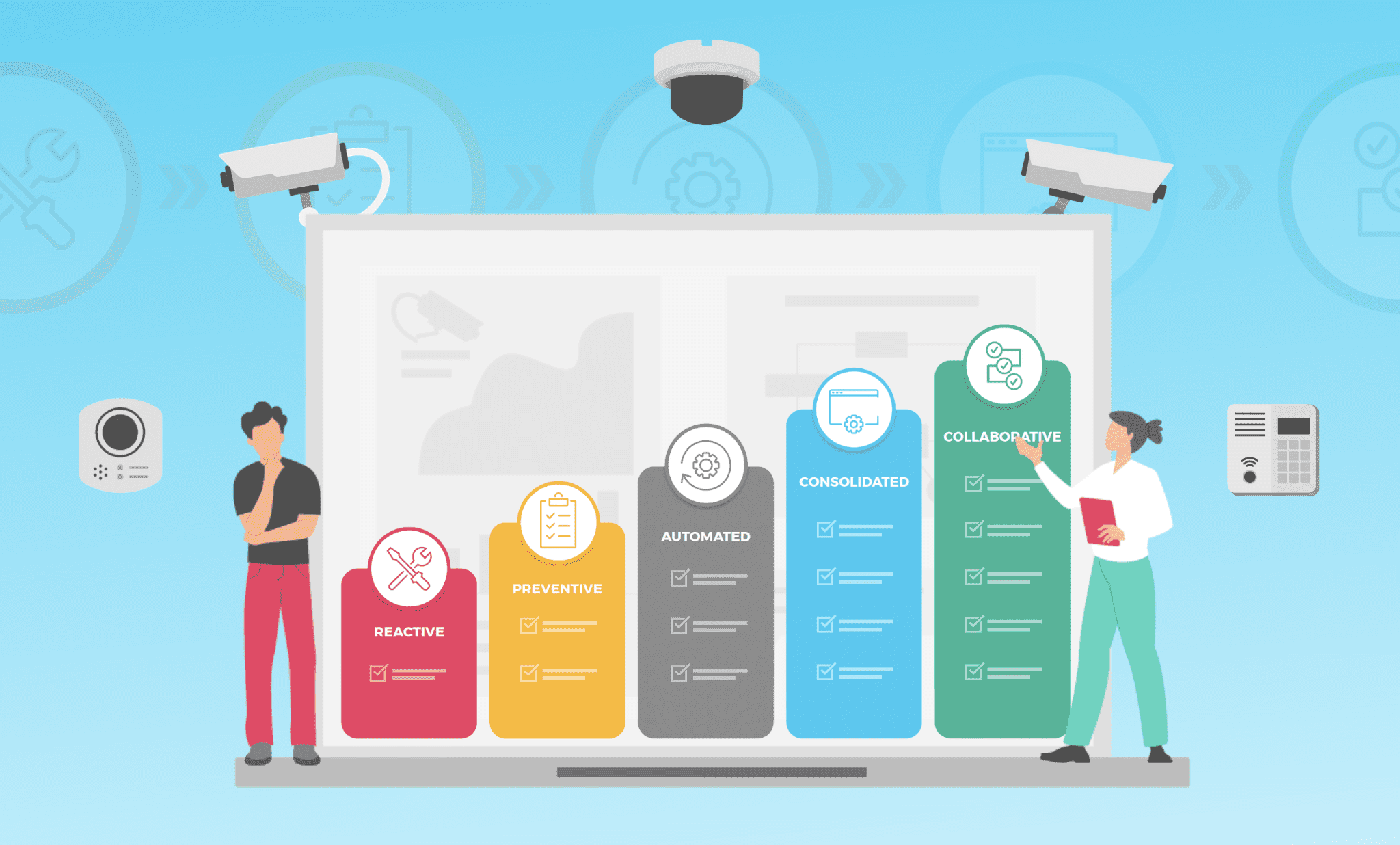
Our physical security maturity model offers a breakdown of the path from a purely reactive stance, to having a fully mature, enterprise-ready approach to managing physical security devices. The further along in the journey you are, the better you are positioned to optimize your overall security posture.
Each stage represents a critical element in building enterprise-ready physical security – enabling you to reduce downtime, harden your devices against cyber threats, ensure compliance, and simply make device management more scalable.
The five stages of the maturity model are:
-
- Reactive, in which organizations have little-to-no visibility over their devices, and are therefore limited to simply reacting to problems or crises as they occur.
- Preventive, in which organizations make some effort to monitor and maintain their physical security devices, but are performing these processes manually – which is ultimately unscalable.
- Automated, in which organizations use automated tools to streamline their maintenance processes to some extent, while also gaining significant – but still siloed – visibility into the real-time status of their physical security devices.
- Consolidated, in which organizations have full device visibility, coupled with a comprehensive layer of automated management capabilities.
- Collaborative, in which physical security teams are empowered to share information with other stakeholders in a seamless and intelligent way – for example via automated alerts and reports.
How assessing your progress can help you move forward
Now that you have a basic understanding of the major stages leading up to enterprise-ready physical security, your next step is to evaluate where within the maturity model your physical security infrastructure currently stands.
Once you have a clear sense of where you stand, you’ll be able to map out the steps for your organization to take in order to reach a fully mature approach to operationally managing its physical security devices. In other words, the general idea is to use the maturity model as a roadmap.
By considering the maturity model and assessing your progress so far, you can help prepare your organization to develop a reliable, efficient, and cost-effective approach to operationally managing its physical security devices. Then, you can use your new insights to help optimize your organization’s overall security posture.
Click here to take the self-assessment and receive a personalized progress report, including guidance on how to move forward towards enterprise-ready physical security.


