CCTV Hacking: Tutorial & Prevention Best Practices
CCTV cameras are almost omnipresent nowadays. You will find CCTV cameras everywhere, from highly secure establishments to small stores.
Several factors have contributed to their widespread adoption:
- Increasing affordability
- Improving resolution
- Minimal infrastructure requirements (thanks to IoT)
- Ease of installation
- Increasing awareness about their importance
- Data breaches due to physical security compromise
- Regulation specific to industry verticals
However, the widespread adoption of CCTV cameras has attracted a proportional interest from hackers. They have several means to hack into your CCTV camera and snoop the video feed. The extent of damage this can cause varies, depending on what the camera (and the hacker) sees. In this article, we will explore CCTV hacking from the cybercriminal perspective and discuss various ways to hack a CCTV camera.
Summary of key CCTV hacking concepts
The table below summarizes four key CCTV hacking concepts this article will explore in detail.
| Concept | Description |
|---|---|
| CCTV camera information flow | In between the camera and the viewer, the CCTV camera data flows through several independent components. Each component and its connections are potential entry points for an attacker. |
| CCTV vulnerabilities | Vulnerabilities across the firmware, network, application, and storage can be exploited by hackers to gain partial or complete access to the camera. |
| How to hack a CCTV Camera | Common CCTV attack methods include brute force dictionary search, backdoor attacks, Man-In-The-Middle attacks, and phishing attacks. Most of these attacks have several variations. |
| Best practices | The attack probability can be minimized if the best practices are followed. Here, we describe useful practices related to firmware updates, network infrastructure, servers, Wi-Fi, and applications are discussed. |
CCTV Camera Information Flow
Consider the diagram below. It shows the various steps involved from the capturing of the video stream by the camera to playback and storage. Almost every node in the diagram can act as an entry point for the hacker.
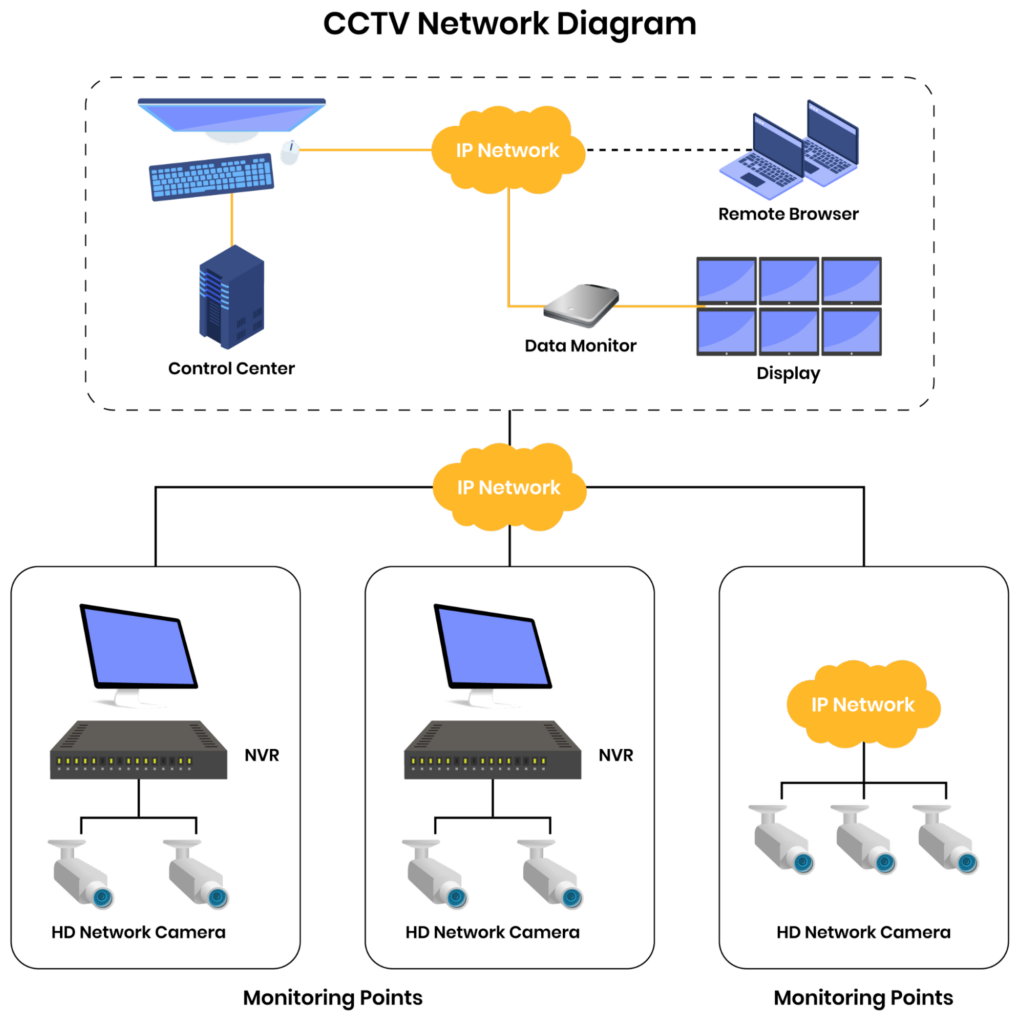
Generic CCTV System: Components and Connections. (Source)
The network keeps getting more complex as more camera units are added. Beyond a point, outsourcing the management of the camera fleet to an enterprise security solution like SecuriThings is advisable over managing the fleet in house.
While several blocks are visible in the above block diagram, they can be broadly categorized as follows:
- Camera: The physical camera units (hardware and firmware).
- Application: The desktop/mobile/web application that can be used to configure the camera and/or view its live feed
- Network: The physical cables or wireless connections between any two components in the above system
- Storage: The memory elements (HDD, SSD, NVMe, etc.) that can be present locally or on the cloud to store the cameras’ historical feed.
-

Monitor the health of security cameras and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
CCTV Vulnerabilities
The information flow diagram in the above section hints at the vulnerabilities in CCTV cameras. Hackers often try to exploit the following targets:
- Camera vulnerabilities:
- Authentication weaknesses: Improper/ weak credentials and improper access management can often provide complete access to the camera
- Firmware vulnerabilities: Hackers can exploit vulnerabilities like buffer overflow, directory traversal, and memory corruption to gain partial or complete access to the camera.
- Network vulnerabilities:
- Unencrypted communication: This enables hackers to tap the video feed in transit (every connection in the above diagram acts as an entry point for hackers; which one they tap depends on how accessible the system is to them)
- Protocol vulnerabilities: Communication between any two nodes in the system involves one or more protocols (like ARP, DNS, HTTP, etc.). Existing vulnerabilities in any of these can be exploited by hackers to get access to the information being exchanged.
- Outdated security: Typically, security protocol versions are updated as vulnerabilities identified in the existing versions are fixed. For example, TLS 1.3 is more secure than TLS 1.2, and so on. Hackers can exploit existing vulnerabilities in outdated security protocol versions to decrypt the tapped feed.
- Application vulnerabilities:
- Cross-Site Scripting (XSS): Hackers can exploit this to execute malicious scripts on the application
- Cross-Site Request Forgery (CSRF): Hackers can send unintended requests to the application on behalf of the user.
- Unlimited password attempts: Hackers can then try to guess the password brute-force, as the application doesn’t restrict them.
- Storage vulnerabilities: Hackers can try to attack the physical or cloud storage hosting the backups of the CCTV camera feed. The vulnerabilities here can be one or more of the above, but on the storage device/application rather than the camera.
This article on camera vulnerabilities explains these vulnerabilities in depth and discusses several vulnerabilities that appeared in different camera products.
How CCTV hacking happens
Having understood the vulnerabilities in the previous section, let us now look at the various tools a hacker can employ to gain access to your CCTV camera.
Brute force dictionary search
This is one of the easiest methods of gaining access to a CCTV camera. Dictionary search is a type of brute force attack where the hacker tries to guess the password by going through a list of commonly used words or phrases. More details about the execution of this attack are provided in this article.
The following needs to be true for this attack to work:
- Your password is easy to guess (in case you leave it at the default or have a very weak password, like ‘password’ or ‘abcd1234’) or
- Your camera application/firmware doesn’t adequately limit wrong password attempts.
Note that if there is no limit to the number of wrong password attempts, a hacker with enough time could theoretically try out all combinations of characters to get the password to your camera.
Backdoor attack
A backdoor attack allows a hacker to bypass the camera’s standard authentication mechanism and gain access via a “backdoor.” Several methods exist for executing such an attack, most involving exploiting an existing vulnerability on the camera or the network.
Developers often leave intentional commands or features in the system that bypass normal authentication measures for testing or debugging. Known as maintenance hooks, these are very attractive for hackers once they are discovered. They can gain unauthorized access, install malicious code, or create another backdoor.
If a maintenance hook is unavailable, hackers can exploit other vulnerabilities to find backdoors. For example, certain firmware vulnerabilities that lead to memory overflow or out-of-bounds memory exceptions can allow hackers to execute remote code on the cameras. An example is CVE-2018-19036, which affected several Bosch IP cameras having firmware version 6.32 or higher.
Man-in-the-middle (MITM) attack
This eavesdropping attack involves the hackers inserting themselves in the communication path between two entities and snooping the communication. The attacker can be a passive snooper or an active intermediary. In the latter case, both entities think that the attacker is the intended recipient of their messages, and both are unaware if the contents of their communication are modified before reaching the actual recipient.
MITM attacks come in various forms, such as:
- Wi-Fi eavesdropping: If the device is on the same Wi-Fi network as you and its communication is unencrypted, you can sniff for all packets exchanged on the Wi-Fi network and get the video feed into your machine. Connecting your cameras to public Wi-Fi networks aggravates the risk.
- ARP Poisoning: Address Resolution Protocol (ARP) is used to discover MAC addresses associated with IP addresses on a network. An attacker employing ARP poisoning would typically get the MAC and IP address of the camera and pretend to be the camera for all other nodes on the network. Since the IP specification doesn’t restrict two devices with the same IP address to exist in a network, this method conveniently works. Once the hacker’s system pretends to be the camera, the hacker’s system will receive any communication from the user to the camera (including credentials). An MITM attack into Dahua/Intelbras cameras demonstrates this. Because the local communication over the network from the user application to the camera was unencrypted, the hackers could get the login credentials for the camera.
- DNS Spoofing: Like ARP maps IP addresses to MAC addresses, DNS (Domain Name System) maps domain names to IP addresses. A DNS spoofing attack messes with this mapping and redirects the host to a malicious/fraudulent domain. This domain operates a fake website that the user mistakes for the original website. The user can unknowingly share sensitive information (like usernames and passwords) with the malicious actor.
Once the attacker is able to intercept the communication between the CCTV camera and the application, the next hurdle is often decrypting the communication if it is encrypted. Several techniques are usually employed, including SSL hijacking, SSL stripping, and SSL BEAST. You can find more details by clicking the respective links.
Phishing
This social engineering technique involves luring the user to reveal sensitive information by clicking a malicious link or replying to a seemingly legitimate text. The end goal is to either obtain credentials from the user or install malware or ransomware on the user’s system. Phishing attacks have become increasingly sophisticated and are the most common type of cybercrime with the FBI’s Internet Crime Complaint Center as of 2020. There are various forms of phishing attacks, like email phishing, SMS phishing, voice phishing, and page hijacking.
Page hijacking is especially important in the context of CCTV cameras. It involves redirecting users to malicious pages, often exploiting a Cross-Site Scripting (XSS) vulnerability on the camera’s application page.
Most phishing attacks, especially in the context of CCTV cameras, employ link manipulation.
This can be achieved in the following ways:
- Misspelling URLs. For example, goodsitr.example.com instead of goodsite.example.com.
- Reordering domains and subdomains. For example, auth.camerasite.com and camerasite.auth.com point to two very different domains. In the first case, camerasite.com is the domain, and auth is the subdomain. In the second case, “auth.com” is the domain and “camerasite” is the subdomain. An untrained eye can easily mistake one for the other.
- Homograph attacks exploit homoglyphs. They take advantage of the fact that several alphabets (like Greek or Latin) have similar-looking characters that are different. Replacing o with 0 and smallcase L (l) with the number 1 are other examples of exploiting homoglyphs in link manipulation.
Five CCTV hacking prevention best practices
Here are a few best practices to shield your CCTV camera from the hacks discussed above:
Automate regular firmware updates
Several hacking attempts (including dictionary search and backdoor attacks) exploit firmware vulnerabilities. Typically, the manufacturer releases a fix as soon as a vulnerability is reported, and keeping the firmware up-to-date ensures that your camera is protected against all known and fixed vulnerabilities. Enterprise camera management solutions (like SecuriThings) are recommended to automate the firmware update process for your fleet of CCTV cameras.
Implement network infrastructure-related best practices
Following best practices can be followed to secure CCTVs:
- Maintain static ARP tables: This adds a substantial administrative burden but can be a strong defense against ARP poisoning. Any change in the network will require manual updates to ARP tables across devices. While infeasible for large organizations, this can be followed when security is highly critical.
- Use Dynamic ARP Inspection (DAI): Most new Ethernet switches come with built-in DAI features that evaluate the validity of each ARP message and drop suspicious/malicious packets. Check if your switches have this feature.
- Implement strong network isolation: Physically controlling access to the network can greatly reduce the attack surface. This can mean having a dedicated network for your CCTV cameras or segmenting the network so that all the camera data flows through a single, more secure subnet.
Follow server-side best practices
Below are three best practices for CCTV camera servers that teams should consider when evaluating a system:
- Implement encryption: The server must ensure that all data transmissions are encrypted on secure channels using strong encryption protocols. For example, HTTPS should use a minimum of TLS 1.2 or higher and not support legacy SSL versions. This simple measure reduces the viability of several potential attacks.
- Secure DNS with DNSSEC: Domain Name System Security Extensions (DNSSEC) is a suite of specifications developed by the Internet Engineering Task Force to secure data exchanged in the Domain Name System in IP networks. You can use the whois command (or the web utility) to check if a particular domain has DNSSEC enabled, and you can encourage your camera provider to enable DNSSEC for all domains that the camera or its user interacts with. This can protect against DNS spoofing attacks.
- Protect against compromised certificates with HPKP: HTTP Public Key Pinning (also called “certificate pinning”) is another security measure that protects against compromised certificate authorities. The server provides a list of “pinned” public key hashes during the first transaction, and subsequent transactions require one or more keys in the list to be used to consider the transaction authenticated.
Perform network monitoring
Network traffic monitoring can give hints about an attack happening. Latency examination can provide indications of a potential MITM attack. The network latency during an MITM attack can increase by tens of seconds as a third party sniffs data and potentially performs complex calculations involving hash functions. Forensic analysis of the network traffic can also provide hints of a past attack by analyzing the IP address, DNS name, and the X.509 certificate of the server. Again, an enterprise camera management solution can do this on the fly for your fleet of cameras.
Use Wi-Fi and application-related best practices
Recommended best practices for Wi-Fi connections and applications are as follows:
- Don’t connect the camera to any password-less Wi-Fi network
- Avoid accessing the camera’s configuration page or the camera feed from a public Wi-Fi network
- Set up multi-factor authentication (MFA) for the application
- Set up a firm password policy (with password auto-rotation)
- Don’t open any other tabs when viewing the camera feed or configuring the camera
- Notice the URL of every camera-related web page you open. Don’t proceed if the browser marks any page as unsecured or the URL seems incorrect.
Conclusion
The widespread and rapid adoption of CCTV cameras will almost inevitably ignite hackers’ interest. The presence of multiple independent components in the CCTV information flow from the camera to the viewer generates a wide attack area for hackers. Hackers often exploit firmware, networks, applications, and storage vulnerabilities. Additionally, attacks such as brute force, backdoor, MITM, and phishing are becoming increasingly common.
However, the amount of protection obtained by following basic security measures, timely updates, and regular monitoring is phenomenal. As your fleet of cameras grows larger and their usage becomes more critical, it is prudent to outsource camera management to an enterprise solution like SecuriThings.


