Camera Vulnerability: Tutorial, Sample CVEs, and Best Practices
IP cameras are essential to physical security. Paradoxically, they’re also a common source of cybersecurity weakness. Unfortunately, IP cameras’ ubiquity and fast growth have come with the cost of overlooked camera vulnerabilities that attackers often discover before patches are released or applied.
This article will explore camera vulnerabilities in detail, including common vulnerabilities and exposures (CVE), how they have appeared in different camera products, and how they are exploited by attackers. We’ll also examine camera vulnerability mitigations and best practices for reducing your exposure to IP camera-related threats.
Summary of Key Camera Vulnerability Concepts
The table below summarizes the key camera vulnerability concepts this article will cover in more detail.
| Concept | Description |
|---|---|
| Evolution of surveillance cameras | Surveillance cameras have evolved from analog to digital to connected systems. Convenience has increased for both users and hackers. |
| Types of vulnerabilities | There are several types of camera vulnerabilities, the severity of which depends on the use case. Common examples include authentication, firmware, application, and data transmission weaknesses. Attackers have exploited IP cameras from well-known manufacturers using these types of vulnerabilities. This article delves into some Common Vulnerabilities and Exposures (CVE). |
| Best practices for managing camera vulnerability | Automated device discovery, firmware updates, password rotation, and access control policies are important mitigation techniques for IP camera-related risks. |
Key camera vulnerability terms
Below is a quick overview of the relevant terms you will encounter in this article or related articles during camera vulnerability evaluation.
- Telnet: A precursor to SSH, telnet is a protocol over TCP/IP (typically using port 23) that was widely used for administrative tasks and remote management. It is typically used to configure the IP camera, perform system checks, and update the system.
- CVE: Several vulnerabilities you find online are reported as CVE-YYYY-NNNN… CVE is an acronym for Common Vulnerabilities and Exposures. The CVE format consists of the CVE acronym, the year of vulnerability reporting, and a random ID assigned to the vulnerability.
- Shodan: Sentient Hyper-Optimized Data Access Network (Shodan) is a search engine for gathering information about devices and systems connected to the Internet. It is generally used for penetration testing and vulnerability analysis.
- Zero-day vulnerability: This refers to a vulnerability for which the developer or vendor has exactly 0 days to fix. In other words, attackers learned about the exploit before the developer; thus, no patch exists for this vulnerability.
- Password rotation: This refers to changing passwords at regular intervals, which reduces the period for which an attacker can exploit a leaked password and the time available for guessing a password in a brute-force manner.
- ONVIF: The Open Network Video Interface Forum (ONVIF) is a forum for developing and using a global and open standard for physical IP-based security products. As its scope has expanded beyond video applications, the longer name has been dropped.
-

Monitor the health of security cameras and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Evolution of surveillance cameras
Like many electronics, IP cameras have become increasingly “smart.” let’s use the TV evolution as an analogy. The early security cameras were analog systems, with their feed connected to a dedicated monitor or a Video Cassette Recording (VCR) System near the camera via a coaxial cable. They had low-resolution feeds, and since the video was stored on magnetic tapes, archival and retrieval required manual handling.
Next came the transition from analog to digital. The technology changed: the VCR became a Digital Video Recorder (DVR), image quality and resolution improved, storage and retrieval became easier (hard drive compared to magnetic tapes), and remote viewing of the camera feed was now possible through connected monitors.
Next came the Internet of Things (IoT) revolution and millions of devices connected to the network with an IP address. Wired gradually became wireless. Cameras started talking to each other. Storage moved to the network video recorder (NVR) or the cloud, and remote viewing became the norm. Advanced analytics became possible (including face recognition, motion detection, and object tracking). The camera firmware was now updatable remotely while in service. Convenience became abundant for both users and hackers. This surge in opportunities for hackers is the primary focus of this article.
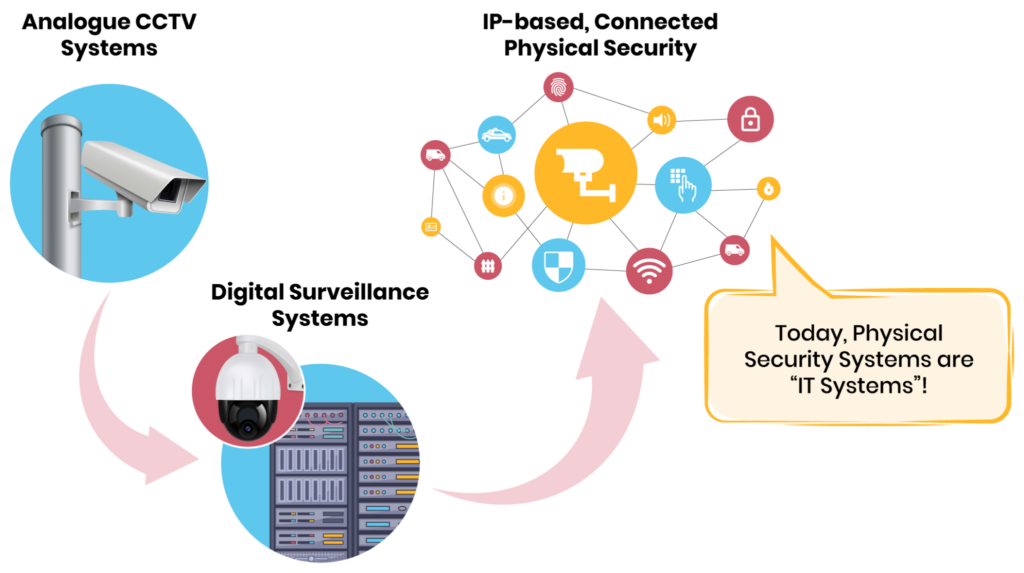
The evolution of cameras from analog to digital to networked. (Source: SecuriThings)
As the cameras became networked, the attack surface increased drastically. For the first time, the attacker did not need to be near the camera to hack it, eliminating a huge barrier for bad actors. Secondly, the number of entry points for attackers increased. Hackers could now target the camera’s authentication mechanism, data transmission, web interface, or even camera firmware. This required a focus on security and compliance.
When cameras became wireless, every manufacturer defined proprietary software protocols, resulting in multiple incompatible protocols in the IP camera market. Eventually, interoperability between hardware and software became a bottleneck, and the industry needed standardization. That’s how the ONVIF (Open Network Video Interface Forum) standard began in 2008. It covers device discovery and management, media configuration, IP configuration, real-time viewing, event handling, video analytics, storage, and security.
Types of camera vulnerabilities
While the comprehensive list of vulnerabilities will include hundreds or even thousands of entries, we will discuss the most common ones here. The severity of the vulnerability greatly depends on the application for which the camera is used. For example, a pet cam’s feed being visible to a malicious user may not be an issue. In contrast, even a few seconds of downtime can be detrimental to a security vault camera.
Improper/weak authentication
Improper/weak authentication is the most common camera vulnerability. If an IP camera does not adequately authenticate users, certain users may be able to escalate their privileges on the system and get access to sensitive information.
Here are three examples of vulnerabilities that have affected IP cameras.
- CVE-2017-7921: Found on several Hikvision devices. This article explains how to hack cameras and provides a detailed description of the exploit. The summary is that any valid token (not necessarily belonging to the camera being exploited) gave access to the camera’s configuration files, users, and even the live snapshot. Essentially, the camera’s firmware just checked for the presence of the access token and not its authenticity.
- CVE-2017-2871: Affecting a certain firmware version (2.52.2.43) of Foscam C1 indoor HD cameras. In this case, the firmware recovery procedure had improper authentication, allowing an attacker in the same subnetwork to get full access to the device by performing a firmware recovery operation using a custom image.
- CVE-2020-6852: Impacting CACAGOO cameras with a specific firmware version (3.4.2.0919). It had weak authentication of TELNET access, thereby providing root privileges without requiring a password.
Remote code execution
This vulnerability allows hackers to execute arbitrary code on your camera. For example, the CVE–2018–10660 vulnerability allowed attackers to execute shell commands on Axis IP cameras with root privileges. When combined with CVE-2018-10661 (access control bypass) and CVE-2018-10662 (exposed insecure interface), an unauthenticated, remote attacker could gain full control over the camera.
Buffer overflow
Attackers can exploit this vulnerability to crash the camera, leading to service downtimes and potentially valuable camera feed loss.
Some examples of this camera vulnerability are listed below:
- CVE-2017-3223: Affected Dahua IP camera products before a certain firmware version. These cameras provided a web interface that did not have input data length validation on the ‘password’ field. Thus, a remote attacker could send a POST request, leading to out-of-bounds memory operation and downtime.
- CVE-2022-2471: Certain EZVIZ models had a buffer overflow vulnerability in the motion detection component, which allowed attackers to execute remote code on the device.
Exposed credentials
Credentials can be exposed to unintended users in several ways. In the IP-camera world, several Hikvision cameras were affected by the ‘password in configuration file’ vulnerability, CVE-2017-7923, which allowed a malicious user to escalate privileges or assume the identity of another user.
Unencrypted communication
This is another common vulnerability that affects several IP cameras, best understood by the examples given below:
- CVE-2022-30563: Affected Dahua’s IP cameras. The attacker could launch a man-in-the-middle attack and sniff the unencrypted ONVIF interactions. Then, by replaying the user’s login packet, they could gain full access to the camera.
- CVE-2020-25748: This was found on certain Rubetek cameras. The video feed was transmitted unencrypted over a cleartext protocol, allowing potential interception and modification of the video.
- CVE-2018-7698: Affected specific D-Link cameras. The mydlink+ app sends the unencrypted username and password for certain connected D-Link cameras from the app to the camera, allowing full control of the camera to intercept attackers.
Cross-site scripting (XSS)
XSS is a vulnerability related to the web interface provided to the user. Attackers exploiting XSS vulnerabilities need to send the user a link to the web application infused with malicious scripts. If a user clicks on this link, the requested web application will open, but the malicious script will also be executed if the application is not properly secured. D-Link IP Camera DCS-2103 and cameras by Eyeplusiot.com are examples of vulnerable cameras.
Cross-site request forgery (CSRF)
While XSS exploits the user’s trust in the application, CSRF exploits the application’s trust in an authenticated user. This vulnerability forces an authenticated user to submit an unintended request to a web application they are authenticated against.
The attacker sends the request to the application on your behalf. This vulnerability affected Bosch IP Cameras with CVE-2021-23849. If the victim was successfully tricked into clicking on a malicious link while logged into the camera, the attacker could successfully trigger actions on the camera on behalf of the user.
Directory traversal
This vulnerability allows an attacker to traverse directories of the camera’s file system, potentially accessing sensitive files. An example is CVE-2010-4231, which affected Camtron and TecVoz IP cameras. In this vulnerability, attackers could exploit a “..” traversal sequence in the URI. For example, exploiting a directory traversal vulnerability to obtain the root password for a Genie Access WIP3BVAF IP camera.
Improper access restrictions
Directories like /tmpfs or /log can be accessible without authentication, potentially revealing sensitive information in plain text format. CVE-2013-2574 is an example that affected certain FOSCAM IP cameras. The reporters of the above vulnerability accessed sensitive information, including access credentials (usernames and plaintext passwords, stored in the config_backup.bin file in the ‘tmpfs’ folder) and Wi-Fi credentials.
Memory corruption
If operations within the bounds of a memory buffer are not properly restricted, it can lead to memory corruption with unpredictable consequences, including downtime. An example is the CVE-2018-10664 vulnerability in multiple models of Axis IP cameras, wherein there was an issue in the HTTPS process. Another example is CVE-2018-19036, which affected several Bosch IP cameras. The out-of-bounds memory operation allowed an unauthorized attacker to execute code on the device.
Best practices for managing camera vulnerabilities
This section will discuss a few practices for managing the vulnerabilities mentioned above.
Automate discovery and monitoring
The first step toward managing your IP cameras is understanding the management scope. It is crucial to identify how many devices are present on your enterprise network, what specifications these devices have, and what firmware version they are running. Whether these devices are internet-facing or only communicating on the intranet can also be checked. Use tools like Shodan to identify if an intranet device inadvertently leaks data to the Internet.
Replace old devices that can’t be remotely managed.
Devices that are end-of-life (EoL) may still be supported by the vendor but have been designated as unfit for long-term use. As such, they should be treated as high-risk and prioritized for replacement. Furthermore, as EoL devices enter the End of Service-Life (EoSL) stage, they will no longer receive patches or updates, which makes them easy targets for attackers due to the certainty of successful exploitation of identified vulnerabilities. Over time, managing these devices becomes a manual effort, and they can be easily overlooked in an enterprise system containing hundreds or thousands of devices. A vulnerability in any of these devices can remain persistent and have long-term consequences on the overall health of your security system.
SecuriThings offers a software solution that simplifies the management of physical security devices. It offers centralized control, automation, and real-time monitoring. Upon deployment, the platform delivers complete visibility into the end-of-life (EOL) timeline for your entire device fleet. Additionally, it recommends suitable replacement models to ensure a smooth transition during device upgrades.
Perform regular firmware updates and automate them where possible
You can fix most of the vulnerabilities discussed in the above section via firmware updates, and manufacturers regularly release patch updates to fix the reported issues. Automating the firmware update process ensures that the vulnerabilities are fixed as soon as a fix is available.
You can set up an automated firmware upgrade routine by setting up a custom service to check with the camera manufacturer for an update (e.g., using an API) and then deploying it in a phased manner across your fleet. Alternatively, you can use enterprise solutions like those provided by SecuriThings to manage the firmware updates.
Implement strong password security practices
First, you should change the default password once the camera is set up. Next, you should enforce a strong password policy to protect against a brute-force dictionary search attack. Next, rotate passwords regularly (preferably in an automated manner). Rotation ensures that the extent of damage caused by a compromised password is limited. Finally, complement password rotation with other features, like multi-factor authentication (MFA). To limit the scope of impact in the event of password compromise or leakage, you should avoid using the same password, despite the complexity, across your IoT estate.
Encrypt data in transit
Ensure that all communication with the camera is encrypted, locally or via the cloud. Disable services like Telnet and FTP that send data in cleartext if they are not required so that your attack surface is reduced.
Enforce strict access controls
Strict access control policies based on the principle of least privilege further help reduce the attack surface. Every unnecessary access is a potential vulnerability source. Human carelessness can be an important enabler for attackers to exploit vulnerabilities, and minimizing access to the bare minimum required provides protection against it.
Follow XSS and CSRF-related best practices
As discussed in the above section, these vulnerabilities are related to the web interface provided by the camera. The best practices when using the web interface are listed below:
- When a camera session is active, don’t use any other website
- Don’t click any link from an untrusted source that takes you back to the camera
- If possible, use a different browser than default when interacting with any camera
- Close the browser after every camera session
Keys, Secret & Certificate management
Secrets, keys, and certificates are key to IoT device security, as they secure authentication, communication between devices, and management solutions. Unmanaged certificates, self-signed certificates, low-complexity keys, high TTL tokens, and insecure storage are common issues attackers use to compromise devices. As organizations deploy a greater number of IoT devices, manual management becomes impractical. Automated management provides clear cost savings and greater value through continuous certificate visibility to enable rotation and provide avenues for efficient issue resolution and decision-making.
Conclusion
A holistic and automated device management setup is essential for protecting fleets of IP cameras deployed for critical applications. While there are many vulnerabilities, following the best practices in your device management setup gives you a strong defense against most of the major camera vulnerabilities.


