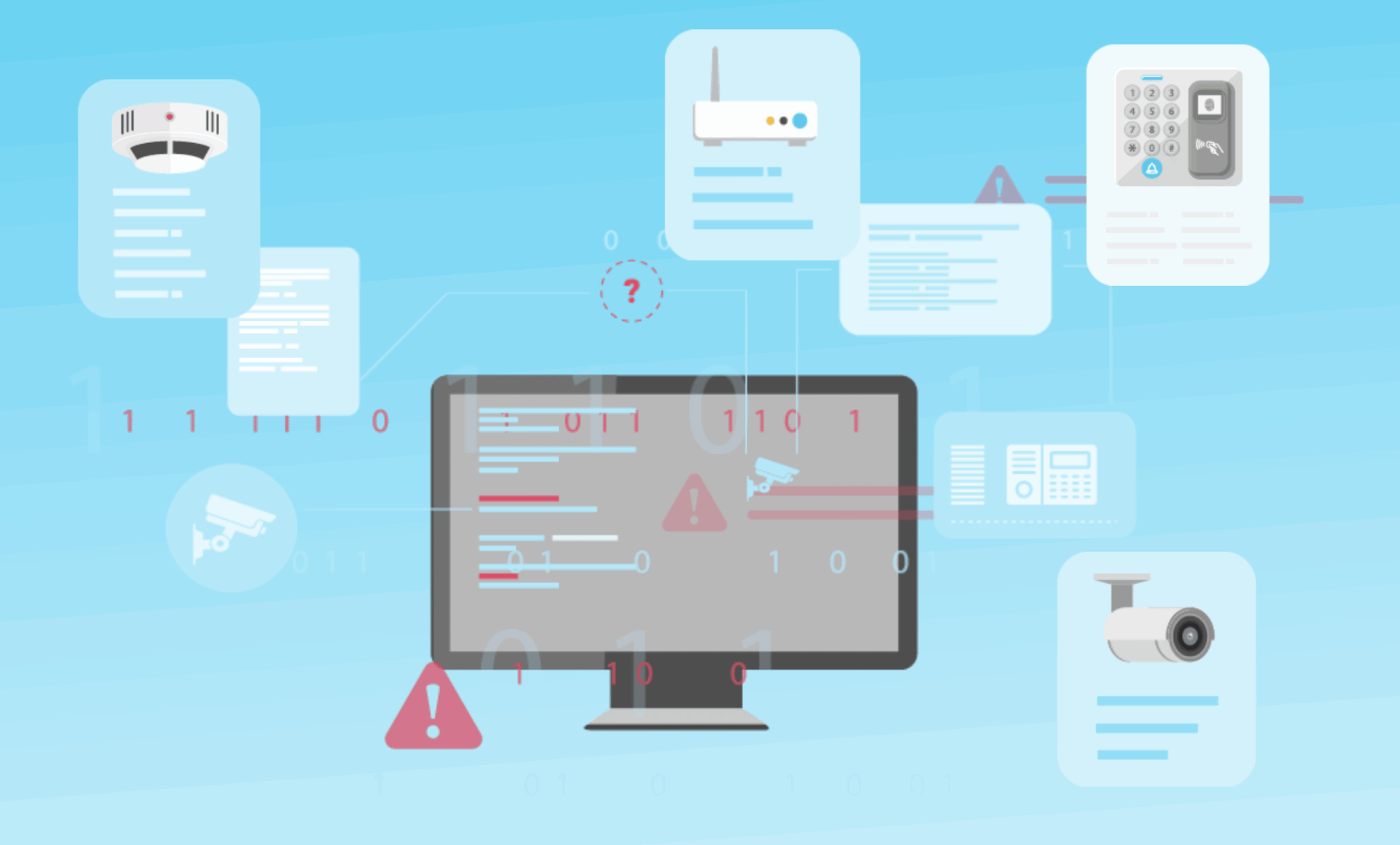
When most people hear “CVE,” their minds go straight to IT systems, not physical security. But here’s the reality: CVEs (Common Vulnerabilities and Exposures) affect everything from your network cameras to access control systems, encoders, and industrial controllers. If it runs firmware, it’s potentially vulnerable.
The physical security risk you can’t ignore
Physical security teams typically focus on uptime and functionality. If a door opens or a camera streams – that’s a win. But under the surface, these devices run complex software—firmware—that’s just as susceptible to vulnerabilities as any IT asset.
Imagine this scenario: An unauthenticated attacker exploits a vulnerability to remotely delete users from access controller web interfaces, effectively locking out legitimate users and affecting their ability to gain entry to their workplace.
CVEs need constant vigilance
The volume and frequency of CVEs demand attention. Security researchers and official organizations such as CISA (Cybersecurity and Infrastructure Security Agency) and NIST (National Institute of Standards and Technology) continually uncover new vulnerabilities. The pace is relentless. And if you think a yearly firmware update is enough, think again—new CVEs surface monthly, even weekly. “Set it and forget it” won’t work here.
From visibility to action
Anyone can dump a list of CVEs into a spreadsheet. What you really need is context:
- Which device is affected?
- What’s the source and description of the vulnerability?
- How severe is the vulnerability?
- Which tools are needed to patch it —and how?
Don’t forget about compliance
Regulatory pressure is mounting. To stay compliant from a vulnerability standpoint, organizations must constantly monitor every CVE, assess the impact, and have a plan to address it. It’s not a “one and done” report—it requires ongoing maintenance and attention.
Bottom line: Vulnerability management is key
Vulnerabilities aren’t identified automatically. Firmware doesn’t fix itself. And compliance doesn’t happen by accident.
Unfortunately, vulnerability management in physical security is often ignored, misunderstood, or siloed away into the cyber team’s domain. Cyber wants insight. Physical Security wants fixes. What’s needed is a bridge—an end-to-end solution that shows which devices are vulnerable, where the issues come from, and gives you the tools to actually patch them.
Managing CVEs in physical security devices has to be an active, ongoing, and integrated part of your physical security strategy. SecuriThings links devices to CVEs, provides clear descriptions and severity, highlights both affected and patched firmware, and — most importantly — gives you the means to patch and remediate
To learn more, take a self-guided demo of the SecuriThings platform.