The world of physical security has evolved dramatically in recent years. New device types, technologies, and applications are being introduced at a rapid rate, and the ecosystem is maturing apace. Despite these developments, there are still some lingering misconceptions about physical security.
Let’s debunk some common physical security myths so they reflect today’s reality.
Myth: Physical security is just about locks and cameras
Reality: Modern physical security involves much more than hardware.
It’s a dynamic system with lots of connected parts, including:
- Real-time monitoring: Security operations centers (SOCs) rely on live feeds, analytics, and alerts to detect and respond to incidents as they unfold.
- Incident response: When a breach or issue arises, a well-coordinated plan—involving both technology and personnel—is critical to minimize impact.
- Integration with IT and Cybersecurity: Physical security devices like cameras and access control systems are now IoT-enabled, making them part of the broader digital ecosystem.
Myth: If devices are working, we are not exposed to cybercrime
Reality: A connected device can still be operational while being hacked. Sophisticated cybercrime often goes undetected. A camera may be recording video perfectly but may still be under attack due to an unpatched vulnerability or an easy password.
Action items
- Patch vulnerabilities promptly and stay on top of firmware updates
- Follow best practices for password rotation
- Conduct routine audits to ensure devices meet current security standards
Myth: Physical security has no overlap with cybersecurity
Reality: IoT-enabled physical devices, such as cameras and access control systems, are often targeted in cyberattacks, making physical and digital security deeply interconnected.
Action items
- Make sure that IT, Cybersecurity, and Physical Security teams work together to prevent cyberattacks.
- Implement recommended device hardening policies.
- Set up a process for identifying and managing vulnerabilities.
Myth: More devices always mean better security
Reality: Adding more devices without a cohesive strategy can increase vulnerabilities and operational inefficiencies.
Action items
- Invest in integrated systems that enhance device interoperability.
- Focus on strategically placing devices to maximize coverage.
- Track end of service and end of life dates and budget accordingly.
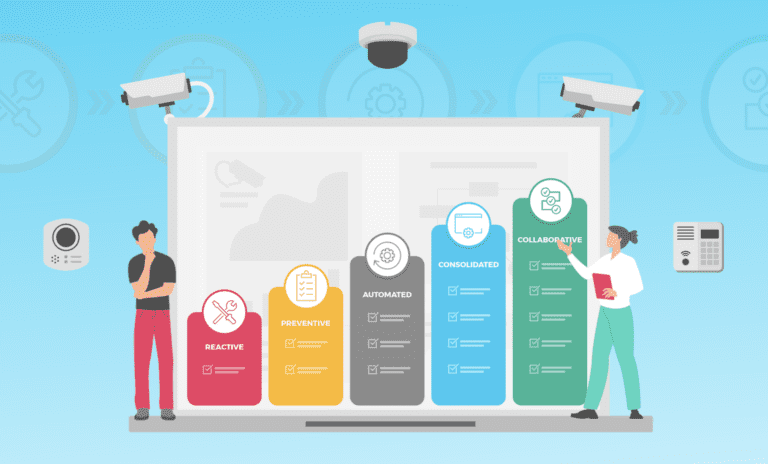
Today’s physical security landscape
Physical security is no longer a standalone operation; it’s an integral part of an organization’s overall risk management strategy. By moving beyond outdated myths and embracing a holistic, proactive approach, enterprises can better protect themselves from the evolving landscape of threats. After all, true security isn’t about the tools you have—it’s about how you manage them.
Download the eBook “Optimizing Physical Security Device Management: A Comprehensive Maturity Model” to learn more.