Connected devices are massively deployed enabling organizations (tech companies, airports, casinos, cities, high education, etc.) to enhance business and security operations. There are different teams which are dealing with these devices, who may be responsible for IoT operations involving physical security devices (cameras, access control, intrusion detection, etc.), building management (HVAC, Elevators, etc.) or even more traditional IoT devices such as printers. In addition to the teams above, there are also third-party system integrators deploying devices and responsible for the initial setup.
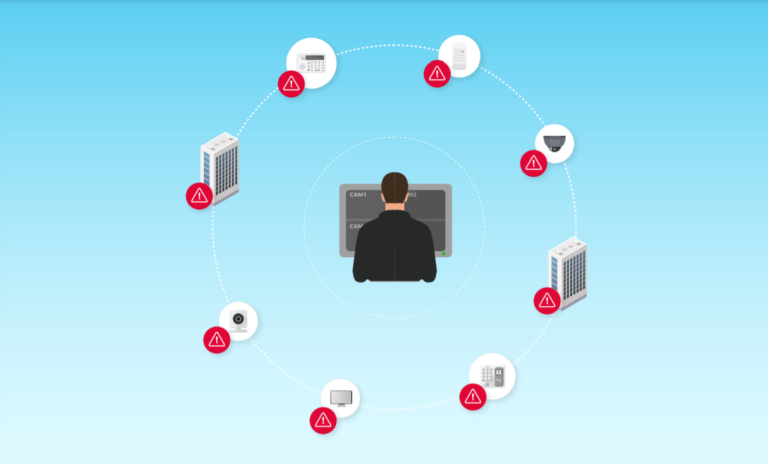
While more and more of these devices are becoming-IP enabled and massively deployed in the field, they have become a management liability. And this trend is just growing.
This is not a matter of discovery – “IoT teams” can mostly say which devices are out there, as they are accountable for their deployment and ongoing management.
We have reached a point in time that “IoT teams” (or in some cases, IT teams) have no idea what is happening with these devices, once deployed in the field – are they secure? Are their firmware versions up-to-date? Are they within compliance of the organizational policy? Are they even working as expected?
All the above make it very different from standard IT operations in terms of the type of devices, the responsibility, the way they are deployed, their physical accessibility, the eco-system players, etc. However, the same IT tools are still being used for IoT Operations.
IoTOps: A new era for IoT Operations
IoTOps encompasses all operational teams that are accountable for the deployment of IoT devices, their availability and their cyber security. These teams are responsible for monitoring the device status, directing technicians, defining and implementing organizational policies, resolving operational issues, overseeing upgrades, and more.
We can categorize the capabilities required for IoTOps in 3 buckets:
- Cyber security
- Predictive maintenance
- Automated operations
These capabilities are critical for IoT-based organizations and for teams within these organizations.
Data is Key in IoT Operations
IoTOps start with the collection of tremendous amounts of data from each and every managed device. This metadata is analyzed and translated into alerts which should be then prioritized, leveraging AI and Machine Learning capabilities.
Automation is Essential for IoT Operations
The scale of IoT deployments prevents the ongoing operations from being performed manually and require IoTOps solutions to run multiple tasks such as password rotation and firmware upgrade, across these devices, in an automated manner.
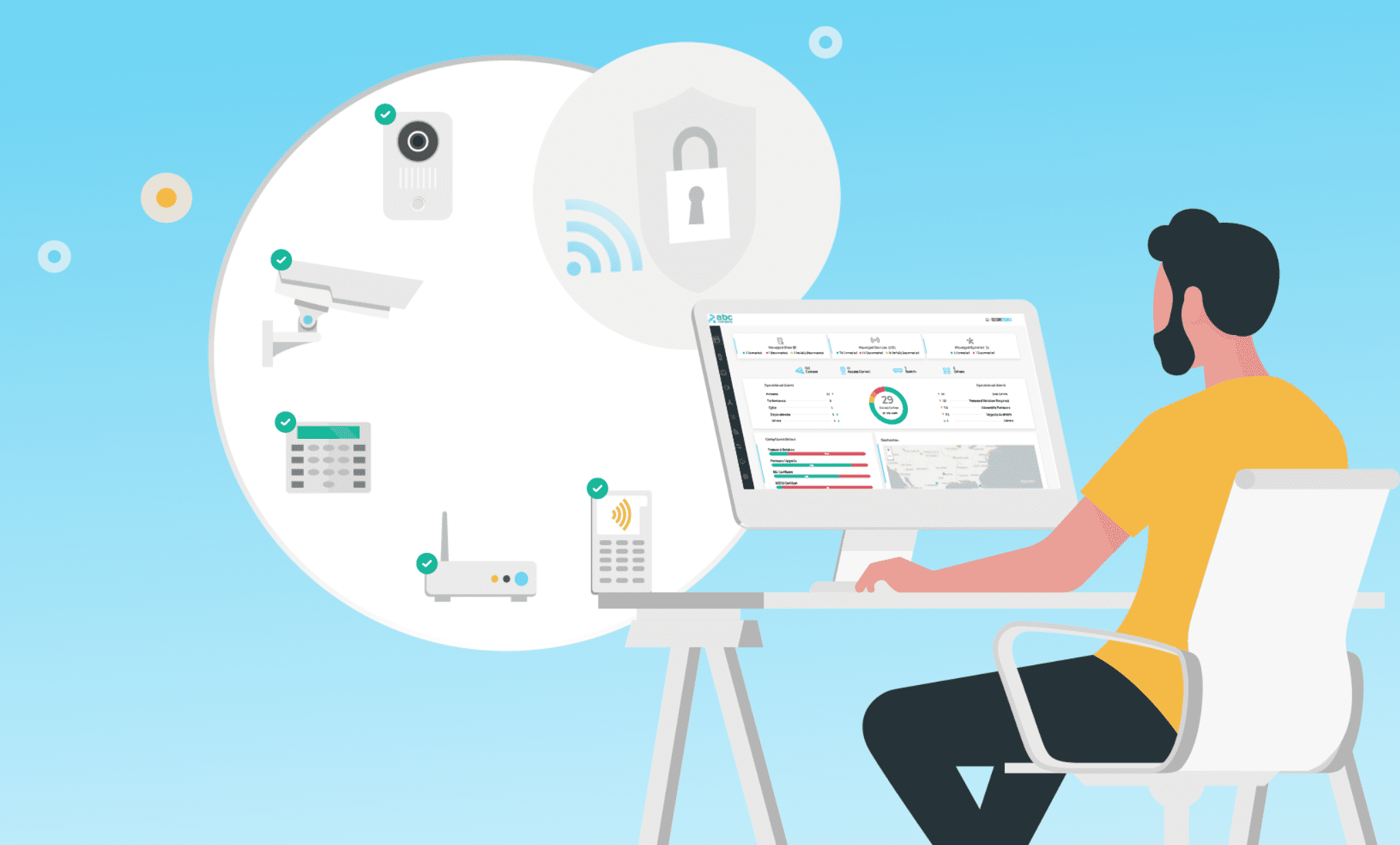
A Centralized View for Effective IoT Operations
Now that IT is also becoming a key player in IoTOps, a unified view is required to get full visibility across all connected devices, and control both their cyber security and ongoing maintenance in one single pane of glass.
IoTOps = Cyber Security + Predictive Maintenance + Automated Operations.
The time has come for IoTOps to be equipped with dedicated solutions, which will provide them with full visibility and control over the devices they are accountable for.
FAQs
What are the primary challenges in managing IoT operations?
Managing IoT operations involves several challenges, including the scale of device deployments, diverse device types, and ensuring security across all devices. Organizations often struggle with keeping firmware updated, rotating passwords, and maintaining compliance with security policies. The sheer number of devices and their geographical dispersion make manual management impractical, requiring automated solutions to ensure efficient and secure operations.
How can IoT operations benefit from predictive maintenance?
Predictive maintenance in IoT operations involves using data analytics and machine learning to predict when a device might fail or require maintenance. This approach helps organizations address issues before they lead to significant downtime or operational disruptions. By predicting and preventing potential problems, organizations can reduce maintenance costs, improve device uptime, and enhance overall operational efficiency.
Why is real-time monitoring crucial for effective IoT operations?
Real-time monitoring is crucial for effective IoT operations because it provides immediate insights into the status and health of connected devices. This continuous oversight allows organizations to quickly identify and resolve issues, ensuring that devices are functioning optimally. Real-time monitoring also enhances security by enabling instant detection of anomalies or breaches, which is essential for protecting sensitive data and maintaining compliance with security standards.
How does automation improve the efficiency of IoT operations?
Automation improves the efficiency of IoT operations by streamlining routine tasks such as firmware updates, password rotations, and compliance checks. Automated systems can perform these tasks faster and more accurately than manual processes, reducing the risk of human error. By automating these operations, organizations can focus their resources on higher-value activities, improve device reliability, and maintain a strong security posture with minimal manual intervention.
What role does data analytics play in optimizing IoT operations?
Data analytics plays a key role in optimizing IoT operations by providing actionable insights from the vast amounts of data generated by connected devices. Analytics can help organizations understand usage patterns, detect anomalies, and predict maintenance needs. By leveraging data analytics, IoT operations teams can make informed decisions, enhance device performance, and ensure that their IoT infrastructure operates efficiently and securely. This data-driven approach is essential for managing complex IoT ecosystems effectively.