Creating a safe and secure campus environment is a complex, ongoing effort involving much more than creating policies, setting up a campus patrol, and installing security cameras. It requires planning, collaboration with local law enforcement, regular risk assessments, and the strategic use of physical and digital security management tools.
From access control and perimeter defenses to emergency communication systems and campus-wide training, institutions that manage campuses must coordinate across departments to prepare for a wide range of physical, environmental, and digital threats. Even with these layers, many campuses face operational blind spots. Security systems may be in place, but they are often fragmented, dysfunctional, damaged, offline, or lacking support from a unified process.
This article examines the most common challenges campuses face in managing security infrastructure and offers best practices for enhancing system reliability, response coordination, and safety.
Summary of campus safety and security concepts
| Concept | Description |
|---|---|
| Campus safety maturity levels | Campus security maturity ranges from basic procedures like ID badges and security guards to intermediate measures involving emergency planning and law enforcement engagement and advanced systems that provide real-time monitoring of security devices. |
| Closing the gaps in security infrastructure | Current campus security operations challenges include multi-vendor device sprawl, lack of system maintenance, and insufficient coordination between physical and cybersecurity teams. |
| Best practices for modern campus security | Numerous best practices across two spheres, operational processes and coordination efforts, and system monitoring and lifecycle management, can improve visibility, integration, and resilience across campus physical security systems. |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Campus safety maturity levels
Campus safety strategies differ widely, but they usually fall into three maturity levels:
- Basic maturity level (what most campuses already have): This includes security guards, surveillance cameras, locked doors, and ID badges. These tools help keep people safe daily, but don’t provide real-time insight.
- Intermediate maturity level (what campuses are starting to adopt): Many campuses are taking safety a step further. They’re building emergency response plans, running safety drills, partnering with local police, and offering systems for students and staff to report anything unusual.
- Advanced maturity level (what most campuses haven’t addressed yet): Few campuses have the tools to see how their security systems perform in real time. That means they might not know if a camera is down or a door isn’t locking properly. The most advanced campuses use tools that connect all their systems, update everything automatically, and alert their teams when something needs attention.
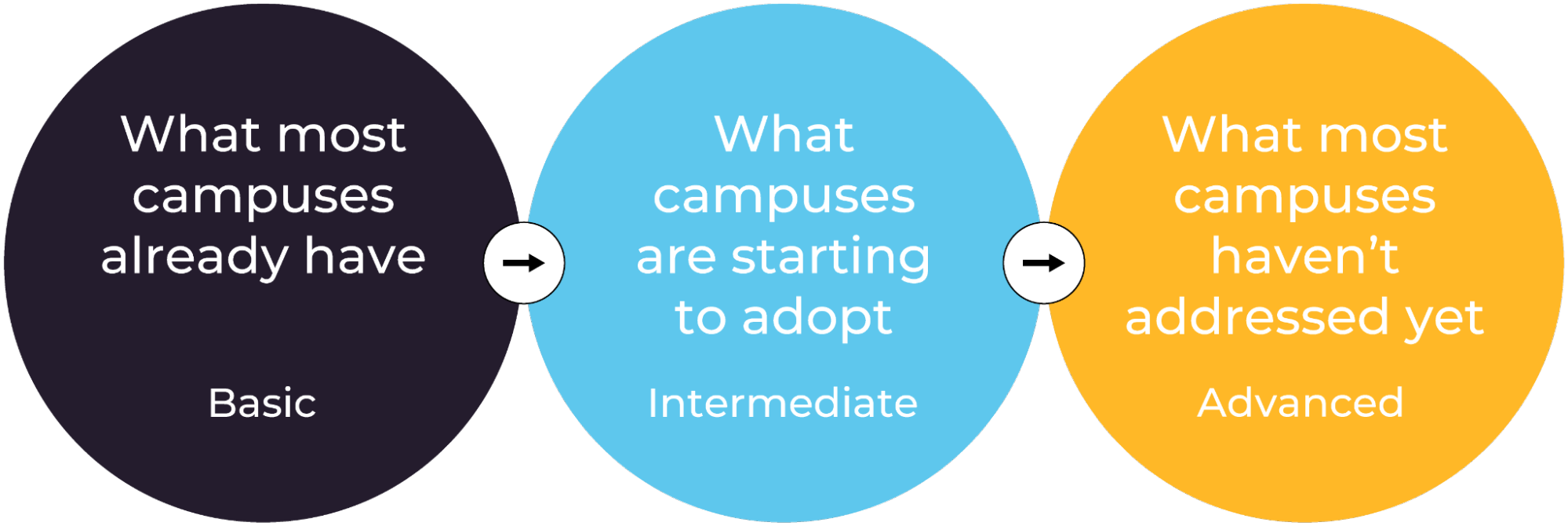
Levels of maturity for campus security
Closing the gaps in security infrastructure
Even with campuses equipped with cameras, access controls, and other security measures, hidden issues often complicate efforts to ensure safety. These challenges are not signs of failure but are typical when systems expand over time without sufficient tracking.
The diagram below highlights four major areas where campus security operations often fall short even when basic security tools exist. These include device status visibility concerns, outdated or missed maintenance actions, disconnected systems that don’t communicate, and poor coordination across teams.
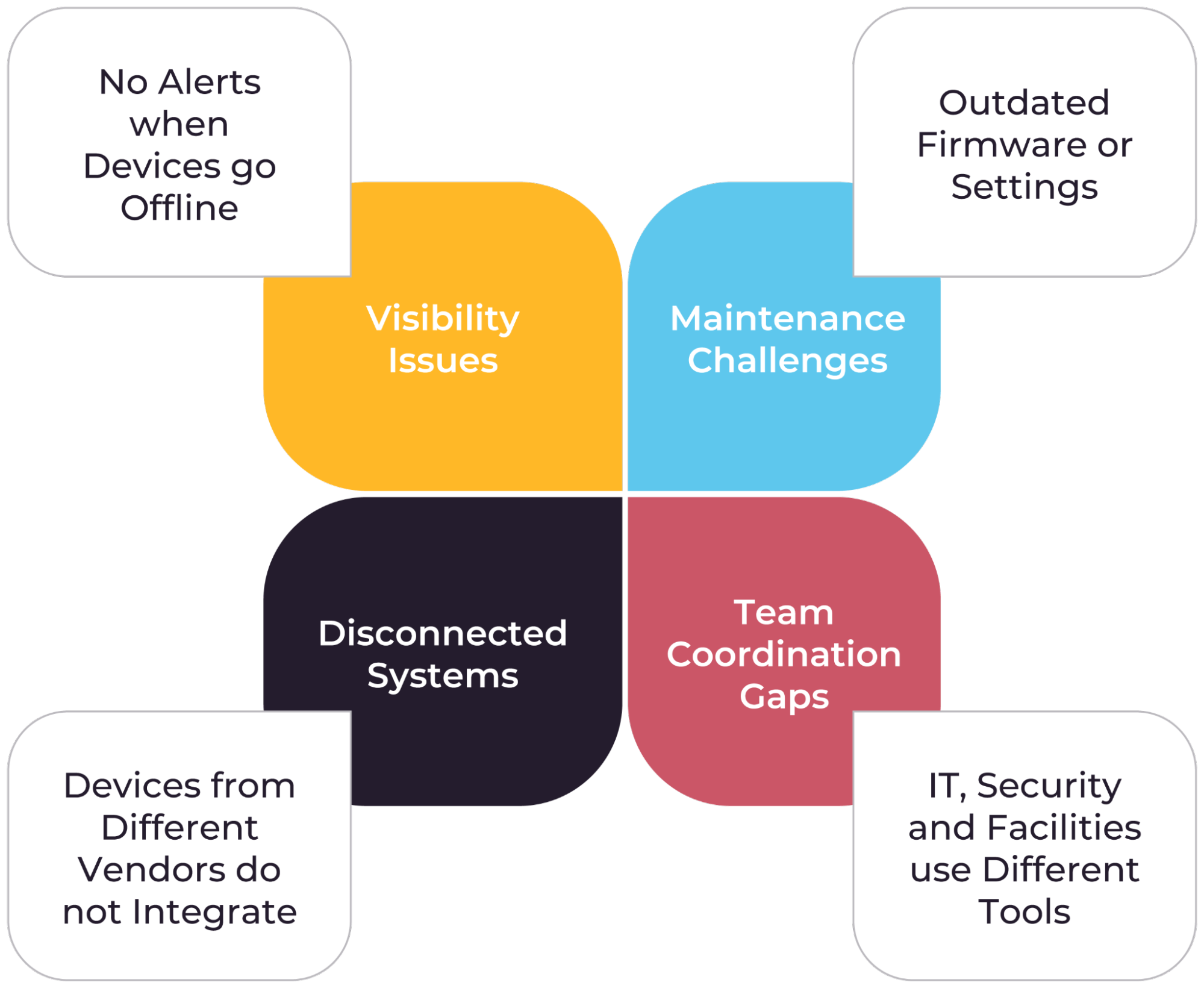
Common operational gaps in campus security
The table below outlines common security gaps that campuses face, grouped by category.
| Gap category | Gap | Impact |
|---|---|---|
| Monitoring and visibility | Limited visibility into device and system performance | Security teams often lack centralized insight into whether critical devices, like cameras, access readers, or intercoms, are online, working correctly, or misconfigured. This limits their ability to respond to issues before they affect operations. |
| No real-time dashboard to monitor device status | Lack of real-time visibility increases the risk of missing urgent issues. | |
| Maintenance challenges
|
Manual firmware updates and checks. | Without automation, devices may operate with outdated software, exposing vulnerabilities. |
| Credentials not rotated or updated regularly. | Outdated credentials can become a security liability if not regularly addressed. | |
| Disconnected systems | Devices from different vendors do not integrate. | Lack of integration slows down response time and limits the value of system data. |
| Team coordination gaps | Security, IT, and facilities teams use separate tools. | Different teams using separate tools often lead to duplicated work or miscommunication. |
| No unified process for resolving or escalating issues. | Lack of coordination results in unclear ownership of problems or delayed resolutions. | |
| Inconsistent incident reporting | No consistent system to log or review incidents | Without logging, campuses miss the opportunity to track trends or improve their response. |
Best practices for modern campus security: Operational processes and coordination efforts
Making campuses safer isn’t just about installing more cameras or increasing security presence; it’s about how people collaborate and how well systems are maintained. Operational processes and coordination efforts focus on how campus teams work together and respond to incidents.
To improve campus safety, you should start with better organization, shared visibility, and department readiness. The following practices help clarify responsibilities, guarantee systems are operational during drills and emergencies, and enhance response times when every second counts.
Maintain a physical security asset inventory
A complete inventory is the foundation for managing a secure environment. It should include every device, from cameras and access control panels to alarms and intercoms, along with each one’s location, configuration, and status. You should keep this inventory up to date to allow teams to identify blind spots, ensure coverage, and plan maintenance or upgrades more effectively.
Define and review security zones
Campuses consist of different types of spaces, each with unique risk levels, such as classrooms, dormitories, labs, and open common areas. You should group these areas into clearly defined zones to allow teams to tailor security controls (e.g., restricted access, video coverage, patrol frequency) based on real-world needs.
Establish an incident response matrix
When an incident occurs, whether it’s a door forced open, a suspicious individual spotted, or a system outage, there should be no confusion about what to do. An incident response matrix should clearly outline roles, communication paths, and step-by-step actions for different types of incidents. Regularly review and update this matrix to reflect current systems, risks, and team structure.
Conduct regular inspections
You should conduct regularly scheduled physical inspections of security systems and infrastructure to help prevent failures. This includes checking the integrity of door locks, functionality of intercoms, visibility of camera feeds, and access control points. Inspections should follow a checklist and be scheduled consistently to catch issues before they impact operations.
Include systems in emergency drills
Design emergency drills based on human actions, evacuation routes, lockdown protocols, and so forth. However, the technology also needs to be tested. Do alert systems send the right messages? Do cameras cover key areas? Do doors lock or unlock as expected? Include systems in these tests to ensure they’re part of the overall safety response and to help surface hidden issues.
Share dashboards across departments
Too often, campus security, IT, and facilities work from separate systems. You should provide shared access to real-time dashboards, showing device health, alerts, and incident trends, allowing for better coordination and faster action. When everyone sees the same picture, responsibilities are clearer and resolution becomes more efficient.
System monitoring and lifecycle management
System monitoring and lifecycle management focus on keeping security infrastructure healthy, connected, and effective. The following best practices ensure that the security infrastructure remains functional, visible, and easy to manage, even at scale.
Monitor device health from a single platform
Without centralized monitoring, campuses risk losing track of which devices are working and which are not. A unified dashboard allows teams to see the status of all physical security devices, cameras, sensors, and access panels in real time. This visibility makes it easier to identify outages, detect unusual behavior, and respond before a system failure becomes a security incident.
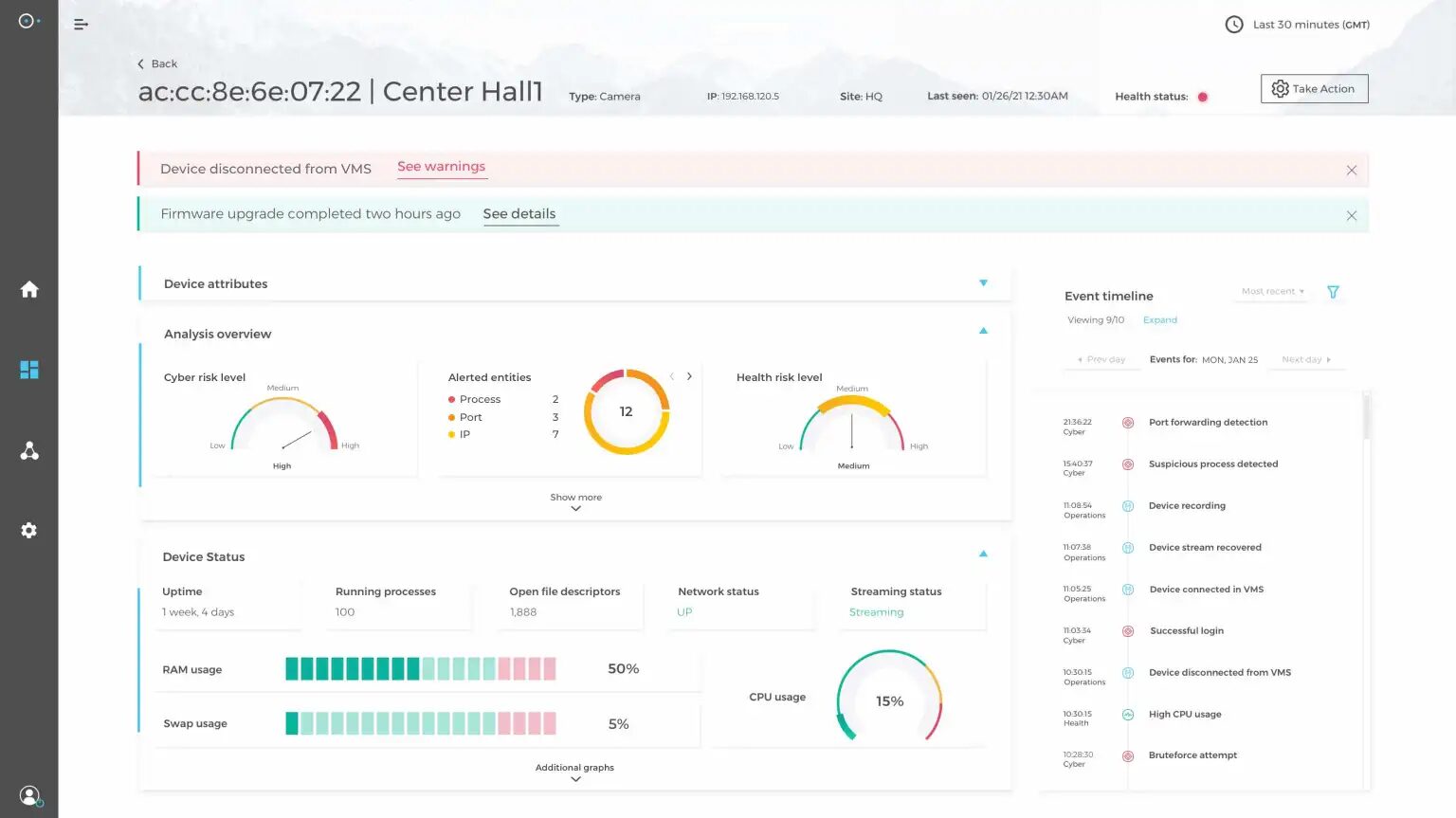
Example of a centralized dashboard showing real-time device health, status, risk levels, and recent security events (source)
Automate updates, credential rotation, and diagnostics
Many devices require regular firmware updates or password changes, but manual processes are often slow and prone to error. You should automate these tasks to ensure that devices stay up to date and secure without burdening staff. This also helps with routine diagnostics, flagging degraded performance or missed connections early.
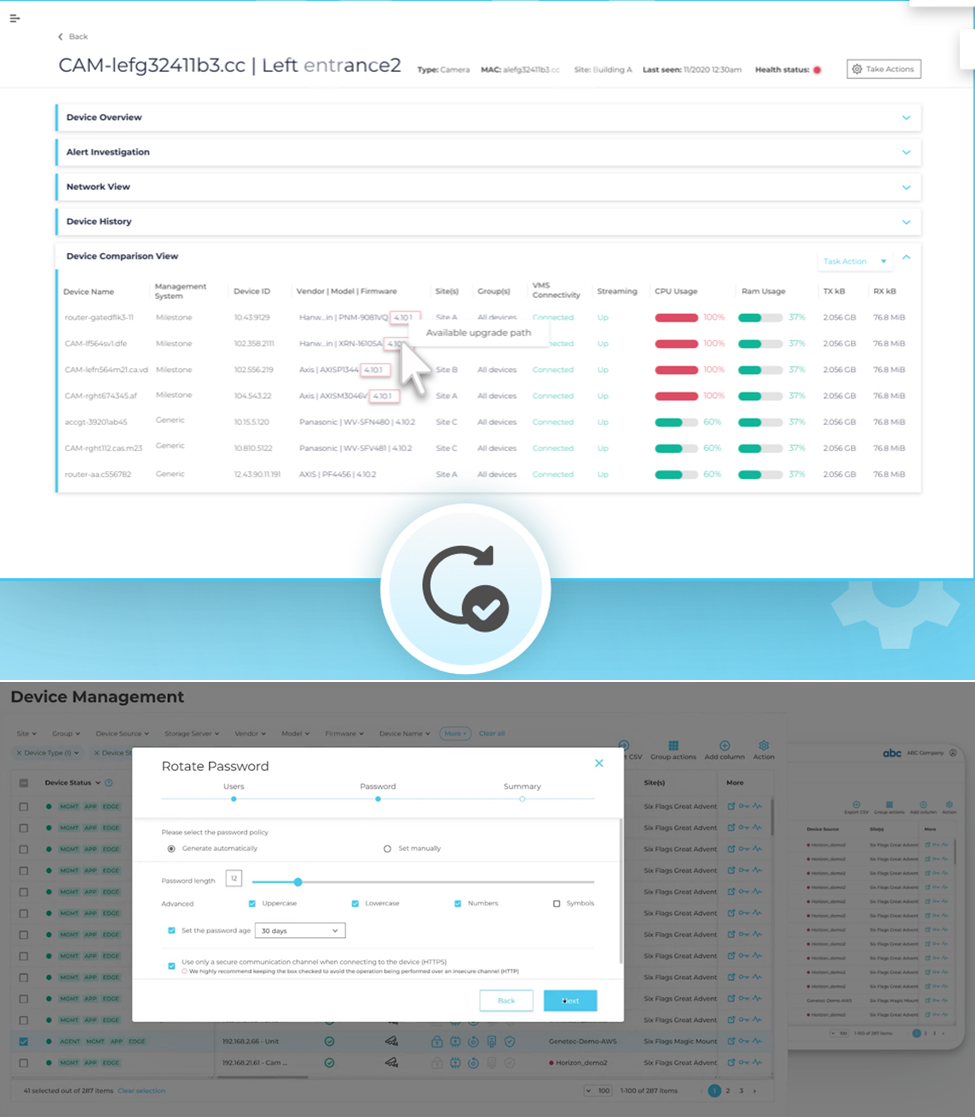
Automated device management in action: centralized firmware upgrades, password rotation, and performance insights across multiple security devices (source)
Integrate systems for better coordination
Many campuses still operate disconnected systems: video feeds that don’t link to access logs, alerts that don’t trigger visual confirmation, and sensors that can’t talk to one another. Integration bridges these gaps. When systems work together, like linking door access with camera footage, it speeds up investigations and improves incident response.
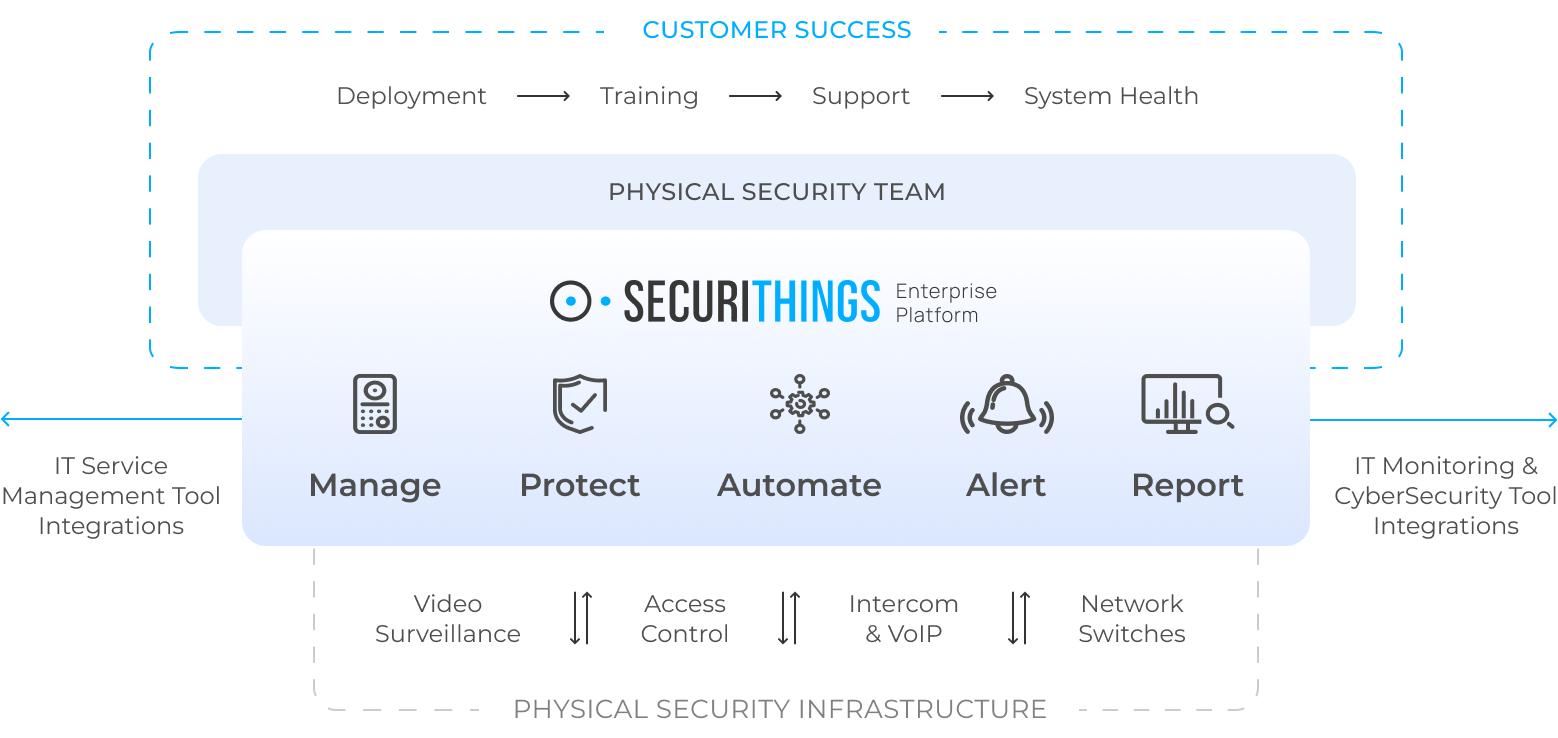
Proactively manage any physical security environment from one place (source)
Use analytics to prioritize and resolve device issues
When hundreds or even thousands of devices are involved, it’s easy to get overwhelmed by alerts. Smart analytics should highlight the most important issues first, such as frequently failing cameras or repeated access attempts at odd hours. These insights help teams focus their attention, allocate resources, and prevent problems before they grow.
Implement physical intrusion detection
Modern intrusion detection tools go beyond motion sensors. They can flag doors forced open, detect entry after hours, or recognize patterns that suggest unauthorized access. Real-time alerts help security teams respond faster, especially when combined with visual confirmation from integrated video systems.
Implement device lifecycle management
Track each physical security device from onboarding to retirement, ensuring regular maintenance, firmware updates, credential rotation, and timely decommissioning, all through a centralized process.
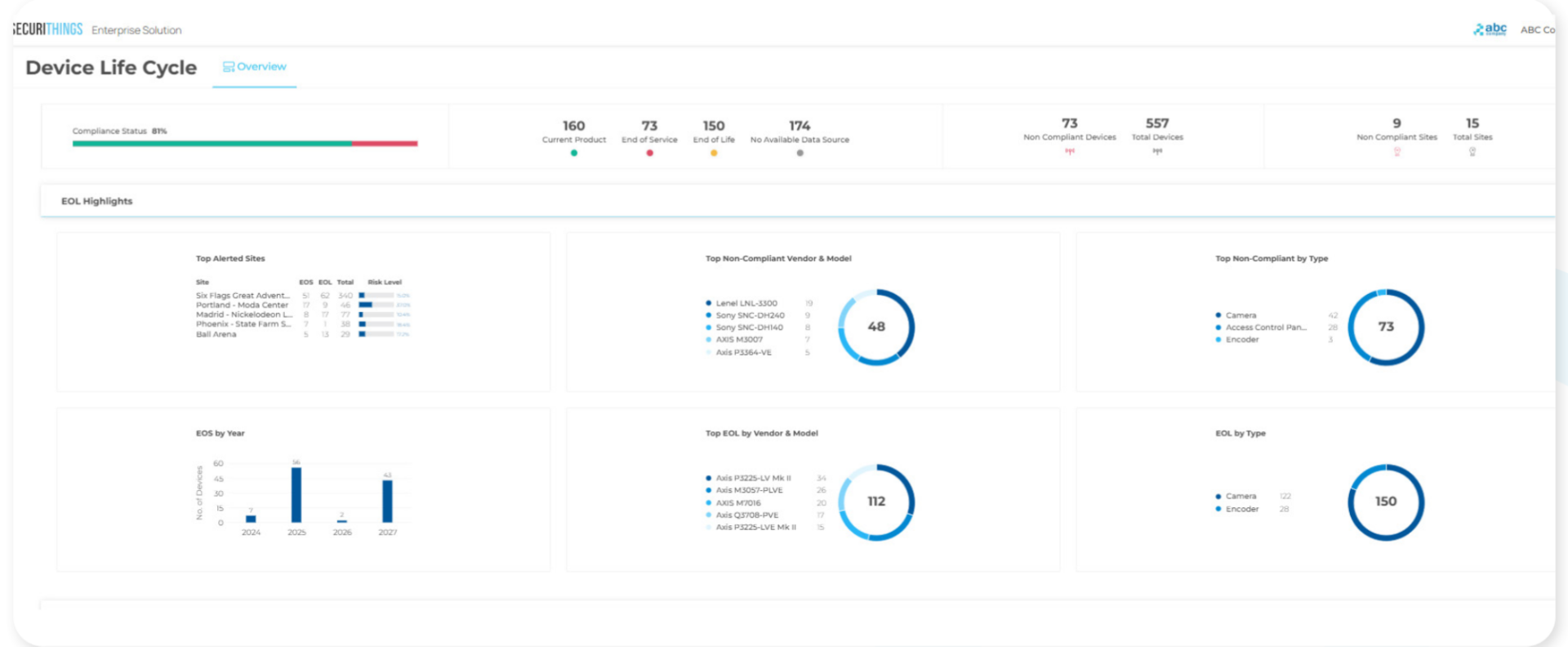
Dashboard view of device lifecycle status, highlighting compliance, end-of-life risk, and non-compliant devices across multiple sites (Source)
As physical security systems become more connected, protecting them from cyber threats is just as important as their core operational function. Attackers are increasingly targeting cameras, access control units, and other edge devices, looking for vulnerable entry points into broader IT networks.
To reduce cyber risk, it’s important to follow best practices such as regularly rotating device credentials with strong, IT-compliant passwords, applying firmware updates as soon as they’re available, and monitoring devices for known vulnerabilities. These actions help close significant security gaps, especially in systems running unchanged for years.
SSL certificate management is another key area often overlooked. Expired or mismanaged certificates can create blind spots in device communications and expose systems to interception and eavesdropping.
Likewise, vulnerabilities in access control systems underscore the need for ongoing monitoring and risk mitigation. Cybersecurity isn’t a separate layer; it’s inserted into every aspect of device lifecycle management. When done right, it protects the physical environment and the digital infrastructure supporting it.
Last thoughts
As campus environments become more complex, the demands on safety and security teams increase. Fixing common gaps like disconnected systems, limited visibility, and outdated maintenance processes is important for reducing risk and building trust across the institution. By adopting coordinated operational practices and modern lifecycle management strategies, campuses can shift from reactive to proactive security.
Solutions like SecuriThings assist campuses in implementing these strategies by providing visibility, automation, and integration throughout the physical security system. With the proper tools and structure, campuses can ensure that safety infrastructure is functional, resilient, scalable, and prepared for future challenges.