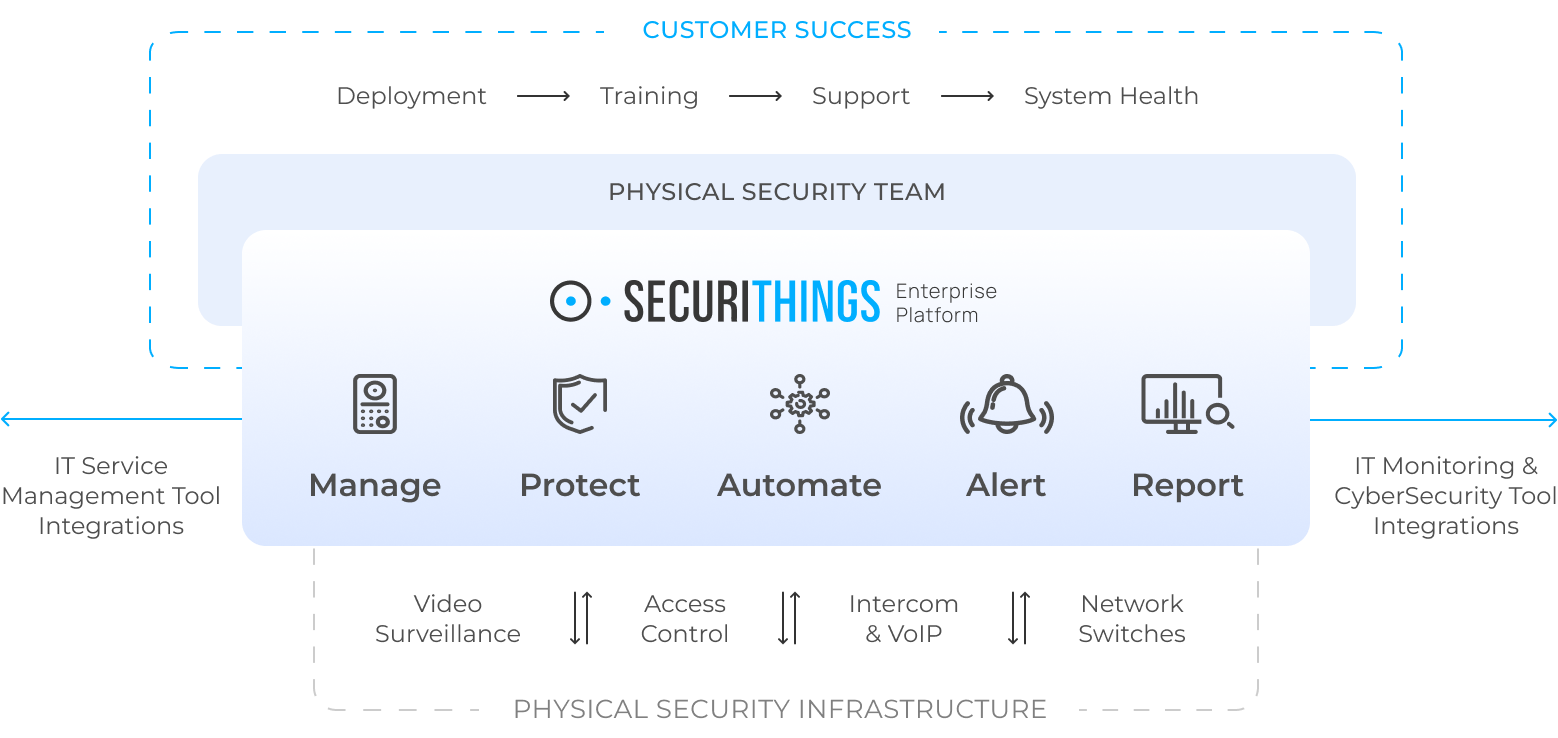
Enterprise Platform
Purpose-built for the modern enterprise
For teams responsible for managing, operating, and cyber-protecting physical security infrastructure.
One platform
for all devices
Proactively manage any heterogeneous physical security environment from one place.
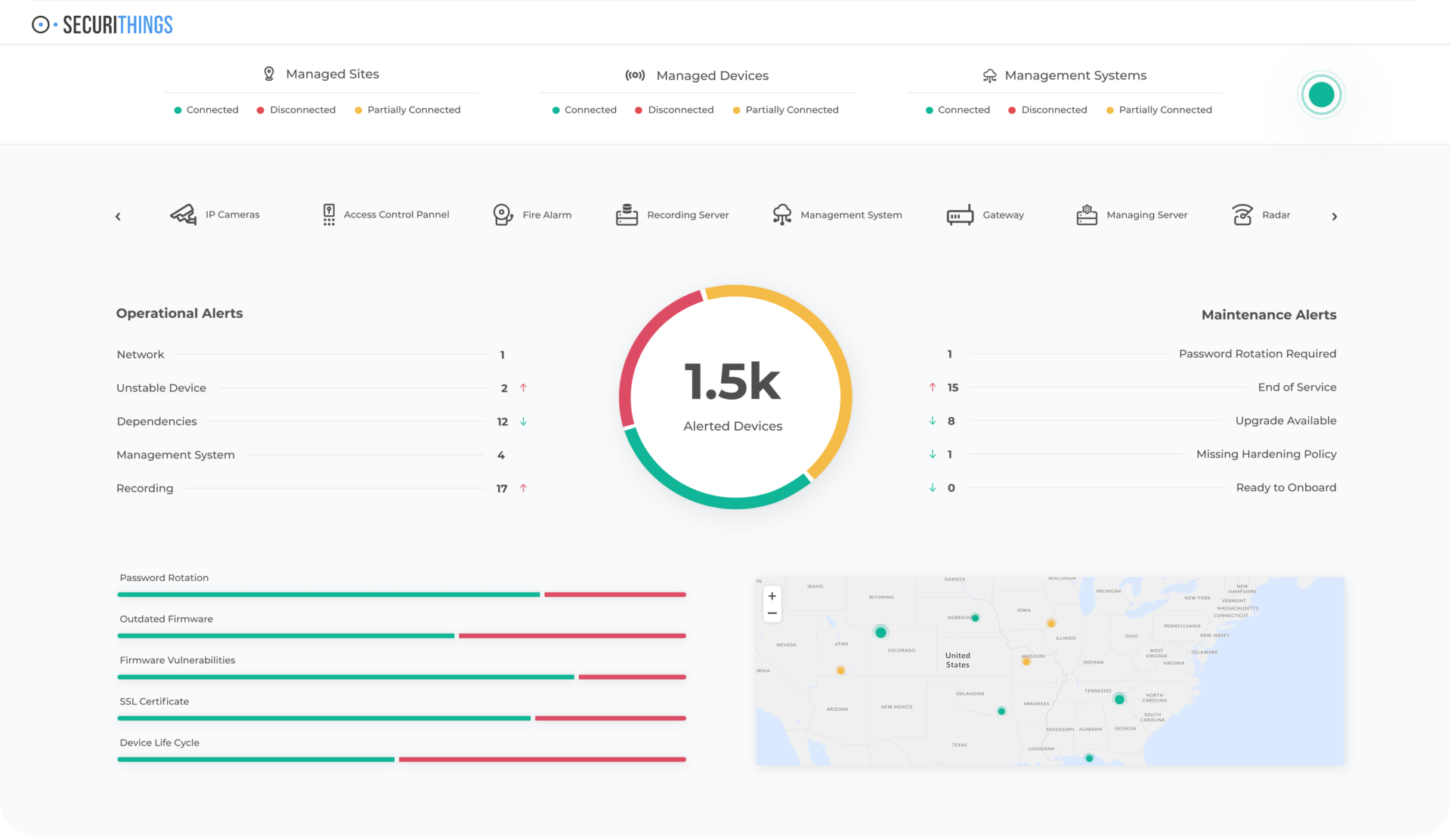
Essential Visibility
- Core platform module
- Comprehensive visibility into physical security infrastructure
- Intuitive dashboards and extensive reporting to monitor all systems and track performance
Operational Management
- Add-on platform module
- Simplified device operations and remediation
- Maintain optimal system uptime across your entire infrastructure from a single pane of glass
Cybersecurity Protection
- Add-on platform module
- Comprehensive and cost-effective cyber protection of physical security infrastructure
- Eliminates expensive, inefficient, and error-prone manual processes
Enterprise Extension
- Add-on platform module
- Enable enterprise-wide collaboration and raise the profile of your team
- Provides the necessary APIs for collaboration between Security, IT and other key stakeholders
Customer Success
- Designated team of experts to empower and support you every step of the way
- System deployment and health monitoring
- Ongoing training and support services