Hospital Physical Security Best Practices
Hospitals face unique challenges enforcing physical security, given the complex interplay among their critical infrastructure, IoT devices, and physical security systems. For example, devices deployed to protect buildings, such as IP surveillance cameras, can be exploited and attack other critical IP infrastructures instead. Avoiding such issues requires close coordination between the physical security and IT/cybersecurity teams.
As healthcare security engineers, your role involves safeguarding all IT systems and ensuring the operational integrity of all medical devices and patient care systems that are critical for the safe and efficient operation of the hospital. This article explores practical strategies for protecting hospital facilities, medical IoT devices, and physical security infrastructure while aligning with cybersecurity and regulatory compliance requirements.
| Concept | Description |
|---|---|
| Physical access control systems | Systems like badge readers and biometric scanners are used to control facility entry. |
| IoT medical device security | It is necessary to protect devices like infusion pumps and patient monitors from cyber threats. |
| Exploitable physical security devices | Examples include IP cameras which can be manipulated if they are not secured. |
| Role-based access control | This security model restricts access based on user roles to minimize risks. |
| Device authentication | This is an effective method to verify the identity of devices before they connect to the network. |
| Network segmentation | Divide a network into zones to limit the spread of potential attacks. |
| Physical security management software | Automate tasks like firmware updates and password rotation for physical devices. |
| Vulnerability assessments | Regularly identify security weaknesses in systems and devices. |
| Compliance reporting | Document security measures to meet regulations like HIPAA. |
| Integrated security operations | Ensure collaboration between physical and cybersecurity teams for comprehensive protection. |
Physical access control systems
Physical access control systems are essential for managing physical entry to hospital facilities and safeguarding restricted areas. These systems should include various technologies designed to secure perimeters, internal zones, and critical assets.
Here are some key systems to consider and relevant recommendations.
| System | Description | Recommendations |
|---|---|---|
| Badge readers and access cards | These grant entrance to authorized personnel, allowing or restricting access to specific areas based on roles.
Vulnerabilities include the potential for lost or stolen cards being misused. |
|
| Biometric systems | Tools include fingerprint scanners, facial recognition, or iris scanners.
Risks involve spoofing or failure to recognize users in emergencies.
|
|
| Turnstiles and mantraps | These physical controls prevent tailgating or piggybacking and provide a controlled space to verify identity before granting entry. |
|
| Surveillance cameras | Cameras are used to monitor entrances, exits, and sensitive areas. They integrate with motion detection and AI analytics for real-time alerts.
Vulnerabilities include unsecured IP cameras being accessed remotely. |
|
| Perimeter security systems | These systems include fences, gates, and motion detection sensors. They integrate with alarms to alert security personnel of breaches.
|
|
| Visitor management systems | These are systems that register and monitor visitors. They can be used to issue temporary access badges with limited permissions.
|
|
Here are some other general recommendations and principles for security engineers:
- Prioritize flexibility: Choose systems that can adapt to both high-security and high-traffic environments.
- Avoid bottlenecks: Avoid solutions like turnstiles in public areas where patient flow is critical.
- Maintain accessibility: Ensure that security measures are inclusive and do not obstruct emergency services or patients with disabilities.
- Focus on layered security: Use a combination of less intrusive measures (e.g., access cards) in public areas and stricter measures (e.g., biometrics) in sensitive zones.
- Regular assessments: Conduct regular risk assessments to identify areas where enhanced security is necessary without compromising operational efficiency.
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
IoT medical device security
IoT medical devices like infusion pumps, patient monitors, and imaging equipment are critical to patient care but introduce significant cybersecurity risks if not adequately protected. These devices often connect to hospital networks, making them potential entry points for attackers.
Here are some of the specific IoT medical device security challenge areas:
- Default credentials: Many IoT devices ship with default usernames and passwords, making them vulnerable to brute-force attacks.
- Unpatched vulnerabilities: Medical devices often have long life cycles but lack regular firmware updates.
- Network exposure: IoT devices are frequently placed on networks without proper segmentation, increasing the risk of lateral movement.
- Data integrity: Compromised devices can alter patient data, leading to misdiagnosis or incorrect treatment.
The following examples highlight the necessity of robust security measures:
- An infusion pump with default credentials is accessed remotely, enabling an attacker to alter dosage levels.
- An imaging device with outdated firmware is used as a foothold to compromise the hospital’s internal network.
- An MRI machine connected to the hospital’s network with default credentials is hijacked, allowing attackers to access sensitive patient images and proprietary medical data.
- Attackers accessed connected wearable devices, such as heart rate trackers used for remote patient monitoring through unsecured Bluetooth connections, exposing sensitive patient information.
The table below lays out some specific recommendations in this area for security engineers.
| Category | Recommendations |
|---|---|
| Device authentication |
|
| Network segmentation |
|
| Patch management |
|
| Real-time monitoring |
|
| Staff training |
|
Modern platforms designed for IoT device management provide comprehensive oversight, offering capabilities like:
- Automated password rotation to eliminate reliance on default credentials
- Real-time monitoring and alerts to detect anomalies or suspicious activity
- Centralized patch management to streamline firmware updates and ensure compliance
- Asset tracking to maintain an up-to-date inventory of connected devices
Such platforms ensure operational continuity while reducing the risk of exploitation, helping healthcare facilities efficiently secure IoT infrastructure.
Exploitable physical security devices
Physical security devices, such as IP cameras, and intercom systems, are integral to hospital operations but can also serve as exploitable points of entry for attackers if not properly secured. As these devices become increasingly interconnected with IT infrastructure, they present various challenges.
Unsecured IP cameras are vulnerable to unauthorized remote access if default credentials are not changed. They can provide attackers with live video feeds or allow them to disable surveillance.
In addition to physical security devices, attackers could also exploit vulnerabilities in network-connected elevator controls to disrupt operations or gain physical access to restricted floors. Similarly, a lack of encryption in older intercom systems could allow eavesdropping or unauthorized communication.
There are also remote access risks to consider. Physical security devices accessible via unsecured remote connections are a common target for attackers seeking lateral movement.
The following examples illustrate how vulnerabilities in physical devices can be exploited, highlighting the critical need for robust security measures:
- An IP camera with an exposed web interface is accessed remotely, allowing an attacker to monitor sensitive hospital areas.
- A networked elevator system is exploited to bypass physical security controls, granting access to restricted floors.
Here are some specific recommendations for security engineers:
- Encrypt communications: Use end-to-end encryption for all data streams, including IP cameras and intercoms.
- Implement centralized management: Employ centralized management platforms to monitor device status, apply updates, and manage access.
- Regular firmware updates: Ensure that all devices are running the latest firmware to protect against known vulnerabilities.
- Network segmentation: Place physical security devices on isolated VLANs to reduce the risk of cross-infection.
- Penetration testing: Conduct regular penetration tests to identify exploitable vulnerabilities in physical security systems.
Role-based access control
Role-based access control (RBAC) is a critical framework for managing access within hospitals. RBAC minimizes the risk of unauthorized access and potential breaches by limiting access to systems and areas based on user roles.
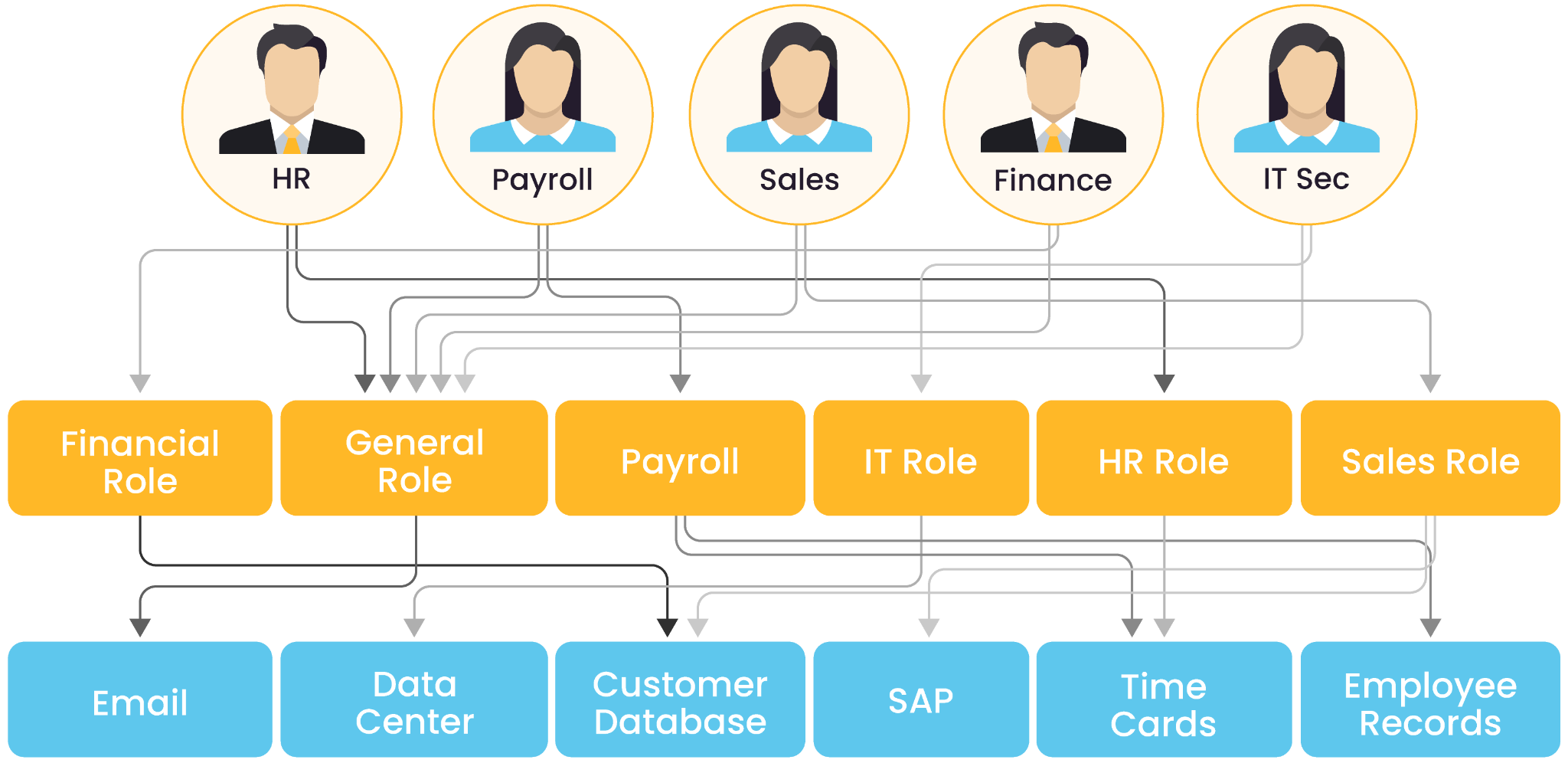
Simple graph illustrating the basics of RBAC (source)
Here are some key challenges for security engineers related to RBAC:
- Dynamic roles: Healthcare environments often have staff with shifting roles, such as visiting physicians or temporary contractors, which can complicate access management.
- Overprivileged accounts: Staff members may have access to areas or systems beyond their responsibilities, increasing risk.
- Manual role updates: Without automation, keeping roles updated can lead to outdated permissions and security gaps.
One example of a problematic scenario is a visiting physician. Unlike a resident physician, this individual probably needs to be given only temporary access to specific patient records and restricted physical areas for the duration of their contract.
Here are some specific recommended RBAC best practices:
- Define clear roles: Establish well-defined roles for all staff, contractors, and visitors. Use the principle of least privilege to assign access.
- Automate role management: Leverage identity and access management (IAM) tools to automate role assignments and updates. Implement workflows to review and approve changes.
- Integrate with physical and digital systems: Ensure that RBAC is consistently applied across both physical access (e.g., badge systems) and IT systems (e.g., patient records).
- Conduct regular audits: Periodically review access logs to identify anomalies or misuse. Ensure that roles reflect current job responsibilities and remove unnecessary privileges.
- Institute both temporary and emergency access controls: Provide time-limited access for temporary staff or emergencies. Use multi-factor authentication (MFA) for sensitive systems and areas.
Device authentication
Device authentication is an essential layer of defense in securing the interconnected systems within hospitals, including IoT devices and physical security infrastructure. For security engineers, the objective is to ensure that only authorized devices can access the network, communicate with other systems, and perform their intended functions without introducing vulnerabilities. This layer of security directly mitigates risks such as unauthorized device access, network infiltration, and operational disruptions.
In hospitals, the challenge of device authentication lies in the diversity and criticality of devices. Many IoT devices, such as infusion pumps and imaging systems, operate continuously and cannot tolerate downtime, making real-time and non-intrusive authentication mechanisms critical.
To meet these challenges, hospital security engineers need to implement authentication protocols that integrate seamlessly with their operational environments. They should use certificate-based authentication to establish trust between devices, relying on cryptographic methods to validate identities without human intervention. They should also leverage public key infrastructure (PKI) to issue, manage, and revoke device certificates, ensuring a secure lifecycle for every connected device.
Another critical approach is adopting zero-trust architecture (ZTA), where every device—regardless of its location or previous trust level—is continuously authenticated and authorized before gaining access to the network. This framework ensures that even devices operating within the hospital’s internal networks are not exempt from scrutiny, significantly reducing the risk of lateral movement by attackers. Security engineers should also focus on automating credential rotation and updates through centralized management platforms, reducing the operational burden while ensuring compliance with stringent security policies.
Device whitelisting is another effective strategy for enhancing security. By restricting network access to a predefined list of authenticated and approved devices, hospitals can limit exposure to rogue or compromised systems. Additionally, multi-factor authentication (MFA) for critical devices can further bolster security by requiring multiple validation layers, such as device certificates paired with biometric verification or one-time tokens.
For security engineers, the focus extends beyond merely implementing authentication protocols. Continuous monitoring and logging of authentication events are essential for detecting anomalies and responding to potential threats. Additionally, the integration of authentication systems with broader security operations, such as security information and event management (SIEM) tools, allows for comprehensive threat detection and incident response.
Network segmentation
Dividing the hospital’s network into distinct segments or zones allows security engineers to limit the lateral movement of attackers, protect sensitive data, and reduce the overall risk of breaches. IoT devices, physical security systems, and critical IT infrastructure coexist in hospitals, and segmentation ensures that vulnerabilities in one area do not compromise the entire network.
Without segmentation, security systems often share the same network, creating a flat architecture that allows attackers to move freely once they gain access. For example, a compromised security camera could serve as a gateway for attackers to access sensitive patient data or disrupt critical operations.
Here are some best practices for network segmentation:
- Create dedicated zones: Security engineers should establish separate network segments for clinical systems, administrative operations, IoT devices, and guest Wi-Fi. Each segment should be tailored to the specific security needs and risk levels of the devices and systems it contains.
- Use virtual local area networks (VLANs): VLANs enable logical segmentation within a single physical network, allowing devices to be grouped based on function or access level. For example, all patient monitoring devices could be placed on one VLAN, while administrative systems reside on another.
- Implement firewalls between segments: Firewalls can control and monitor traffic between network segments, ensuring that only authorized communication occurs.
- Enforce access controls: RBAC and MFA should be implemented to restrict access to specific network segments based on user roles and responsibilities.
- Monitor inter-segment traffic: Deploy network monitoring tools to detect and respond to unusual traffic patterns or unauthorized access attempts between segments. Real-time monitoring is critical for identifying threats before they escalate.
Physical security management software
Hospitals rely on various physical security systems, including access control devices, IP cameras, intercoms, and biometric systems. Without a centralized solution, managing these different devices becomes challenging, leading to vulnerabilities such as unpatched firmware, inconsistent password policies, or undetected device failures.
Physical security management software addresses these challenges by integrating device management, monitoring, and compliance reporting into a single platform.
This software enables real-time visibility into the status of all connected devices, ensuring that security engineers are promptly alerted to potential issues, such as a disabled surveillance camera or a device operating with outdated firmware. The following table shows the key features and benefits of such software.
| Key feature | Description |
|---|---|
| Centralized monitoring and control | The software provides a unified dashboard for tracking the health and status of all physical security devices. For example, if an IP camera is disconnected or an access control device is tampered with, the system can send real-time alerts to security teams. |
| Automated updates and patching | Keeping devices up to date with the latest security patches is critical in preventing exploitation of known vulnerabilities. Physical security management software automates this process, ensuring that all devices are protected without disrupting hospital operations. |
| Password management | Automated password rotation eliminates the risk of weak or reused credentials. Security engineers can set policies to enforce strong, unique passwords across all devices and ensure compliance with industry standards. |
| Regulatory compliance | Hospitals must comply with regulations like HIPAA, which mandate stringent controls over both physical and digital security. The software simplifies compliance reporting by generating detailed audit logs, asset inventories, and security status reports. |
| Device lifecycle management | From deployment to decommissioning, the software helps track the lifecycle of all security devices, ensuring that outdated or unsupported devices are replaced before they become security risks. |
| Integration with IT and cybersecurity tools | By integrating physical security data with broader cybersecurity tools, such as SIEM platforms, the software enables a more cohesive and responsive security posture. |
In hospitals, the interconnected nature of IoT devices, physical security systems, and IT infrastructure demands seamless coordination. Physical security management software facilitates this by bridging the gap between physical and digital security measures. For example, a centralized platform can monitor both physical devices, like badge readers, and digital systems, such as network access logs, allowing security engineers to correlate events and respond to potential threats faster.
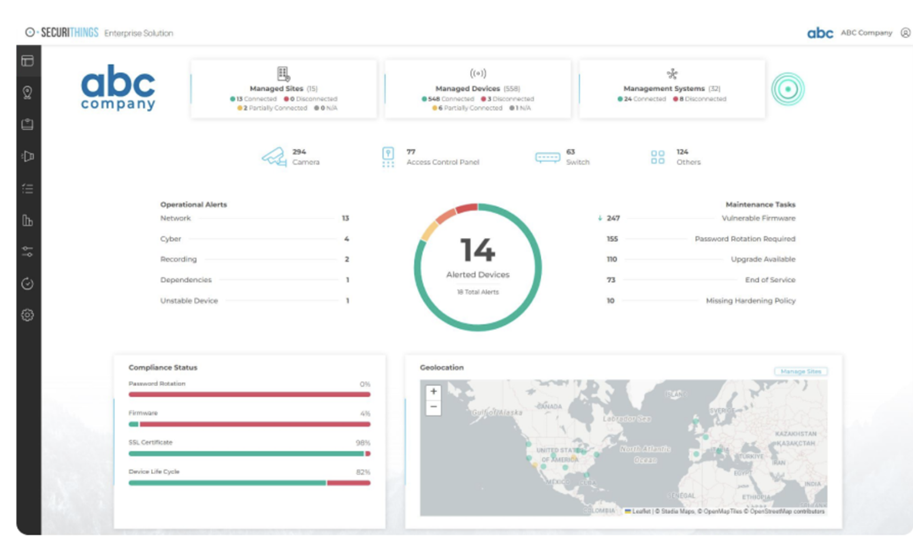
An example of a centralized platform for monitoring devices (Source)
Vulnerability assessments
Vulnerability assessments offer a systematic method to evaluate physical security systems, prioritize risks, and implement remediation strategies before attackers can exploit them. For example, an unpatched access control system could allow unauthorized entry to sensitive areas, while an outdated IoT device could serve as a pivot point for lateral movement within the hospital network.
Security engineers must adopt proactive measures to uncover vulnerabilities, prioritize remediation efforts, and ensure alignment with hospital operations and regulatory requirements. Security engineers should consider the following recommendations:
- Conduct regular assessments: Schedule routine vulnerability assessments for all critical systems, including IoT devices, physical security devices, and IT infrastructure. Ensure that these assessments account for newly deployed technologies and evolving threats.
- Utilize automated tools: Leverage advanced vulnerability management platforms that integrate AI and machine learning to detect risks in real time. These tools can automate the scanning of devices for unpatched firmware, weak credentials, or misconfigurations, reducing manual effort.
- Prioritize based on risk: Implement a risk-based approach to remediation. Address vulnerabilities with the highest severity and potential impact first, such as those affecting patient safety or critical operations.
- Incorporate penetration testing: Complement vulnerability assessments with periodic penetration testing to simulate real-world attack scenarios. This provides insights into how vulnerabilities might be exploited and validates the effectiveness of current security measures.
- Maintain comprehensive documentation: Keep detailed records of vulnerabilities, remediation efforts, and system improvements. These documents are essential for internal tracking and regulatory compliance, demonstrating the hospital’s commitment to robust security practices.
- Integrate findings with incident response plans: Use the results of assessments to refine and update incident response strategies. Ensure that all identified vulnerabilities are addressed in recovery plans to minimize impact during potential security incidents.
- Coordinate with multidisciplinary teams: Collaborate with IT, facilities management, and clinical staff to be sure that security measures are implemented without disrupting hospital operations or patient care.
- Monitor and reassess: Continuously monitor systems for emerging threats and reassess vulnerabilities in response to significant changes, such as the introduction of new devices, software updates, or shifting regulatory requirements.
Compliance reporting
Compliance reporting is a critical element of hospital security, ensuring adherence to regulatory requirements such as the Health Insurance Portability and Accountability Act (HIPAA) and other industry standards.
Compliance reporting is particularly important in addressing risks associated with interconnected systems. For instance, a breach involving an IP camera could expose protected health information (PHI) if the device is not properly segmented or monitored. Regular reporting allows security engineers to demonstrate proactive risk mitigation and adherence to compliance standards.
It is very important for security engineers to consider the following recommendations:
- Automate reporting processes: Use security management software to generate automated compliance reports, reducing manual effort and ensuring consistency. These tools can provide up-to-date information on device statuses, access logs, and remediation activities.
- Maintain comprehensive asset inventories: Keep detailed records of all physical and IoT devices, including their locations, firmware versions, and access controls.
- Document incident responses: Record all security incidents, including their detection, response, and resolution. Include timelines, involved systems, and lessons learned to showcase an organized and accountable approach to incident management.
- Perform regular audits: Schedule periodic internal audits to identify compliance gaps and ensure adherence to regulatory requirements. Use these audits to validate the effectiveness of existing security measures and update reporting processes as necessary.
- Collaborate with legal and regulatory teams: Work closely with compliance officers and legal advisors to ensure reports align with applicable laws and standards. This collaboration helps security engineers stay informed about regulatory updates and incorporate them into their practices.
- Include physical and cybersecurity metrics: Integrate data from both physical and digital security systems into reports. For example, access control logs from badge readers can be combined with network activity data to provide a holistic view of security operations.
- Enable real-time monitoring and alerts: Implement tools that offer real-time visibility into compliance-related activities. These can include alerts for unpatched devices, unauthorized access attempts, or anomalies in access logs, ensuring timely reporting and remediation.
Integrated security operations
Integrated security operations involve combining physical and cybersecurity efforts into a unified approach to protect hospital systems, devices, and data. This integration is particularly critical in healthcare environments where interconnected systems, such as IoT devices and access controls, blur the line between physical and cyber risks.
Security engineers should consider the following recommendations:
- Implement centralized management tools: Use platforms that integrate data from physical security systems (e.g., cameras, access controls) and cybersecurity tools (e.g., firewalls, SIEM systems). This allows for a single-pane-of-glass view of all security operations.
- Adopt real-time monitoring and alerts: Configure integrated systems to provide real-time alerts for both physical and digital threats. For instance, an unauthorized access attempt at a badge reader should trigger alerts across both physical and cyber systems.
- Conduct coordinated vulnerability assessments: Assess both physical and digital assets during vulnerability assessments. Identify risks that span both domains, such as unsecured IoT devices connected to physical security systems.
- Establish unified incident response protocols: Create incident response plans that address both physical breaches (e.g., unauthorized door entry) and their potential cyber implications (e.g., network infiltration through compromised devices). Train teams to collaborate during cross-domain incidents.
- Enable data correlation and analytics: Leverage tools that correlate data from access logs, video feeds, and network activity. This can help detect patterns that indicate coordinated attacks or insider threats.
- Conduct regular drills and simulations: Run tabletop exercises that simulate integrated threats, such as a phishing attack combined with physical entry attempts. This ensures that teams are prepared to respond cohesively.
- Ensure cross-team communication: Facilitate regular meetings between physical security, cybersecurity, and facilities management teams. This fosters collaboration and ensures all teams are aware of emerging risks and coordinated strategies.
Conclusion
Hospital security is a multifaceted challenge that requires a holistic approach to protect patients, staff, and critical systems. From physical access controls and IoT device security to integrated security operations and compliance reporting, each element plays a vital role in building a robust security framework. Security engineers must adopt advanced tools and practices, such as vulnerability assessments, network segmentation, and physical security management software, to address the unique risks posed by interconnected healthcare environments.
By aligning physical and cybersecurity efforts, automating key processes, and maintaining regulatory compliance, hospitals can safeguard their operations while prioritizing patient safety and trust. A proactive and integrated approach ensures resilience against evolving threats, enabling hospitals to deliver uninterrupted, high-quality care in a secure environment.


