HIPAA Physical Security Best Practices
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule addresses the protection of electronic Personal Health Information (ePHI).
ePHI is primarily accessed and processed on laptops and computer workstations. However, ePHI doesn’t just live inside computers. In a broader sense, ePHI is also present wherever a person’s information is linked to digital data about a health condition— for example, in facilities where health insurance is processed, doctors’ offices where patients receive treatment, and laboratories that test samples for diseases.
At one time, physical security for ePHI meant controlling access to sensitive paperwork. Today, the physical security team must protect both physical facilities and computing devices, as well as Internet of Things (IoT) devices and their networks.
HIPAA physical security controls are outlined in the Security Rule under 45 CFR § 164.310, Physical Safeguards. These requirements include:
- Access control and validation
- A security plan
- Contingency operations
- Documentation of changes and repairs.
They also involve physical security around workstations to protect the ePHI stored and processed there, as well as the electronic media that could host protected health information.
Controls fall under addressable and required categories. Addressable does not mean optional. You must implement the addressable controls if they are reasonable and appropriate for your organization. If a control does not make sense, you must document why and implement an equivalent alternative measure if necessary.
This article reviews the physical security controls of the HIPAA Security Rule and develops a methodical approach to assessing the physical environment for compliance.
Monitor the health of physical security devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports



Summary of key HIPAA physical security concepts
| Concept | Description |
|---|---|
| HIPAA Security Rule | Addresses the protection of electronic Personal Health Information (ePHI). Review the requirements to see how they apply to your healthcare operations. |
| Identify and assess applicable areas and networked medical and access devices. | Identify all areas, devices, and media that might contain or access ePHI. For example:
|
| Implement facility security controls. | Use networked and IoT access control systems to implement credential, visitor, and emergency access management for facilities that contain ePHI. |
| Implement workstation security controls. | Assess stationary and mobile workstations to limit unauthorized viewing and access of ePHI on screens. |
| Implement device and media controls. | Assess handling and transport control of data storage devices and media, such as USB drives and laptop computers |
| Identify gaps and remediation plans. | The HIPAA physical security controls are never optional, and all control gaps should be monitored, identified, and remedied, or alternatives implemented. |
| Document outcomes and reassessment criteria. | Document assessment approaches and outcomes, and review them with your organization’s HIPAA leader. Describe any circumstances that would require a new assessment. |
Identify and assess applicable areas and networked medical and access devices
First, scope the facility and determine all areas, devices, and media that might contain or access ePHI. Document which HIPAA requirements apply to each area and device type.
A physical scope inventory for a healthcare facility primarily includes
- Reception
- Clinical treatment rooms
- Medical record storage area
- Nurse or provider workstations.
ePHI could also live in less obvious areas, such as administrative offices, telehealth consultation rooms, and mobile workstations in treatment rooms. You should document the manual and electronic controls that separate public areas from areas where ePHI is expected to reside.
Networked devices used for treatment, such as smart infusion pumps and networked diagnostic equipment, also store or transmit ePHI and require physical protection. When cataloging these areas and devices, note who should have authorized access and what security controls are currently in place. This inventory forms the foundation of your assessment plan.
IoT and networked medical devices deserve extra diligence on the part of the assessor, as they are a relatively new—and often insecure—addition in clinical settings.
Assessment plan
A structured assessment plan guides the evaluation of all physical security controls. Before beginning the assessment, draft the plan scope and consider objectives for the areas and device types to be evaluated. For instance, the objectives for the waiting area would include limiting physical access and ensuring that badge readers log access attempts.
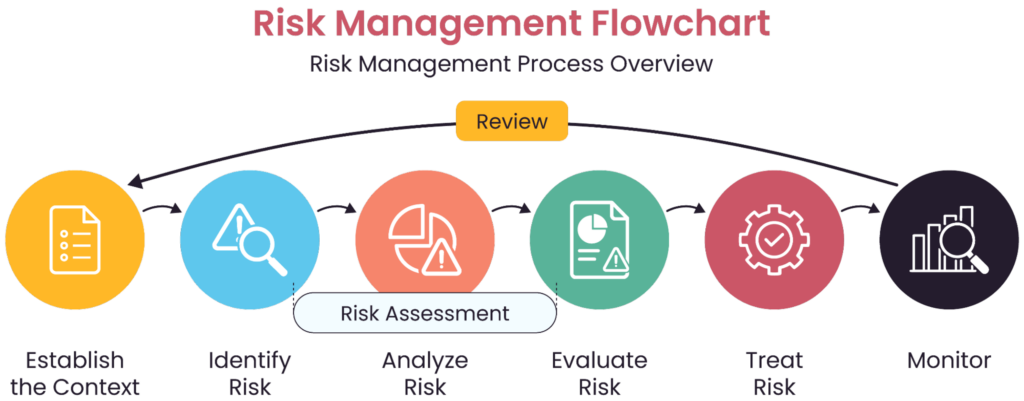
An example of a risk assessment flow (source)
For each area and its assessment objective, define an evaluation method that provides objective evidence of the control being met.
For example, employees may report that they lock workstations when they move away. However, they may not do so every time.
Comparing the camera or badge records of movement with the computer system event logs is stronger evidence of whether the procedure is followed every time.
Run objective tests and observe system logs for evidence regarding access and environmental controls. That way, when incidents occur—for instance, a room that overheats or a water leak in a monitored area—you will already have records that show the date and time the event occurred, as well as the monitoring records that triggered an alert.
Implement facility security controls
Networked and IoT access control systems are best suited for implementing facility security controls. They link physical access events to digital records, providing better logging and control than older code and key systems. Proper user information and time synchronization across physical and digital systems gives the security team a coherent trail of physical and digital access.
However, HIPAA compliance is not out of reach for smaller facilities with manual access controls. Comparing your control records will take longer, for instance, comparing visitor logs and video monitoring, or reviewing worker schedules with ePHI system access records. However, these are still relevant activities that you can log and use as evidence of control review.
Some things to consider:
Credential management
Credential management systems include electronic badge readers, smart card systems, or biometric access controls. They may also interact with IoT-enabled locks and door control systems, security cameras, and video monitoring systems.
Systems should automatically revoke all physical access when employment is terminated, without requiring multiple manual processes across different departments. Test whether access permissions accurately reflect current roles, rather than accumulating over time—a common compliance gap in many organizations.
Visitor management
Visitor management should combine physical barriers, visual indicators, and access control technology that limits visitor access. Determine if the signage is appropriate and directs visitors away from areas where ePHI can be seen or heard. Consider adding signage, such as “Wait here for the receptionist,” and keeping appointment sign-in sheets behind the receptionist counters. Visitor tracking logs, clearly marked visitor badges with restricted access, and escort policies are all essential requirements.
Since visitors in a treatment setting may also be persons disclosing their ePHI, all visitor information must also be protected. Examine how visitor management systems protect collections of identifying information. Visitor management systems that indicate treatment should be placed under the same controls as clinical systems.
Emergency access management
The HIPAA Security Rule permits emergency access protocols under Contingency Operations (§ 164.310(a)(2)(i)). When evaluating emergency access controls, focus on documentation and practical implementation.
Verify that emergency access procedures are automatically documented and that systems include mandatory post-event justification before continuing normal operations. This retrospective documentation prevents emergency procedures from becoming routine workarounds to standard security controls.
Test regularly under realistic conditions. For example, schedule regular drills that simulate different emergency scenarios to verify that staff know how to maintain security during emergencies. Record observations from these tests as evidence of ongoing diligence. While HIPAA does not mandate a specific timeframe for reassessment or testing, good practice is to reassess at least once a year and more frequently for critical systems.
Workstation security controls
Healthcare environments feature increasingly mobile workstations and flexible viewing arrangements that complicate traditional screen protection approaches. When assessing workstation placement, look beyond screen positioning to evaluate comprehensive visual privacy measures. Workstations in high-traffic areas require more protection than those in private offices; your assessment should take these environmental differences into account.
Assess how easily unauthorized individuals could view ePHI on screens from public or semi-public areas. Stand in patient waiting areas, hallways, and other public spaces to verify screen visibility. A physical privacy screen and proper monitor positioning reduce the risk of data being viewed in public areas.
You should also review how often workstation users leave the area without logging out or locking their computers. All systems should have a set screen lock or login timeout based on their usage patterns and the criticality of quick access during a crisis.
As a best practice, require a physical factor, like a smart card reader, at login. Employees must remove their ID badge from the reader when they leave the workstation, as it is needed to access other restricted areas. This activates the workstation screen lock automatically and protects access to sensitive information.
Implement device and media controls
Many organizations have gaps in tracking shared mobile media and devices on the go. Their relocation may become unintentionally permanent. Security teams should maintain documentation of who is responsible for all mobile media and devices at any given time.
Accountability for devices and media with ePHI
When assessing accountability controls, verify inventory management processes for all devices and media containing ePHI. Practical implementations maintain comprehensive inventories and perform regular reconciliations to detect missing items before they result in breaches. Test whether newly acquired devices are promptly added to inventory and whether decommissioned devices are adequately documented and removed. Tracking systems for device and media movement should report the current location and the entire chain of custody.
Devices or media with ePHI but without individual assignment should never be left unsupervised or unaccounted for. There should be a formal transfer of responsibility when items change hands, such as a signed physical log of the hand-off.
Media disposal or reuse
Media disposal or reuse procedures must ensure that ePHI is rendered permanently inaccessible at the end of its lifecycle. The US National Institute of Standards and Technology (NIST) offers information and guidance on proper sanitization of electronic media in Special Publication 800-88.
Test sanitization methods
Test the effectiveness of physical destruction or data sanitization methods for different media types. For physical destruction, verify that the resulting material cannot be reassembled or recovered using commonly available tools or techniques. For electronic sanitization, use forensic tools to attempt data recovery on sanitized media—if your assessment team can retrieve data, so can potential attackers.
Commercial tools like Wondershare Recoverit and DiskDrill Data Recovery have intuitive user interfaces and are highly recommended by professional reviewers. Whichever tool you choose, ensure that no sensitive data is sent or stored outside your network during the recovery process.
Track media marked for disposal
Organizations commonly have delays between when media is removed from service and when it is destroyed. Maintain chain of custody throughout the disposal process. Verify documentation of completed disposal actions, including specific information about what was disposed of, when, how, and by whom. Test whether the documentation process is consistently followed, especially for routine disposal activities that may become less rigorous over time.
Assess media reuse procedures
Organizations must remove ePHI before media reuse to prevent unauthorized disclosure. When assessing media re-use procedures, evaluate
- Technical effectiveness of data removal methods
- Practical implementation of verification processes.
Remember that standard file deletion or quick formatting doesn’t completely remove data—it only removes the reference to the data, leaving the content potentially recoverable. Test data wiping procedures using actual media scheduled for reuse. For electronic media, forensic tools are used to attempt to recover data that has been removed.
Each sanitized device should have records showing the method used, when it was performed, the verification results, and who performed and verified the procedure. Test whether the organization consistently maintains this documentation and whether it is readily available during audits.
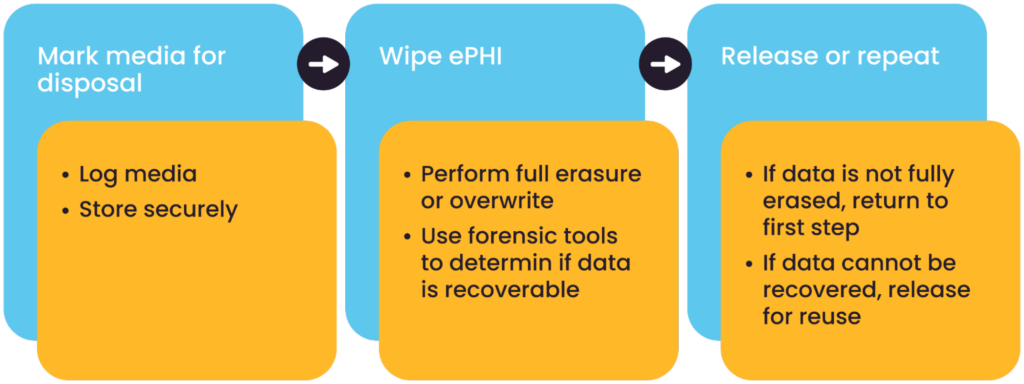
Media disposal and reuse controls
Identify gaps and remediation plans
After completing your assessment, identify and prioritize gaps in your physical security controls. Categorize gaps based on:
- Regulatory status
- Risk level
- Implementation complexity
- Resource requirements
- Impact on clinical operations.
Risk level assessment should consider the likelihood and potential impact of security incidents resulting from identified gaps. Critical gaps typically involve required specifications with a high likelihood of exploitation and severe consequences. Low-risk gaps involve addressable specifications with minimal exploitation potential and limited impact.
Remediation planning
Develop a detailed remediation plan for each identified gap, including:
- The gap description
- Proposed solution
- Required resources, including technical expertise, equipment, software, staff time, and other information necessary to plan and budget remediation.
- Implementation timeline
- Responsible parties
- Success criteria to prevent scope creep during implementation, while ensuring remediation efforts fully address identified gaps.
- Post-implementation validation methodology.
Prioritize remediation efforts based on risk level, focusing first on gaps in required specifications and those presenting the highest risk to ePHI security.
Compensating controls
Identify appropriate compensating controls for gaps that cannot be immediately remediated. Alternative measures should address the same security objectives as the primary controls, but use different methods or technologies. For example, if continuous video monitoring isn’t feasible in a particular location, a compensating control might combine periodic security rounds with enhanced access controls and intrusion detection systems.
Document why primary controls cannot be implemented, whether due to technical limitations, resource constraints, operational requirements, or other factors.
Ongoing monitoring
Define manual and automatic processes for continuously monitoring physical security controls between formal assessments. Continuous monitoring helps identify new and recurring issues before they become compliance problems or security incidents.
Implement security management software to support the logging and monitoring of your electronic security devices. It can collate logs and provide holistic summaries and visuals to measure compliance from a single dashboard.
Beyond monitoring physical spaces and access events, organizations should also monitor the health, security, and compliance status of physical security systems, such as surveillance cameras, access control systems, and alarms. Proactive monitoring platforms can detect device failures, outdated firmware, misconfigurations, and cyber vulnerabilities that could compromise security. Identifying issues before they affect operations, these tools help ensure that security infrastructure remains functional, up to date, and compliant with regulations like HIPAA.
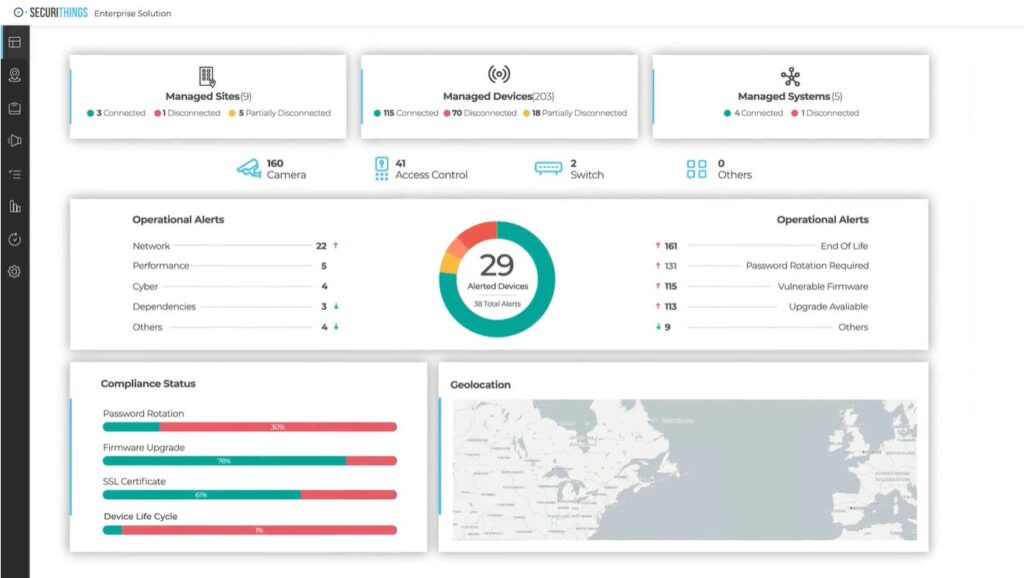
Dashboard example showing real-time monitoring of physical security systems, including device connectivity, operational alerts, and compliance indicators (Source)
Document outcomes and reassessment criteria
Comprehensive documentation serves as evidence of your diligence during audits and provides a roadmap for ongoing security improvements. It should include:
- The structured approach used to evaluate physical security controls, including information about assessment teams, evaluation tools and techniques, testing procedures, and classification criteria for findings.
- Gap analysis connecting findings to specific HIPAA requirements, with risk assessments for each gap.
- Evidence of testing and validation, like test results, audit logs, and configuration screenshots, that proves that security controls are functioning as intended.
Like other security-related information, this documentation should be treated as sensitive. For you, the collection is a guide for remediation. For an intruder, this documentation maps the weakest points in your protection. Handle this compilation with the same care as the data it protects.
Reassessment triggers
Establish clear criteria that would trigger reassessment of physical security controls. Reassessment triggers can be significant changes to facility layout or use, deployment of new IoT technologies, or changes to regulatory requirements. Additionally, security incidents or breaches should always trigger reassessments.
Last thoughts
Although protecting ePHI sounds like it is solely the domain of computer security, physical security teams are also impacted by HIPAA Security Rule requirements. The HIPAA requirements relate to controls that the physical security team is already responsible for, but HIPAA expands the scope of these requirements to include access control and media disposal. Assessments require documentation, and evaluations require supporting evidence.
Organizations may find these additional tasks and more stringent requirements taxing. However, the risks of HIPAA violation penalties and potential criminal prosecution are significant and tangible. Implementing the HIPAA security rule is the duty of all healthcare providers and data processors to the population that trusts them to protect their health and privacy.