IoT vulnerabilities in healthcare: Tutorial & Best Practices
The widespread adoption of IoT devices in healthcare has transformed hospital operations by improving patient care, streamlining workflows, and enhancing security measures. These devices are used across various applications in healthcare, ranging from clinical tools like patient monitors and imaging systems to operational technologies such as smart HVAC systems and wearable devices. They also include physical security systems like IP cameras and badge readers.
However, this interconnected system also introduces significant vulnerabilities, such as reused passwords, unpatched firmware, and a lack of robust security protocols. These risks can endanger patient safety, data integrity, and operational continuity.
This article explores the vulnerabilities affecting IoT devices in healthcare, categorizing device types, identifying common threats, and presenting actionable solutions. Security engineers will find insights into advanced techniques, such as physical security management software and centralized monitoring platforms, to mitigate risks and ensure compliance.
Summary of key concepts related to IoT vulnerabilities in healthcare
| Concept | Description |
|---|---|
| Types of IoT devices in healthcare | IoT devices can be broken down into categories that include medical devices (such as infusion pumps and imaging systems), wearables (remote patient monitoring tools), operational tools (like smart lighting and HVAC systems), and physical security devices (IP cameras, badge readers, and so on). |
| Vulnerability categories in IoT devices | Vulnerabilities include reused passwords, unpatched operating systems, exposure to untracked common vulnerabilities and exposures (CVEs), a lack of network segmentation, and insecure data transmission. These risks can compromise patient data, operational integrity, and hospital networks. |
| Practical illustrations of IoT vulnerabilities | Real-world scenarios and examples can illustrate the dangers in this area, including ransomware attacks on medical IoT devices and breaches of IP cameras. |
| Techniques and measures to protect against IoT vulnerabilities | Important security practices include enforcing strong device authentication, automating firmware updates, implementing network segmentation, and integrating centralized monitoring tools for real-time oversight. |
| Physical security device management solutions | Advanced platforms that go beyond traditional video management systems (VMS) to offer centralized monitoring, automated credential rotation, compliance reporting, and real-time analytics for physical security devices like IP cameras and access control systems. |
| Best practices for securing healthcare IoT | Best practices include adopting zero trust principles, enhancing device visibility and inventory, implementing end-to-end encryption, leveraging AI and anomaly detection, educating and training staff, and integrating security tools. |
Types of IoT devices in healthcare
As the healthcare industry evolves, IoT devices are increasingly enhancing clinical and operational outcomes. These devices range from life-saving medical equipment to essential operational tools. Each type serves a distinct purpose, yet all share a common vulnerability: They are interconnected and susceptible to cyber threats. Security engineers should understand the specific roles and risks of these devices and design effective security protocols.
The table below categorizes the common types of IoT devices used in healthcare, their applications, and associated risks.
| Type | Examples | Applications | Associated risks |
|---|---|---|---|
| Medical devices | Infusion pumps, ventilators, dialysis machines | Delivering medications, supporting life functions | Firmware flaws, weak encryption, unauthorized access |
| Wearable devices | Heart rate monitors, glucose trackers, smartwatches | Monitoring chronic conditions, empowering patient care | Data leaks, inadequate authentication mechanisms |
| Operational tools | Smart lighting, IoT-enabled HVAC systems | Enhancing energy efficiency and patient comfort | Backdoor access, weak network defenses |
| Physical security devices | Surveillance cameras, biometric access systems | Protecting sensitive areas, controlling access | Credential misuse, network intrusion opportunities |
| Telemedicine devices | IoT-enabled video conferencing tools, diagnostic kits | Facilitating remote consultations and diagnoses | Data interception, vulnerabilities in remote access software |
| Smart pharmacy systems | Automated dispensing units, inventory management systems | Managing medication distribution and tracking inventory in real time | Unauthorized access, supply chain tracking disruptions |
| Laboratory IoT devices | IoT-enabled centrifuges, smart refrigerators | Automating laboratory workflows, ensuring proper environmental conditions | Malfunctioning sensors, tampering with temperature control data |
| Robotic surgical systems | IoT-integrated robotic surgery tools | Performing minimally invasive surgeries with precision | Device hacking, operational errors, patient harm |
| Emergency response systems | IoT-connected ambulances, smart defibrillators | Enhancing emergency response times, improving outcomes during critical events | GPS spoofing, unauthorized control of critical systems |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Vulnerability categories in IoT devices
IoT devices in healthcare face vulnerabilities that span multiple categories, each with distinct characteristics and challenges.
The following table provides a structured overview of the critical vulnerabilities associated with IoT devices in healthcare environments. It categorizes vulnerabilities into seven main distinct areas, detailing the nature of each vulnerability, real-world examples, and potential impacts.
| Category | Description | Example | Impact |
|---|---|---|---|
| Device-level vulnerabilities | Weaknesses in device design or configuration, including outdated firmware and default passwords | An infusion pump using default credentials, which can be easily accessed | Device malfunctions, patient safety risks, unauthorized control |
| Network-level vulnerabilities | Insecure network configurations, lack of encryption, insufficient segmentation | A compromised IP camera that allows attackers to move laterally across the network | Widespread data breaches, operational disruptions, regulatory violations |
| Application-level vulnerabilities | Weak APIs, flawed web interfaces, poor application logic | A vulnerable API in a telemedicine application that can be exploited to access sensitive data | Unauthorized data access, compromise of critical healthcare applications |
| Data-level vulnerabilities | Poor data encryption, improper handling of sensitive data | Unencrypted health data transmitted from wearable devices intercepted during transit | Data breaches, patient confidentiality violations, compliance failures |
| Operational vulnerabilities | Improper device maintenance, lack of monitoring, operational dependencies | A laboratory centrifuge’s outdated firmware exploited for network entry | Operational downtime, safety hazards, data integrity issues |
| Supply chain vulnerabilities | Risks from unverified vendors and compromised components | IoT devices with pre-installed malware from unvetted suppliers | Compromised systems before deployment that create systemic vulnerabilities |
| Human factors | Misconfigurations, unintentional errors, insufficient training | Incorrect network permissions, allowing unauthorized device access | Security bypasses that nullify technical safeguards |
Security engineers should address these categories and build a multi-layered defense strategy to protect healthcare IoT systems.
Practical illustrations of IoT vulnerabilities
The best way to really understand IoT vulnerabilities is by looking at real-world examples. The following examples highlight how these vulnerabilities manifest in healthcare environments, emphasizing their impacts and the need for strong security measures.
Imaging system ransomware attacks
A ransomware attack on imaging systems, for example, showcases the devastating consequences of cybersecurity breaches. In these incidents, attackers encrypt data on MRI and CT scanners, rendering them inoperable until a ransom is paid. This disruption delays essential diagnostic services, impacts patient care, and results in significant financial losses.
To mitigate such risks, healthcare organizations can implement advanced backup solutions, segment their networks to isolate vulnerable devices, and deploy anti-ransomware protections to safeguard critical systems.
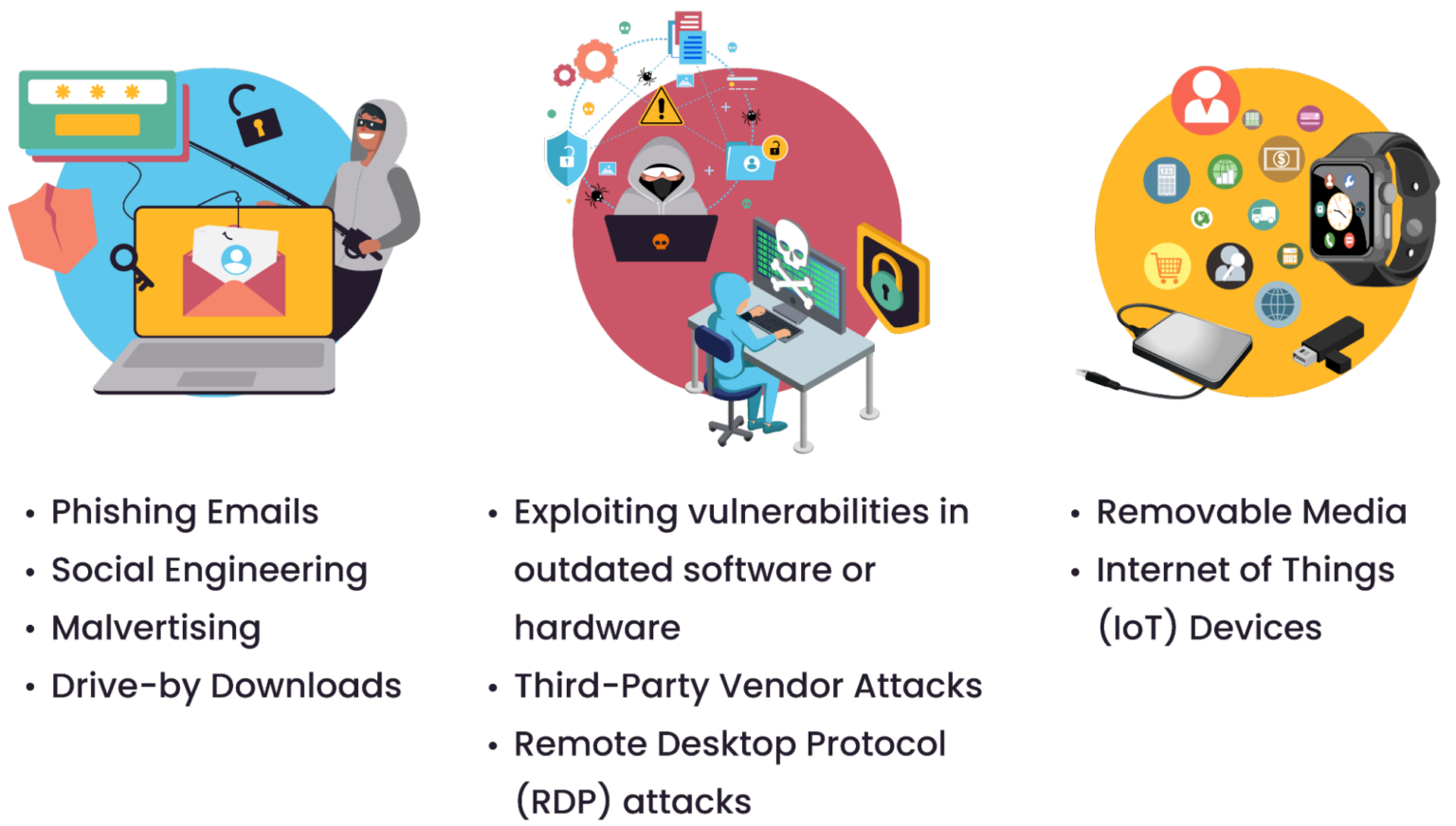
An illustration of how ransomware enters healthcare systems (source)
The figure above illustrates the primary methods through which ransomware infiltrates healthcare systems, highlighting various vulnerabilities and attack vectors that cybercriminals exploit. It showcases common entry points such as phishing emails, social engineering tactics, malvertising, and drive-by downloads. Additionally, the figure emphasizes risks posed by outdated software or hardware, third-party vendor attacks, and unsecured Remote Desktop Protocol (RDP) connections. It also draws attention to the dangers associated with removable media and vulnerable Internet of Things (IoT) devices, which are increasingly prevalent in healthcare settings.
IP camera exploits
Another example involves IP cameras being exploited to gain unauthorized access to a hospital’s network. Using weak passwords, attackers can breach physical security systems, move laterally across the network, and exfiltrate sensitive patient data. For instance, attackers may utilize publicly available tools to scan for IoT devices with default credentials, leading to operational downtime, legal ramifications, and reputational harm. Beyond data theft, these breaches often disable critical surveillance systems, exposing physical vulnerabilities.
Mitigation strategies include enforcing strong and unique passwords, implementing network segmentation, and using secure remote access methods such as VPNs or secure tunnels. Additionally, auditing access logs and ensuring firmware supports automated patching further reduce these risks.
IP cameras are also a common target for attackers exploiting weak passwords to gain unauthorized network access. For example, CVE-2021-32934 highlights a vulnerability in certain IP cameras that allows attackers to bypass authentication and access device settings. Understanding these risks helps organizations identify vulnerable devices and implement measures such as strong passwords, network segmentation, and regular firmware updates to mitigate threats effectively.
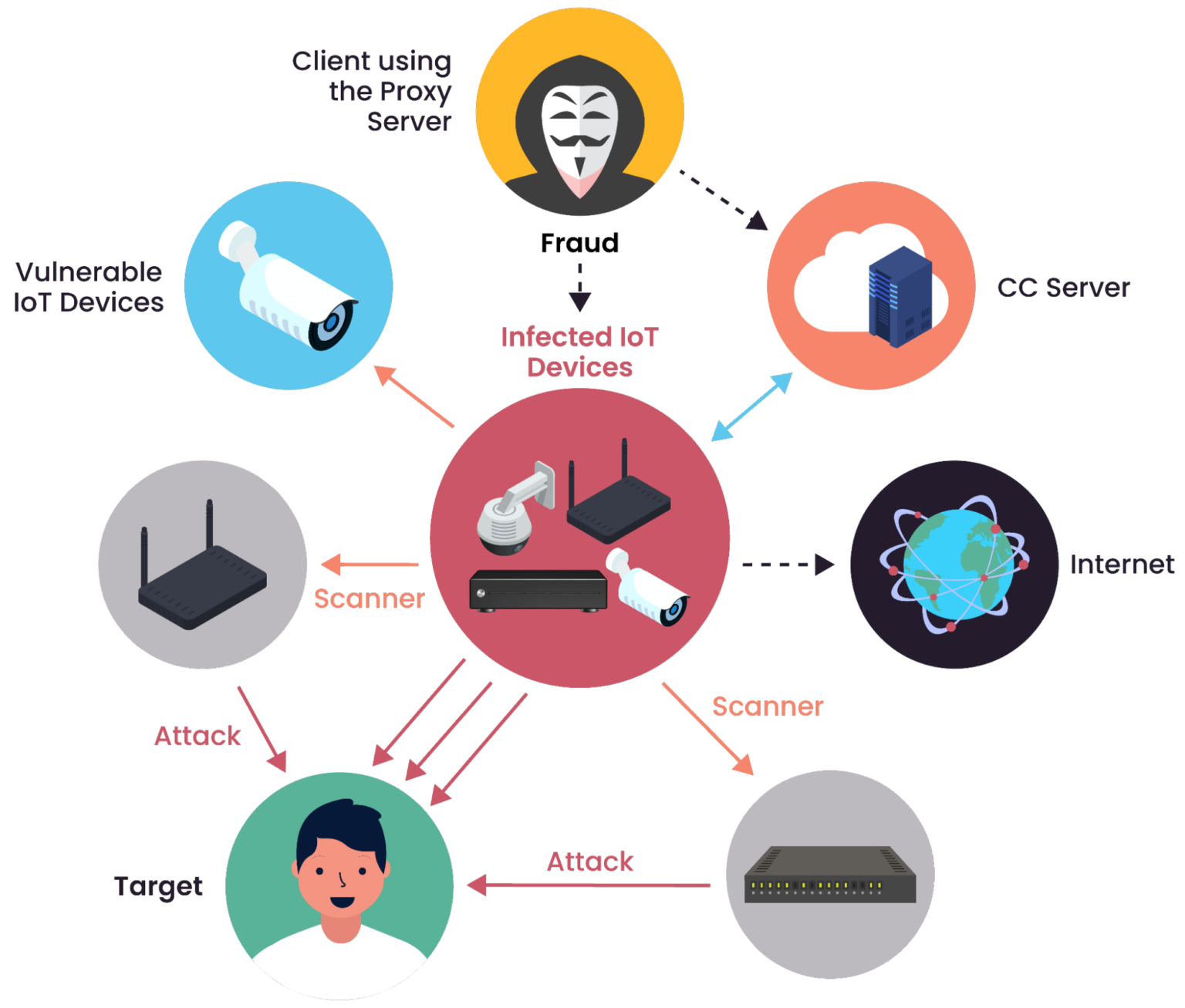
An example of an IP camera exploit that leads to a network breach (Source)
This diagram illustrates the process of an IP camera exploit that leads to a network breach. The flow begins with an attacker using a proxy server to scan for vulnerable IoT devices. Once a device is compromised, it becomes part of a botnet of infected IoT devices, managed by a command-and-control (CC) server. From there, attackers can use these infected devices to launch targeted attacks on a victim, including data exfiltration or further lateral movement within the network. This highlights the critical importance of securing IoT devices to prevent such exploits.
Wearable device risks
IoT vulnerabilities also extend to wearable devices, such as glucose trackers that transmit unencrypted health data. During wireless transmission, attackers can intercept sensitive information, leading to potential HIPAA violations and a loss of patient trust. Employing end-to-end encryption and educating device vendors on secure design practices are effective measures to prevent such breaches.

An illustration of medical data transmission from wearable health devices (Source)
The figure above illustrates the process of medical data transmission in a healthcare IoT system, highlighting both the functional flow and potential vulnerabilities. Data from wearable health devices is transmitted through access points to a cloud network for processing and storage on servers. This data is then made accessible at diagnostic points for analysis and decision-making. However, the diagram also depicts potential security risks, with attackers targeting the transmission pathways, access points, or storage servers to compromise sensitive medical data.
Outdated medical device firmware
Outdated firmware in critical medical devices poses another significant risk. For example, vulnerabilities in infusion pumps may be exploited by attackers to alter dosage settings remotely, directly endangering patient safety and exposing the healthcare provider to legal liabilities. Establishing a routine firmware update process and monitoring devices for unusual activity are important steps in mitigating these threats.
Supply chain issues
Supply chain compromises further demonstrate how unverified IoT devices can act as backdoors for attackers. Devices preinstalled with malware can compromise an entire network before being fully operational. Rigorous vendor assessments, mandatory security certifications, and secure pre-deployment testing are essential to prevent such scenarios.
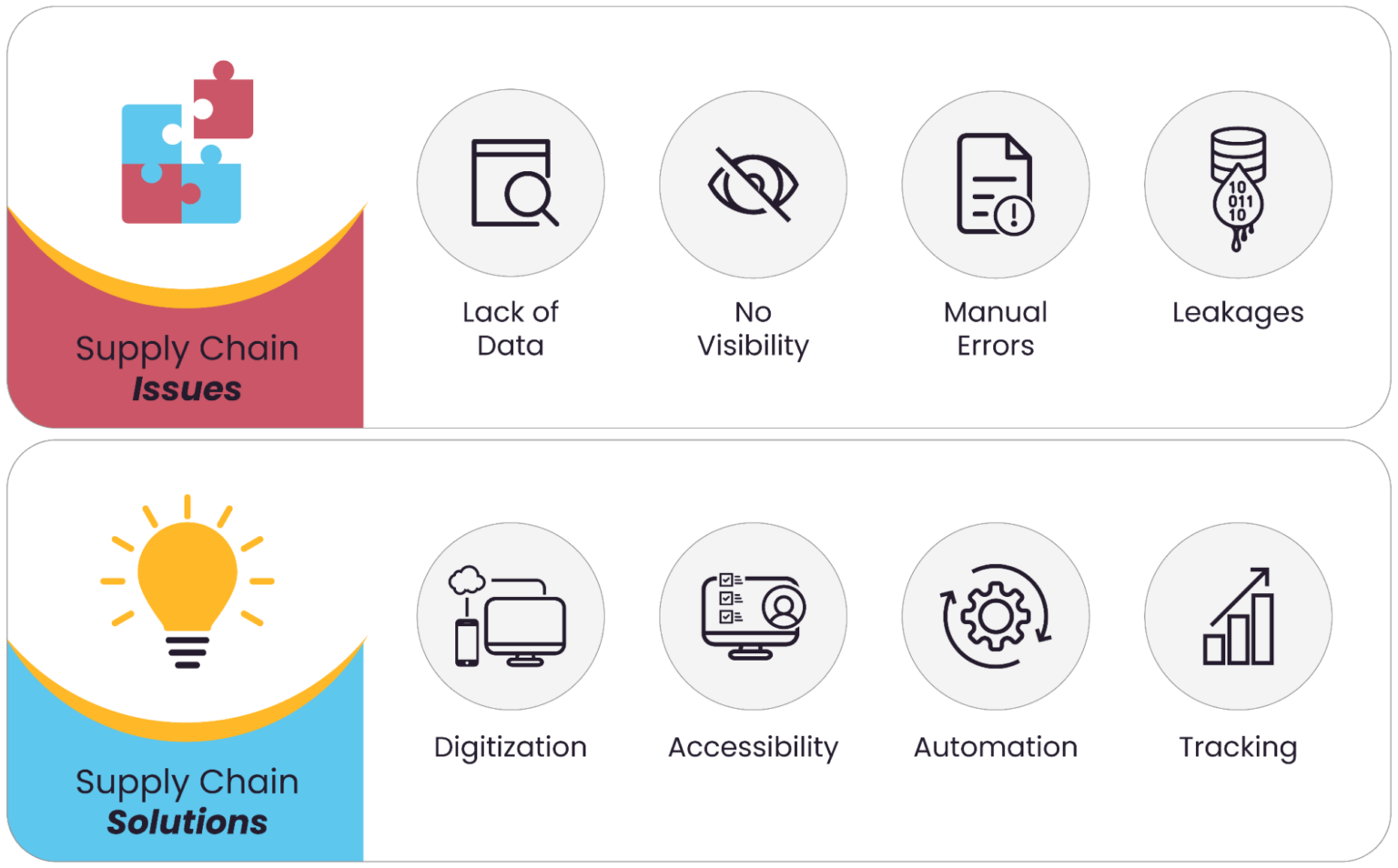
An illustration of supply chain issues and corresponding solutions (source)
The figure above highlights common supply chain issues and their corresponding solutions. The top section identifies key challenges in supply chain management that lead to inefficiencies and potential losses. The bottom section proposes solutions to address these challenges. These solutions aim to streamline operations, reduce human errors, and improve overall visibility and control within the supply chain.
Compromised robotic surgery systems
These systems illustrate the potential for attackers to disrupt critical medical procedures. By remotely accessing them, attackers can cause delays, jeopardize patient outcomes, and erode trust in advanced medical technologies. Enforcing multi-factor authentication, real-time system access monitoring, and isolating critical systems from external networks are key strategies to ensure these devices remain secure.
Techniques and measures to protect against IoT vulnerabilities and best practices
Implementing robust techniques and measures to safeguard IoT systems can significantly mitigate vulnerabilities and reduce risks.
The following table provides a structured overview of key techniques and measures to protect IoT devices in healthcare. It serves as a practical resource for security engineers, offering insights into implementing a multi-layered defense strategy tailored to the unique challenges of IoT in healthcare.
| Technique | Overview | Implementation | Benefit |
|---|---|---|---|
| Zero trust architecture (ZTA) | Adopt a “never trust, always verify” model to authenticate all access requests. | Deploy micro-segmentation, continuous identity verification, and least privilege principles. | Reduces lateral movement by attackers and limits the impact of breaches |
| IoT device visibility and inventory | Maintain an up-to-date inventory of all IoT devices on the network. | Use automated discovery tools to detect and classify connected devices. | Enables rapid identification of unauthorized or rogue devices |
| End-to-end encryption | Protect data at rest, in transit, and in use through robust encryption standards. | Deploy TLS/SSL for data transmission and AES for storage. | Prevents data interception and ensures compliance with privacy regulations |
| Anomaly detection systems | Leverage AI and machine learning to detect unusual patterns in device behavior. | Integrate anomaly detection tools into SIEM platforms for real-time alerts. | Identifies potential threats before they escalate into full-scale attacks |
| IoT-specific patch management | Develop a comprehensive patch management strategy specific to IoT devices. | Use automated tools to schedule and deploy patches without disrupting operations. | Addresses known vulnerabilities promptly and reduces the attack surface |
| Vendor risk management | Conduct thorough security assessments of IoT vendors and their products. | Require vendors to provide security certifications and software bills of materials (SBOMs). | Ensures that IoT devices meet security benchmarks before integration |
| Physical security controls | Secure physical access to IoT devices to prevent tampering or theft. | Use locked enclosures, video surveillance, and biometric access controls. | Enhances overall device integrity and prevents unauthorized manipulation |
| Cybersecurity training for staff | Educate healthcare staff on IoT-specific risks and security best practices. | Conduct regular workshops, phishing tests, and incident response drills. | Reduces human error and fosters a security-aware culture |
| Network isolation for IoT devices | Isolate IoT devices into separate network segments to contain potential breaches. | Use VLANs, firewalls, and virtual private networks (VPNs) for secure connectivity. | Limits attackers’ ability to access critical systems through IoT entry points |
| Secure API integration | Ensure that APIs used by IoT devices are properly secured. | Use API gateways, token-based authentication, and rate limiting. | Prevents exploitation of APIs as an attack vector |
Physical security device management solutions
In today’s healthcare environments, physical security devices, such as surveillance cameras, access control systems, and alarm systems, form an essential part of healthcare IoT systems. Managing these devices securely requires advanced device management solutions that go beyond traditional tools. This should not be confused with video management systems (VMS), which are also critical for managing and viewing camera feeds. Instead, device management solutions focus on securing and maintaining the underlying hardware and software of physical security devices — enabling centralized monitoring, credential automation, and compliance enforcement.
Such solutions address vulnerabilities in physical security devices by offering robust tools and capabilities in a variety of areas:
- Regular monitoring of device health and performance is essential for maintaining uninterrupted operations. With proactive health analysis, irregularities can be detected early, and failing components can be addressed before they cause disruptions.
- Compliance is another area where these software solutions excel. They simplify the often complex process of regulatory audits by generating real-time compliance reports.
- Automated credential management is another critical aspect, reducing the risks associated with default or weak passwords by enforcing regular password rotations and preventing credential reuse.
- Integrating physical security systems with cybersecurity platforms, such as SIEM tools, provides a unified defense strategy. By combining insights from physical and digital security layers, healthcare organizations gain a comprehensive view of potential threats.
One key approach to managing these systems is leveraging IoT platforms that combine device visibility with advanced analytics. These platforms enable security teams to proactively detect vulnerabilities, automate updates, and respond to emerging threats in real time.
For example, a centralized software platform can monitor all surveillance cameras within a hospital, providing insights into device health, access logs, and potential unauthorized activities. These platforms often integrate seamlessly with existing network infrastructures, offering scalability and ease of use. Advanced features like anomaly detection and predictive maintenance further ensure that devices operate securely and efficiently, minimizing risks to patient safety and data integrity.
The graphic below displays a dashboard from an IoT enterprise management solution, showcasing an overview of connected sites, devices, and systems. It includes operational alerts categorized by network, performance, cybersecurity, and dependencies, as well as a summary of compliance statuses such as password rotations, firmware upgrades, and SSL certificate renewals. The geolocation map indicates device distribution, while the alert metrics highlight critical issues like vulnerable firmware and devices nearing their end of life. This tool helps streamline IoT device monitoring, enhance compliance, and improve security posture across managed systems.
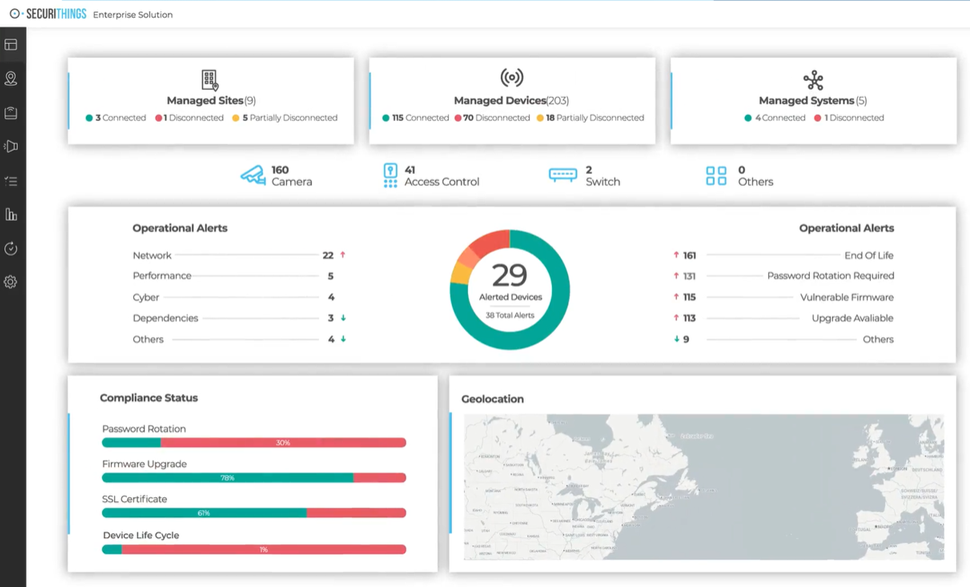
An example of a comprehensive IoT device management dashboard for operational and security insights (source)
Best practices for securing healthcare IoT
This section consolidates the most critical best practices into a streamlined framework, providing actionable strategies for securing IoT systems. By focusing on these recommendations, security engineers can enhance patient safety, protect sensitive data, and build resilience against evolving cyber threats.
Here are some essential best practices to follow for success:
- Adopt zero trust principles: Enforce strict access controls and continuously verify the identity of devices and users.
- Enhance device visibility and inventory: Maintain a comprehensive, real-time inventory of IoT devices to quickly detect and address unauthorized activity.
- Prioritize regular patch management: Address vulnerabilities by promptly updating device firmware and software.
- Implement end-to-end encryption: Safeguard sensitive data during transmission, storage, and processing to prevent unauthorized access.
- Strengthen vendor risk management: Partner with vendors adhering to high security standards and conduct thorough evaluations of their devices.
- Leverage AI and anomaly detection: Use advanced tools to monitor device behavior and identify unusual activity in real time.
- Secure physical devices: Protect IoT devices with tamper-proof enclosures, biometric access, and surveillance systems.
- Educate and train staff: Conduct regular cybersecurity training to minimize human error and foster a culture of security awareness.
- Utilize network segmentation: Isolate IoT devices from critical systems to limit the impact of breaches.
- Integrate security tools: Deploy centralized management platforms to streamline monitoring, compliance reporting, and response to emerging threats.
Conclusion
The integration of IoT in healthcare presents immense opportunities and challenges. Proactively addressing vulnerabilities with robust strategies like zero trust architecture, end-to-end encryption, and staff training ensures data security, patient safety, and operational resilience. A collaborative approach among stakeholders is essential to fully harness the potential of IoT technologies while safeguarding critical assets.
As IoT continues to evolve, healthcare organizations must stay ahead of emerging threats by embracing innovation in security practices. Continuous monitoring and partnerships with trusted vendors will strengthen defenses against cyber risks, ensuring the long-term success and safety of IoT implementations in healthcare.


