IoT Security Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
Internet of Things (IoT) devices are everywhere. IoT devices are essential to various industries, from medicine to agriculture, manufacturing to space exploration, and defense to consumer appliances. Some use IoT technologies to increase profits, while others aim to improve productivity, reduce waste, or enhance convenience and well-being.
Unfortunately, along with the increasing importance of IoT comes an increase in attention from threat actors. IoT devices are often targets of attacks and common entry points for attackers looking to compromise physical security.
In this article, we discuss the challenges of IoT security and explain the best practices engineering teams can follow to keep devices safe.
Summary of key IoT security concepts
The table below summarizes the three high-level IoT security concepts this article will explore.
| Concept | Description |
|---|---|
| IoT security challenges | Resource constraints like limited memory, processing capabilities, power, and connectivity pose challenges to securing IoT devices. Limited user mindshare is also a design constraint. The user application and sensors can also pose liabilities, and their vulnerabilities can compromise the security of IoT devices. |
| IoT security best practices | Many design decisions related to the device, app, and cloud can affect the long-term security of your IoT platform. Following best practices at the development stage can ease life cycle management. Continuous efforts are required throughout the device’s life cycle to ensure comprehensive security. |
| IoT security management software | As your platform scales, it makes sense to invest in security management software to ease the day-to-day monitoring, alerting, compliance reporting, and automation of OTA updates. |
IoT security challenges
On December 10, 2017, the BrickerBot malware was retired after affecting more than 10 million devices globally. This malware attempted to permanently disable (‘brick’) insecure IoT devices, such as routers and cameras. Its modus operandi was:
- Brute force the telnet password
- Run commands using BusyBox to corrupt the storage
- Delete all files
- Disconnect the device from the internet
The BrickerBot malware inflicted a Permanent Denial of Service (PDoS) on the victim’s devices. Here’s the interesting part: BrickerBot’s creator can be considered an anti-hero. He created the malware to prevent Mirai from infecting insecure IoT devices. Mirai, in turn, was another malware that turned insecure IoT devices into bots executing coordinated Distributed Denial of Service (DDoS) attacks. One such attack was on Dyn, a DNS provider that disrupted services such as Twitter, Netflix, and others. Therefore, the creator of BrickerBot believed that removing insecure IoT devices from the internet was preferable to them being infected by Mirai and subsequently used for DDoS attacks against other services.
The fascinating story above provides several insights into the challenges of securing IoT devices. The challenges stem primarily from these devices’ resource constraints but include other limitations, as shown below.
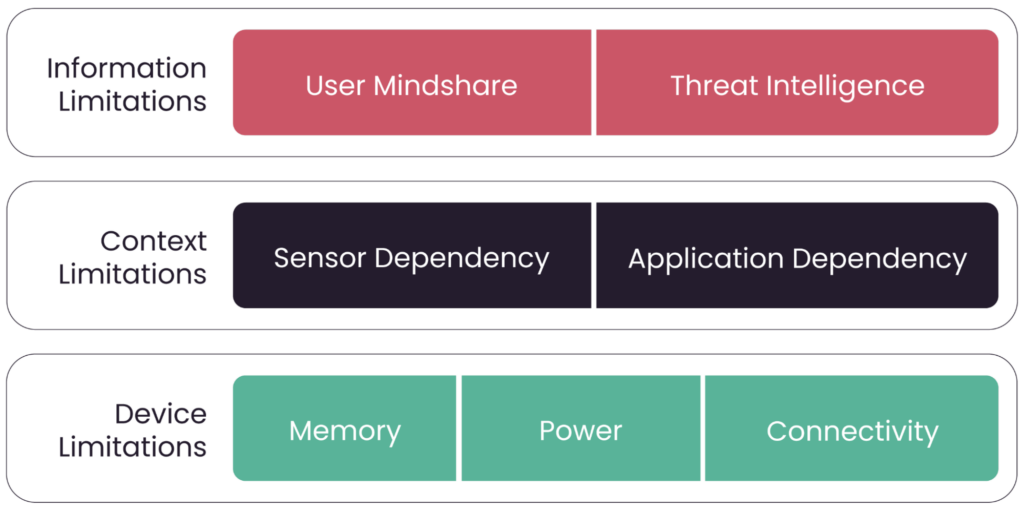
Types of limitations causing security vulnerabilities. (Source)
Let’s examine each one in order of importance.
- Limited memory: A typical laptop or server would recover from such an attack by defaulting to the factory firmware image (if the firmware got corrupted). However, most IoT devices cannot afford enough memory to store factory images.
- Limited threat intelligence: A computer typically has an antivirus program that detects malware and anomalous actions, like rapid file deletion. IoT devices usually lack the memory and processing for such programs to execute.
- Limited user mindshare: Users typically change the default password on their mobile phones or laptops as soon as they set them up. These devices significantly occupy the user’s time and mental space, holding significant personal and sensitive data. IoT devices do not receive the same level of mindshare from users, and users’ perceptions of security with IoT devices are not particularly strong. Several users leave the password settings at the default. If they change the password, it is typically a weak password like ‘abcd1234’ or ‘password’ that can easily be cracked by a brute-force attack. This is the reason why BrickerBot and Mirai were successful. The onus of creating a secure system with minimal user intervention is often on the device manufacturer.
The challenges demonstrated in the BrickerBot attack are just a subset of the broader IoT security challenges teams face. Let’s take a look at four more common IoT-related constraints.
IoT security management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Limited power
Several IoT devices are battery-powered, low-power devices. This makes it easy for an attacker to take down the device without injecting any malware. All they must do is keep pinging the devices to drain the battery. Researchers have found that the key fob of the Tesla Model S is vulnerable to such an attack, where the battery can be rapidly drained by flooding it with authentication requests.
Limited connectivity
Many IoT devices lack internet connectivity and communicate locally using protocols such as Bluetooth, Zigbee, or LoRaWAN. Consequently, automatic firmware updates are not possible for many of them. They either rely on the user to update the firmware or lack the capability altogether. Thus, bugs discovered in connectivity stacks and fixed in subsequent updates often are not passed on to these devices.
Application dependency
For many IoT devices, even if considerable focus is placed on securing the device, the efforts can be compromised if the user interface (mobile app, website, or web app) is not secure enough, especially if the device shares sensitive information with the user interface.
This may appear counterintuitive, considering that apps are more popular than IoT devices, and conventional wisdom would predict that app security practices would be more widespread than those for IoT devices. However, the ground reality is that many IoT companies often only focus on the thing, i.e., the physical device. Very few take the holistic view of IoT, incorporating networking, cloud, and application development within their purview.
Companies often cannot afford to build in-house app teams at the early stages. Application development is often outsourced to third parties, who may prioritize delivering a functional app over ensuring security.
Sensor dependency
By their very nature, IoT devices are dependent on sensors. The most common function of IoT devices is to transmit sensor data to the user interface. Often, these sensors are highly specialized to the application, and the IoT device expects a specific characteristic output from these sensors. Suppose the sensor data is outside these characteristics. In that case, the device may be unable to process it, resulting in a buffer overflow, memory corruption, or getting stuck in a logic loop. The sensors also make way for potential attackers to hijack the device.
Consider the most straightforward example: a smoke detector raises an alarm when smoke levels cross a certain threshold. An attacker seeking to create panic may need to cause the detector to indicate that the smoke level exceeds a certain threshold. Redundant sensors for fault tolerance, detection of faulty sensors, and multiple similar devices communicating with each other—these features are often not present with IoT devices, given their limited memory and processing capacity.
IoT security best practices
As illustrated below, adherence to IoT security compliance management best practices requires the institution of policies enforced during different phases of an IoT device’s lifecycle. This is why we’ve organized the next part of this article, which focuses on the best practices for improving IoT security, into two separate sections.
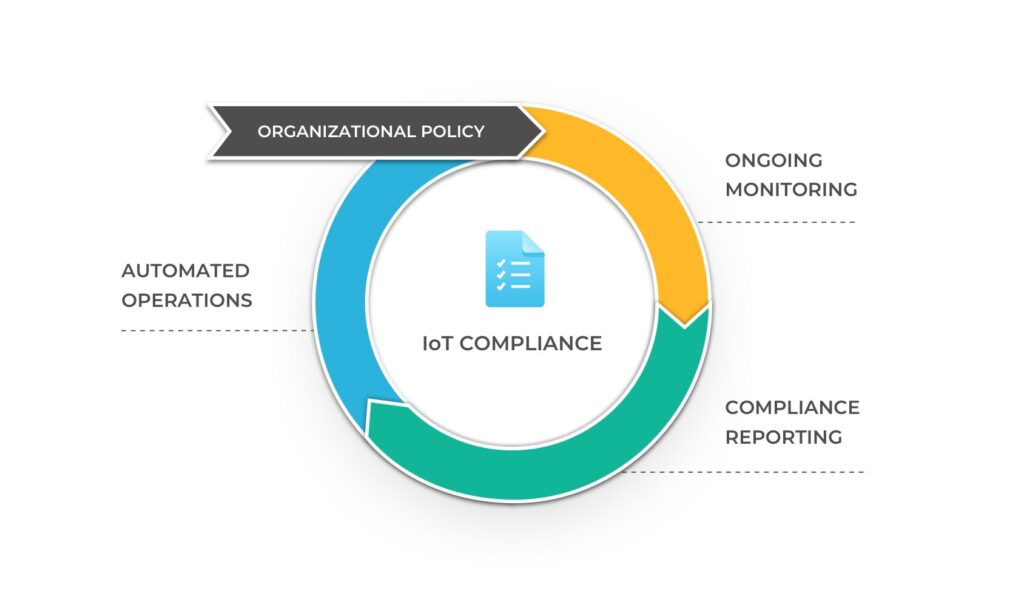
The lifecycle of IoT security compliance management. (Source)
First are the best practices that apply to security measures during a project’s development and procurement phases. The second set of best practices covers the security measures during operations and the lifecycle of IoT devices.
IoT security best practices for procurement and development
Building or buying (procuring) IoT devices is essential to IoT security. The procurement and development processes can introduce vulnerabilities and weaknesses that can be difficult to address once a device is in production. Let’s look at the 11 best practices to help organizations secure their IoT deployments.
Assume users will NOT follow guidelines
Assume that the user will not follow any guidelines: Design so that security hardly depends on the user’s discretion. An example is mandating the default password change with a firm password policy in place at the time of device setup, rather than leaving it to the user’s choice.
Select IoT chips with security requirements in mind
When selecting a chipset, look for the following:
- Enough flash memory to support over-the-air (OTA) updates and factory reset. This means the flash memory should be at least 3x your application image size. If that cannot be afforded, at least 2x memory should be present to support OTA updates.
- Presence of hardware accelerators. Hardware accelerators enable encryption and decryption on the chip, using cryptographic algorithms such as SHA-256 and AES-128. This facilitates the use of secure protocols like HTTPS and RTSPS.
- Sufficient RAM to support the cryptography stack. Even with hardware accelerators, some amount of RAM is still required for encryption and decryption, and this can become a bottleneck when the application and connectivity stacks consume the available RAM.
- Support for secure boot and flash encryption. This ensures that only signed firmware is loaded into memory, preventing a malicious actor from reading the firmware. Presence of Hardware Security Modules (HSMs) for storage of cryptographic keys. HSMs are recommended for mission-critical applications with strict security requirements.
Use secure network protocols and strong encryption
For communication, choose secure protocols wherever possible (for example, HTTPS, RTSPS, Secured MQTT). If the protocol doesn’t have secure equivalents, perform a custom encryption of data before transmitting it. AES-128 is also good enough for a custom encryption layer on top of the data.
Leverage sensors for physical security data
Hardware sensors enable adequate physical security. If the product can afford it, add hardware sensors for tamper detection. This is especially important for security devices like smart locks and video doorbells.
Adopt certificate-based authentication
Teams should use certificate-based authentication (e.g., X.509) over simple API keys. The best practice is to have a unique certificate for each device.
Disable unused features
Teams should ensure that all unused communication ports are sealed off (both on the device and in the cloud). Otherwise, these can act as entry points for malicious actors.
Ensure security requirements are met during development
If possible, develop the application in-house. If that is not feasible, ensure adequate security measures are part of the contract with the third-party agency developing the application.
Don’t hard-code credentials
Avoid hard-coding credentials in the firmware and ensure that no back gates are present in the production firmware.
Secure the cloud side of your IoT systems
Rate limiting should be implemented on the cloud and application sides to protect against brute force and DDoS attacks.
Consider observability and troubleshooting
Provide mechanisms to diagnose and troubleshoot devices remotely and, if possible, extract logs from them remotely.
Apply frameworks to guide development, design, and implementation choices
Comply with security frameworks like NIST IoT Security Guidelines. Also, use OWASP IoT Top 10 as a reference and ensure that your device and infrastructure avoid the common vulnerabilities.
Best practices for post-deployment IoT security
IoT security remains important after deployment throughout the entire operational lifecycle of an IoT device. Let’s explore eight key best practices teams can use to secure IoT devices once deployed.
Audit cloud infrastructure and apps regularly
Ensure regular security audits of the cloud infrastructure and the application. This also includes Vulnerability and Penetration Testing (VAPT)
Patch bugs and vulnerabilities quickly
Be on the lookout for any bugs or vulnerabilities reported by users. When found, release the fix automatically to devices with the auto-OTA feature and notify users to update the device where manual intervention is required. This also applies to the user application.
Automate certificate rotation
Set up automated certificate rotation to prevent expired certificates from being exploited.
Enforce RBAC and MFA
Ensure role-based access control (RBAC) for device data and cloud infrastructure access. This includes summary dashboards. Depending on the sensitivity of the data, implement multi-factor authentication (MFA). For infrastructure access, MFA should be mandatory.
Stop using devices that reach end of support
If software support is available for only a few years after the sale of the device, inform the users about the end of support as the deadline approaches, and educate them about potential security risks. Once a device reaches the end of support, decommission
Make compliance a priority
Ensure the user’s data is handled in compliance with the applicable regulations, like GDPR.
Monitor for suspicious activity
Perform anomaly detection on the cloud using AI/ML or simple rule-based systems to detect unusual activity, such as excessive data transmission and too many new device registrations.
Properly dispose of IoT devices
When it comes time to decommission an IoT device, follow these two steps consistently:
- Make sure to wipe all sensitive information from the device before disposal.
- Revoke the device’s access tokens, certificates, and keys from the cloud.
IoT security management software
IoT security combines device, cloud, and application security. It always boils down to the weakest link, so a holistic view of security is necessary. Additionally, organizations often require a comprehensive view of the security system’s health and a summary of all associated risks.
To address all these requirements, it is prudent to have dedicated software for managing IoT security. Enterprise solutions like SecuriThings are designed for such a use case.
For example, an IoT security management software can help achieve:
- Centralized monitoring and control
- Automatic OTA updates
- Password management and rotation
- Compliance reporting
- Device lifecycle management, from deployment to decommissioning
- Integration with other cybersecurity tools like SIEM
In addition to the field devices, this software can also help manage physical security devices at your premises, including CCTV cameras, biometric and RFID scanners, and other similar devices, as illustrated below.
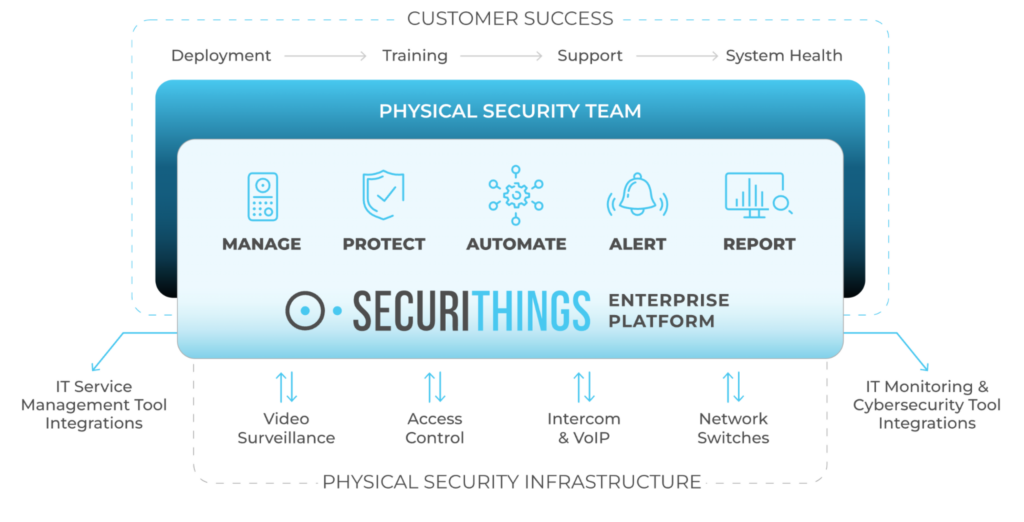
As you scale, it makes sense to invest in security management software and let it handle the bulk of the monitoring and alerting, allowing you to focus on building better products and services.
Not all IoT environments are created equal. Physical security devices, such as surveillance cameras, access control systems, biometric readers, and video management platforms, introduce unique challenges beyond standard IoT device management. These systems often operate in fragmented ecosystems with little standardization, rely on proprietary protocols, and come from various manufacturers. As a result, traditional IT and cybersecurity tools, like SNMP-based monitoring platforms or endpoint protection solutions, cannot typically interpret, manage, or secure them effectively.
This creates a significant blind spot for IT and security teams and places a heavy operational burden on physical security teams. Common IT tools often fall short in critical areas such as lifecycle management, root-cause diagnostics, automated firmware upgrades, password rotation, and compliance tracking. Addressing these challenges requires purpose-built solutions that support deep integration with physical security infrastructure, ensuring availability, security, and resilience at scale.
The ecosystem for managing connected systems is broad and fragmented. Traditional tools are optimized for IT infrastructure, business apps, or cyber-physical security, but they often fall short when applied to physical security environments. The diagram below highlights how various categories of tools serve different needs and why selecting the right tool for the job is essential.
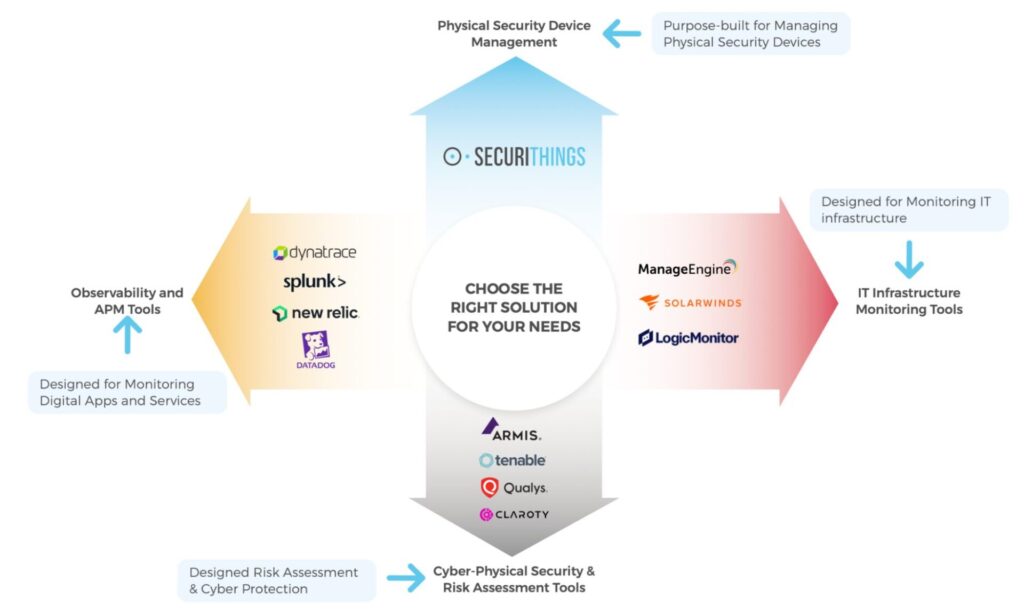
Tool categories for managing IT, digital services, and physical security infrastructure (Source)
The diagram above illustrates how different tools are designed to serve distinct purposes, whether monitoring digital services, managing IT infrastructure, or securing physical security environments. To further clarify the differences, the following table summarizes the primary use case of each tool category. It highlights why traditional solutions often fall short when applied to physical security systems.
| Tool category | Primary use case | Limitations for physical security |
|---|---|---|
| Observability & APM Tools (e.g., Splunk, New Relic) | Monitoring digital applications and services | Lack of physical device visibility and lifecycle capabilities |
| IT Infrastructure monitoring tools (e.g., SolarWinds, LogicMonitor) | Network device health and uptime | Can’t interpret proprietary protocols or manage physical devices |
| Cyber-Physical security & Risk assessment tools (e.g., Armis, Tenable) | Threat detection and cyber risk scoring | Focused on cyber risks, not operational/device lifecycle management |
| Purpose-built physical security platforms | Managing CCTV, access control, and biometric systems | Specifically designed for operational and cybersecurity management of physical security devices |
Choosing the right tool based on the IT, cyber, or physical environment is key to effective management, visibility, and security across the IoT landscape.
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Conclusion
Security is crucial to the scalability of IoT, and organizations that implement IoT security effectively can gain a competitive advantage. IoT device security poses unique challenges primarily from resource constraints (memory, processing, power, connectivity). The battle is half won during the development stage. Security-focused decisions taken during system development can significantly reduce risk during deployment. Post-development security management software like SecuriThings can improve and simplify IoT security.


