Enterprise IoT Security Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
Enterprises increasingly rely on IoT devices to streamline operations, but this convenience comes with a cost. With over 21.5 billion IoT devices projected globally by the end of 2025, more than 20% are attached to local area networks via wired or wireless connections. Connecting these IoT devices to the enterprise network helps automate many tasks and streamlines processes. Still, on the other side, it increases the attack surface and introduces new attack vectors against the enterprise network.
As per Zscaler ThreatLabz 2023 Enterprise IoT and OT Threat Report, IoT malware attacks increased 400% in 2023, compared to the same period in 2022. While most of these attacks target routers (approximately 66.7%), a significant portion also focused on internet-connected cameras (7.7%) and DVRs (5.1%). Botnet activity continues to dominate the threat landscape, with the Mirai and Gafgyt malware families accounting for 66% of observed attack payloads.
To protect the enterprise network from vulnerability and attacks introduced by IoT devices, the network and security teams should develop a clear plan and guidelines for controlling their connectivity to the enterprise network and provide clear visibility and granular control over traffic generated and received by these devices.
This article examines best practices for enterprise IoT security, providing actionable guidelines and recommendations for network and security teams to effectively secure, monitor, and manage IoT devices.
Summary of key enterprise IoT security best practices
The table below summarizes the best practices and mitigation strategies enterprises can adopt to reduce the risk associated with IoT device integration.
| Best Practices | Description |
|---|---|
| Define clear policies | It all starts with policy and guidelines. This policy should be detailed and precise for technical and non-technical employees. |
| Perform network and device hardening | Modify default configurations: disable non-essential features, remove unnecessary services, disable insecure protocols, and apply security patches. |
| Include security requirements as part of IoT device selection | Security teams must be involved in the device selection process and ensure all IoT assets meet minimum security standards defined by organizational policy. |
| Regularly run IoT device discovery | You can’t secure what you don’t know. Regular device discovery using specialized tools is essential to identify unmanaged or unauthorized IoT devices. |
| Use zero trust with your IoT devices | Never trust, always verify. All devices must authenticate before connecting to the network. |
| Follow the principle of least privilege | Provide users and devices with only the minimum privilege required to achieve the expected functions, not more. |
| Segment IoT networks and devices | To limit this lateral movement, organizations should implement robust segmentation strategies. |
| Monitor IoT devices continuously | Security is an ongoing process, and continuous monitoring is critical to any effective security operation. This includes leveraging centralized, automated platforms for enterprise IoT environments to monitor device activity, health, and security events at scale. |
| Make security awareness a priority across the organization | Building a strong security culture through training, accountability, and clear policies is essential to minimizing human-related risks. |
| Create an incident response plan | Even with strong security controls, incidents can still occur, making an incident response plan essential. It outlines the steps to detect, contain, investigate, and recover from security breaches. |
| Invest in end-to-end device lifecycle management | IoT devices beyond their End of Service (EOS) or End of Life (EoL) introduce serious risks as they no longer receive firmware updates or security patches from the manufacturer, leaving them vulnerable to cyber threats and exploitation. |
Monitor the health of physical IoT devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports
IoT security management



10 enterprise IoT security best practices
In enterprise environments, IoT is used for automation, environmental monitoring, physical security, and a wide range of other applications. These devices often require accessibility and monitoring through the corporate IT network.
The core IoT security challenge is that these devices become part of your network and may interact with critical IT assets. This requires careful planning, strict access control, and continuous monitoring.
The following sections outline 10 practical enterprise IoT security best practices that can help mitigate business risk and enhance an organization’s security posture.
Define clear policies
A clear, precise, and well-communicated policy is the starting point before any IoT deployment. This policy should cover all aspects of the IoT device life cycle, from procurement to selection to deployment and monitoring.
When it comes to enterprise IoT security, below are examples of key points that organizations should cover in their policies:
- Minimum security requirements: IoT devices should support secure authentication when connecting to the network, such as 802.1X, using secure credentials like certificates (EAP-TLS). Administrators should ensure that the certificate is stored securely on the device.
- Vendor support and patching policy: the expected lifetime and the vendor’s support level for patching and software updates.
- Data encryption at rest and in transit using a secure protocol like AES128/256, TLS1.3.
- Physical security for IoT devices and how to ensure that no one can tamper with or steal them, particularly when they are mounted in public or open areas. In the event of tampering, devices should not retain configurations or settings that hackers can use to compromise the network or other devices.
- Connectivity to the network and security controls are required for segmentation and access control between IT (where enterprise assets are connected) and OT environment (where IoT devices are connected).
Perform network and device hardening
Hardening is modifying the default configuration of a device or system to reduce its attack surface by disabling unnecessary features, enforcing strong authentication, and applying security controls. Proper hardening should be applied to IoT devices and to any network component where they are connected (and to all connected components in the enterprise in general). IoT devices come with default settings designed to simplify configuration and access. Administrators should review and modify default settings before connecting IoT devices to an enterprise network.
Examples of hardening processes include:
- Changing a default password to a more complex and secure one
- Applying firmware upgrades regularly
- Disabling insecure protocols (e.g., Telnet, HTTP)
- Disabling unused ports and services
- Implement logging and monitoring using secure protocols only
Include security requirements as part of IoT device selection
IoT devices support various departments within the enterprise, and often, these departments may need to order them using their budgets. Without a clear policy and IoT selection process, you risk having insecure IoT devices connected to the enterprise network in an insecure manner, lacking secure authentication and communication methods. It is crucial that enterprises clearly communicate their IoT selection policy to all stakeholders and have the IT and security departments review the specifications and features of IoT devices before ordering them.
When selecting an IoT device, it is essential to review the supported security and communication protocols. A general guideline is to ensure they meet the minimum accepted security protocols in your enterprise. There are instances where the business needs to order specific devices that do not meet this criterion; in these cases, all stakeholders should be aware of the risks and agree on security mitigation controls that should be added to the network before connecting these devices.
Regularly run IoT device discovery
According to a Zscaler report, consumer-grade IoT devices account for nearly 50% of those found in enterprise environments. This includes shadow IoT devices (devices installed without your approval), which is why frequent discovery is essential.
You cannot manage or secure what you don’t see, and a full scan of the network may reveal many devices and systems that are currently flying under the radar and creating enterprise IoT security risks.
Traditional network discovery tools often use ping, SNMP, and LLDP protocols to identify devices. Still, this approach has limitations, particularly for physical security devices, which frequently use proprietary or non-standard protocols. As a result, traditional IT or cybersecurity monitoring tools may be unable to communicate with these devices beyond basic network-level visibility (e.g., up/down status).
Effective enterprise IoT discovery requires tools capable of handling these fragmented ecosystems. Depending on the manufacturer, these tools often use agentless and agent-based methods. These tools provide the visibility needed to manage and secure devices that would otherwise remain opaque.
Use zero trust with your IoT devices
Never trust, always verify. This is one of the core tenets of modern cybersecurity. Before connecting to the network, all devices must authenticate by providing valid credentials, such as certificates or a username and password. Some IoT devices only support less secure authentication protocols like MAC authentication or WLAN PSK. Special consideration should be included to mitigate the risk of these devices, like segmentation, NGFW (Next Generation Firewalls), or behavior analytics using advanced AI and ML algorithms.
Zero trust goes beyond authentication and network access control. It enforces continuous verification and least-privilege access as long as the device is connected to the network. Even after a device is authenticated, its access must be tightly controlled based on its role, behavior, and context. If a device starts behaving unexpectedly, such as sending traffic to unknown destinations, it should be automatically isolated. Zero Trust for IoT requires integration with identity services, network segmentation, and real-time monitoring tools to ensure that trust is never assumed and every action is validated.
The figure below illustrates the core principles of zero trust, as outlined by Gartner. We will cover some of them in other sections of this article.
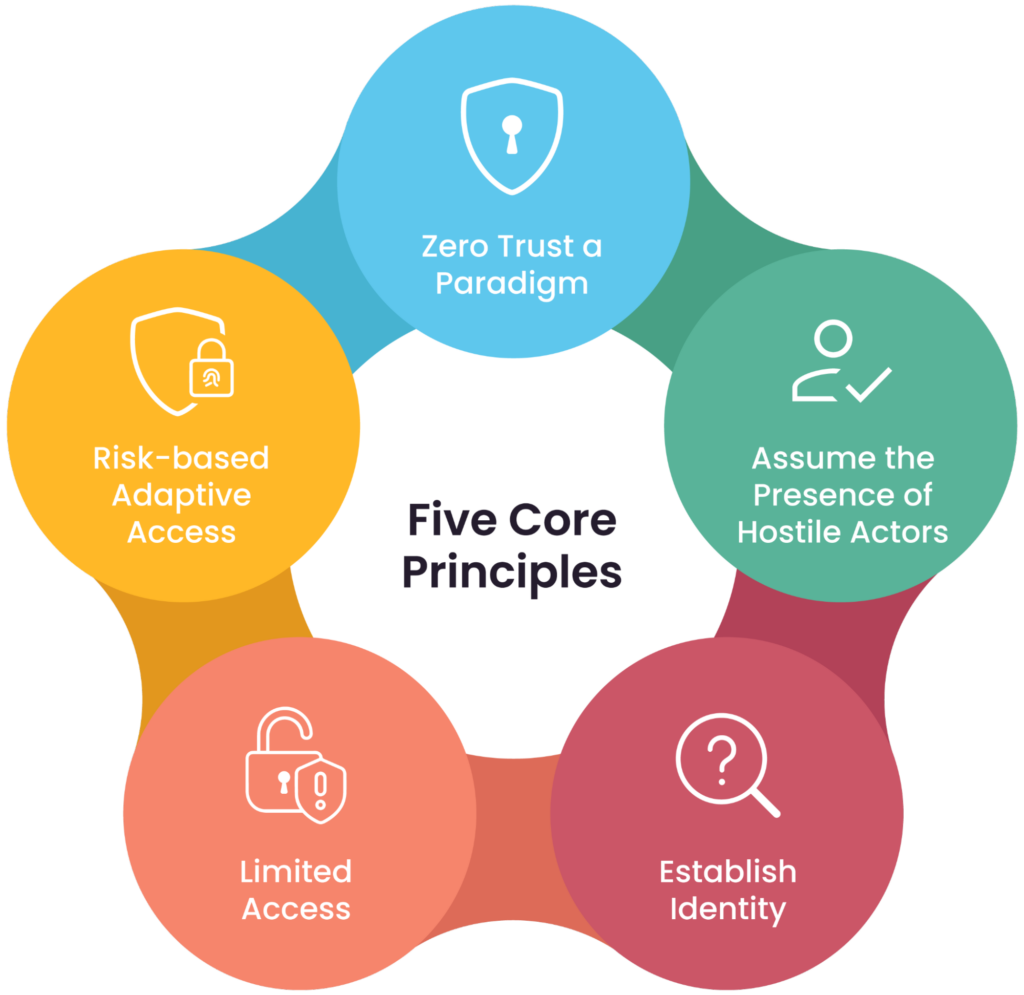
Zero Trust core principles (Source)
Follow the principle of least privilege
Least privilege is about providing entities (users, devices, services, applications) with the minimum access required to achieve their functions. This access or privilege should be reviewed regularly to ensure it remains necessary and essential for the functionality of these devices or users.
IoT devices typically need to communicate with other systems inside the enterprise to report telemetry or automate certain operations. They may also need to communicate with cloud services for updates, monitoring, or instructions. It is essential to monitor and control these interactions to ensure they don’t communicate with unknown or unnecessary systems inside the enterprise or over the Internet.
Segment IoT networks and devices
Segmentation is dividing the network into smaller sections and isolating these sections using security appliances and tools. In extreme cases, segmentation may mean an air gap, where systems are totally isolated and cannot communicate over the network.
The figure below shows a simple presentation of the main segmentation options.
- In subnet or VLAN-based segmentation, communication between segments typically occurs through a firewall. To ensure robust security, it is recommended to use a Next-Generation Firewall (NGFW) that offers advanced features, including deep packet inspection, application control, and threat prevention. Relying solely on routing or basic ACLs is insufficient when robust security is required.
- In an air-gapped setup, networks are physically isolated, with no shared connections or communication paths. This type of segmentation provides a high level of security by design, preventing threats from spreading across environments. However, it introduces operational challenges, such as limited remote access and difficulties in patch management, requiring strict procedures for data transfers.
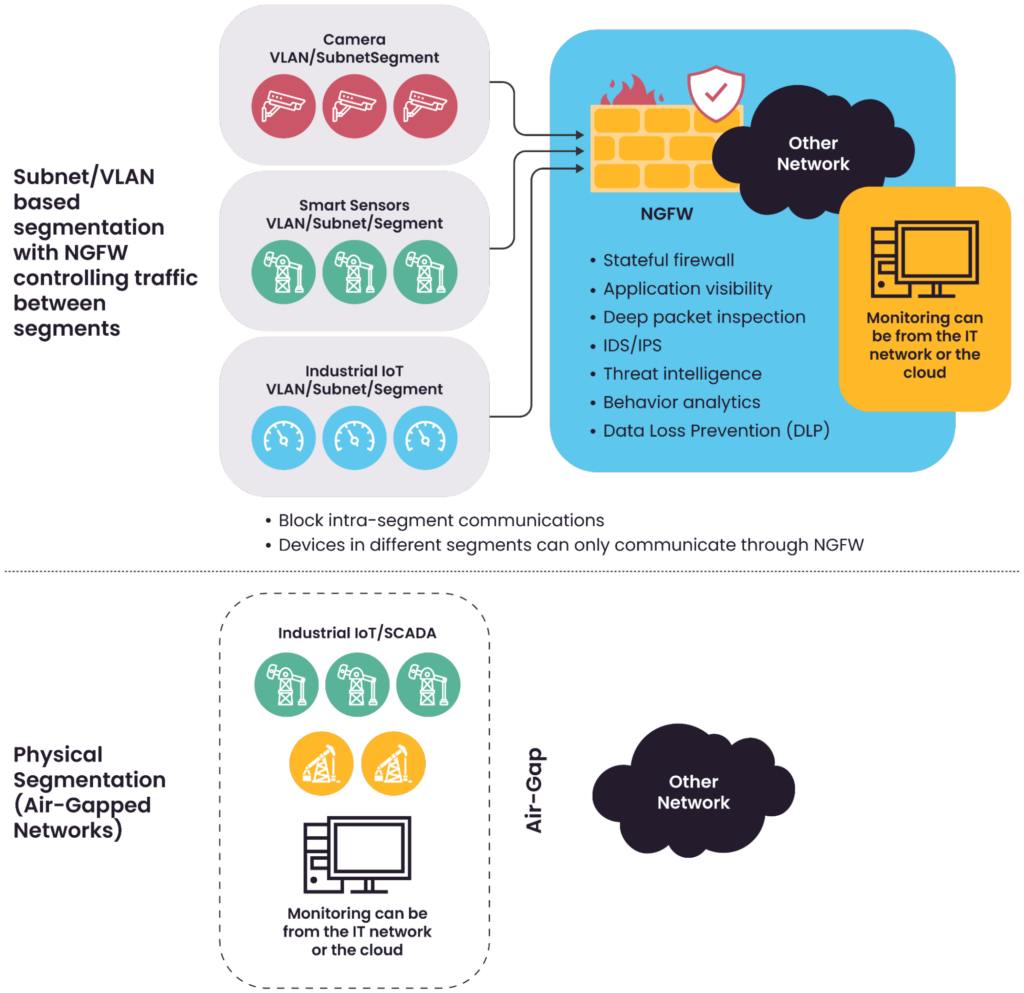
A simple presentation of the main segmentation options.
In cybersecurity and IoT connectivity, the primary purpose of segmentation is to control the connectivity between device groups and limit the lateral movement of hackers or malicious users in case of device compromise. This segmentation can be per device group (macro segmentation) or device (microsegmentation).
While air gaps can be considered the most secure solution for protecting IoT devices, they require careful planning and strict adherence to rules to ensure their effectiveness. On the other hand, they limit the visibility and control of these devices from the IT network, which may limit their functionality.
Effective segmentation requires striking a balance between security and usability. Segmentation rules should align with business needs and technical constraints to ensure devices are both protected and able to perform their designated roles.
Monitor IoT devices continuously
Security is an ongoing process, and without monitoring, you cannot measure the effectiveness of your security controls. Monitoring also encompasses the operation and availability of your IoT devices, as well as the status of their hardware, firmware, and connectivity.
Many IoT device vendors offer the option to monitor their devices from the cloud and provide specialized tools for this purpose. With different vendors managing different device types, this siloed approach becomes difficult to scale because not all tools offer the visibility or controls required for effective monitoring.
Although obtaining a completely unified view of all connected IoT devices is challenging because of the absence of industry standards, organizations can significantly enhance visibility by implementing centralized platforms for operational technology (OT) and physical security devices. These platform providers collaborate with IoT and OT vendors to develop integrations with various device models. These integrations provide insight into device status, activity, and security posture, streamlining operations across enterprise environments and enabling consistent policy enforcement.
Make security awareness a priority across the organization
Securing the enterprise is not only the responsibility of network and security teams. It’s a shared responsibility across the entire organization. Many cyberattacks begin with social engineering tactics that exploit uninformed or untrained employees or through the use of unauthorized IoT devices introduced via shadow IT. Building a strong security culture through training, accountability, and clear policies is essential to minimizing human-related risks.
A security awareness program may include items like:
- Mandatory annual security training that covers the basics of information security, social engineering techniques, and the risk of shadow IT.
- Role-based security training for specific groups like IT, developers, and finance.
- Security orientation for new hires during the onboarding process.
- Phishing simulations that mimic real-world attack scenarios to test employee awareness, identify vulnerable users, and reinforce safe email practices by asking failing employees to attend additional training.
Create an incident response plan
Cyberattacks pose a constant threat to any network-connected system, and even with the highest security controls, incidents can still occur. An effective incident response plan ensures that all stakeholders know their roles during a security event, reducing confusion and response time. It should include predefined playbooks for common scenarios such as ransomware, IoT device compromise, or unauthorized access. Regular drills and tabletop exercises help validate the plan and prepare teams to act quickly and decisively when an actual incident occurs.
NIST SP 800-61 Rev. 3 provides a structured framework for building and enhancing an effective incident response capability. It highlights the critical importance of preparation, clearly defined roles, and thorough documentation to ensure consistent and coordinated response efforts.
NIST SP 800-61 Revision 3 emphasizes the critical role of preparation, continuous learning, and adaptability in building an effective incident response plan. It encourages organizations to invest time in proactive planning and to routinely review and refine their strategies in response to evolving threats, technological advancements, and lessons learned from past incidents. These practices are essential for reducing response time and improving overall resilience to future incidents.
The guidance introduces a high-level incident response lifecycle model, as shown in the figure below, that aligns with the six functions of the NIST Cybersecurity Framework (CSF) 2.0. These functions represent foundational cybersecurity outcomes and provide a structured approach to managing risk throughout the incident lifecycle:
- Govern (GV): Establishes, communicates, and monitors the organization’s cybersecurity risk management strategy, policies, and expectations.
- Identify (ID): Involves understanding the organization’s current cybersecurity risks, assets, and potential vulnerabilities.
- Protect (PR): Focuses on implementing safeguards and controls to manage identified cybersecurity risks and prevent incidents.
- Detect (DE): Enables timely discovery and analysis of potential cybersecurity events or anomalies.
- Respond (RS): Guides the appropriate and coordinated actions to contain, analyze, and mitigate the impact of a detected incident.
- Recover (RC): Supports the restoration of affected systems, services, and operations, while incorporating lessons learned to strengthen future preparedness.
The figure below illustrates the incident response lifecycle based on the NIST Cybersecurity Framework 2.0 functions. This model applies to any incident response plan and is not limited to IoT-related incidents.
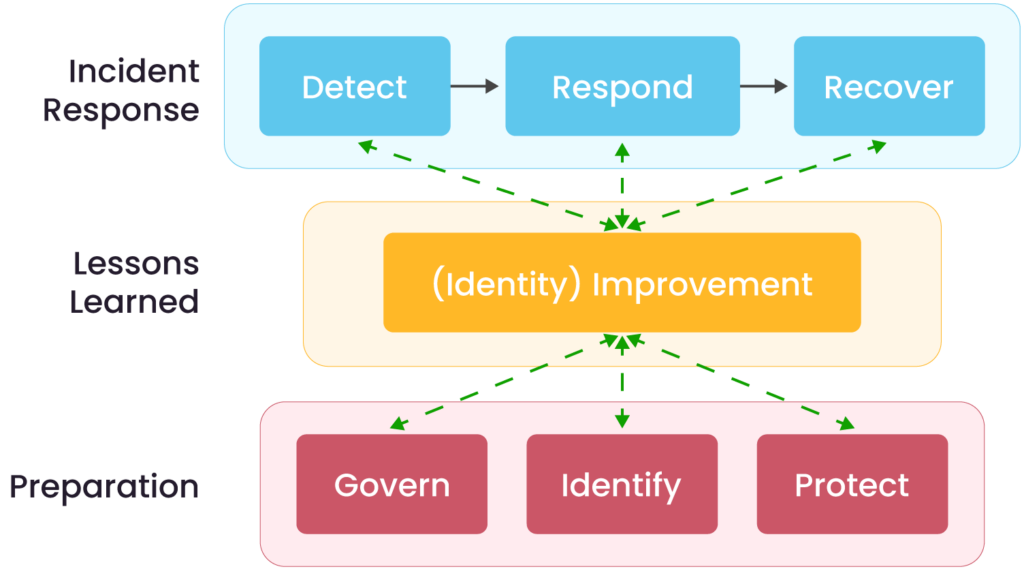
Incident response life cycle model based on CSF 2.0 Functions(Source)
Invest in end-to-end device lifecycle management
There are two important dates to monitor in the life cycle of IoT devices:
- End of Life (EoL): indicates that a device has reached the end of its lifespan and will no longer be produced or sold.
- End of Service (EoS): the date when firmware updates, security patches, and manufacturer support are no longer available.
After the EoL date, manufacturers typically stop introducing new features and the latest technologies into the device, but they still provide bug fixes and vulnerability patches. However, once the device reaches EoS, the manufacturer offers no support, and any newly discovered vulnerabilities will remain unpatched, creating a growing cybersecurity risk.
Manufacturers follow different timelines and policies for declaring EoL and EoS, making it difficult for organizations to track and plan replacements. Some vendors publish clear schedules, while others may change dates without notice, adding complexity to lifecycle management.
To address this issue, you need to keep track of EoL and EoS dates using a centralized system that consolidates data across all device types and manufacturers. This visibility enables IT and security teams to proactively plan replacements, minimize risks, and ensure ongoing compliance.
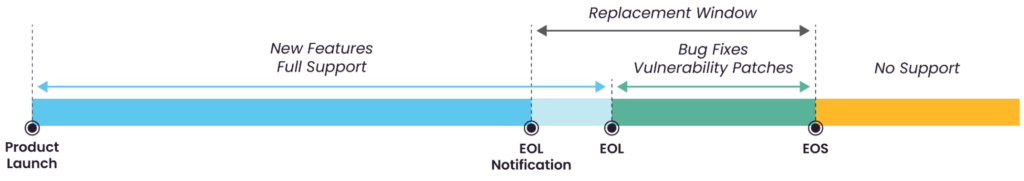
Simple device lifecycle management overview. (Source)
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Last thoughts
IoT devices are essential for modern business operations, but they introduce significant security risks and vulnerabilities. Securing enterprise IoT environments requires more than isolated technical fixes. It demands a comprehensive, proactive strategy that spans the full lifecycle of each device, from procurement to decommissioning. This includes establishing clear policies that define security expectations for all stakeholders, hardening devices and networks to minimize vulnerabilities, and involving security teams in the device selection process.
Organizations must also prioritize continuous device discovery to maintain complete visibility, enforce zero-trust and least-privilege principles for access control, and deploy effective network segmentation to limit lateral movement. Building a culture of security awareness across the organization is equally important, as is preparing a robust incident response plan. Finally, actively managing device lifecycles, especially monitoring End of Life (EoL) and End of Service (EoS) timelines, helps prevent risks associated with outdated and unsupported technologies.
As the number and diversity of IoT devices continue to grow, traditional security approaches are no longer sufficient. Organizations must move toward scalable, automated, and integrated solutions that provide unified visibility, real-time analytics, and policy enforcement across their IoT infrastructure.
Adopting a centralized monitoring platform for operational and physical security devices can significantly reduce the complexity of managing heterogeneous systems. It also strengthens the security posture of these environments by enabling faster detection, response, and remediation of threats across a large portion of the connected device fleet.