IoT Network Security: Tutorial & Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
While IoT devices enhance convenience in modern life, they also expand attack surfaces and often lack essential security features. As a result, IoT systems are prime targets for threat actors. For example, a botnet called Matrix ran distributed denial of service (DDoS) attacks on multiple IoT device models. You can learn more about how Matrix exploited the IoT devices by reading this article. Organizations that deploy such devices must implement IoT network security and privacy controls to effectively mitigate this type of risk.
In this article, we will discuss the unique challenges of IoT network security, along with common risks and attacks that target IoT devices. We will also explore techniques and tools that can improve the overall security posture of your network, reduce business risk, and secure IoT devices.
Summary of key IoT network security concepts
The table below summarizes nine essential IoT network security concepts that this article will explore in detail.
| Concept | Description |
|---|---|
| IoT device constraints | IoT devices are deployed in massive quantities, and in many cases, they lack sufficient computational, storage, and power resources, which makes it challenging to implement advanced security features in these devices and makes them an easy target for hackers in many cases. |
| Siloed deployments | IoT devices come from different vendors, and each one has its own monitoring and management solution, making it difficult to apply common network and security settings to them. |
| Lack of common IoT standards | IoT devices have many architectures; companies follow different design models and layered concepts. This makes it challenging to apply a single unified security protocol and settings to them. |
| Zero trust | A cybersecurity concept that means no user or device should be trusted to access network resources without proper validation. This validation should be dynamic and continuous throughout the connectivity and can be updated at any time based on the user or device’s current security posture. |
| Least privilege | A security concept that involves limiting users or devices to the minimum privileges and access necessary for them to perform their required tasks. This helps minimize potential damage from security attacks and improves the security and privacy of the network by granting access to data and resources only to those who need it. This access is also restricted to the operations they must perform as part of their assigned duties. |
| Network segmentation | A security practice that divides the network into multiple security segments or zones and controls access between segments. This control can range from total isolation (air gap), next-generation firewall (NGFW), or simply access control lists (ACL) between them.
Network segmentation is not primarily intended to prevent attacks; rather, it helps limit the impact by restricting the lateral movement of hackers within the same segment, which can be confined to a single device (micro-segmentation). |
| Network access control (NAC) | A security tool that limits access to the network to authorized users and devices only and controls their privileges in the network. It achieves this typically by applying the AAA concept (Authentication, Authorization, and Accounting) to all users and devices that connect to the network. |
| Man-in-the-Middle-Attack (MITM) | A cybersecurity attack where the malicious actor intercepts the communication between two parties to steal confidential information or alter the data exchanged between them.
MITM typically starts with a malicious user establishing a trust relationship with one or both parties and inserting himself into the conversation while both parties believe they are communicating directly with each other. |
| Botnet attack | A type of cybersecurity attack in which the malicious actor compromises and controls the victim devices—often referred to as bots or zombies—remotely and establishes a command center to control them in a coordinated attack against targeted resources, commonly known as a distributed denial-of-service (DDoS) attack. |
Understanding IoT device constraints
As the need to connect IoT devices to the network increases, network and security teams are required to provide ways to make the onboarding of these devices easy while maintaining the performance and security of the network.
These devices come from different manufacturers and have different levels of network and security support. While IoT devices make our spaces “smart,” they often lack the necessary resources to comply with enterprise security and network requirements. Let’s start by exploring the implications of these constraints.
IoT network technology selection
IoT device constraints include limited power, storage, and processing capabilities. Organizations should consider these constraints as they source, deploy, and secure systems.
Key factors to consider include:
- Range: The distance the technology can effectively cover.
- Speed: The rate at which data can be transmitted.
- Power consumption: The amount of energy required for operation.
- Cost: The expenses associated with implementing and maintaining the technology.
- Interference: Susceptibility to disruptions from other devices or environmental factors.
Despite these constraints, IoT systems often generate massive volumes of data through various connected devices, including sensors, cameras, and smart appliances. These devices continually capture real-time data such as temperature, motion, health measurements, energy consumption, and additional metrics. With the increasing number of IoT devices, the scale and variety of data produced are growing exponentially, offering rich resources for AI and Machine Learning (ML) model training.
IoT engineers must balance these constraints, the need for bandwidth, and the security implications of having limited computing resources (like CPU and memory) to support the requirements imposed by enterprise regulatory compliance, typically enforced by deploying agents.
This makes network technology selection an important aspect of IoT engineering. Factors such as range, power consumption, bandwidth, cost, and interference are critical in determining the most suitable option. For instance, technologies such as Wi-Fi and Ethernet offer high bandwidth for data-intensive applications. In contrast, LoRa and Zigbee are energy-efficient for long-range and low-power use cases. Additionally, emerging technologies, such as 5G and LPWAN, provide new opportunities for scalability and enhanced connectivity. Table I compares the primary technologies used to connect the IoT devices.
| Technology | Range | Power | Bandwidth | Use Case |
|---|---|---|---|---|
| Wi-Fi | Medium (~100m) | High | High | Smart homes, cameras |
| Bluetooth | Short (~10m) | Low | Medium | Wearables, smart speakers |
| Zigbee | Short (~100m) | Low | Low | Home automation, smart lighting |
| 5G | Long (Global) | High | Very High | Autonomous vehicles, IIoT |
| LoRa | Long (~10km) | Very Low | Low | Agriculture, tracking devices |
| LPWAN | Long (~10-40km) | Very Low | Low | Smart meters, environmental monitoring |
| Ethernet | Short (~100m) | Low | High | Industrial IoT, surveillance |
| Satellite | Long (Global) | High | Medium | Remote monitoring, maritime IoT |
IoT security management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
What makes IoT devices different?
While the term IoT may have different meanings for different people, it generally covers a wide range of physical devices that collect data and transmit it to the cloud or network for monitoring, automation, analytics, control, and other applications. There is no single architectural model for these devices. The only common element among them is network connectivity. Some of these devices may run the same operating system and applications as typical enterprise-managed computers, but in most cases, they differ in many ways.
Constrained device resources
As we have seen, IoT devices come with inherent resource constraints. They have the minimum components necessary to collect data and transmit data. Given their vast quantities, reducing the cost per device is one of the main incentives for manufacturers and end users. While this leads to lower costs, it adds challenges to networking and security, as their limited IoT hardware cannot run advanced authentication and encryption algorithms and has limited networking capabilities.
In addition to hardware limitations, many of these devices are deployed in remote areas and powered by batteries or renewable energy sources, which adds to their constraints. They must run the minimum required networking and security protocols to extend battery life.
Multiple operating systems (OS)
Some IoT devices may run enterprise Windows or Linux operating systems, but their resource-constrained hardware usually runs more specialized operating systems. Some may run lightweight Linux or Android, and in many cases, they run different families of operating systems designed specifically for IoT devices and embedded systems. Many IoT devices use Real-Time Operating Systems (RTOS) like FreeRTOS, Zephyr, or VxWorks, which are designed to handle tasks with precise timing requirements.
For network administrators, this means the tools and controllers you use to manage and patch enterprise computers cannot be applied to these systems, and special management and monitoring tools are required for IoT devices. With the diverse nature of IoT devices, each company of the OS family may need its own tools for patching, monitoring, and management.
Lack of standardization
There is no single shared standard for IoT devices. Every company has its own standards and protocols and its own platform for monitoring, managing, and controlling these devices. For organizations implementing IoT devices, this means dealing with many protocol stacks, each with its own networking capabilities, security requirements, and cybersecurity standards.
Limited support for advanced network and security features
As IoT devices are hardware and resource-constrained, supporting advanced networks and cybersecurity features is not a priority for many IoT manufacturers; their main focus is reducing costs. This is similar for many stakeholders on the consumer side, particularly in the procurement department, where they need to purchase a vast number of IoT devices. Any reduction in price per unit means significant savings for them. However, for you as a network or security manager, this translates to a larger attack surface, increased vulnerability, and more cybersecurity attacks.
The FCC’s program defining rules for IoT cybersecurity labeling may help organizations begin to address the standardization challenge. The initiative aims to categorize IoT devices based on their cybersecurity capabilities and standardize consumer communication about these capabilities. This makes it easier for consumers and procurement departments to select devices that better support cybersecurity algorithms and standards.
Outdated hardware and software
IoT devices are typically installed in large quantities and in remote or complex areas in a way that makes replacement an expensive and complicated process. Thus, organizations tend to increase the life cycle of these devices and keep them in service for longer than other assets.
While this reduces the direct ownership cost of these devices, it means that network administrators must manage outdated hardware running old software and firmware. In many cases, systems have reached the end of support from the manufacturer and vendor, and no software patches, firmware updates, or bug fixes are available.
Scalability issues
IoT devices are typically installed in large amounts as they are needed to manage all aspects of physical security, automation, environmental monitoring, or similar applications that require installing these IoT devices to cover large physical areas or production systems. For you as a network and security administrator, the complexity of connecting, monitoring, managing, and securing IoT devices is multiplied by a large number of devices. Additionally, the heterogeneous nature of these devices and siloed monitoring and management systems makes monitoring and managing them more challenging, especially considering the lack of skilled resources you may have in your organization.
Common attacks against IoT networks
Now that we understand the networking and cybersecurity challenges IoT devices pose, let’s review how threat actors can exploit IoT vulnerabilities to launch cyberattacks.
Man in the middle attack (MITM)
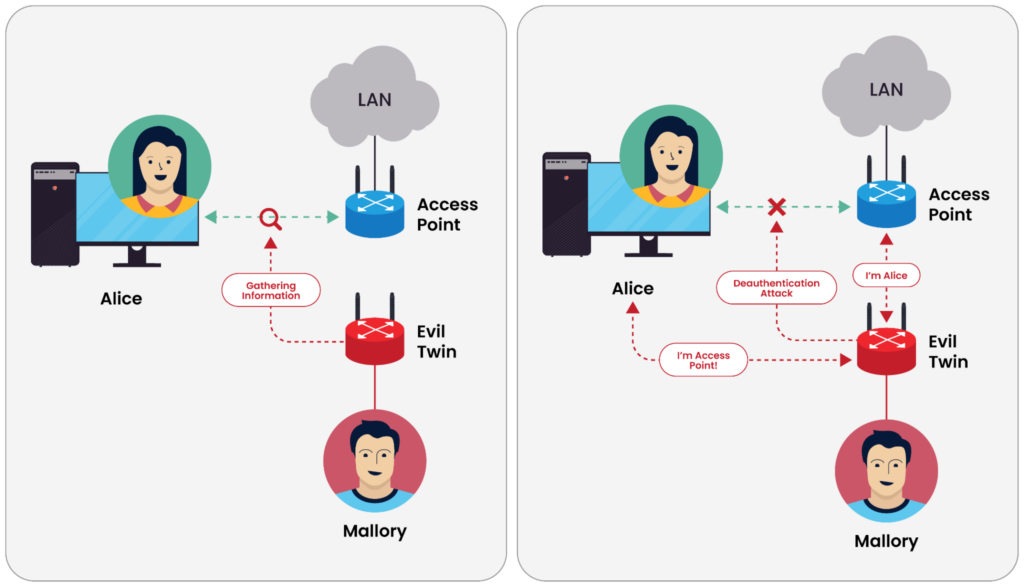
An evil twin attack. (Source)
A man-in-the-middle (MITM) attack is a cyberattack where an attacker secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating. While this attack may target any network-connected devices that a malicious actor can communicate with, IoT devices are more vulnerable to these attacks as they lack support for advanced security features.
Let’s consider a WLAN example. Recent Wi-Fi protocols support mutual authentication, which requires the user to provide credentials to authenticate and the server or network to provide credentials and proof of trust before they start communicating. The concept of mutual trust is essential in current authentication frameworks like EAP-PEAP and EAP-TLS. However, since many IT devices don’t support these protocols, they may rely on outdated and vulnerable protocols like WPA2-Personal with PSK to connect to the network. These vulnerable protocols lack any reliable mechanism to verify network identity, and they rely on weak PSK that can be easily cracked by hackers who may impersonate a valid AP by broadcasting an identical SSID with the same PSK (Evil Twin attack) and intercepting communication between IoT devices and the network.
Distributed DoS (DDoS) attacks
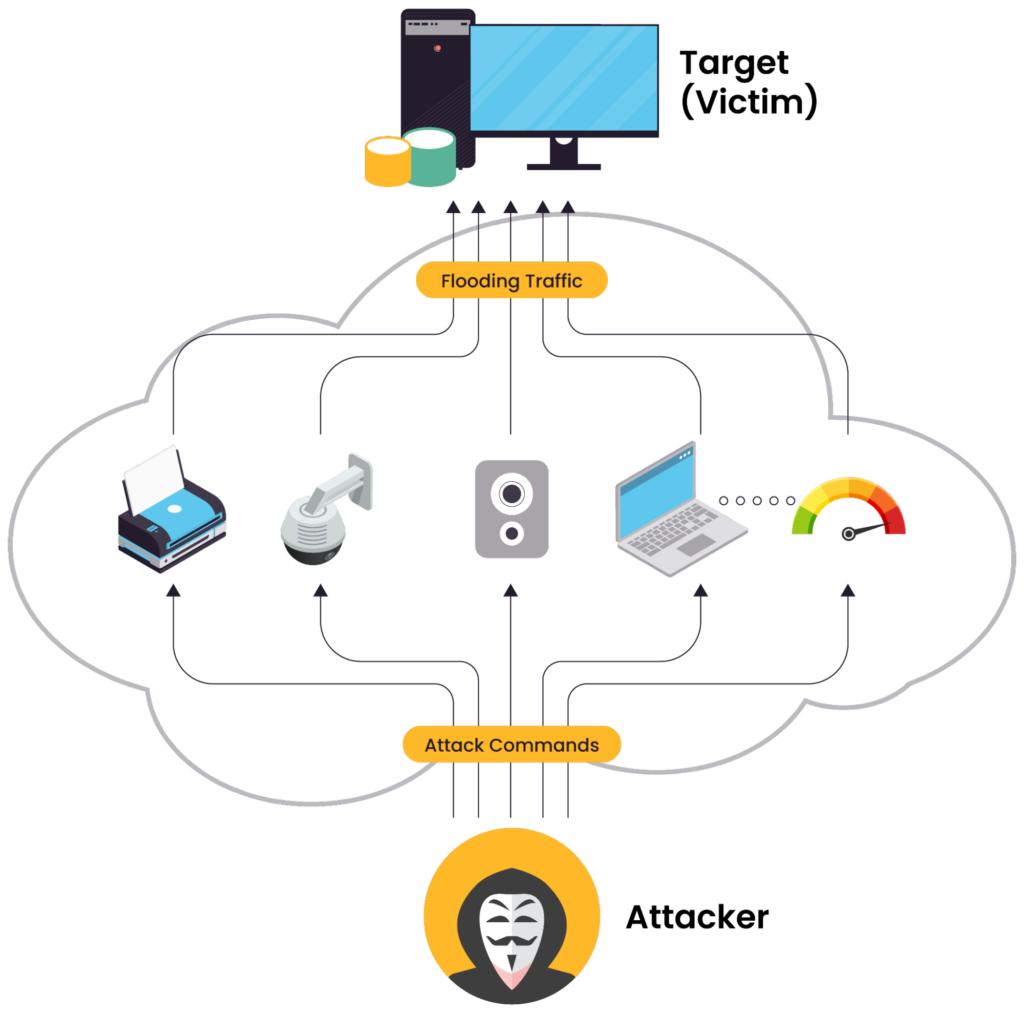
DDoS attached using vulnerable IoT devices. (Source)
IoT devices can be vulnerable due to weak security measures, such as default or easily guessable passwords and outdated firmware. They can be hijacked into a botnet that launches a Distributed Denial-of-Service (DDoS) attack. In a DDoS attack, these compromised devices simultaneously flood a target with excessive traffic, effectively taking it offline.
One well-known example is the Mirai botnet. In 2016, Mirai scanned the internet for IoT devices with weak security. Once compromised, it took control of devices such as IP cameras, DVRs, and routers. The botnet then initiated a massive DDoS attack against Dyn, a major DNS provider, causing widespread internet outages and impacting popular websites like Twitter, Netflix, and Reddit. This attack demonstrated how a significant number of insecure IoT devices could be transformed into a powerful force for disruption.
Spoofing attacks
With weak authentication and poor encryption algorithms, IoT devices are at risk of spoofing attacks. In these attacks, a malicious user introduces a rogue device on the network that impersonates an IoT device by exploiting weak authentication methods, such as MAC authentication, or by cracking vulnerable encryption protocols like WPA-2 PSK. Attackers can use these rogue IoT devices to gain unauthorized access to your network, posing significant security risks. They can exfiltrate sensitive data, disrupt operations through denial-of-service attacks, propagate malware, and compromise system integrity.
You can protect your network from these attacks by implementing more secure authentication protocols, such as certificate-based authentication like EAP-TLS. Additionally, avoid using MAC address filtering as your primary authentication method since MAC addresses can be easily spoofed. Organizations should also avoid using WPA/WPA2 PSK, which threat actors can easily crack with tools like Aircrack-ng.
Eavesdropping & data theft
IoT devices collect sensitive information from your organization, such as telemetry, video, and sensor readings. This makes them a target for eavesdropping and data theft attacks, mainly if they send or store traffic unencrypted or using a weak encryption algorithm. They are also subject to supply chain attacks, where compromised or counterfeit devices can be used by third parties to launch attacks against your network or exfiltrate valuable information.
Lateral movement
Malicious actors who want to access your network may select IoT devices as an entry point into more critical areas of the network. In these cases, they compromise IoT devices as an entry point to move laterally within a network and attack more valuable assets. In these attacks, malicious users find IoT devices easy targets as they lack advanced security features and are vulnerable to exploits.
How to improve IoT network security
Improving IoT security posture is essential to enhancing the overall security posture of the entire network. This section will focus on the techniques and controls that empower organizations to strengthen their IoT network security.
Visibility
Security begins with visibility; you cannot secure what you don’t see. With IoT devices introduced to the network by different departments in your organization, you need to have the necessary features and tools in your network that can scan, profile, and list these devices, providing you with information about device types, operating systems, and device families. This helps you build your network and security strategies around the types of devices connecting to your network.
Visibility also includes maintaining an up-to-date inventory of IoT devices connected to your network and details about manufacturer information, ownership, and physical location. This can be combined with your network access control, scanning, and profiling tools to help track these devices and identify any rogue devices connected to your network. SecuriThings offers a comprehensive IoT and physical device security management platform, which includes inventory discovery, automated patch management, password rotation, regulatory compliance reporting, and more.
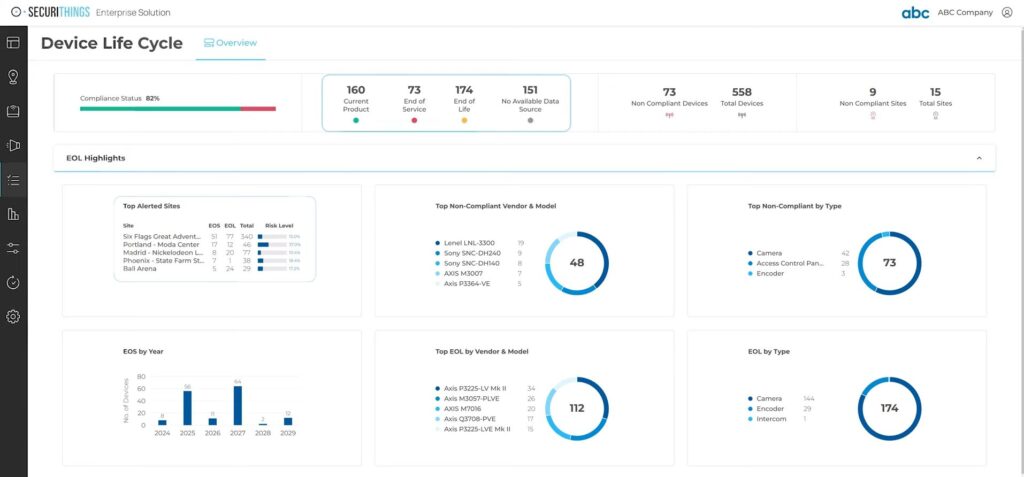
Device life cycle management
With the increasing number of IoT devices, you may lose track of what has been added to your network. This becomes a security concern when some of these devices reach the end of their life cycle and stop receiving new features or security patches from the manufacturer. These “end-of-life” devices, running old and unpatched software, are considered easy targets for hackers and malicious actors.
To mitigate this risk, you need to keep track of all End of Life (EOL) announcements from different vendors and compare part numbers with what you have in your environment. This task becomes more challenging when you have a large number of IoT devices from different vendors and multiple part numbers, as they are purchased at different times. For this reason, it is important to implement monitoring platforms with built-in inventory and life-cycle management, such as SecuriThings, to track and assess the life-cycle status of all devices in your environment. This allows you to replace old or obsolete devices before they reach their end-of-life state as specified by the manufacturer.
The figure below shows the SecuriThings “Device Life Cycle” dashboard.
Monitoring
Monitoring is an essential part of your network security and incident management process. The faster you detect an attack, the more effectively you can isolate it, eradicate threats, and recover systems. Your network should include tools such as SIEM, EDR, XDR, and logging for effective monitoring and alerting in the event of any compromise, exploit, or attack.
With many network attacks initiated by compromising IoT devices, you also need to consider monitoring and managing these devices as part of your overall network security strategy. The challenge is that these devices follow different architectures, and every manufacturer has his own monitoring and management tools with different feature sets, which makes this subject challenging. You need a single pane of glass solution that provides you with a unified view of all IoT devices in your environment, with the option to manage them and verify their compliance with your security policies, such as password complexity, password expiration policies, authentication protocols, encryption algorithms, and hardware and software compliance with regulations and policies.
Patching
While you might have patching solutions for common enterprise operating systems such as Windows, Linux, and macOS, these solutions are often ineffective for many IoT devices. As we discussed before, one of the challenges with IoT devices is in their various operating systems, which are embedded or manufacturer-specific in many cases. The other challenge is that IoT devices operate 24/7, and arranging a maintenance window to upgrade them is difficult. Many IoT manufacturers offer patching solutions or provide patches through their websites, but integrating all these sources and tools into your software patching strategy can be cumbersome.
To effectively manage your IoT device operating system and patching requirements, you need a unified platform that monitors published CVEs, correlates them with your specific environment, highlights relevant vulnerabilities, and coordinates a patching schedule for your IoT devices. Solutions like SecuriThings offer CVE feeds and OS patching as part of their IoT monitoring and management platform, which can help you in your patching process.
Device Hardening
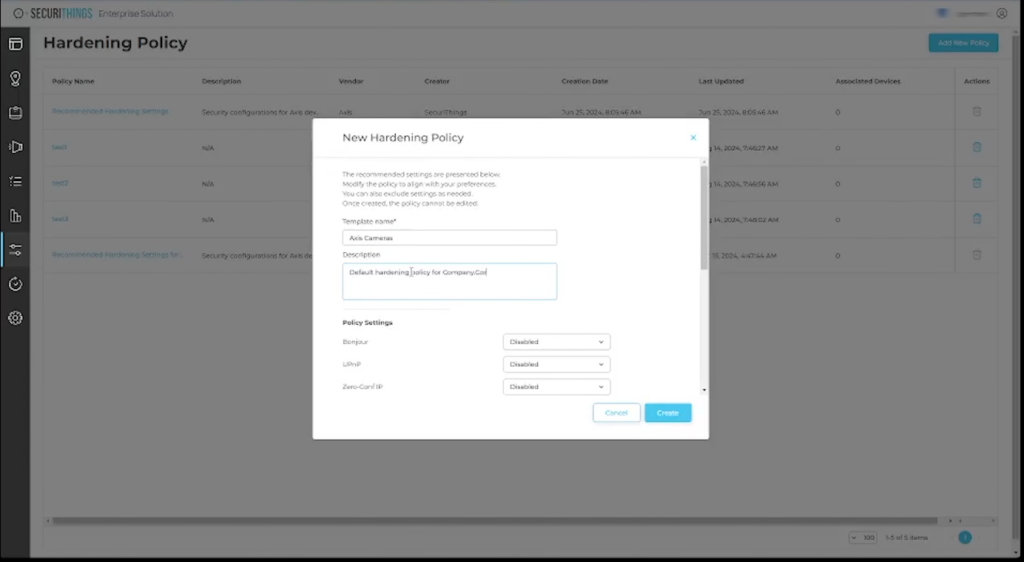
IoT devices come from the manufacturer with default settings that, in many cases, don’t follow best practices. Sometimes manufacturers want devices to be easy to discover and connect to with default settings, but this should change once devices are connected to the enterprise network. The process of modifying default device settings to make them more secure is called “hardening”. The hardening process includes disabling insecure protocols, such as Telnet, HTTP, SNMP v1/2, and other management and communication protocols that are considered insecure. It also includes configuring more complex passwords, among other recommended configuration changes, to make IoT devices more secure and comply with industry and organizational security requirements. This process of hardening becomes more challenging with the large number of IoT devices and different capabilities and configuration requirements for each device type.
To address this challenge, platforms like SecuriThings provide a tool for configuring hardening policies. The tool applies these policies to different device types based on the communication and configuration steps for each type. The figure below shows the process of creating a sample hardening policy. This policy can later be applied to one or multiple device types for better security and consistency.
Network security controls
IoT device security is part of overall network security. To secure IoT devices, you must follow risk management frameworks and best practices and apply the necessary security controls. You also need to deploy network security products like next-generation firewalls (NGFW), intrusion detection systems (IDS), and intrusion prevention systems (IPS), and enable advanced security features like deep packet inspection (DPI), URL filtering, application visibility and control, behavior analytics, and the latest security features. You may need to apply higher security standards in networks or segments where IoT devices are connected.
Security awareness is also an essential part of your overall network security strategy. Educating users (both IT and non-IT employees) about the risks of adding unmanaged or uncontrolled devices into the network can also help improve your overall IoT network security.
Password protection
Passwords are added to prevent unauthorized access to the device, but in many cases, they can be a vulnerability if they do not comply with certain standards and if they are not changed frequently. Many IoT-specific attacks, like Mirai, targeted IoT devices connected to the network with default or simple passwords. Your IoT security policy should include modifying default credentials before connecting IoT devices to the network and scanning these devices for any default or guessable passwords. As explained in this blog about the need for password rotation, a tool like SecuriThings will help enforce such a policy across all the IoT devices in your environment.
The same applies to WLAN PSK. While WPA3 provides more secure protocols for WLAN access, many IoT devices only support outdated and vulnerable protocols. More complex PSK techniques, such as MPSK, frequent key modification, more granular segmentation, and strict security controls within this network segment, may help reduce risks. However, considering more secure protocols should be part of your strategy when purchasing new IoT devices or upgrading current ones.
Network access control
As part of your zero-trust policy, organizations must ensure that only authorized devices are connected to their network. Solutions like network access control (NAC) implement the authentication, authorization, and accounting (AAA) framework to verify and authenticate each device before allowing it into the network. These NAC solutions support multiple authentication protocols, and the security of your NAC department relies on the protocol you select for authentication.
One option is MAC authentication or MAC filtering, but since MAC addresses can be easily detected and spoofed, you should never consider a MAC address as your authentication credential. Administrators should consider more secure techniques like username/password, but they require user interaction and come with risks like simple passwords and password leaks.
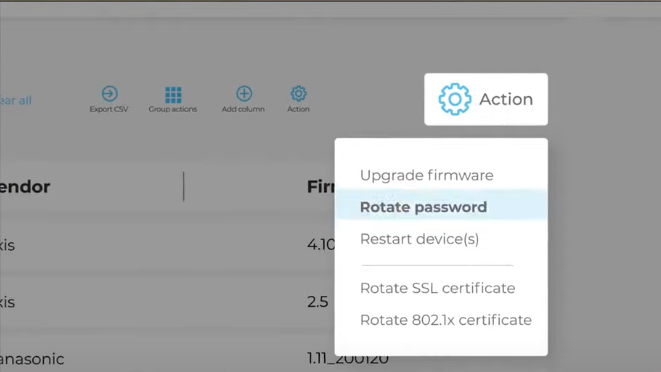
Authentication protocols based on digital certificates have proven more secure and scalable for IoT devices. However, they require special tools and protocols to issue certificates from a trusted root CA and install and renew certificates before expiration. Teams must also monitor certificates for any revocations or expired certificates and ensure that their NAC and IoT management solutions are integrated to automate the lifecycle management of IoT device digital certificates. To automate certificate management on IoT devices, solutions like SecuiThings can help rotate 802.1X and SSL certificates from a central location. The figure below shows some of the features of SecuriyThings when it comes to password and certificate rotation.
Segmentation
Even with robust security controls in place, attackers can sometimes find vulnerabilities faster than you and exploit them to compromise one of your IoT devices. In this case, they attempt to move laterally to more valuable assets in your network, using the compromised IoT device as a pivot point. In some cases, they leverage it to compromise additional IoT devices and control them from a remote command and control center, using them in a coordinated attack against other resources.
Implement network segmentation to limit the impact of such an attack and easily isolate compromised network segments in case of a security incident. A network segment can be a subnet or a VLAN, or even each device can be in its own micro-segment. Organization-critical assets should be in a separate segment or segments, and strict security controls should be applied in one or multiple layers to allow only verified and authorized requests into that segment.
Advanced threat detection and response
In addition to all the security controls discussed above, teams should implement advanced threat detection and response tools. These tools integrate with external threat intelligence feeds and apply machine learning and artificial intelligence techniques to analyze user and device behavior in the network and detect any anomalies or potential compromises in your network.
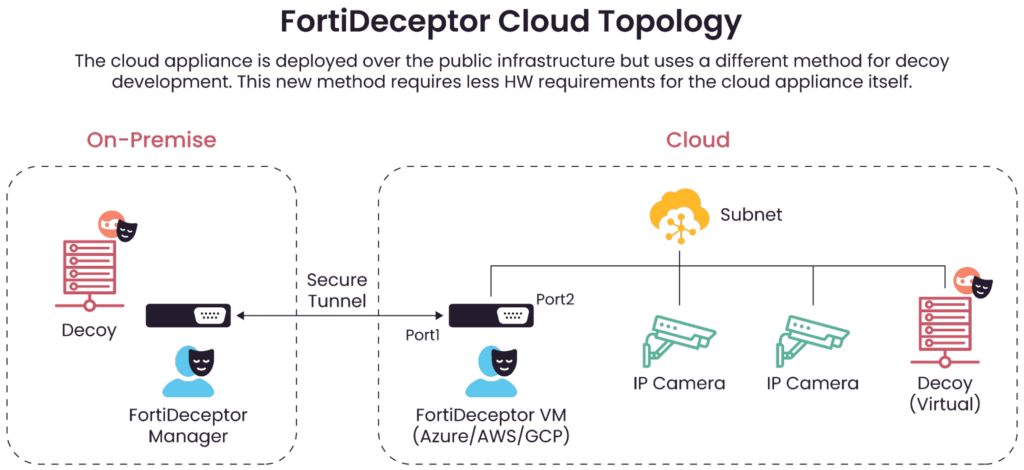
One innovative tool you can consider for your network is IoT decoys and honeypots designed to lure cyber attackers away from genuine devices while gathering intelligence on their malicious activities. For example, one IoT decoy or honeypot might mimic a vulnerable IP camera, attracting hackers to launch their exploits and exposing their methods.
This technique should be used as part of a complete solution that gathers the information and uses it to better protect your network without introducing any additional risk into your network. An example of this solution is a product named FortiDeceptor. You can learn more about it on Fortinet’s documentation page.
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Conclusion
IoT network security is an essential part of your overall network security. IoT devices pose unique challenges and vulnerabilities that demand specific tools and tailored strategies. Many network security products provide additional features or modules specializing in IoT network security to enhance segmentation and incident detection, often integrating machine learning and artificial intelligence. Nevertheless, organizations still require a comprehensive solution to monitor and manage their IoT devices.
A trusted solution for managing IoT devices, like cameras and physical security devices, is SecuriThings. This specialized platform provides a unified single pane of glass for monitoring, managing, patching, and verifying physical security infrastructure compliance. By integrating a platform like SecuriThings into your network security strategy, you protect your critical IoT assets and reinforce your entire network’s defense against emerging threats.


