IoT Security Challenges and Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
Many organizations adopt Internet of Things (IoT) devices to improve automation, gain better operational control, enhance monitoring, and streamline processes. From smart cameras and sensors to access control systems and HVAC automation, these connected devices offer undeniable benefits. However, they also introduce a wide range of security challenges.
IoT devices are typically resource-constrained, heterogeneous, and headless, making them easier targets for attackers and prone to failure. To mitigate the risk of security breaches, organizations must assess these risks, implement adequate controls, and ensure that IoT deployments are secure, resilient, and compliant with relevant organizational and industry regulations and standards.
As shown in the figure below, research from the Journal of Sensors helps highlight the magnitude of IoT security challenges. Among all the complexities facing organizations that use IoT devices, the study found that security is a leading issue and challenge.
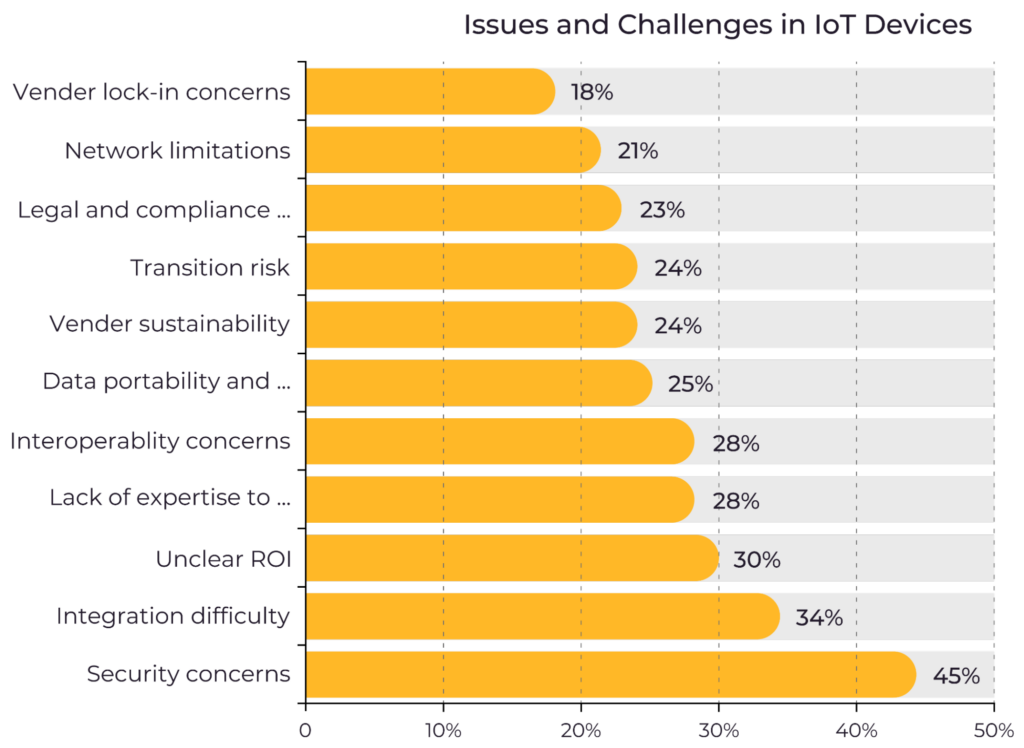
Top IoT device management challenges. (Source)
This article will examine IoT security challenges in detail, providing recommendations and tools to help teams integrate these devices securely into production environments while also addressing their limitations and vulnerabilities. We will also provide actionable strategies to reduce risks, enhance visibility, and ensure long-term security for IoT systems.
Summary of key IoT security challenges
The table below highlights twelve key IoT-related security challenges that will be discussed in detail throughout this article.
| Challenge | Description | Recommendation |
|---|---|---|
| Default and simple passwords | IoT devices come with widely known default passwords, which can be challenging, especially with many devices. | Modify the default password and use more complex passwords. Scan current devices regularly for any known or simple passwords. |
| Outdated and vulnerable software | Many IoT devices are headless with no GUI interface, and they need unique management systems to patch or update software | Use monitoring and management solutions that can provide a unified interface to identify vulnerable software, list CVEs, and apply required patches |
| Limited support for security features | IoT devices are typically resource-constrained to reduce the cost, with limited support for security features that are required in current organizations. | More security controls should be added to the segment where IoT devices are installed. |
| Supply chain security and compliance | IoT devices come from many manufacturers and, in many cases, use specialized and embedded software, which increases the risk of introducing unauthorized hardware or software. | Ensure you purchase IoT devices from approved and trusted vendors and use management and monitoring tools to identify unauthorized devices or software. |
| Privacy challenges | With IoT devices collecting confidential and personal information, it becomes more challenging to comply with privacy regulations. | When collecting data using IoT devices, it is essential to consider privacy requirements and regulations. Hiring an expert and using the proper tools can help apply the required security controls. |
| Physical security of IoT devices | With IoT devices deployed in public or remote areas, their physical security becomes more challenging, as malicious users may tamper with or steal them. | Remote monitoring, physical security, and verifications can help reduce this risk and discover suspicious activities. |
| Lack of visibility | With the large number of IoT devices and the introduction of new models by different departments, each with its own management solution, monitoring and controlling these devices becomes more challenging. | Implement a unified monitoring and management system and a Network Access Control (NAC) system to discover and block rogue or unauthorized devices. |
| Lack of standards | IoT devices come from various manufacturers, and many utilize their proprietary protocols. IoT systems adhere to multiple architectural designs, and many IoT platforms follow their communication standards. | When connecting these devices to the network, follow security best practices, regardless of the protocol or communication method. Apply additional security controls where applicable. |
| Compliance with standards and regulations | Many IoT deployments fail to meet security and privacy standards and regulations, such as GDPR, HIPAA, PCI-DSS, or NIST. Non-compliance can lead to legal penalties and damage to your reputation. | Stay current with relevant industry regulations. Implement security controls that align with relevant regulations and standards requirements and maintain accurate audit trails. |
Monitor the health of physical IoT devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports
IoT security management



IoT security challenges
In the following sections, we will delve deeper into each IoT security challenge, presented in the same order as the summary table above, and explore strategies for overcoming them.
Default and simple passwords
One of the most overlooked yet dangerous device vulnerabilities in IoT environments is the use of default or simple passwords. Many IoT devices come preconfigured with factory-set credentials, such as “admin/admin” or “123456,” which users often forget or neglect to change. Cybercriminals exploit this weakness by using automated tools to scan networks for exposed devices, thereby quickly gaining access without requiring advanced techniques.
An infamous example is the Mirai botnet attack, which hijacked hundreds of thousands of IoT devices by exploiting default passwords and turning them into a massive DDoS army (also known as a botnet or Zombie Army). This incident highlights how something as basic as a weak password can escalate into a significant security threat, making password hygiene a critical first step in securing your IoT ecosystem.
Password attacks can pose privacy and compliance issues, especially if IoT devices are used for video or voice recording. Hackers can access confidential information by compromising cameras or other monitoring devices.
Changing default passwords before connecting any IoT device to your network is essential to mitigate this risk. This simple step can block many automated attacks that rely on factory-set credentials. In addition, you should regularly scan all IoT devices across your organization using centralized tools and modify weak passwords, as shown in the diagram below. Together, these practices form a strong first line of defense against credential-based attacks.
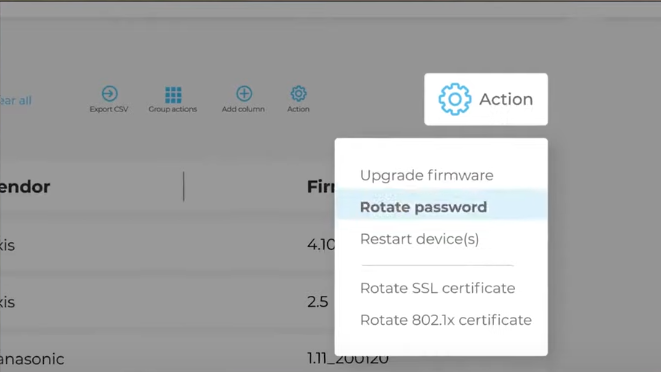
SecuriThings password rotation (source)
Outdated and vulnerable software
Keeping IoT devices updated with the latest software and security patches is critical for ensuring their functionality, protecting against threats, and maintaining compliance with industry standards. However, in environments where hundreds or thousands of devices are deployed, often from multiple vendors (such as Axis, Cisco, Samsung, and Siemens), and running various operating systems (such as Windows, Linux, Android, Zephyr, and RIOT) and firmware versions, this task becomes highly complex, time-consuming, and prone to human error.
Manually tracking software versions, identifying vulnerabilities (such as CVE-2017-7921, CVE-2017-2871, and CVE-2020-6852), and applying patches across such a fragmented landscape is not only inefficient but also leaves room for errors and security gaps.
This is where automation becomes essential, using tools compatible with different IoT devices in your environment. Platforms like SecuriThings, a platform that manages, automates, and secures your physical security infrastructure, can help you streamline this process by automatically communicating with various IoT devices, verifying their operating system status, checking for known bugs or Common Vulnerabilities and Exposures (CVEs), and initiating or scheduling patches and upgrades when necessary. The figure below shows a sample dashboard to automate the upgrade process for IoT devices.
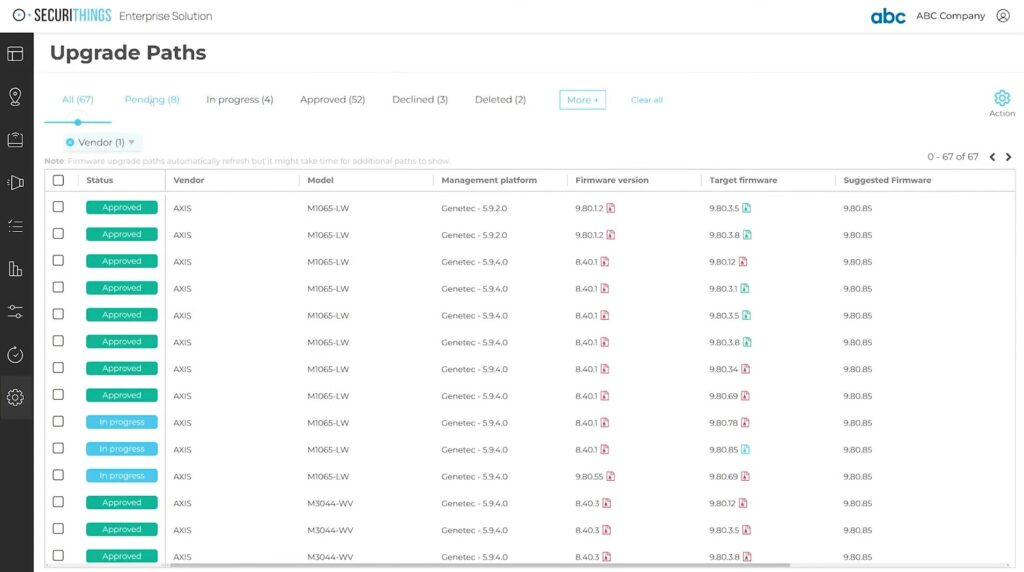
SecuriThings firmware upgrade dashboard (source)
Limited support for security features
As IoT devices continue to be deployed in mass quantities, many manufacturers and organizations aim to reduce the cost of IoT deployments by manufacturing or deploying cheaper IoT devices that lack enough processing power, memory, and energy to run advanced security features or protocols. While this approach makes large-scale deployment more affordable, it often comes at the expense of critical security features, making these devices far more vulnerable than traditional IT assets within your network.
To address this risk, enforcing a policy that ensures only IoT devices meeting your organization’s minimum-security requirements are approved for deployment is essential. Additionally, compensating controls should be implemented in the network segments hosting these devices.
Examples of additional security controls that can be applied include:
- Segmentation with Next Generation Firewalls (NGFW) between segments. For example, placing IoT devices or each group of IoT devices in separate VLANs with an advanced Next-Generation Firewall (NGFW) as the only device connecting them. You can apply deep packet inspection and advanced IDS/IPS (Intrusion Detection Systems/Intrusion Prevention Systems) features in this NGFW.
- Limit or block any communication between IoT devices within each segment if this is not required for these devices to function. Many WLAN solutions have this feature built into the system, but you must enable it. For wired switches, this may require additional configuration, and VLANs or Private VLANs can be used to achieve per-device segmentation, also known as microsegmentation.
- Network Access Control (NAC), which we discussed above.
- Behaviour Analytics using AI and ML models to detect sophisticated threats that may not match existing signatures or security rules.
- Honeypots or deception systems, which are fake IoT devices that lure attackers to collect more information about them and their strategies.
The figure below explains the concept of segmentation and the architecture of typical network segmentation based on VLAN.
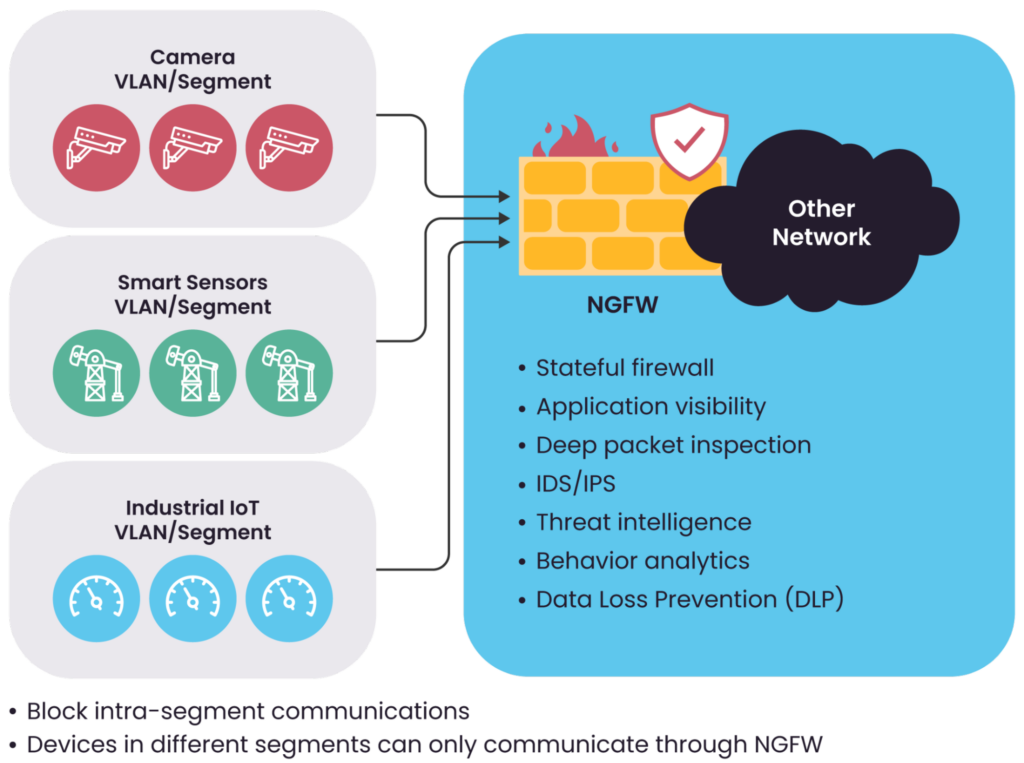
A conceptual overview of network segmentation.
Supply chain security and compliance
IoT devices come from a wide range of manufacturers and often run on specialized or embedded software, which increases the risk of introducing unauthorized hardware or software into your network. This diversity in origin and architecture can create blind spots in your security posture, mainly when devices are sourced without strict vendor vetting. Regulations like the NDAA (National Defense Authorization Act) have specific requirements on hardware components that restrict the use of products from particular vendors. Organizations should use management and monitoring tools to detect any unauthorized or unknown devices and continuously monitor their network to identify any rogue devices or unauthorized components connected to it. Centralised IoT monitoring platforms can help you automate device verification, flag unapproved devices or components, and ensure ongoing compliance with supply chain policies.
Privacy challenges
IoT devices like cameras and access security devices often collect sensitive and personal information, such as video recordings, facial recognition data, and entry logs. This creates significant privacy challenges, particularly when complying with regulations such as GDPR, CCPA, and other data protection laws. Unlike traditional systems, these IoT devices are deployed in remote areas where data may be transmitted over the Internet or unsecured WAN links. Additionally, these devices may lack built-in privacy controls, making it more challenging to manage data access, consent, and retention policies.
When deploying such devices, it’s essential to consider privacy requirements from the outset, ensuring that data collection practices align with regulatory expectations. Hiring a regulatory compliance expert and leveraging specialized tools can help implement the necessary controls and safeguards, reducing the risk of non-compliance and protecting individual privacy across your IoT ecosystem. It’s essential to protect this data in all its states: in transit, at rest, and in use. Implementing data confidentiality techniques like encryption and controlling data access helps ensure that information remains confidential during transmission and storage.
One approach to protecting confidential data in IoT ecosystems is to process information near its source using edge computing. By handling data locally on devices or nearby servers, edge computing reduces the need to transmit sensitive information over WAN links to centralized data centers, thereby minimizing exposure to potential interception or unauthorized access. This localized processing not only enhances data security but also decreases latency, leading to faster decision-making and improved system performance.
The figure below illustrates an example of edge computing and its role in enhancing data privacy by processing confidential data locally. Privacy-preserving techniques, such as masking, anonymization, and homomorphic encryption, can still be applied with edge computing.
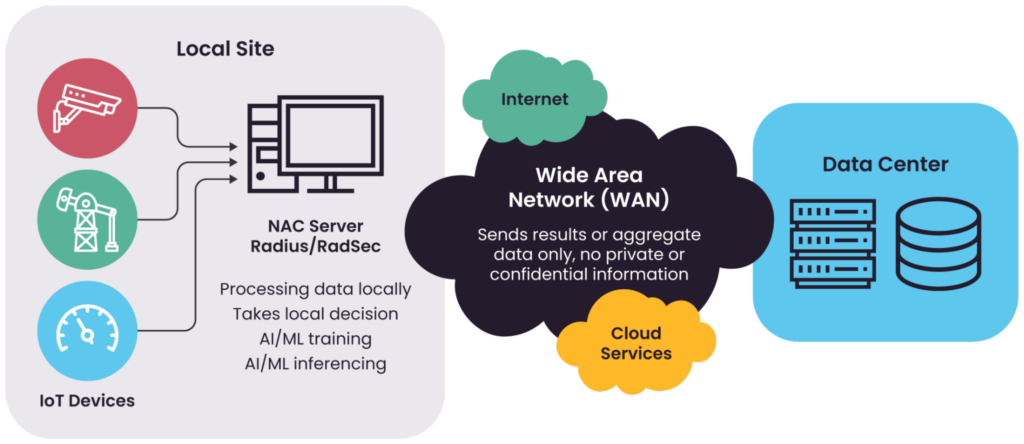
Processing data locally with edge computing
Physical security of IoT devices
IoT devices, such as cameras and sensors, are commonly deployed to enhance physical security and monitor environmental conditions. However, their widespread placement in easily accessible or unsecured locations makes them susceptible to physical tampering. Attackers can exploit this vulnerability to gain unauthorized access, manipulate device functionality, or introduce malicious code into the network.
To mitigate these risks, it’s essential to implement robust physical security measures, including secure mounting, tamper-evident enclosures, and regular inspections. Additionally, integrating these devices into a comprehensive security framework that includes continuous monitoring and anomaly detection can help identify and respond to potential threats promptly. Centralized monitoring platforms can help mitigate this risk by continuously monitoring the availability and integrity of these devices and alerting you when any malicious activity or device failure occurs.
The photos below show examples of tamper-proof IP camera designs and tamper-resistant labels that teams can add to exposed enclosures or IoT devices. Organizations should inspect these labels regularly to ensure that devices are not tampered with.

Tamper-proof IP camera design (Source)
Lack of visibility
IoT devices often originate from various vendors and are introduced into the network by different departments within an organization. This decentralized approach can lead to a fragmented ecosystem, where each department utilizes its own management solutions, thereby challenging the monitoring and control of all devices. The lack of centralized visibility increases the risk of unauthorized devices connecting to the network, potentially exposing the organization to security threats.
To mitigate this risk, teams must deploy a centralized monitoring system that can integrate with the diverse range of IoT devices across their organization and help automate operational tasks. Such a system provides comprehensive visibility and control, enabling efficient management of device configurations, performance, and security status. Additionally, implementing a Network Access Control (NAC) solution enhances security by identifying all devices attempting to connect to the network, ensuring that only authorized devices gain access. This is the basis of the zero-trust concept in cybersecurity.
The figure below shows the main components of a NAC system.
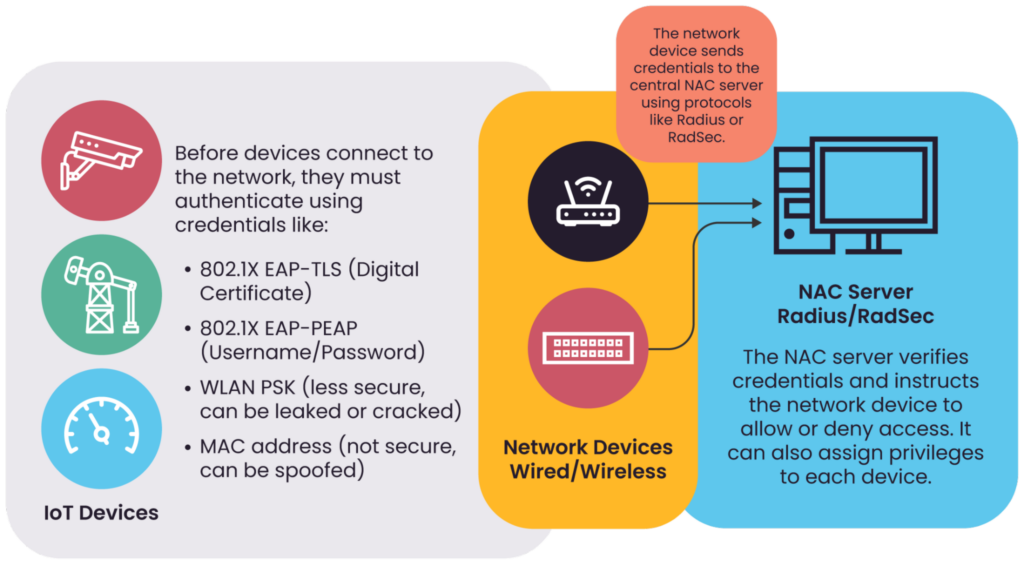
The main components of a Network Access Control system
Lack of standards
The diverse range of IoT device manufacturers and communication protocols makes ensuring consistent security measures increasingly complex. Many IoT devices operate on proprietary protocols and adhere to various architectural designs, leading to a fragmented ecosystem that complicates interoperability and standard security implementations. Risk assessment frameworks and methodologies (such as NIST IR 8259 and MITRE ATT&CK) can support the identification and prioritization of key security risks and attack vectors in IoT environments, enabling more effective evaluation and mitigation strategies.
Furthermore, when integrating these devices into your network, it is crucial to follow security best practices, regardless of their specific protocols or communication methods.
Aim to ensure the following:
- The zero-trust principle is applied. Only trusted devices are allowed to communicate over expected ports.
- Least privilege rules are applied (only required ports are permitted). Apply firewalls or ACLs as close as possible to IoT devices.
- Traffic is encrypted, especially over WAN or untrusted links.
- You have complete visibility into all devices and traffic in your network. NAC systems and NGFW devices can help here.
- Baselines of regular traffic are defined. Baselines enable the identification of any anomalies, and systems can then trigger alerts to report them.
To support organizations in addressing IoT security challenges, the Federal Communications Commission (FCC) has recently adopted rules creating a voluntary cybersecurity labeling program for wireless consumer IoT products. This program introduces the U.S. Cyber Trust Mark, which aims to help consumers make informed purchasing decisions and encourage manufacturers to meet higher cybersecurity standards. This labeling program can help IT and procurement departments select IoT devices that meet minimum security requirements, regardless of the manufacturer or protocol.

Labels recommended by the FCC. (Source)
Compliance with standards and regulations
Ensuring compliance with established standards and regulations is crucial for organizations that handle sensitive data. Regulatory and standard frameworks, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), and guidelines from the National Institute of Standards and Technology (NIST), set stringent requirements to protect personal and financial information. Failure to adhere to these standards can result in severe legal penalties and significant reputational damage.
Organizations should stay informed about relevant industry regulations to maintain compliance and implement security controls that align with these requirements. If you work in an industry where compliance with specific rules or standards is required, it is advisable to hire an expert to help achieve and verify this compliance.
Device management solutions, like SecuriThings, help you apply security rules and controls at scale, a fundamental step in any compliance process. Additionally, SecuriThings provides you with the necessary logs and audit trails to verify compliance and trace any anomalies or incidents as part of the compliance verification and audit process.
Compliance with standards and regulations
Ensuring compliance with established standards and regulations is crucial for organizations that handle sensitive data. Regulatory and standard frameworks, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI-DSS), and guidelines from the National Institute of Standards and Technology (NIST), set stringent requirements to protect personal and financial information. Failure to adhere to these standards can result in severe legal penalties and significant reputational damage.
Organizations should stay informed about relevant industry regulations to maintain compliance and implement security controls that align with these requirements. If you work in an industry where compliance with specific rules or standards is required, it is advisable to hire an expert to help achieve and verify this compliance.
Device management solutions, like SecuriThings, help you apply security rules and controls at scale, a fundamental step in any compliance process. Additionally, SecuriThings provides you with the necessary logs and audit trails to verify compliance and trace any anomalies or incidents as part of the compliance verification and audit process.
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Last thoughts
Organizations face escalating IoT security challenges as the use of smart devices continues to expand. Some of these challenges stem from the limited capabilities of many IoT systems, which often lack robust security features such as strong authentication mechanisms and encryption protocols. Others arise from the complexity of managing and securing various devices from different manufacturers, each with its own firmware and communication standards. This diversity can lead to compatibility issues and difficulties implementing uniform security policies across all devices.
Addressing these challenges requires a multifaceted approach. Organizations should prioritize deploying devices that support essential security features and ensure that all devices are regularly updated with the latest firmware to mitigate known vulnerabilities. Centralized management platforms can streamline the oversight of diverse IoT devices, enabling consistent application of security policies and timely responses to potential threats. SecuriThings addresses these challenges by providing a unified platform for automating the operational management of IoT devices at scale. It enables real-time monitoring, automates maintenance tasks such as firmware upgrades and password rotations, and ensures compliance with organizational policies. This centralized approach simplifies the management of diverse devices, enhances security, and reduces the operational burden on IT teams.