IoT Security Standards Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
The rapid growth of IoT devices has improved convenience and efficiency across sectors. However, it has also increased the attack surface for hackers and attackers, and infamous incidents, like the Matrix Botnet attack, make customers rightfully apprehensive about IoT.
One way to build customer trust is to demonstrate that your IoT devices comply with established security standards. This indicates to customers that the devices were developed with security in mind, and the definition of security was established by a third party, typically a consortium or government body, with the customer’s best interests in mind. Complying with IoT security standards also eases the development process, as certain decisions, such as chipset and communication protocol selection, become easier to make as the choices narrow.
This article offers a practical overview of key IoT security standards, compares their features, and helps you choose the right one based on your use case. It also outlines steps for achieving IoT compliance and securing devices throughout their lifecycle.
Summary of key IoT security standards concepts
The table below summarizes the IoT security standards concepts this article will explore in more detail.
| Concept | Description |
|---|---|
| Major IoT security standards | ISO/IEC 27400:2022 is the most comprehensive standard on IoT security, but depending on your region of interest, standards like NIST for the USA or ETSI for the EU region may be applicable. These standards cover almost all aspects that affect the security across the lifecycle of the device, including authentication, communication, updates, physical security and a lot more. |
| Which IoT security standard to comply with? | Your industry, region of interest, legal and regulatory frameworks, and customer preferences largely dictate the list of standards applicable to you. |
| How to achieve compliance and implement controls for IoT devices? | The key steps include performing a gap assessment, outlining gap-filling options, testing and validation, documentation, engagement with a certification body, and implementing lifecycle controls. |
Monitor the health of physical IoT devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports
IoT security management



Major IoT security standards
There are several IoT security standards. However, covering all of them wouldn’t be possible within the scope of this article. Considering their scope and sector coverage, we will examine the major ones. The most comprehensive standard for IoT across cyber and physical security dimensions is the ISO/IEC 27400:2022. If you are a developer based in the US, it will be worthwhile to comply with the NIST standards. These are strong on core device capabilities but less hardware-focused. However, their lack of hardware focus can be addressed by FIPS 140-3. A standard very popular among developers is the OWASP IoT Top 10. It should be noted that this is a risk-focused standard that is great for design and testing awareness, but it is not certifiable. Nevertheless, they are great for developers to perform self-assessments and corrections.
The two tables below provide a comprehensive overview of these significant standards. The first table outlines each standard’s scope, target region, and target sector, while the second table highlights major IoT security features (e.g., securing firmware updates) relevant to each standard.
| Standard | Publisher | Scope | Certification Path Available? | Cybersecurity | Physical Security | Region | Target Sector |
|---|---|---|---|---|---|---|---|
| ISO/IEC 27400:2022 | ISO / IEC | General IoT security and privacy | Not certifiable directly | Covered | Covered | Global | Cross-sector (generic IoT) |
| NIST IR 8259 Series | NIST (U.S.) | Core IoT cybersecurity capabilities | No (guidelines only) | Covered | Partially Covered | U.S. | Government, industry |
| NIST SP 800-213 | NIST (U.S.) | IoT integration into federal systems | No (guidelines only) | Covered | Covered (integration & resilience) | U.S. | Federal IoT systems |
| FIPS 140-3 | NIST (U.S.) | Cryptographic modules | Yes (Cryptographic Module Validation Program – CMVP) | Covered | Covered (tamper evidence, coatings) | U.S. | Government, healthcare, finance |
| ETSI EN 303 645 | ETSI (EU) | Baseline consumer IoT security | Yes (via EN 303 645 assessments like IASME) | Covered | Partially Covered (port hardening) | EU | Consumer IoT |
| UL 2900 Series | UL | Cybersecurity for connected devices | Yes (UL cybersecurity certification) | Covered | Partially Covered (port/interface review) | Global | Medical, industrial, smart home |
| Common Criteria (EAL) | ISO / IEC 15408 | Security assurance for IT products | Yes (Evaluation Assurance Levels) | Covered | Covered (tamper, hardware) | Global | Embedded, critical infrastructure |
| OWASP IoT Top 10 | OWASP | Security risk awareness | No (awareness tool) | Covered | Not Covered | Global | Developer education, assessments |
| CSA IoT Controls Framework | Cloud Security Alliance | IoT cloud-connected devices | No (used for self-assessment) | Covered | Partially Covered (physical interfaces) | Global | Cloud-integrated IoT systems |
As you can see from the above table, all standards cover aspects related to cybersecurity. However, more and more standards are covering physical security aspects as well.
| Feature | ISO/IEC 27400 | NIST IR 8259 / SP 800-213 | ETSI EN 303 645 | UL 2900 | FIPS 140-3 | OWASP IoT Top 10 | CSA IoT Framework |
|---|---|---|---|---|---|---|---|
| Authentication & Identity Management | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Encryption of Data (at rest/in transit) | Yes | Yes | Yes | Yes | Strong | Partial | Yes |
| Secure Software/Firmware Updates | Yes | Yes | Yes | Yes | No | Yes | Yes |
| Access Control Mechanisms | Yes | Yes | Yes | Yes | Indirect | Yes | Yes |
| Vulnerability Disclosure Policies | Yes | Yes | Required | Yes | No | Yes | Yes |
| Physical Security / Tamper Protection | Yes | Partial | Minimal | Partial | Strong | No | Partial |
| Logging & Auditing | Yes | Yes | Optional | Yes | No | Partial | Yes |
| Security by Design / Lifecycle Approach | Strong | Yes | Yes | Yes | No | Partial | Yes |
| Default Password Elimination | Yes | Yes | Required | Yes | No | Yes | Yes |
| Third-Party Integration & Compliance | Yes | Yes | Yes | Yes | Yes | No | Yes |
The above tables include three types of standards from NIST: SP, IR, and FIPS. NIST SPs and IRs are not formal standards, but they provide authoritative guidance and are often used like standards, particularly in U.S. Federal and critical infrastructure contexts. Here is a brief explainer of the three types of NIST standards:
- SP (Special Publication): Detailed guidance, best practices, or frameworks; widely used across industries. These can be used when structured implementation guidance is needed.
- IR (Interagency Reports): Early research, draft work, or supporting material for SPs or federal programs. These can be used when exploring emerging best practices.
- FIPS (Federal Information Processing Standard): U.S. federal mandatory standard. These need to be used when developing products and services for the U.S. government.
Standard vs. Regulation
You may have noticed significant regulations like HIPAA and GDPR were missing from the lists above. The omission was deliberate because these are regulations not standards. A standard provides best practices, and compliance is typically voluntary, whereas a regulation is legally enforced, and you must compulsorily meet its requirements.
A regulation often has high-level legal language, whereas the standard lists detailed technical controls, protocols, and requirements. Suppose you are building a medical IoT device; then HIPAA requires you to protect customer data, and NIST or ISO standards provide guidance on how to do so securely.
Which IoT security standard to comply with?
The answer to this question typically depends on the following factors:
- Your industry and use case.
- The region where you operate and sell.
- Legal and regulatory frameworks.
- Customer preferences.
For example, if you are operating in the US in the healthcare space, you will have to adhere to the HIPAA regulation, which, in turn, will redirect you to the NIST or ISO standards. If you sell to the US federal government, the FIPS standard will apply to your devices. Even though you are creating IoT devices, it may be worthwhile to comply with widespread standards in your industry before IoT adoption starts. For example, the ISO 26262 standard for the functional safety of electrical and electronic systems is not exclusive to IoT devices, but it may still be worthwhile to comply with.
The table below provides practical examples of selecting the standards that apply to you, categorized by region and industry. Please note that the table is not comprehensive, and you should conduct your own search for information specific to your industry and region.
| Industry | Recommended Standards | Region |
|---|---|---|
| Healthcare | – HIPAA (regulation)
– FIPS 140-3 |
USA (HIPAA, NIST), Global (ISO, FIPS) |
| Consumer Devices | – ETSI EN 303 645
– OWASP IoT Top 10 – ISO/IEC 27400 – UL 2900 |
EU (ETSI), Global (ISO, OWASP), USA (UL) |
| Industrial / OT | – IEC 62443
– NIST IR 8259 – Common Criteria |
Global (IEC, ISO), USA (NIST), Global (CC) |
| Automotive | – ISO/SAE 21434
– ISO/IEC 27400 |
Global (ISO/SAE) |
| Smart Cities | – NIST Smart City Framework
– CSA IoT Framework |
USA (NIST), Global (ISO, CSA) |
| Finance / Payments | – PCI DSS
– ISO/IEC 27001 – FIPS 140-3 |
Global (PCI, ISO), USA (FIPS) |
| Government / Military | – NIST SP 800-series
– FIPS 140-3 – Common Criteria |
USA (NIST, FIPS), Global (CC) |
| Electric Utility/ Smart Grid | – NERC CIP
– ISO/IEC 27001 – IEC 62443 |
USA, Canada, Parts of Mexico |
If you operate in an industry with high consumer awareness of standards, consider selecting standards that have a certification path. For example, many organizations follow ISO/IEC 27001 or UL 2900, as they have well-defined certification paths. If consumer awareness is low and having the certification is not a differentiator or an unwritten requirement, complying with directional standards like OWASP IoT Top 10 may be sufficient.
If you are a customer of IoT devices, please note that physical security devices, such as IP cameras, biometrics-based access control, and intruder alarms, are also considered IoT devices and should be taken into account when selecting the standards applicable to you and designing your control plan.
How to achieve compliance and implement controls for IoT devices?
Once you have understood the standards or regulations that apply to you, the next steps are as follows:
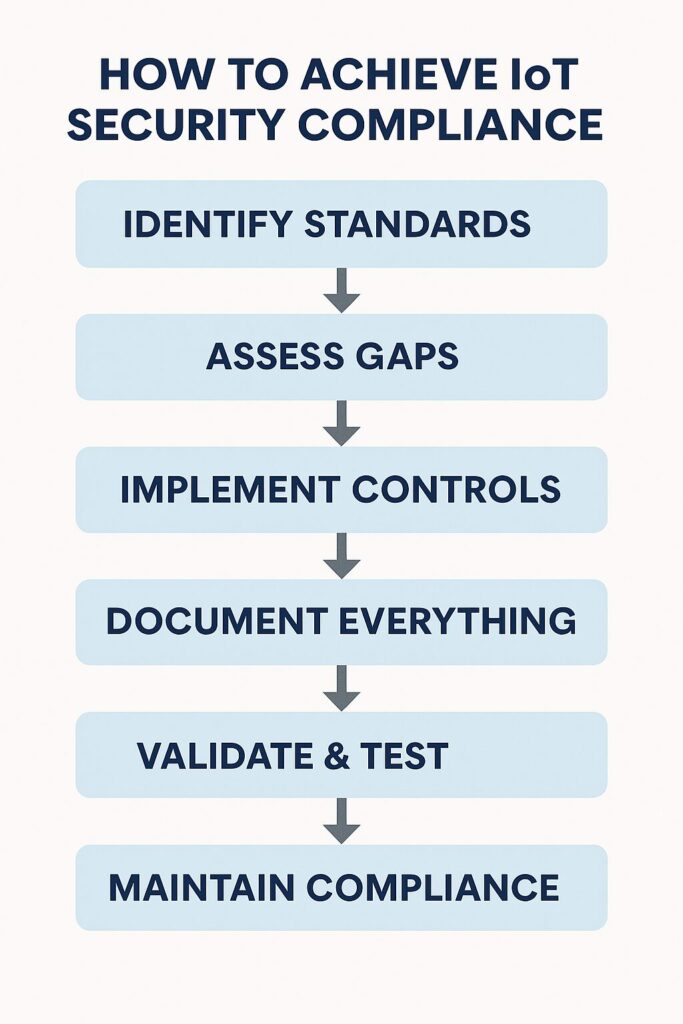
An overview of the steps required to achieve compliance with IoT security standards.
1. Perform gap assessment: Check if your current practices, architecture, and protocols meet the standard’s requirements. For example, a quick read-up of any standard could pop up the following questions:
-
- Do you use default credentials?
- Are software updates cryptographically signed and authenticated?
- Do you have incident response and vulnerability disclosure policies?
- Is sensitive data encrypted in transit and at rest?
- Are there controls for physical tampering or access?
2. Map out and implement gap-filling options: Once the relevant questions have been asked, the next step is to populate suitable answers against each question. Thus, you could be developing a control plan that looks similar to the plan below:
| Control Area | Example Implementation |
|---|---|
| Authentication | Mutual TLS, OAuth2, X.509 certificates |
| Encryption | AES-256 for storage, TLS 1.3 for transmission |
| Secure Boot | Verified bootloader with signed firmware |
| Update Mechanism | OTA updates with rollback protection and integrity checks |
| Access Control | Role-based access, least privilege, time-bound device access tokens |
| Monitoring & Logging | Central log aggregation, tamper-proof audit trails |
| Physical Security | Tamper detection, secure enclosures, secure debug ports |
| Privacy Controls | Data minimization, anonymization, user consent |
3. Conduct testing and validation: Once development is complete, test your device or platform. Testing can be conducted in-house or through a third-party provider. If done in-house, organizations should ensure that developers and testers remain independent to avoid conflicts of interest. Testing by an approved laboratory is required for certifications such as UL 2900 or ETSI conformance.
4. Document everything: From conceptualization to implementation to testing, document all the steps, ideas, algorithms, and protocols. A non-comprehensive list of what you can document is given below:
- Policies & Procedures (e.g., incident response, access control)
- Asset Inventory (devices, firmware, data flows)
- Risk Assessment & Mitigation Plans
- Audit Logs & Security Testing Reports
- Third-party agreements and supply chain assurances
5. Engage with a certification body (if required): For standards with a certification path:
- Choose an accredited body (e.g., UL lab, Common Criteria scheme)
- Submit the required documentation
- Go through the audit or evaluation
- Address any non-conformities
6. Lifecycle controls: Whether you are a developer or a customer, compliance with standards is not a one-time activity. It requires constant work throughout the device’s lifecycle. Monitoring devices and alerting when anyone crosses a threshold, conducting regular audits, managing patches, providing periodic training for developers and operators, and upgrading compliance as standards evolve are just some of the activities that fall within the purview of lifecycle controls.
Beyond a certain scale, enterprise device management platforms, like SecuriThings, become essential for effectively performing IoT compliance checks. Such platforms can perform device discovery, monitoring, patch updates, password rotation, access management, and a lot more that can help you achieve compliance throughout the IoT lifecycle.
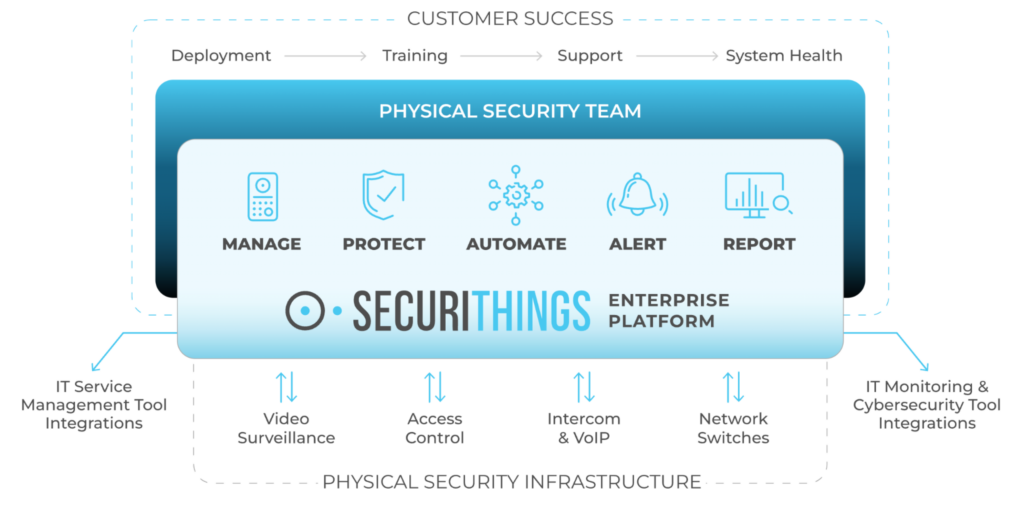
SecuriThings capabilities. (Source)
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Conclusion
IoT security standards facilitate development and purchasing decisions, ensuring that basic security measures are in place to address common and known threats. The first step toward compliance is identifying the standards applicable to you, depending on your industry, geography, and customer preferences. Furthermore, teams must take measures during development and throughout the device or platform’s lifecycle to ensure compliance is consistently maintained. For your lifecycle needs, consider platforms like SecuriThings.