SSL Certificate for IoT Devices Best Practices
- Chapter 1: IoT Security Best Practices
- Chapter 2: IoT Network Security
- Chapter 3: IoT Security Challenges and Best Practices
- Chapter 4: IoT Security Standards Best Practices
- Chapter 5: Enterprise IoT Security Best Practices
- Chapter 6: SSL Certificate for IoT Devices Best Practices
- Chapter 7: Best Practices for IoT Vulnerabilities
The rapid growth of IoT devices, ranging from smart thermostats and security cameras to industrial sensors and medical equipment, has introduced a new and growing security challenge. These devices often operate with limited resources, weak default settings, and poor patching mechanisms, making them prime targets for attackers.
A single compromised IoT device can open the door to devastating consequences. In the infamous Mirai botnet attack, hackers took control of thousands of IoT devices and launched massive DDoS attacks, disrupting major websites like Twitter and Netflix. More recently, research by Unit 42 at Palo Alto Networks has shown that nearly 57% of IoT devices are vulnerable to medium- or high-severity attacks, threatening personal privacy and corporate networks.
To protect organizations from these risks, two security pillars are essential:
- Authenticating the identity of IoT devices to ensure that only trusted devices can connect and interact.
- Encrypting data in transit to prevent attackers from intercepting or tampering with confidential communications.
These two pillars are where an SSL/TLS certificate for IoT devices plays a key role. When properly managed, these certificates provide a secure foundation for device authentication and encrypted communication.
This article explores how SSL/TLS certificates for IoT devices can secure your IoT deployments. It covers certificate types, Public Key Infrastructure (PKI), certificate issuance and revocation, and best practices for secure certificate storage on devices to ensure a resilient IoT infrastructure in a connected world.
Summary of key concepts on SSL certificate for IoT devices
The table below summarizes key concepts related to SSL certificates for IoT devices that this article will explore in more detail.
| Concept | Description |
|---|---|
| PKI (Public Key Infrastructure) | A framework that manages digital certificates and encryption keys to secure communication and verify identities. |
| Key pair: public key and private key | The public key is shared openly and is used to encrypt data or verify digital signatures. The private key is kept secret and is used to decrypt data or create digital signatures. Together, they enable secure communication and identity verification without sharing secrets. |
| Use strong key lengths | Ensure RSA keys are at least 2048 bits or use ECC (e.g., secp256r1) for better security and speed. |
| Enable mutual authentication | Require both the server and the client (IoT device) to present valid certificates for mutual authentication. |
| Use short certificate lifetimes | Short-lived certificates reduce exposure if a key is compromised. Identity & Access: Internet Giants Agree to Reduce TLS Certificate Lifespan to 47 Days by 2029 |
| Automate certificate issuance | Use automation protocols (such as SCEP, EST, or ACME protocol) to avoid manual errors and delays. |
| Certificate life cycle management | Use a Centralized Certificate Authority (CA) and Automate Certificate Issuance and Renewal. |
| Secure private key storage | Store private keys in secure elements, TPMs, or hardware security modules (HSMs) to prevent theft. |
| Rotate certificates regularly | Rotate or renew certificates before they expire to maintain secure, uninterrupted connections. |
| Revoke compromised certificates | Use CRLs or OCSP to revoke and check the status of certificates that are no longer trusted. |
| Use trusted Certificate Authorities (CAs) | Issue certificates only from reputable internal or external CAs to ensure devices trust each other. |
| Log and monitor certificate use | Track where and how certificates are used to detect anomalies and prevent misuse. |
Monitor the health of physical IoT devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports
IoT security management



Public Key Infrastructure (PKI)
In the fields of cryptography and cybersecurity, encryption, key exchange, and trust are essential building blocks for protecting data confidentiality. These elements support the widely recognized CIA triad—Confidentiality, Integrity, and Availability—which forms the foundation of cybersecurity principles.
To establish trust across digital communications, the internet relies on a model called Public Key Infrastructure (PKI). An SSL certificate for IoT devices depends on this proven model.
PKI is built around a hierarchical “chain of trust” that connects digital certificates and signatures from a trusted root authority down to end-user devices. This structure enables verification of identities and secure communication channels.
At the core of PKI is asymmetric encryption, which involves two keys: a public key that can be shared freely and a private key that remains confidential. Data encrypted with the public key can only be decrypted using the corresponding private key.
Here’s how the process works in an IoT context:
- The IoT device wants to send data to the server securely. The server has a unique key pair, consisting of a publicly accessible public key and a securely stored private key.
- During the TLS handshake, the IoT device verifies the server’s identity by checking its digital certificate. Once verified, the device uses the server’s public key to securely encrypt and exchange information needed to generate a shared session key.
- Only the server can decrypt the message using its private key, which is never shared. This guarantees that the data remains confidential and is only accessible to its intended recipient.
- Once both sides have derived the same symmetric session key, they switch to symmetric encryption (e.g., AES) for the remainder of the session. This approach is significantly faster and less resource-intensive than asymmetric encryption, which is important for performance, especially in constrained IoT environments.
- From this point forward, all data exchanged between the IoT device and the server is encrypted using the agreed-upon symmetric key, ensuring confidentiality and integrity throughout the session.
This method ensures secure communication over public or untrusted networks, maintaining the integrity and privacy of the data throughout its journey. The process of using the private and public keys to encrypt the data or the session key is explained in the diagram below.
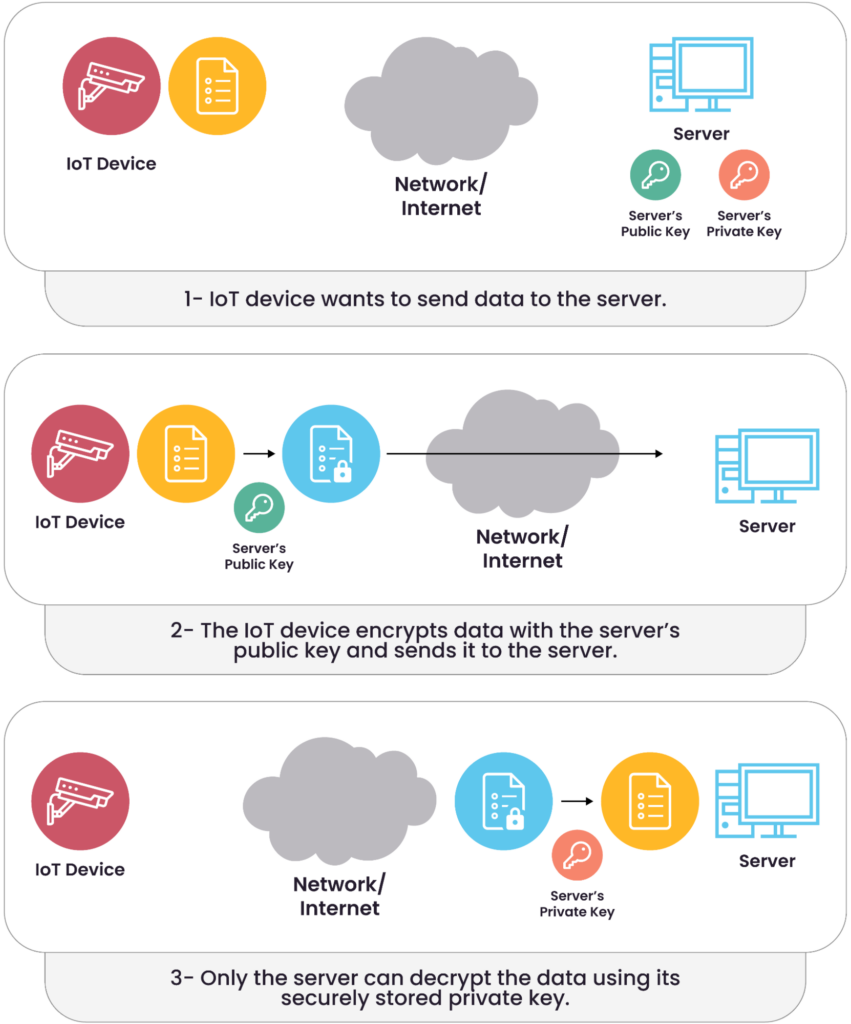
Using a key pair to encrypt data
Public and private key pairs are also essential for creating digital signatures, which offer authentication, message integrity, and non-repudiation in secure communications. A digital signature works by having the sender sign the message using their private key, while the recipient uses the sender’s public key to verify the signature. This guarantees that the message truly originated from the claimed sender and hasn’t been altered in transit.
Here’s how the digital signature process typically unfolds:
- Node-A computes a hash (a fixed-length summary) of the message.
- It then encrypts this hash using its private key, creating the digital signature.
- The original message and the signature are sent to Node-B over the network.
- Node-B receives the message and re-generates the hash from it.
- It then decrypts the digital signature using Node-A’s public key, retrieving the original hash.
- If the two hashes are identical, Node-B confirms that the message is authentic and has not been tampered with.
This mechanism ensures trust in both the origin and the integrity of the message, even when communicating over untrusted networks.
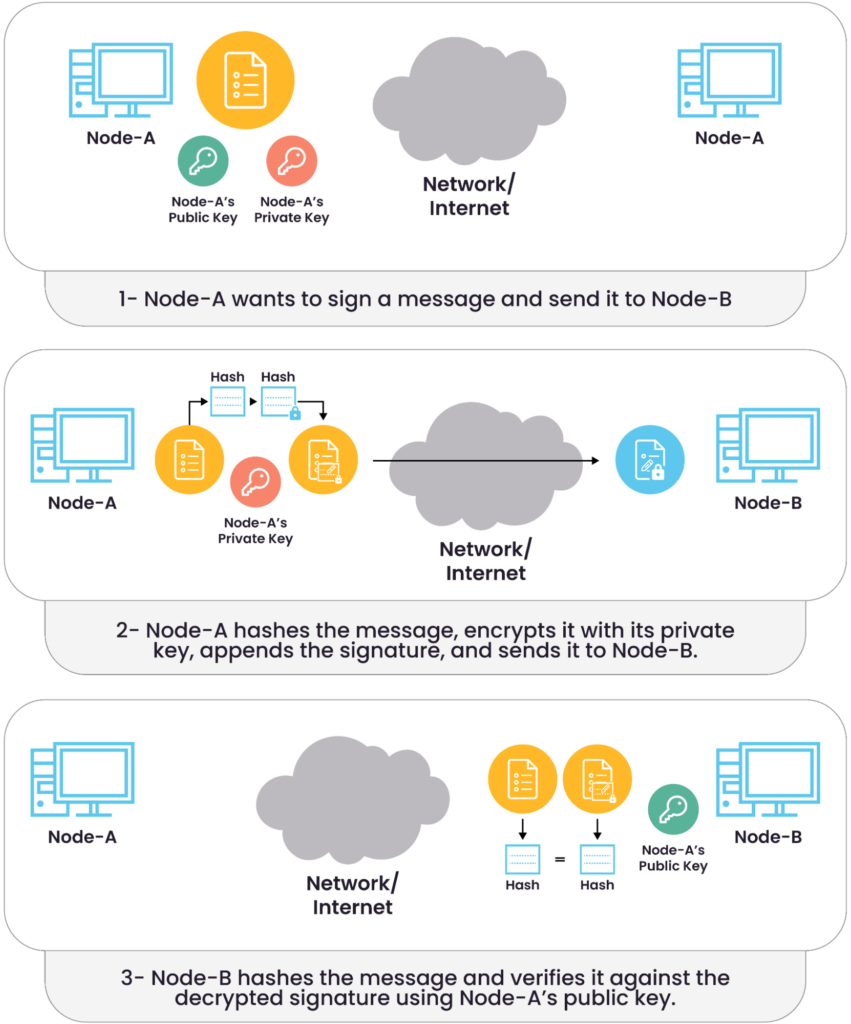
Using a key pair to sign messages.
Digital signatures are used for authentication via CAs (we will review CAs in a subsequent section):
- The Root CA issues a digital certificate and signs it using its private key.
- When a device (like an IoT sensor) presents its certificate to a server:
- The server checks the digital signature on the certificate.
- It uses the Root CA’s public key (already trusted and stored on the system) to verify that the certificate was indeed signed by the legitimate CA.
- If the verification succeeds:
- The certificate is trusted.
- The device’s identity is considered authentic.
Certificate-based authentication methods, like EAP-TLS, depend on certificates, CAs, a chain of trust, and signed certificates to verify the identity of IoT devices before allowing them into the network. These concepts will be discussed in more detail in the coming sections.
Secure private key storage
Protecting the private key is critical to maintaining the integrity of SSL certificate-based authentication. If a private key is stolen or exposed, attackers can impersonate the device, decrypt traffic, or forge digital signatures. To prevent this, keys should never be stored in plain text or exposed in software memory.
Hardware-based solutions like Trusted Platform Modules (TPMs) and Hardware Security Modules (HSMs) provide robust protection by generating and storing keys in tamper-resistant environments. TPMs are often embedded in the device and offer a cost-effective layer of protection for endpoint security. HSMs are external or network-attached appliances designed for centralized key management at scale, offering strong isolation and compliance-grade security.
However, in many IoT devices, hardware modules may not be available. In such cases, software-based techniques such as encrypted key stores or operating system-level key isolation like Secure Enclaves or TrustZone, can be used, though they offer less protection against physical threats and attacks against IoT firmware.
Certificate Authorities
Certificate Authorities (CAs) are the backbone of trust in a Public Key Infrastructure (PKI). They issue and digitally sign certificates that verify the identity of devices, servers, or users. In doing so, they act as a trusted third party, vouching that the entity holding the certificate is legitimate. This process is essential for establishing secure communication in IoT environments, where devices often operate autonomously and at scale. By validating each device’s certificate, organizations can prevent unauthorized access and reduce the risk of spoofed or rogue devices.
The trust model typically starts with a Root CA, which is trusted by operating systems, browsers, and devices. To enhance security and scalability, Root CAs often delegate responsibilities to Intermediate CAs, which may further pass signing authority to Issuing CAs. This layered structure forms a hierarchical “chain of trust” where each certificate is validated by the authority above it. In IoT deployments, this model is especially valuable for managing thousands of certificates in a scalable and auditable way.
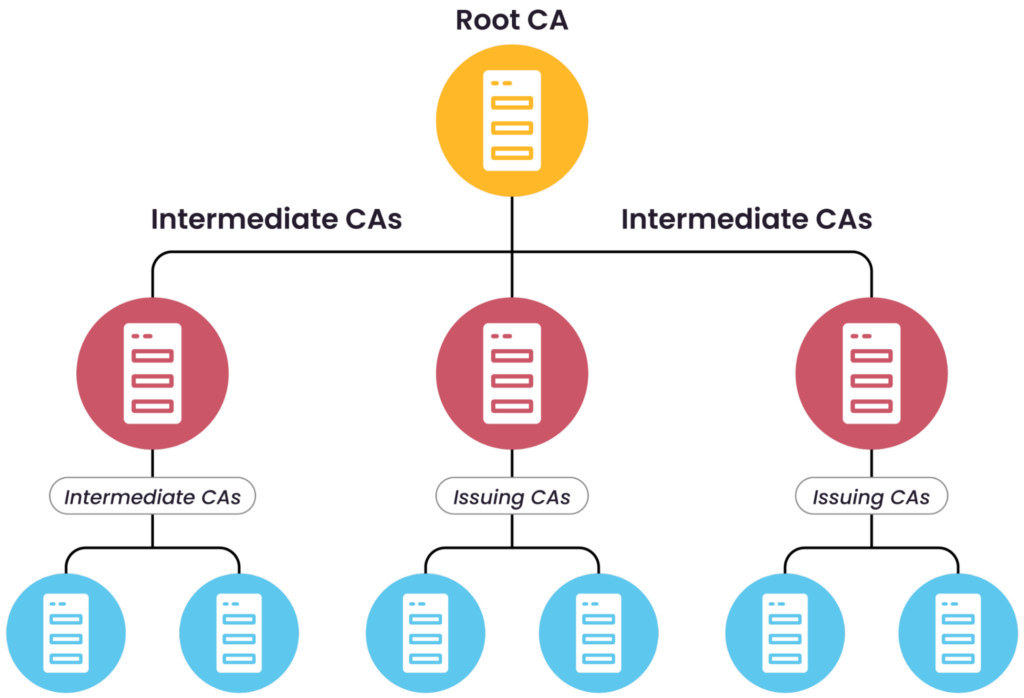
Chain of trust starting with a root CA. (Source)
Organizations may choose to use a private CA hierarchy—often including both intermediate and issuing CAs—for full control over device identities and lifecycles, or opt for public CAs when global trust and interoperability are required. Securing the private keys of all CA levels is critical, as any breach could compromise the entire ecosystem.
| CA Type | Description | Example Use Case |
|---|---|---|
| Root CA | Highest trust anchor; directly trusted by systems | Embedded in OS, browsers, or IoT firmware |
| Intermediate CA | Acts as a bridge between Root and Issuing CA; adds isolation and flexibility | Delegated trust inside an organization |
| Issuing CA | Directly signs end-entity certificates (e.g., IoT device certs) | Daily certificate operations in IoT systems |
| Private CA | Internally managed CA structure for custom device identity control | Enterprise IoT, manufacturing |
| Public CA | Trusted third-party CA used for wide compatibility | Consumer smart devices, third-party APIs |
Organizations can have an SSL certificate for IoT devices issued using one of the options below:
- Manufacturer Root CA: Devices come preloaded with manufacturer-signed certificates used for initial authentication and onboarding.
- Private Root CA: Organizations issue and manage certificates internally, offering control, scalability, and policy enforcement.
- Public Root CA: Rare in IoT due to high cost and limited flexibility, typically used for consumer devices requiring global trust, like public websites or services.
Key length
Key length is a fundamental factor in determining the strength of cryptographic algorithms used to secure communication between IoT devices and servers. Longer keys generally offer stronger security by making it more difficult for attackers to break the encryption through brute-force methods. One of the most widely used algorithms is RSA (Rivest–Shamir–Adleman), which relies on the mathematical difficulty of factoring large prime numbers. However, RSA’s security depends heavily on key size—2048-bit keys are currently considered the minimum for secure communication, while 3072- or 4096-bit keys offer greater protection but require significantly more processing power and memory. This makes them less suitable for IoT devices, which often have limited computational resources and power constraints.
In contrast, Elliptic Curve Cryptography (ECC) provides a more efficient and modern approach. ECC achieves equivalent security with much shorter key lengths by leveraging the complexity of elliptic curve equations.
For example, a 256-bit ECC key (such as secp256r1) offers a security level roughly equal to a 3072-bit RSA key, but with far less impact on performance and resource usage. This efficiency is particularly valuable in IoT environments, where devices may run on battery power, operate in real-time, or use minimal hardware.
ECC also results in smaller certificates and faster cryptographic operations, making it the preferred choice for securing communications in constrained devices. As the IoT ecosystem scales, using ECC can reduce bandwidth, improve speed, and support longer device lifespans without compromising security.
Mutual authentication
Mutual authentication is the process where both the IoT device and the authentication server verify each other’s identities before exchanging sensitive data. Typically, the process begins with the device validating the server’s digital certificate, ensuring it is communicating with a trusted and authorized endpoint. Only after this verification does the device present its own certificate for authentication. This order is critical in preventing attacks like Man-in-the-Middle (MITM), where an attacker could impersonate a legitimate server to intercept or manipulate communication.
Mutual authentication, often implemented through protocols like EAP-TLS which is part of 802.1X protocol, protects against rogue networks and unauthorized devices by requiring both parties to prove their identities using certificates issued by a trusted CA. In large-scale IoT environments, this two-way trust mechanism is essential for maintaining secure, encrypted communications and ensuring only approved devices can connect to the network.
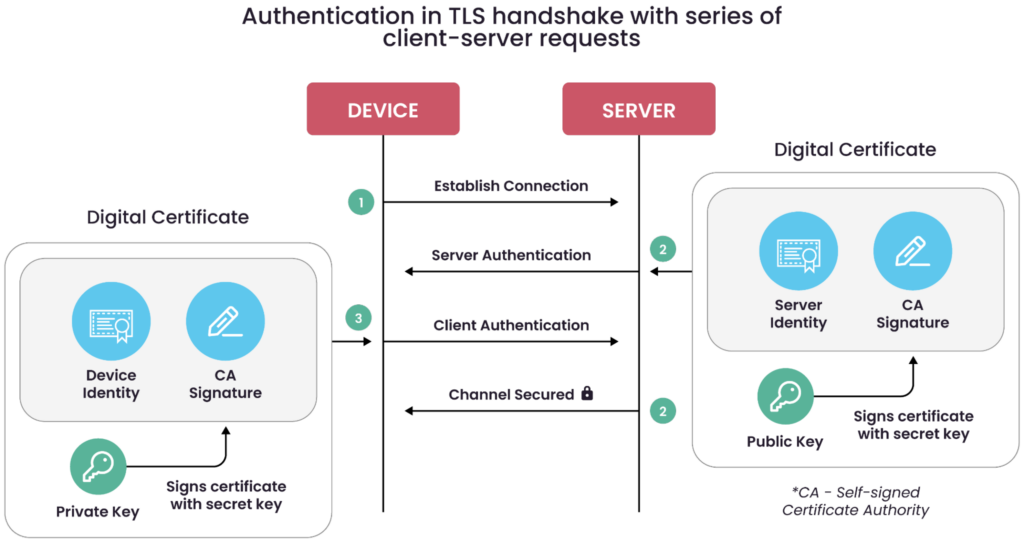
A logical overview of mutual authentication. (Source)
Certificate expiry date
Digital certificates have a defined expiration date, which is determined at the time of issuance by the CA. The validity period is typically configured as part of a certificate template or policy, which dictates how long a certificate remains trusted before it must be renewed. This expiration mechanism is essential for maintaining cryptographic hygiene and ensuring outdated or potentially compromised credentials are no longer accepted.
One growing trend is the use of short-lived certificates, which reduce the window of risk in the event a private key is compromised. Instead of relying heavily on revocation mechanisms like CRLs or OCSP (discussed in the next section), short-lived certificates naturally expire quickly, which limits their usefulness to an attacker. Reflecting this best practice, major tech companies have committed to reducing the maximum lifespan of public TLS certificates to 47 days by 2029, emphasizing the shift toward tighter control of digital identities.
To avoid service interruptions, organizations must ensure that certificates are renewed before their expiration date, ideally using automated renewal systems. Manual tracking and replacement can be error-prone and unmanageable, especially in IoT environments with thousands of devices. Leveraging protocols like EST, ACME, or SCEP allows for seamless, policy-driven certificate renewal and replacement, ensuring continuous authentication and secure communication across the IoT ecosystem.
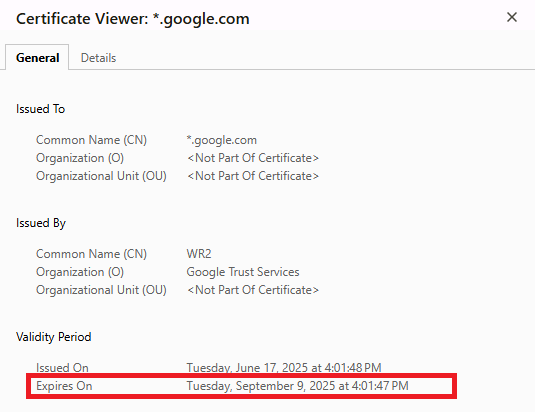
An example of a certificate expiry date.
Certificate revocation and verification
Certificate revocation and verification are essential components of a secure certificate management strategy. Even after a certificate is issued, there are cases where it must be invalidated before its expiration date, such as when a device is compromised, its private key is exposed, or it is decommissioned. This process is called certificate revocation. Once a certificate is revoked, it should no longer be trusted by any system. To enforce this, systems must perform certificate status verification, which ensures that a certificate is still valid at the time of use.
The two most common methods for this are the Certificate Revocation List (CRL) and the Online Certificate Status Protocol (OCSP).
- A CRL is a periodically published list of serial numbers of revoked certificates issued by a CA. Clients must download and cache the list, which can grow large and become outdated between updates.
- OCSP, on the other hand, allows clients to check the revocation status of a specific certificate in real time by querying an OCSP responder. While OCSP offers faster and more dynamic checks, it introduces reliance on online availability and the responsiveness of the OCSP server.
In IoT environments, where connectivity might be intermittent or constrained, choosing the right revocation method involves balancing performance, scalability, and real-time security requirements. The table below compares CRL and OCSP for certificate revocation.
| Feature | CRL (Certificate Revocation List) | OCSP (Online Certificate Status Protocol) |
|---|---|---|
| Mechanism | Downloads a full list of revoked certificates from the CA | Queries the CA or responder for status of a single certificate |
| Latency | Slower – must parse large lists, especially in big deployments | Faster – real-time validation of individual certificates |
| Bandwidth Usage | High – entire list is downloaded and stored locally | Low – only queries for specific certificates |
| Freshness of Data | Depends on update interval (could be hours or days) | Near real-time, depending on responder availability |
| Scalability | Less scalable for large environments | More scalable, but adds dependency on OCSP responder |
| Offline Capability | Can be cached for offline use | Requires active internet or network connection |
| Implementation Complexity | Simpler to implement and distribute | More complex; requires reliable and secure OCSP infrastructure |
Certificate life cycle management
As organizations move toward short-lived certificates to reduce risk, the frequency of renewals and updates increases dramatically. In IoT deployments, where devices often number in the thousands and are deployed across wide geographic areas, this shift introduces real operational complexity.
The certificate lifecycle includes several critical stages: issuance, distribution, renewal, rotation, revocation, and retirement. The table below lists these stages, their description, and key considerations. Each stage must be handled correctly and on time to ensure devices remain authenticated and can securely communicate. Even a single expired or revoked certificate can trigger outages, disrupt workflows, or expose sensitive data.
When certificates are short-lived—sometimes lasting just weeks—the potential for failure grows unless the process is centralized and automated.
| Stage | Description | Key considerations |
|---|---|---|
| Issuance | The certificate is generated and signed by a Certificate Authority (CA). | Ensure correct key strength, identity validation, and adherence to security policies. |
| Distribution | The certificate is securely deployed to the device or endpoint. | Use secure channels; verify correct certificate installation on the intended device. |
| Renewal | The certificate is reissued before it expires to maintain trust continuity. | Automate this step to avoid service outages due to expiration. |
| Rotation | Replacing certificates periodically, even if not expired, to enhance security. | Helps mitigate risks from undetected compromise or cryptographic aging. |
| Revocation | Certificates are invalidated before expiration due to compromise or decommissioning. | Must be communicated quickly via CRL or OCSP to prevent misuse. |
| Retirement | The certificate and key are securely removed when the device is no longer active. | Prevents future reuse; ensure secure key destruction or deletion. |
Manual tracking using spreadsheets or isolated systems simply doesn’t scale. IoT teams need a centralized management platform that can monitor all certificates in real time, verify expiration dates, and trigger automated alerts or renewal and deployment workflows. Such systems reduce human error, eliminate downtime from overlooked expirations, and support consistent security policies across the organization. Additionally, they provide vital visibility: security teams can quickly pinpoint which certificates are expiring soon, which devices are using weak keys, or whether any certificates have failed to renew.
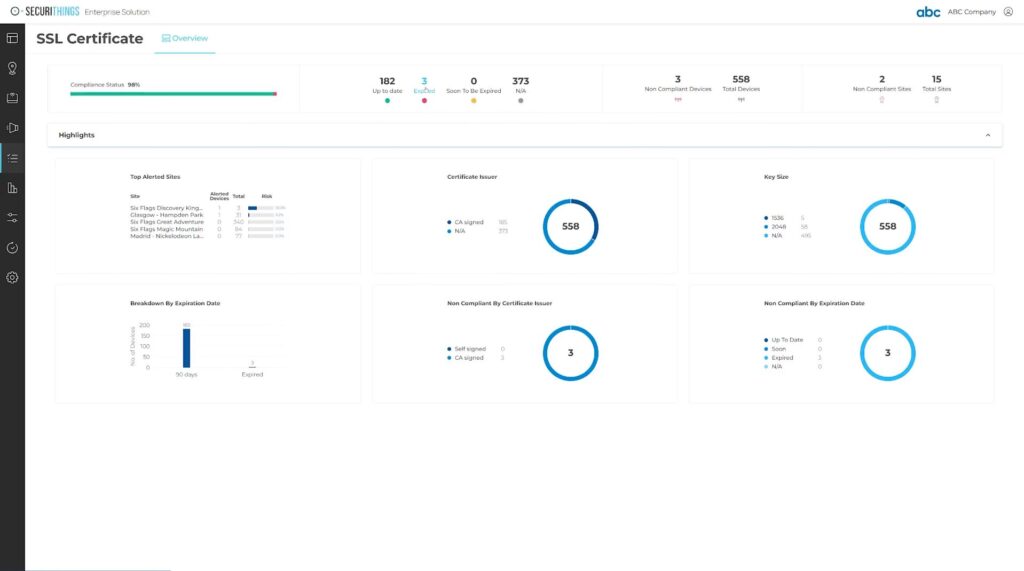
SecuriThings SSL Certificate Dashboard. (Source)
IoT operations management
-

Monitor the health of physical IoT devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Last thoughts
Certificates are essential in authenticating IoT devices, encrypting traffic, and digital signing, but their effectiveness depends entirely on how well they are managed throughout their lifecycle. With the industry moving toward shorter certificate lifespans and the number of devices growing exponentially, manual management is no longer sustainable.
Without automation, organizations risk expired certificates, broken trust chains, and security gaps. A centralized, automated certificate lifecycle management system not only prevents these issues, but it also enables scalable, policy-driven trust across all connected IoT devices. Real-world solutions like SecuriThings provide automated certificate lifecycle management at scale, helping organizations reduce operational burden and enhance security posture across their IoT infrastructure.