Compliance is a recurring challenge for organizations using IoT solutions. Two main issues that make compliance in IoT so tricky are the lack of visibility into what’s happening with devices in the field and the absence of well-defined IoT compliance standards, such as those in the IT world.
Compliance in IoT comprises both cyber security and operational challenges. IoT teams need to know whether their devices are secure and working correctly at all times (e.g., are firmware versions and passwords up to date?). These challenges are further accentuated at scale and when devices are deployed at multiple sites.
Let’s look at these challenges and how organizations can improve their compliance posture.
IoT Compliance Challenges & The Resulting Issues
| IoT Security Compliance Challenges | IoT devices are often deployed with a default password (or no password), extending organizations’ cyber-attack surface.
IoT devices being physically accessible also heightens these threats. |
Hackers can easily access IoT devices and:
|
| IoT Operational Compliance Challenges | IoT devices are particularly prone to failures, which can impair – and sometimes completely disrupt – organizations’ daily activities.
The lack of visibility into device status makes it even harder to address maintenance issues in a timely manner. |
These challenges may lead to:
|
Guidelines for Strengthening Your IoT Compliance
With the need for clear-cut IoT regulatory compliance standards, organizations can define their policies based on cyber security and operational criteria. In some cases, they will also have to address existing regulatory directives.
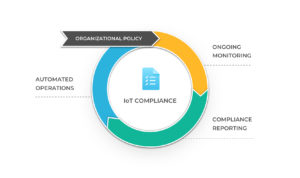
To apply these policies, IoT teams must continuously monitor each IoT device’s health and cyber security status. There are three main guidelines for improving compliance in IoT:
- Admins must have visibility into all connected devices across sites without toggling between multiple screens and systems.
- Real-time reporting is crucial for allowing IoT teams to understand their compliance status for all devices across the system (e.g. percentage of passwords and firmware versions to be updated). By integrating with third-party ticketing and SIEM solutions, IoT teams can make sure that follow-ups on discovered compliance issues are tracked and handled in a timely manner.
- Lastly, automation of operational tasks, such as password rotation and firmware upgrade, is essential for enabling organizations of all sizes to meet their IoT compliance challenges. The need for automation is naturally accentuated in large-scale deployments (thousands of devices or more).
Improving IoT Compliance with SecuriThings’ Solution
Ensuring compliance with your organization’s cyber security and operational goals is a constant effort, especially for resource-challenged IoT teams. Organizations can gain real-time visibility over device operational status by automating device monitoring and reporting, enforcing organizational policies, and continually improving compliance.
SecuriThings Enterprise is an IoTOps solution that supports ongoing health and cyber monitoring, compliance reporting, and automated operations across IoT devices. Using data, analytics, and automation, SecuriThings brings IT management standards and capabilities to the world of IoT.
To read more, download our one-pager about compliance in IoT.
FAQs
What is IoT compliance?
IoT compliance refers to adhering to cybersecurity and operational standards for Internet of Things (IoT) devices within an organization. It encompasses many measures to ensure that devices are secure from cyberattacks, vulnerabilities, and unauthorized access. It optimally prevents operational disruptions, data loss, and potential regulatory fines.
Why is IoT compliance particularly challenging?
IoT compliance is notably challenging due to several factors. First, the sheer number and diversity of IoT devices deployed across various locations and networks can make maintaining visibility into their status and security difficult. Second, the need for standardized industry regulations and guidelines for IoT devices creates ambiguity and requires organizations to establish policies, adding another layer of complexity. Additionally, the rapid evolution of IoT technology and the constantly changing threat landscape require continuous adaptation to ensure ongoing compliance.
What are the essential guidelines for improving IoT compliance?
First, organizations must establish comprehensive visibility into all connected devices across their networks. This includes real-time monitoring of device health, security status, and adherence to established policies. Secondly, implementing real-time reporting mechanisms allows for continuous tracking of compliance status, enabling prompt identification and remediation of any issues. Lastly, automating routine operational tasks such as password rotation, firmware updates, and vulnerability scanning can significantly streamline compliance efforts and reduce the risk of human error.
How can SecuriThings’ solution help with IoT compliance?
SecuriThings Enterprise is an IoTOps solution that automates device monitoring, reporting, and operations. It provides real-time visibility into device health and cybersecurity, enforces organizational policies, and helps improve IoT compliance.
Compliance is a recurring challenge for organizations using IoT solutions. There are two main issues that make compliance in IoT so difficult. These are the lack of visibility into what’s happening with devices in the field and the absence of well-defined IoT compliance standards such as those in the IT world.
Compliance in IoT comprises both cyber security and operational challenges. IoT teams need to know whether their devices are secure and working properly at all times (e.g. are firmware versions and passwords up to date?). These challenges are further accentuated at scale and when devices are deployed at multiple sites.
Let’s take a closer look at these challenges and the steps organizations can take to improve their compliance posture.
Challenges & The Resulting Issues
| IoT Security Compliance Challenges | IoT devices are often deployed with a default password (or no password at all), extending organizations’ cyber-attack surface.
IoT devices being physically accessible also heightens these threats. |
Hackers can easily access IoT devices and:
|
| IoT Operational Compliance Challenges | IoT devices are particularly prone to failures, which can impair – and sometimes completely disrupt – organizations’ daily activities.
The lack of visibility into device status makes it even harder to address maintenance issues in a timely manner. |
These challenges may lead to:
|
Guidelines for Strengthening Your IoT Compliance
With the lack of clear-cut, IoT regulatory compliance standards, organizations can define their own policies, based on cyber security and operational criteria. In some cases, they will also have to address existing regulatory directives in place.

To apply these policies, IoT teams need to continuously monitor both the health and cyber security status of each IoT device. There are three main guidelines for improving compliance in IoT:
- Admins must have visibility into all connected devices across sites without having to toggle between multiple screens and systems.
- Real-time reporting is crucial for allowing IoT teams to understand their compliance status for all devices across the system (e.g. percentage of passwords and firmware versions to be updated). By integrating with third-party ticketing and SIEM solutions, IoT teams can make sure that follow-ups on discovered compliance issues are tracked and handled in a timely manner.
- Lastly, automation of operational tasks, such as password rotation and firmware upgrade, is essential for enabling organizations of all sizes to meet their IoT compliance challenges. Naturally, in large-scale deployments (thousands of devices or more), the need for automation is accentuated.

Improving IoT Compliance with SecuriThings’ Solution
Ensuring compliance with your organization’s cyber security and operational goals is a constant effort, especially for resource-challenged IoT teams. By automating device monitoring and reporting, organizations can gain real-time visibility over device operational status, enforce organizational policies and continually improve their compliance status.
SecuriThings Enterprise is an IoTOps solution that supports ongoing health and cyber monitoring, compliance reporting and automated operations across IoT devices. Using data, analytics and automation, SecuriThings brings IT management standards and capabilities to the world of IoT.
To read more, download our one-pager about compliance in IoT.