Data Center Physical Security
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
Data centers are essential to modern digital business. While we often don’t think about their existence regularly, their importance becomes evident when one of them suffers an outage. Mission-critical apps and websites depend on data centers, and downtime can have a massive impact on customers, business revenues, and reputation.
Cybersecurity and disaster recovery typically come to mind in discussions about data center uptime. However, physical security is as critical. IBM Security’s 2024 ‘Cost of Data Breach’ report indicated nearly 1 in 10 data breaches are due to physical security compromise. There have been documented instances of armed robberies worth millions of dollars from data centers and fires destroying data center facilities, causing several hours of downtime and affecting hundreds of thousands of users. These examples demonstrate that, data center physical security is essential to reducing business risk and maintaining system uptime.
This article will explore data center physical security in detail, including data center infrastructure, threats to physical security, critical aspects of data center physical security, and best practices.
Summary of key data center physical security concepts
The table below summarizes four key data center physical security concepts this article will explore in detail.
| Concept | Description |
|---|---|
| Data center infrastructure | A data center is a collection of computing and storage equipment and a sophisticated system consisting of electrical, HVAC, fire protection, security, and communication systems. |
| Data center physical security threat examples | From fire to robberies, several actual incidents highlight the impact of lapses in data center physical security. |
| Essential aspects of data center physical security | Location identification, perimeter security, access controls, visitor management, equipment disposal, and environmental protection are crucial aspects of the data center’s physical security. |
| Best practices for data center physical security | Adhering to compliance, maintaining a well-trained staff, and having adequate redundancies ensure robust data center physical security. |
Data center infrastructure
By definition, a data center is a collection of servers, storage systems, and networking equipment. A typical data center server would reside on raised floors to route power distribution units and chilled air ducts underneath. Servers and networking infrastructure can produce significant heat, and cooling is vital for reliable operations. The servers are typically arranged in racks or cabinets and these are surrounded by a metal mesh known as the cage. This cage is often the last line of defense between the server equipment and an unauthorized hacker in its vicinity. Typically, the ceiling area is composed of fiber optic cables and fire prevention systems.
A modern data center is designed for scalability, reliability, efficiency, and high availability and has a complex architecture optimized for performance and adaptability. In addition to servers and networking equipment, data centers include electrical, HVAC, security, fire protection, and communication systems.
Depending on the availability requirements and application, data centers are categorized into four tiers, as shown in the image below:
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
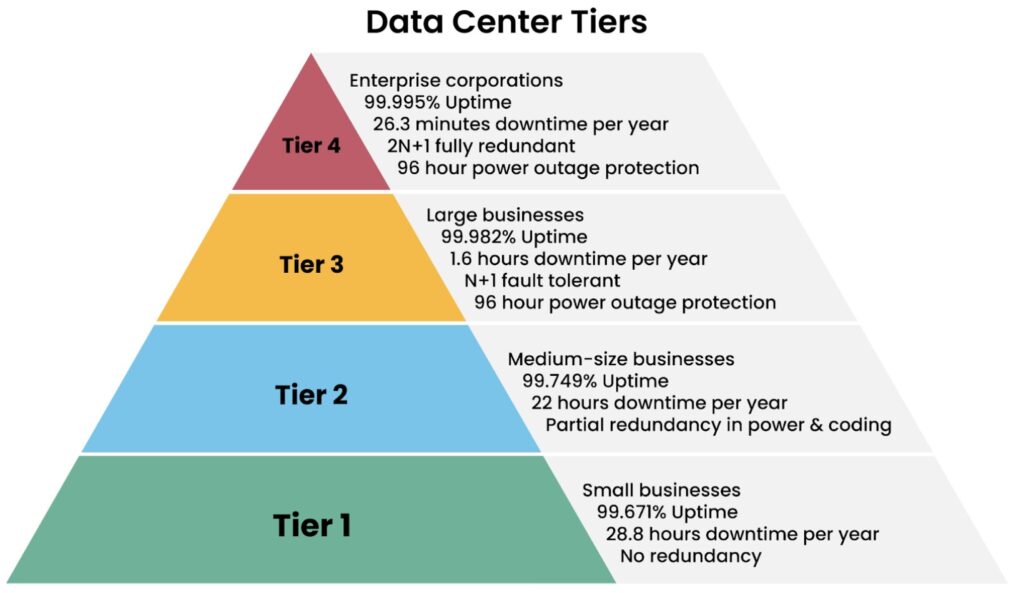
Description of the four data center tiers. (Source)
A data center’s redundancy configuration can range from none to 2N+1 redundancy. The redundancy nomenclature is expressed below:
- N represents the number of units of critical components and systems required to run the data center. For example, if the data center requires one air conditioning unit to operate, 2N redundancy would ensure two independent units.
- +1 is an additional spare unit beyond the redundancy provided by 2N. This is useful if one of the 2N units needs to be repaired or replaced.
The higher the uptime requirements for a data center, the more critical physical security is to meet those requirements. Even less than an hour of downtime caused by a small fire or power fluctuation can cause a breach of service level agreements (SLAs).
Real-world examples of data center physical security threats
From harsh weather to hackers to malicious insiders, the list of threats to a data center is long. And there are real-life incidents that showcase the criticality of these threats.
In March 2011, hundreds of thousands of Vodafone customers in the United Kingdom lost service after thieves broke into their exchange center at Basingstoke and stole switch equipment. While not exactly a data center, an exchange center is a physical infrastructure through which Internet Service Providers (ISPs), content delivery networks (CDNs), and other networks interconnect to exchange Internet traffic.
On December 6, 2007, intruders dressed as police officers broke into Verizon’s London data center and stole equipment worth more than $4 million. Another armed robbery was reported in 2005 in Chicago’s colocation center operated by CI Host, and equipment worth $15,000 was stolen.
On March 10, 2021, a fire completely destroyed one of OVHCloud’s data centers in France and partially destroyed another. Another fire at the AT&T data center in Texas in October 2018 led to 12 hours of downtime. On October 15, 2021, a fire at the SK C&C data center in Pangyo, South Korea, impacted two tech companies, Kakao Corporation and Naver Corporation. Naver swiftly restored its servers, but Kakao experienced extended outages, causing disruptions to its messaging services, payment apps, and rideshare platforms for several hours.
The above are just a few examples highlighting the damage that lapses in the data center’s physical security can cause. The impact can create millions of dollars in loss and damages.
Six essential aspects of data center physical security
The sections below explain the six essential aspects of modern data center physical security.
Geographical viability
The data center’s location is vital to the physical security of the data center infrastructure. The following geographical factors should be considered when selecting the right site for the data center:
- Natural disaster likelihood: Your data center should ideally be situated in an area with a very low probability of natural disasters like earthquakes, cyclones, and floods.
- Proximity to hazardous industries: Your data center should not be located in a region surrounded by chemical factories, mining and quarrying sites, power plants, heavy manufacturing, oil and gas industries. Emissions, environmental contamination, power fluctuations, vibration, and dust can disrupt the sensitive hardware in a data center and cause performance issues.
- Availability of power and water: Data centers are power-hungry, and stable power availability helps. While backup generators and UPS systems present at the data center site can handle short-term power outages, they cannot sustain the data center’s operations in case of a long-term power outage. Similarly, water availability is crucial for cooling equipment.
- Proximity to essential services: Good connectivity to police stations, fire stations, hospitals, and townships, and availability of transportation ensures rapid emergency response and timely equipment delivery and installation.
Perimeter security
Perimeter is the first line of defense at the site. It typically involves the following components:
- Fencing and walls: The entire perimeter must be guarded with a strong physical barrier. Microsoft typically uses long steel and concrete walls across all Azure data centers. Anti-climbing measures and barbed wires can be additionally employed to improve security.
- Surveillance systems: The entire perimeter, especially the entry points and other vulnerable areas, must be monitored using security cameras. These cameras should have night vision and thermal imaging to detect intrusions in low light. In addition, they can have motion detection and computer-vision model-based suspicious activity alarms to alert the security personnel at the site.
- Security personnel: All entry points must be guarded by trained personnel
Access control
Access to the facility and all sections within the facility should be strictly controlled using access cards and biometrics.
The following characteristics are essential when it comes to physical access controls:
- Principle of least privilege: All access should be based on the principle of least privilege, i.e., the person should only be given as much access as required for fulfilling their duties. Any additional access is a potential security threat.
- Anti-tailgating systems: All access points should be equipped with anti-tailgating systems to ensure that an unauthorized person cannot tailgate an authorized person and enter the facility.
- Facility video surveillance: All sections of the facility, especially the sensitive areas, should have video surveillance to ensure that any unauthorized person is immediately flagged. The cameras should be equipped with face recognition to ensure the person is identified even without human intervention.
- Logging: All accesses should be logged. The logs can provide valuable information about people’s access patterns and might help identify a potential insider threat. Of course, logs can help with the investigation if an incident happens.
- Multi-factor authentication (MFA): Sensitive areas like computer rooms, cabinets, cages, or racks should only be accessible after dual authentication (for example, access card and biometric)
Visitor management
The data center has visitors from time to time. The purpose of their visit can range from maintenance to audit. Managing visitors’ access to the data center forms an essential aspect of its physical security.
Key visitor management concepts to consider:
- Planned vs. unplanned visits: You should only allow planned visits wherever possible. This helps you vet and approve requests and create access cards with only the requisite permissions.
- Escorting visitors: To avoid giving visitors direct access cards, an authorized employee can escort visitors to the required areas. The employee will then be responsible for the movement of the visitor within the premises.
- Access card management: All visitor access cards should be collected before the visitor leaves, and they should be cleared of all access permissions
- Surveillance: Again, facility-wide surveillance, preferably with facial recognition (if permitted by local privacy laws), can help identify the presence of a visitor in an unauthorized location
Disposal of data-bearing equipment
All systems eventually reach their end-of-life, and they need to be disposed of according to proper procedure. The data should be erased in all memory devices that support it. Memory devices that don’t should be destroyed by shredding, pulverization, incineration, or any other means that make data extraction from the device impossible. The media sanitization process should be compliant with NIST-800-88.
Environmental Security
The facility should be equipped with automatic fire detection, alarm, and suppression systems. The facility should have an efficient drainage system to avoid the risk of flooding. HVAC system maintenance should be carried out periodically because overheating is a significant risk in data centers. A comprehensive incident response plan should be created, and an emergency response team should be identified and trained to deal with environmental incidents.
Four data center physical security best practices
Typically, the specifics of physical security will be driven by the details of a site, risk appetite, available resources, and compliance requirements. However, there are foundational best practices that most organizations can follow. The sections below detail four essential data center physical security best practices that can help guide specific implementations.
Maintain compliance
Here’s the list of common compliance standards for data centers, especially those operating in the USA:
- ISO 27001: This is an international standard for Information Security Management Systems. It outlines the requirements for establishing, implementing, maintaining, and continually improving an ISMS to manage and protect sensitive information. Physical security practices are also addressed within this standard, along with protection of sensitive information, risk management, and maintaining system availability.
- HIPAA (Health Insurance Portability and Accountability Act): This U.S. Law establishes national standards for protecting patients’ sensitive health information. It also provides guidelines for the physical safety of the infrastructure that stores and processes electronic Protected Health Information (ePHI)
- SOC 2 (Systems and Organization Controls 2): Developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 is focused on operational and compliance controls related to data security, including physical security. SOC 1, on the other hand, is primarily focused on financial reporting.
- FedRAMP (Federal Risk and Authorization Management Program): This U.S. government-wide program targets cloud products and services. If your data center acts as a cloud service provider (CSP) to the U.S. Government, then you need to adhere to the security assessment, authorization, and continuous monitoring framework provided by FedRAMP. FedRAMP incorporates the National Institute of Standards and Technology (NIST) Special Publication 800-53 security controls, which include guidelines on physical security.
- PCI DSS (Payment Card Industry Data Security Standard ): This is a global standard for organizations that handle credit card information. It includes strict measures to protect cardholder data, including physical security requirements for data centers processing or storing credit card information.
- FISMA (Federal Information Security Management Act): This is a U.S. Law that mandates the protection of federal information systems and includes measures for the physical security of data centers handling government data.
Additionally, several other standards may apply to your data center, depending on the geography within which it operates or the region whose data is processed. These may include E.U.’s General Data Protection Regulation (GDPR), Australia’s Infosec Registered Assessor’s Program (IRAP), Singapore’s Multi-Tier Cloud Security (MTCS), India’s Digital Personal Data Protection Act (DPDPA), etc. You can get a substantially comprehensive list of standards applicable to data centers by looking at the standards that Microsoft Azure complies with.
It is essential to identify the standards applicable to your data center and comply with those standards. The standards are updated periodically, and it helps to keep yourself up-to-date with the latest requirements. Most of the standards also specify the frequency and SOP of regular audits. Organizations should perform regular audits to avoid disruptions in their data center operations.
Train and empower personnel
The personnel securing the data center should be periodically trained to know the latest regulations and the upgraded security equipment being used. Mock drills should be conducted from time to time to ensure the readiness of the personnel. Ideally, there should also be a separation of concerns: the security personnel should not be able to sign in to the data center systems. Otherwise, there is a risk of insider threats.
Implement physical redundancy
Depending on the data center’s tier, sufficient redundancy should be provided for utilities like electricity, HVAC equipment, and water. These redundancies should be distributed to avoid common-mode failure. Redundancies ensure high system availability, which is essential for data centers.
Build robust facilities and infrastructure
Depending on the data center’s location, if there is even a slight risk of earthquakes, then the design of the data center can be made earthquake-resistant. This could include usage of newer seismic racks, and selection of earthquake-resistant construction materials.
Within the facility, temperature and humidity control should be monitored regularly and any deviations from the acceptable range should be immediately escalated.
The physical hardware’s integrity should also be monitored from time to time. There should be tamper detection protocols in place to identify any meddling with the hardware, and the affected hardware should be immediately replaced.
Conclusion
Physical security is important for protecting data center information and ensuring seamless operation. Lapses in physical security can lead to damages ranging from a few hours of downtime to millions of lost dollars. Physical security consists of several aspects, from identifying the data center’s location to perimeter security, access management, visitor management, standard equipment disposal procedures, and environmental controls. Complying with applicable standards, keeping the staff well-trained and ready for emergency response, and ensuring adequate redundancy can keep the physical security of your data center in good health.


