Physical Security Plan and Best Practices
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
- Chapter 13: Best Practices for Corporate Physical Security
- Chapter 14: Physical Security Best Practices
- Chapter 15: How physical security powers
- Chapter 15: Best Practices for Physical Security Devices
Physical security planning (PSP) is vital for protecting assets through deterrence, detection, delay, and response but is often overlooked in favor of network and software security.
In military settings, physical security protects sensitive data, equipment, and personnel through layered measures that combine electronic, mechanical, and electrical controls. Examples include integrating video surveillance with physical barriers such as blast-resistant enclosures and using TEMPEST shielding to guard against espionage.
In the private sector, physical security planning addresses threats such as unauthorized server room access, data center vulnerabilities, and IoT exploitation in smart building systems. Securing IoT and industrial devices, ranging from HVAC systems to security cameras, aligns closely with broader cybersecurity strategies.
Tools designed to manage the lifecycle of physical security devices strengthen physical security by hardening access, monitoring the devices, and ensuring compliance and normal functionality, which is why they are a fundamental component of any physical security plan.
This article offers a technical framework engineers can use to improve security within their respective domains. It also guides engineers through creating a PSP to protect assets, personnel, and information from physical threats. It covers the key components, including threat assessment, access control, surveillance, and incident response. This article also offers best practices for integrating physical and cybersecurity measures, using advanced technologies, and training staff. Finally, it addresses challenges like budget limitations and evolving threats, providing practical insights to help engineers adapt security strategies.
Summary of key physical security plan concepts
| Concept | Description |
|---|---|
| Overview and importance of military and private sector PSP | A physical security plan protects assets and people from physical threats. Military plans are more stringent, emphasizing high-risk defense measures, while private companies balance cost and security using technology and access controls. |
| Developing and implementing a PSP: roles and responsibilities | Clear roles and responsibilities ensure effective coordination and execution of physical security plans. |
| Key components of a PSP | A PSP includes a number of key components, like facility profiling, assigned roles, and threat management. |
| Best practices for physical security planning | Establish policies to ensure consistency in protecting assets, guide security procedures, and help maintain a secure environment by outlining clear protocols for preventing and responding to threats. Implement a physical security management solution for modern physical security planning. |
| Challenges and considerations in physical security planning | Planners must manage costs and address legal requirements, employee safety, and operational impacts to create an effective, balanced security strategy. |
| Physical security plan sample | A practical sample illustrates how to ensure all security protocols are in place, covering areas like access control, surveillance, and emergency procedures. |
Overview and importance of military and private sector physical security plans
A physical security plan safeguards personnel, property, and information. It relies on threat analysis to establish procedures and physical measures. These measures aim to prevent unauthorized access to equipment, facilities, materials, and data while protecting against espionage, terrorism, sabotage, damage, misuse, and theft. Organizations and companies protect personnel, information, and critical resources in all locations and situations against various threats by developing and implementing effective physical security programs, policies, and procedures.
The physical security program is the interrelationship of components that complement each other to produce a comprehensive approach to security matters. These components include—at a minimum—the PSP, physical security inspections, and a continuing assessment of the installation’s physical security posture. The goal of the security system for an installation, area, facility, or asset is to employ security in depth to prevent or reduce the potential for sabotage, theft, trespass, terrorism, espionage, or other criminal activity.
For military organizations, physical security is a critical component of national defense. Military installations and operations need to be highly protected because of the sensitive nature of their operations, the valuable assets they handle, and the security threats they face from hostile forces. In military environments, the PSP focuses on protecting people, sensitive data, weapons, military hardware, and critical infrastructure from threats that include terrorism, espionage, and military assaults. Given the high stakes in military operations, their physical security plans are typically more rigid, formalized, and backed by comprehensive protocols that ensure immediate and effective responses to threats.
While private companies may not face the same high-intensity security threats as military organizations, they still have significant concerns about protecting their assets, employees, and information. Physical security in the private sector is primarily driven by the need to safeguard intellectual property, proprietary data, critical infrastructure, and employee safety from external and internal risks, including theft, vandalism, and corporate espionage.
Here are some well-known incidents caused by inadequate physical security planning:
- Security Vendor RSA SecurID Breach (2011): Attackers used social engineering to gain physical access to RSA’s facilities and steal sensitive data. This led to the compromise of SecurID authentication tokens, affecting thousands of customers.
- Edward Snowden Leaks (2013): Weak physical access controls allowed Snowden to smuggle data out of NSA facilities, exposing classified surveillance programs and sparking a global debate on privacy and security.
- Ashley Madison Hack (2015): A lack of physical security at data centers contributed to unauthorized access, allowing attackers to steal and leak sensitive user data and cause widespread reputational and financial damage.
The table below compares key characteristics of physical security plans in military and private organizations.
| Key characteristic | Military physical security plan | Private sector physical security plan |
|---|---|---|
| Perimeter security | Stringent control over access points with barriers, walls, and guarded checkpoints | Fences, gates, and access control systems, but typically less fortified than military installations |
| Personnel vetting and screening | Rigid background checks, continuous monitoring, and security clearances for personnel | Background checks and employee screenings, with ongoing monitoring, but usually less extensive |
| Access control | Highly controlled access to sensitive areas with multiple clearance levels | Use of keycards, biometric scanners, and security badges to control access |
| Surveillance and monitoring | Extensive use of surveillance systems, including perimeter sensors, cameras, and guards | CCTV, motion detectors, and real-time monitoring systems to detect intrusions |
| Security protocols and readiness | Combat-readiness mindset, quick response teams, and high-security protocols | Emphasis on threat mitigation, incident response, and emergency evacuation protocols |
| Technology integration | Often more traditional methods (e.g., guards and barriers), though some military use advanced tech for surveillance and response | Heavy reliance on advanced technologies such as AI-based threat detection and smart access control |
| Employee and contractor security | Tight control and monitoring of military personnel and contractors with access to sensitive facilities | Security training for employees, contractors, and third-party vendors |
| Risk assessment and continuity plans | Comprehensive risk management plans to address security threats and military operations continuity | Risk assessments focus on physical asset protection, business continuity, and emergency preparedness |
| Incident response | Military units are trained for rapid mobilization and may involve coordination with other defense forces | Focus on quick internal response with escalation to external security providers if needed |
| Focus of security | Protection against espionage, sabotage, terrorism, and enemy forces | Protection against theft, vandalism, cyber threats, and workplace violence |
| Cost considerations | Cost is generally secondary to mission readiness and national security. | Cost-effective solutions balancing risk mitigation and operational efficiency |
| Legal and compliance regulations | Strict adherence to national defense regulations, laws, and international security protocol. | Compliance with industry-specific regulations (e.g., OSHA, GDPR, HIPAA) and local safety laws |
Whether in military defense or private enterprise, physical security planning is essential for protecting an organization’s assets and ensuring its continued operation in an increasingly complex security environment.
Developing and implementing a physical security plan: roles and responsibilities
Physical security planning should focus on safeguarding business assets, intellectual property, and employee safety. Compared with the military, the private sector’s roles tend to be more specialized, integrating risk management and compliance with a broader range of security measures balanced with cost-effectiveness. There is also a greater reliance on technology and collaboration across departments (e.g., IT, HR, and facilities). While both sectors share similar roles (e.g., security officers, managers, and specialists), the military emphasizes defense and readiness, while the private sector focuses on operational security and risk management.
The table below shows some important roles in private organizations that contribute to building a PSP.
| Private sector role | Responsibilities |
|---|---|
| Senior leaders (e.g., CEO and CSO) | Make high-level decisions about security priorities, budgets, and compliance |
| Security manager | Oversees corporate security strategy and aligns with overall business goals and risk management |
| Physical security specialist | Assesses and manages physical security risks in private organizations, often focusing on commercial assets and employee safety |
| Security personnel | Manage access control, surveillance, and incident management in a commercial setting |
| Risk analyst | Analyzes potential threats to business continuity, often including physical, cyber, and environmental risks |
| Facilities manager | Oversees facility security measures, such as building access, employee safety, and integration with physical security systems |
| IT/cybersecurity team | Works with physical security to protect networked security systems and prevent breaches of physical security via cyberattacks |
| Legal and compliance officer | Ensures compliance with private sector regulations, industry standards, and legal requirements related to physical security |
Key components of a physical security plan
The elements listed in this section are recommendations for areas to consider when developing a PSP. The level of detail in the plan may vary based on the facility’s nature.
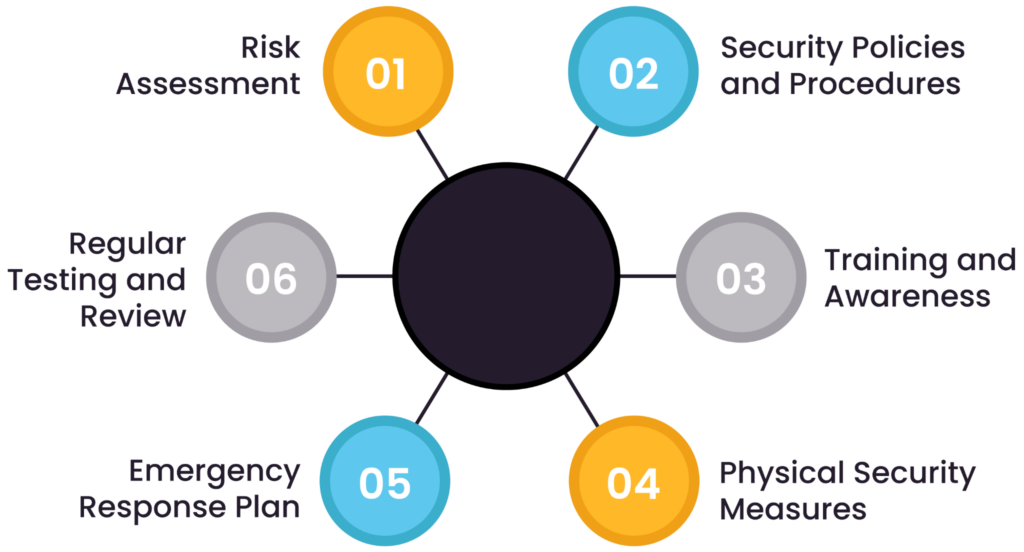
Critical components of a security plan (source)
AI is transforming physical security from predictive maintenance to real-time threat detection and automated response. But most organizations aren’t ready to take advantage of it.
Facility profile
The facility profile should describe the facility, including the following:
- Type of facility (e.g., single-story or multi-story)
- Population (e.g., single tenant or multi-tenant, child care center, visitors)
- Mission and critical functions conducted at the facility (e.g., administration, operations center, classified information, continuity of operations site)
- Utilities (e.g., power, water, gas)
- The most current facility diagrams, construction documents, and specifications
Roles and responsibilities
Identify facility-specific positions and explain roles and responsibilities for security-related tasks. Include who is responsible for preparing and approving the plan. Also include contacts for all first-responder and/or support organizations responsible for securing the facility (i.e., local law enforcement, security organizations, and building management).
Risk management strategy
Utilizing information from the risk management plan (RMP), outline and prioritize threats to the facility, tenant agencies, and/or operations, and prepare an overview of the strategies used to mitigate them. Explain any risks accepted as part of the risk management process and any possible consequences.
Security countermeasures
Identify and describe in detail all current and planned security countermeasures (including floor plans when available) to address all identified threats. As much as possible, ensure that countermeasures are scalable to allow for an increased or decreased security posture as the threat evolves.
Maintenance, repair, and testing procedures
Describe requirements for operator and manufacturer maintenance and repair of security countermeasures. Outline a testing schedule performed by the security manager.
Incident response management and procedures
Describe in detail the procedures for responding to security incidents and emergencies. Details should include the following:
- Reporting: How do employees report incidents? Do they call an internal operations center or 911?
- Notification: How are first responders and facility occupants notified that an incident is taking place or has occurred?
- Response: Who should respond and how? What is the chain of command?
- Law enforcement and security organizations
- Fire department
- Medical
- Alarm response
- Recovery: Once an incident response is terminated, what is the process to resume normal operations?
- Documentation: How is an incident documented? Where is the information maintained? Who has authorized access to that information?
Critical components of incident response management in physical security. (source)
Facility-specific policies
Include any unique requirements to address issues such as landlord or tenant agreements or special missions (i.e., classified areas, operations centers, network control centers, child care centers, etc.).
Government property
Include procedures to control pilferage, destruction, and disposal of government-owned property.
Training and exercising the plan
Develop a strategy or program to train personnel and exercise all aspects of the PSP. These exercises can be table-top, drills, or full-scale exercises.
Program review
Provide program review guidelines within the plan. Program reviews should be conducted at least annually.
Resource support
Outline fiscal instructions on how funding support is gained to sustain security operations from pre- to post-incident.
Information security
If applicable, address issues related to protecting sensitive but unclassified and classified information.
Cybersecurity
Collaborate with all tenant CIOs to develop a plan for the physical and logical protection of information technology systems and equipment associated with security countermeasures. Security devices like IP cameras represent an attack surface that can be exploited. The following section explains how specialized software can streamline this process.
Physical security management software
A critical component that organizations should consider is implementing a physical security management solution.
Organizations should incorporate a physical security management solution to strengthen the overall security posture and streamline the management of complex security operations.
Integrating various security device management processes into a single interface enhances operational efficiency and ensures systematic protection.
Key functionalities of such platforms include:
- Device health monitoring:
- Tracks the operational status of security devices such as surveillance cameras and access control systems, ensuring they are always functional.
- Automated alerts:
- Sends real-time notifications for device malfunctions, security breaches, or unusual activity, allowing quick action.
- Analytics and insights:
- Generates reports on device performance, security trends, and compliance status to help organizations make data-driven decisions.
- Centralized access control:
- Manages permissions and access across facilities, reducing vulnerabilities associated with unauthorized access.
- Compliance management:
- Automates compliance checks to ensure all security measures align with regulatory requirements and internal policies.
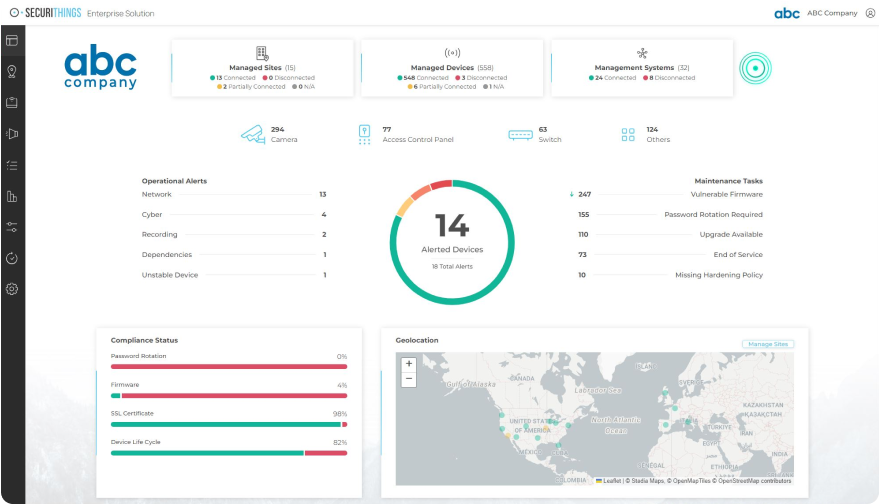
Example interface of a physical security management platform (Source)
Best practices for physical security planning
Organizations should implement physical security practices in a well-structured security plan to mitigate risks, prevent unauthorized access, and enhance their resilience against potential threats.
The table below shows best practices to consider when creating a PSP.
| Best practice | Description |
|---|---|
| Conduct comprehensive risk assessments | Assess potential threats, vulnerabilities, and the impact of various risks regularly. Based on these assessments, update the security plan as needed. |
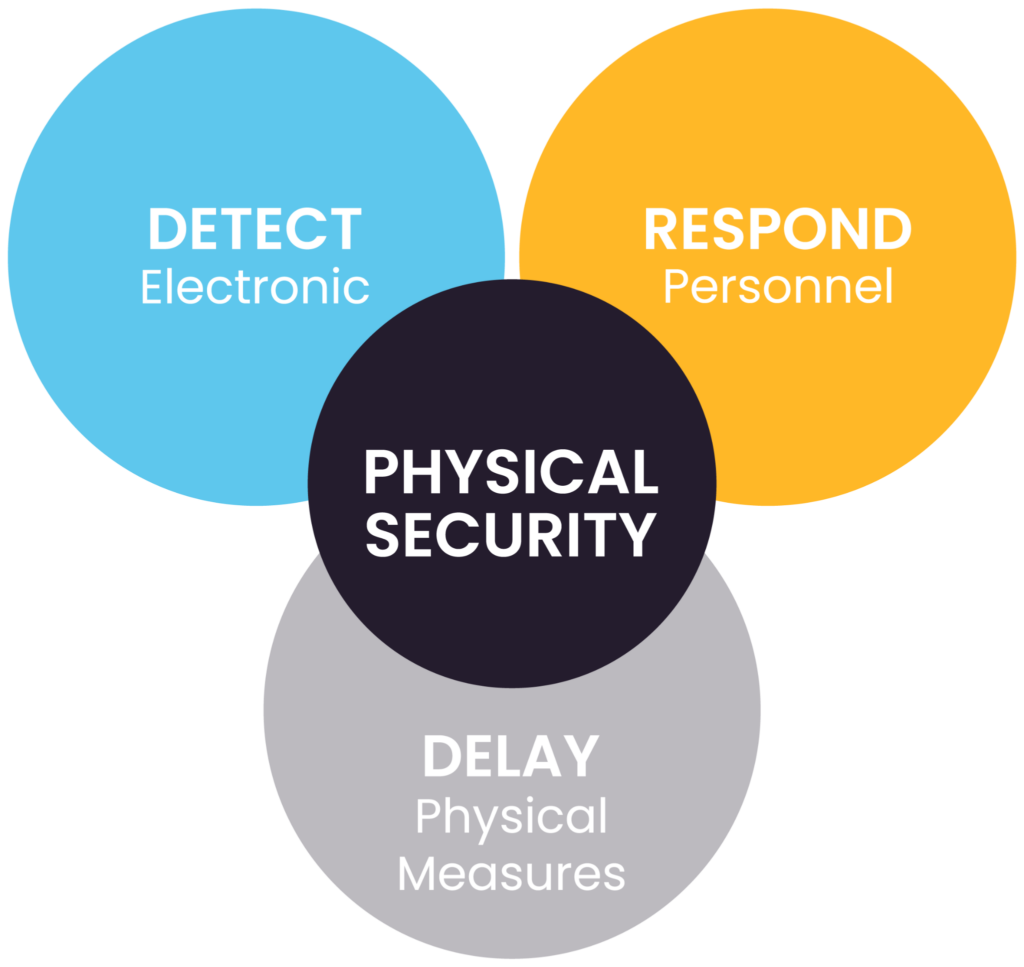
| Establish a layered security approach | Implement multiple layers of security (e.g., perimeter control, access control, and internal security) to deter or delay unauthorized access and minimize risks. |
| Integrate technology with physical security | Leverage advanced technologies like CCTV, biometric systems, motion detectors, and smart security solutions for real-time monitoring and threat detection. |
| Ensure clear and consistent communication | Develop clear communication protocols for security teams, employees, and management. |
| Implement strong access control policies | Enforce access policies based on the principle of least privilege, using multi-factor authentication and regularly updating access credentials. |
| Regularly train employees and security personnel | Conduct training for all employees on security awareness, and provide specialized training for security staff to handle incidents and emergencies effectively. |
| Establish incident response and recovery plans | Create documented plans for responding to security breaches, including business continuity and disaster recovery protocols. Test and update regularly. |
| Monitor and evaluate security performance | Continuously track the effectiveness of security measures, conduct audits, and seek feedback for improvements. |
| Implement a unified physical security management solution | Modern physical management software allows teams to centralize key administrative workflows required for security posture and regulatory compliance |
| Comply with industry regulations and standards | Stay informed on legal and regulatory requirements (e.g., OSHA, GDPR) and ensure that your PSP complies in order to avoid penalties or legal issues. |
| Maintain security and emergency contact lists | Keep up-to-date contact lists of emergency services (e.g., law enforcement and medical facilities) and ensure that they are accessible during a crisis. |
An example of “layered security” that comes under the best practices of implementing physical security (source)
Challenges and considerations in physical security planning
When creating a PSP, organizations could face several significant challenges. Some key considerations include the following:
- Technological integration complexity: Incorporating advanced technologies like CCTV, biometric systems, and motion detectors can greatly enhance security. However, integrating these systems with existing security protocols and ensuring their compatibility can be substantial. You must choose the right technology that fits the organization’s specific needs and implement it efficiently.
- Regulatory compliance: Navigating the varying legal and regulatory environments in which an organization operates can be challenging. You must ensure that all aspects of the PSP adhere to regulations such as OSHA, GDPR, etc.
- Cost implications: A robust physical security system can have a significant financial outlay. You should balance cost with the need for effective security measures.
- The human factor: Ensuring that all employees adhere to security protocols poses a significant challenge. This includes managing the human risk of noncompliance or insider threats. Continuous training and awareness programs are essential to mitigate this risk and maintain high-security awareness among staff.
- Dynamic threat landscape, scalability, and flexibility: The threat landscape constantly evolves, with new vulnerabilities emerging regularly. A PSP must be dynamic, scalable, and flexible enough to adapt to these changes. Regular updates and assessments are necessary to ensure security measures remain effective against the latest threats.
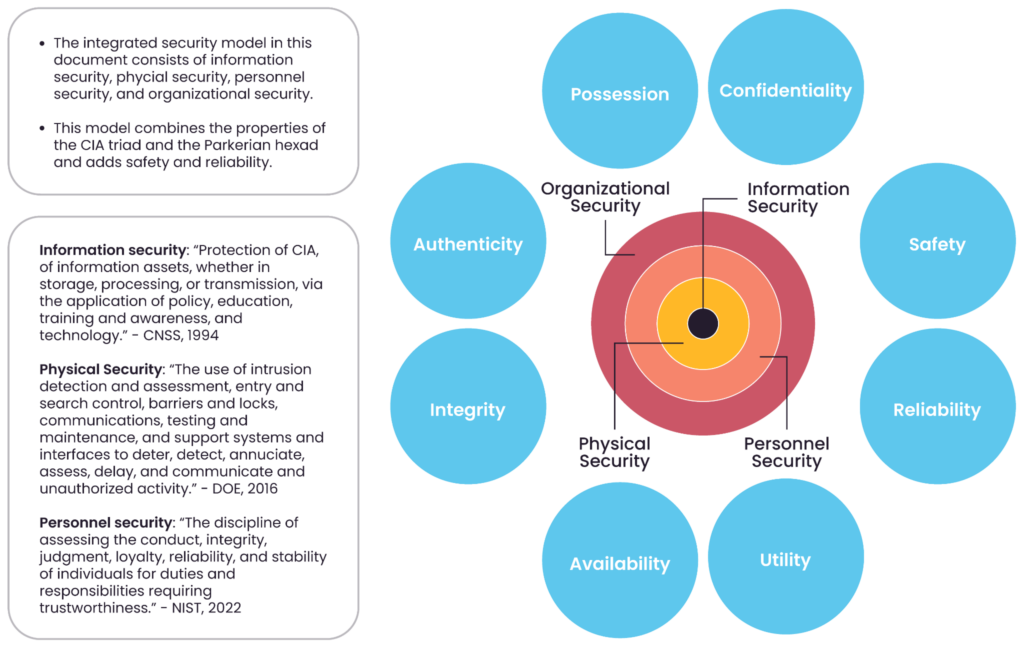
A visual representation of the challenges faced in physical security planning by highlighting the interplay between various domains of security: information, physical, personnel, and organizational. (source)
These considerations underscore the importance of a thoughtful, comprehensive approach to physical security beyond implementing standard measures and involve strategic planning, continuous evaluation, and adjustment.
Physical security plan sample
Here’s a sample PSP organized by section with descriptions and subcategories.
Purpose
Description: State the plan’s purpose.
Responsibilities
Description: List the people responsible for physical security and their specific responsibilities.
Policies
Description: Define security levels and associated priorities.
Subcategories:
- Area security:
-
- CATEGORY I: Maximum Level Security.
- CATEGORY II: Advanced Level Security.
- CATEGORY III: Intermediate Level Security.
- CATEGORY IV: Basic Level Security.
Access control measures
Description: Categorize restrictions by personnel, materials, and vehicles.
Subcategories:
- Personnel access: Authority for access. Criteria for access (company personnel, visitors, maintenance personnel, contractors, emergency response teams).
- Identification and control: Description and application of the system (company personnel, visitors, vendors, contractors, fail-safe procedures during power outages).
- Material control: Requirements for admission, search and inspection, and special controls.
- Vehicle Control: Search policy, parking regulations, entrance controls (company vehicles, privately owned vehicles, emergency vehicles, vehicle registration).
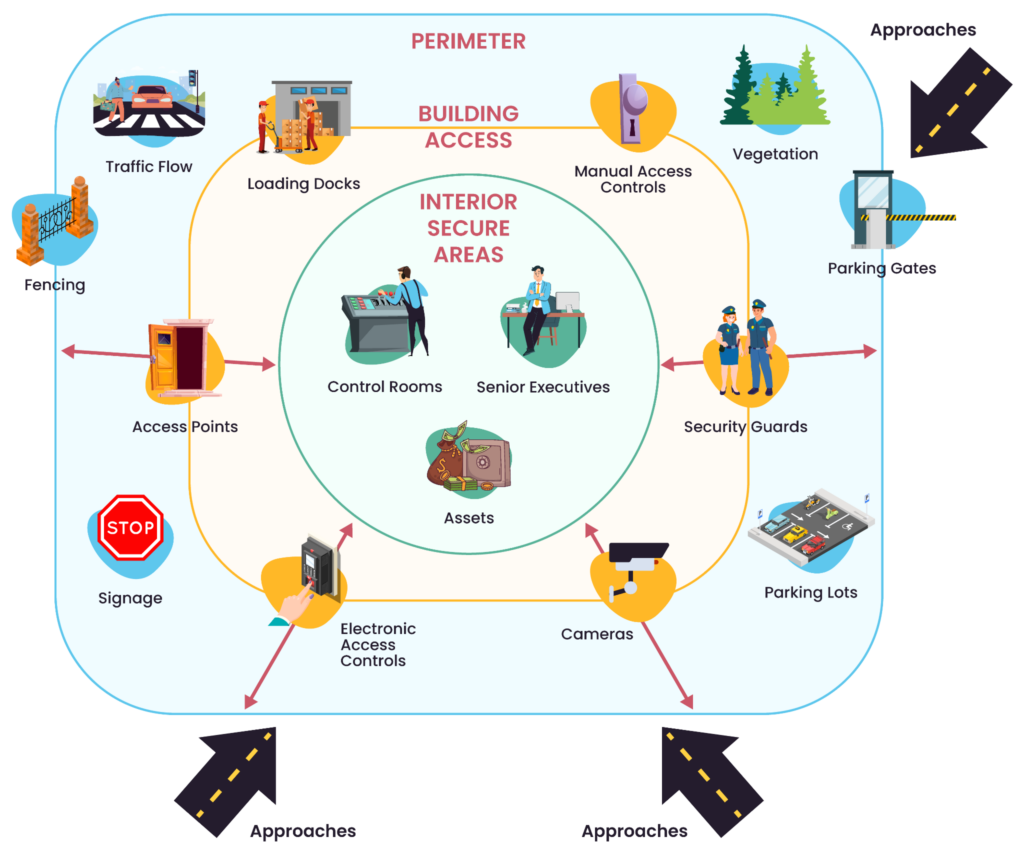
Physical security measures
Description: Protective barriers, CCTV systems, lighting, IDS, and communication protocols.
Subcategories:
- Protective barriers: Fences, clear zones, signs, gates (location, hours, security requirements, barrier plan).
- CCTV systems: Installation, monitoring, remote access, maintenance.
- Lighting systems: Use, inspection, and power failure protocols.
- IDS: Security classification, inspection, use and monitoring, alarm conditions, maintenance.
- Communications: Locations, use, tests, authentication.
- Security forces: Composition, tour of duty, posts, weapons, training, alert forces.
- Contingency plans: Emergencies (terrorism, bomb threats, hostage situations, disasters).
Annexes
Description: Detailed actions for specific threats, disasters, and disruptions.
Subcategories:
- Threat response plans: bomb threats, civil disturbances, natural disasters, operational disruptions (work stoppages).
Conclusion
A well-structured physical security plan protects valuable assets, infrastructure, and personnel and supports broader cybersecurity and organizational resilience. Security strategies must adapt to evolving threats, regulatory demands, and technological advancements for the military and the private sector.