Physical Security Controls: Modern Best Practices
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
Physical security controls protect an enterprise’s assets, personnel, and infrastructure from physical threats, including unauthorized access, theft, vandalism, and natural disasters. These controls are structured in layers and range from deterrent and preventive to compensatory and recovery, ensuring the security of digital and physical assets. They are essential to strengthening an organization’s physical security cybersecurity and provide a fundamental deterrent to threat actors. Implementing suitable physical security controls is vital to achieving robustness in financial institutions, government offices, residential areas, shopping centers, and commercial building security systems.
This article examines nine categories of physical security controls. It discusses the systems and technologies that implement these controls and their application in various environments. It also outlines best practices for implementing these controls. The article aims to ensure that organizations have a solid and effective physical security structure.
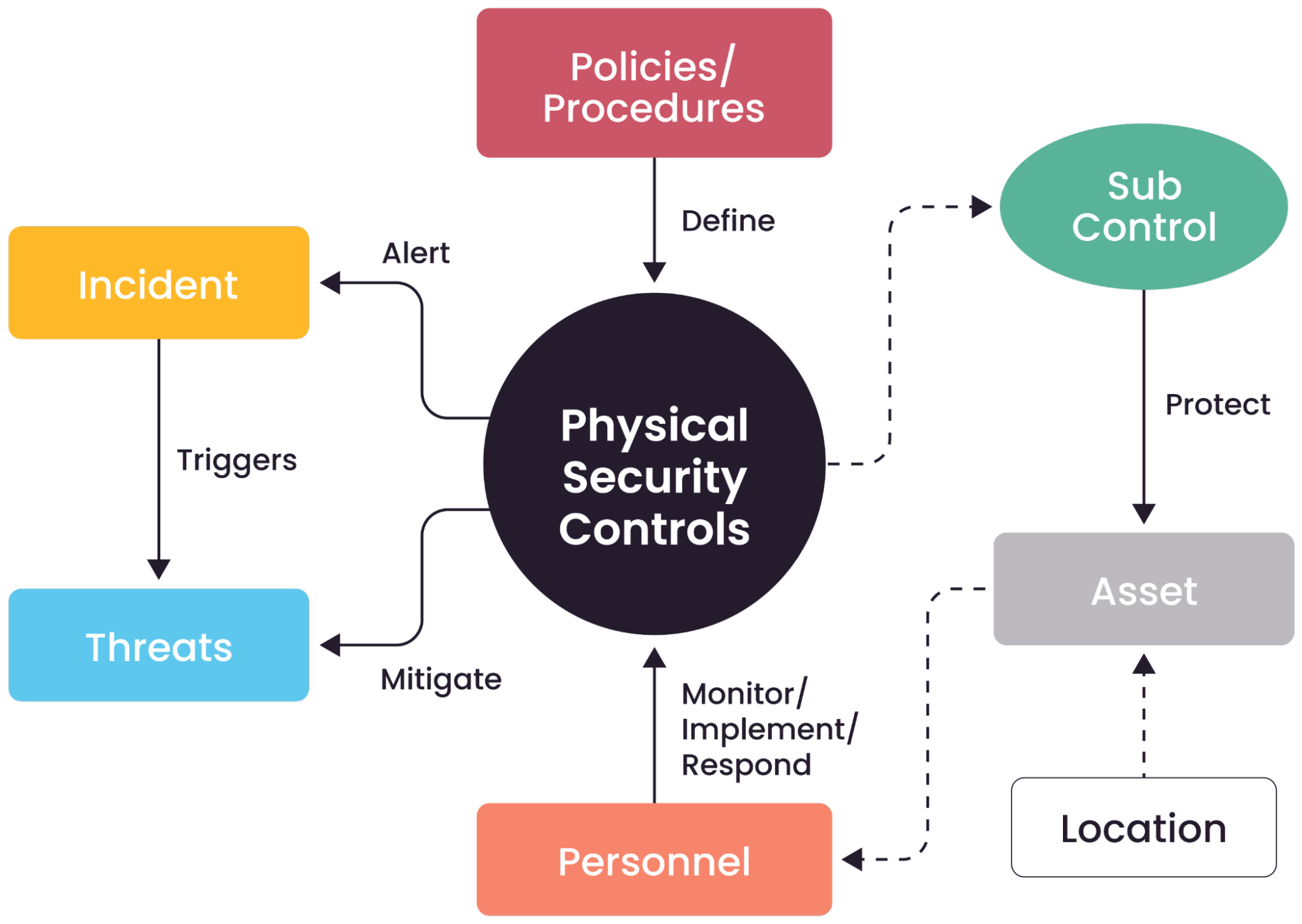
A logical overview of the relationships among physical security controls, assets, personnel, threats, and incidents
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Summary of physical security control categories
| Control category | Purpose |
|---|---|
| Deterrent controls | Discourage potential attackers or unauthorized access by creating a perception of security presence |
| Preventive controls | Physically block or mitigate unauthorized access before a threat can materialize |
| Detective controls | Identify and alert about unauthorized or suspicious activity in real-time |
| Corrective controls | Respond to and mitigate the damage of security incidents after they have occurred |
| Compensatory controls | Provide alternative protection in scenarios where primary controls are inadequate or detective controls indicate an ongoing security breach |
| Recovery controls | Help recover assets or operations following a breach or disaster; these are forms of disaster recovery plans and business continuity plans |
| Environmental Controls | Guard against environmental threats such as fire, flooding, or extreme weather |
| Cyber-physical controls | Manage and monitor interactions between digital systems and physical security systems, ensuring the security and optimal performance of operational technology and information technology devices |
| Administrative controls | Manage and enforce the proper implementation of physical security by guiding personnel behavior and decision-making |
Deterrent controls
Deterrent controls discourage potential attackers by creating a visible security presence; they focus on instilling a risk perception in those considering unauthorized actions. These controls are implemented to reduce the likelihood of security violations. Here are some examples:
- Guards and robot sentries provide a human or robotic presence to deter and respond to security incidents. Robot sentries for security patrols are becoming increasingly common due to their accuracy in real-time threat detection.
- Alarm output devices trigger audio and visible alerts when unauthorized access or suspicious activities are detected. Examples of these devices are sirens and strobes.
- Warning signs are displayed to alert individuals of video surveillance, potential hazards from live electric fences, and the presence of security dogs.
- Fencing and walls create physical barriers to deter unauthorized entry. These structures serve as the first line of defense, making it visibly and physically challenging for intruders to gain access.
- Perimeter lighting includes motion-triggered, ambient-light-triggered, and photocell-based lights. Sometimes, a combination of these is used to deter nighttime intruders.
Preventive controls
Preventive controls form the first line of defense by physically preventing unauthorized access and mitigating potential security threats before they materialize. These controls include physical barriers, lighting systems, and access control technologies.
Take security locks, for instance: a key element of preventive controls. These locks incorporate mechanisms to resist tampering and picking. Mechanical locks offer reliability, while electronic locks improve security with fail-secure strike locks (which remain locked during power interruptions) and fail-safe magnetic locks (which unlock in emergencies to ensure safe egress).
The diagram below illustrates how these mechanisms operate during power interruptions.
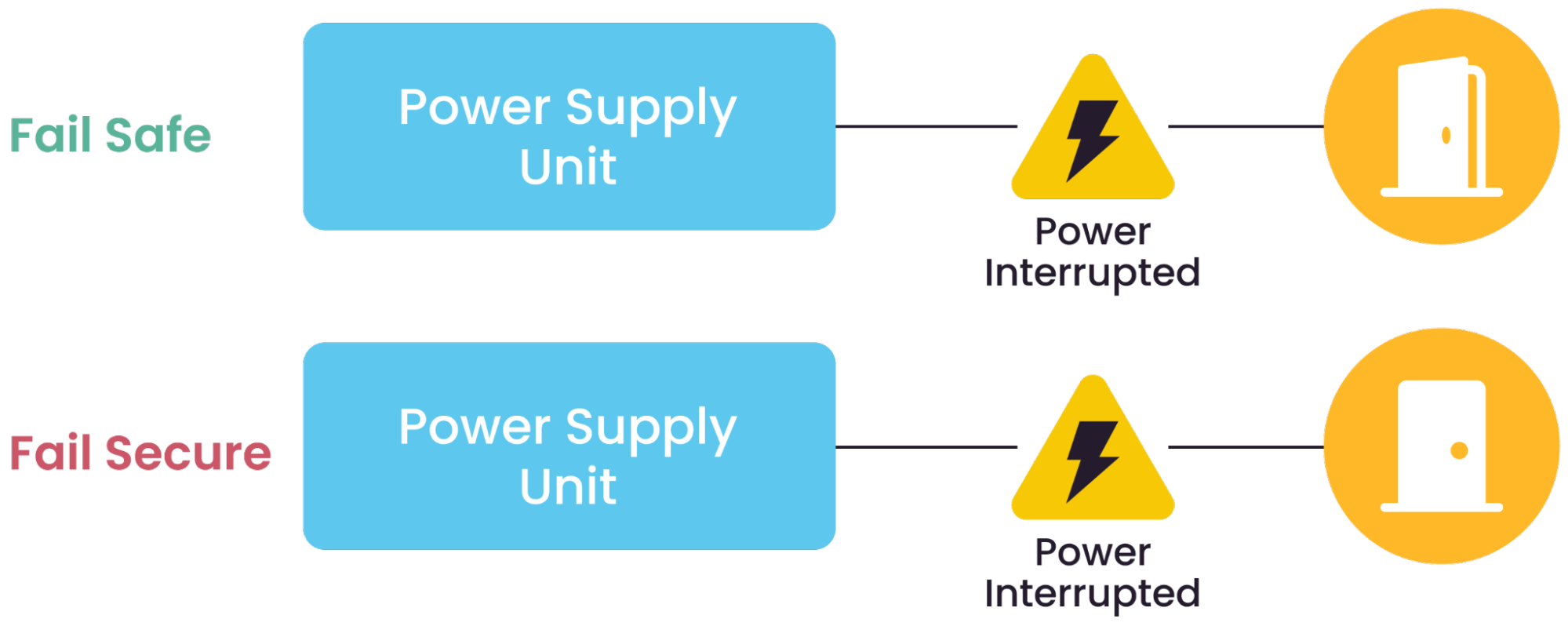
A diagram of the controls of electronic locking mechanisms during power interruptions
Equally critical are access control systems, which regulate entry and exit into restricted zones and monitor and log activities for security audits. These systems include:
- Card readers and keypads: These devices authenticate access through credentials such as keycards or PINs. Depending on the chosen technology—RFID, magnetic stripe, or smart cards—they operate at different frequencies (125 kHz for low-frequency RFID or 13.56 MHz for high-frequency RFID) to ensure security.
- Biometric systems: These authenticate individuals using unique physical traits like fingerprints or facial recognition, adding an extra layer of security that is difficult to replicate.
Other preventive controls include turnstiles, vestibules, and security gates, which are pivotal in regulating and monitoring the movement of individuals entering and exiting a facility. Electric fencing provides a deterrent barrier at facilities’ perimeters by delivering a high-voltage electric current along the fence line. For the secure storage of sensitive documents, valuables, and equipment, safes and vaults offer preventive control, with some offering features such as a multiuser-dependent “bank mode” and dispatch-center-reliant interactive code systems to ensure proper access controls.
Detective controls
A good physical security design prioritizes technologies and systems that detect and alert security teams about unauthorized access or suspicious activity. If well implemented, detective controls identify and expose potential intruders or attackers as they attempt to gather information on accessing the premises.
Here are standard detective controls ordered by ease of implementation, effectiveness, and applicability in commercial building security systems:
- Surveillance systems: Video analytics enhance surveillance by using AI for automated tasks such as facial recognition, people counting, and automatic number plate recognition (ANPR). This enables real-time detection and control of access to restricted areas through remote monitoring systems. Market.us Scoop’s 2024 “Physical Security Statistics” Report indicated that 40% of companies have adopted surveillance as a physical security control.
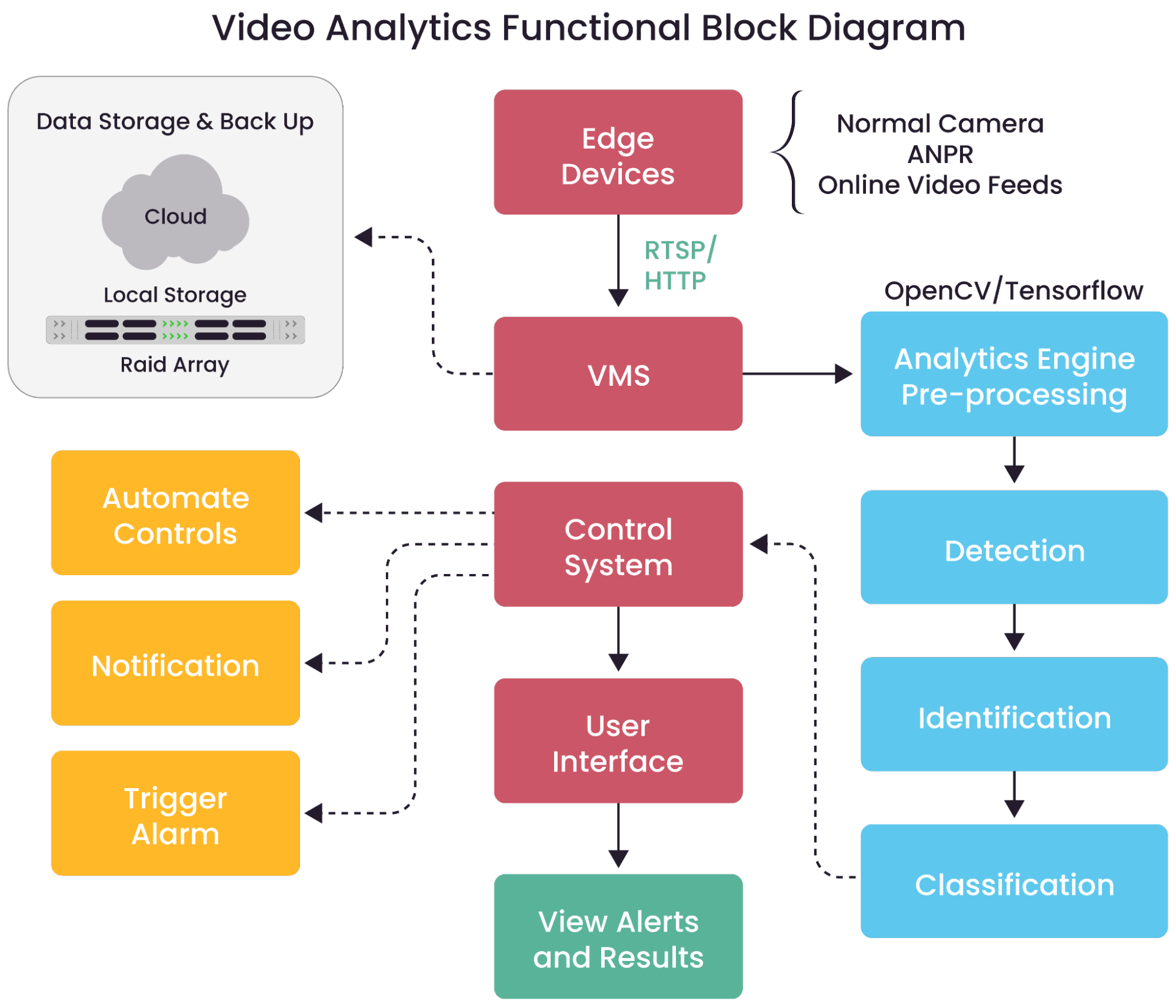
A functional block diagram illustrating video analytics and the associated controls.
- Intrusion detection systems: These systems use various peripheral input devices—such as circuit-based sensors, motion detectors, panic buttons, glass break sensors, and pressure mats—to accurately detect unauthorized access to restricted areas.
- Security patrols and monitoring systems: These systems, including routine checks by personnel and the deployment of robotic sentries, serve as detective controls in physical security by actively monitoring premises for suspicious activity or breaches.
- Virtual fencing: This approach uses underground sensors that detect vibrations or pressure changes when crossed. These systems trigger alarms when an intruder crosses the invisible boundary, offering a discreet way to secure perimeters.
Corrective controls
These controls react to security breaches and incidents, stopping or mitigating damage after it occurs. They include:
- Fire suppression systems: Automatic sprinkler systems and portable fire extinguishers serve as corrective controls to detect, suppress, and control fire hazards by rapidly deploying water or fire-retardant agents.
- Power backup solutions: Security breaches often target the power sources for physical security systems first. Backup batteries maintain or restore power for detective and preventive control systems to maintain functionality. Most physical security systems use linear or switched-mode power supplies.
- Emergency exit systems: Emergency exits should have visible exit signs and devices such as key guards and break glass for emergency door release. These devices are usually integrated with alarm systems to ensure proper logging and response during an emergency activation.
Compensatory or response controls
These measures provide an alternative solution to enhance security when primary controls (deterrence, detective, and corrective) fail or are insufficient. A common practice is manual security checks, which involve dispatching response crews to premises with reported alarm signals. Central monitoring systems are crucial in these response controls, as they receive alarms and intelligent CCTV alerts.
Additionally, temporary controls are implemented in access control systems to enforce the fail-secure protocol during system outages. This protocol ensures the automatic closure of all entry points when the server is offline and edge devices, such as readers, cannot retrieve access-level data, effectively blocking unauthorized access while maintaining security.
Recovery controls
Recovery controls are measures implemented with physical security systems to restore operations or facilities after a security breach or disaster. There are two common recovery controls applied in physical security:
- Data recovery systems: Every physical security system should incorporate a local or cloud-based database backup that an engineer can use to restore following an incident that leads to data loss quickly.
- Systems and instance replications: Physical security engineers should implement replication of any video management system or security information and event management system. Instance replication allows for quick failover to a mirrored system if the primary system is physically or cyber-compromised, supporting robust business continuity planning.
Environmental controls
These controls safeguard facilities and assets from environmental hazards like natural disasters and extreme conditions. These systems protect against fire, flooding, gas leaks, or extreme weather. They include the following:
- Uninterruptible power supplies (UPS) and surge protectors: A physical security system should be implemented to protect devices from voltage surges and sudden power losses.
- Fire suppression systems: Use sprinklers, gas, or foam to extinguish fires and protect equipment.
- HVAC systems: Maintain optimal temperature and humidity to protect sensitive equipment.
- Environmental detection sensors: Modern alarm systems utilize IoT devices, such as water leak and gas leak sensors, to enhance the functionality and responsiveness of traditional alarm systems, providing real-time monitoring and alerts for environmental hazards.
Cyber-physical controls
These measures and systems manage and monitor interactions between digital and physical security systems, ensuring safety, security, and functionality.
Cyber-physical controls include:
- Security information and event management systems that Integrate physical and cyber security monitoring
- Network segmentation to isolate sensitive systems from general access to enhance security
- Access logs and audits that record and review access attempts and activities to detect and respond to anomalies, possibly by implementing visitor management systems
- Physical security management software offers a comprehensive cyber-protection solution that enhances the security of physical security systems by automating device hardening, effortless password rotation, reliable firmware upgrades, and efficient certificate management.
Physical security management software protects the attack surface created by physical protection systems connected to the network, like IP cameras and physical access control devices. SecuriThings offers the industry’s most comprehensive physical security management software, which covers the lifecycle of physical device management with features such as maintaining inventory, installing operating systems patches, rotating passwords, and generating regulatory compliance reports.
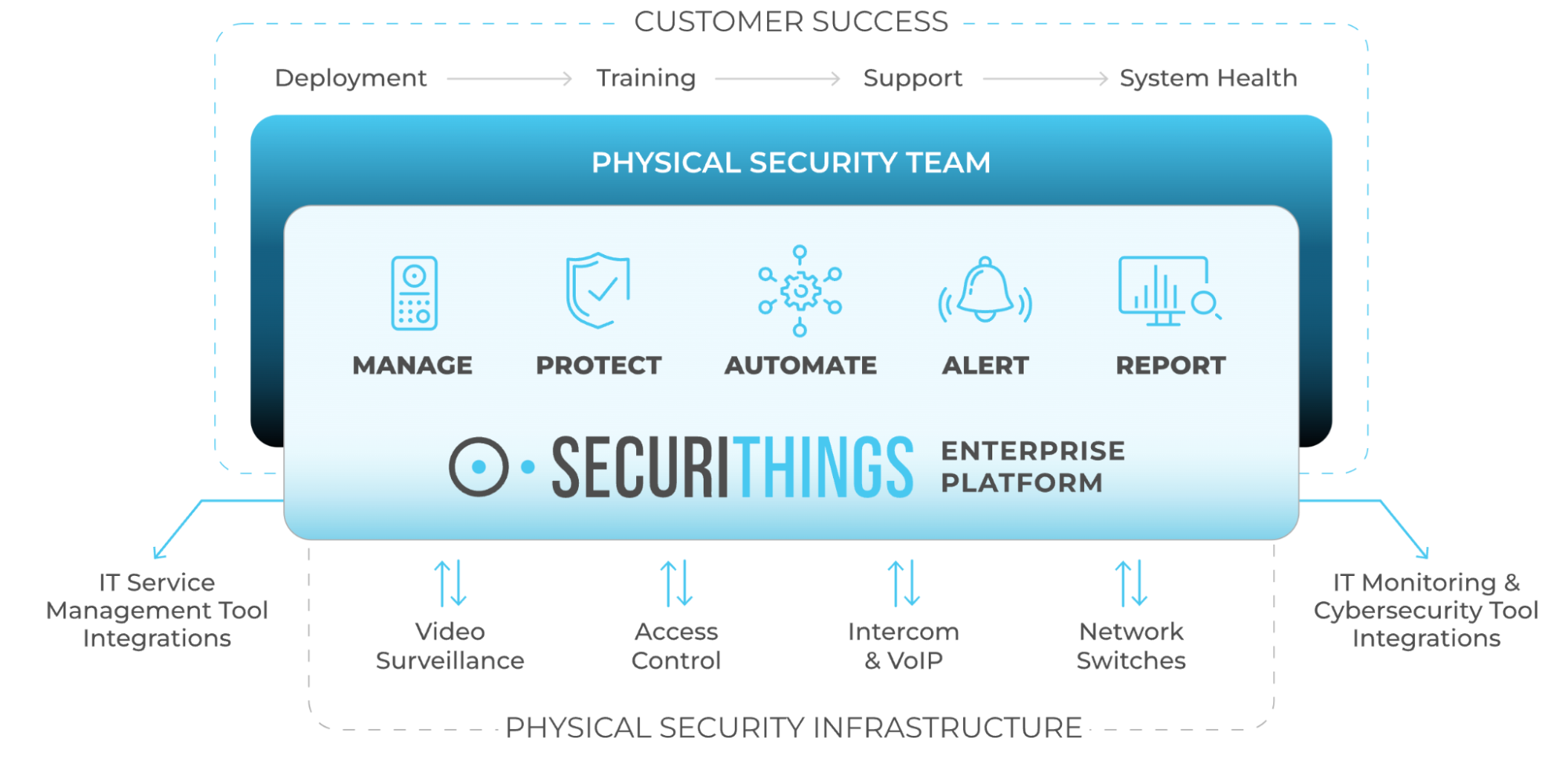
Administrative controls
These involve policies, procedures, and measures that govern the implementation and management of physical security. These controls ensure that physical security measures are correctly applied, maintained, and aligned with an organization’s risk management strategies:
- Security policies and procedures: Organizations should establish detailed policies that define the implementation and management of physical security systems, such as CCTV, access control, and alarm systems.
- Access control management: Administrative controls define how access to physical security systems is managed.
- Training and awareness: Organizations should ensure that employees are trained on physical security protocols, such as how to use access control systems (e.g., RFID cards or biometric systems), respond to alarms, and identify potential security threats.
- Incident response plans: These include detailed steps for reporting incidents, triggering alarm systems, and activating emergency exits or lockdowns.
Application of physical security controls across various environments
The table below describes the application environments of the various control categories discussed above and examples of relevant systems.
| Control category | Application environment | Examples of systems |
|---|---|---|
| Deterrent | Office buildings, malls, schools | Electric fences, warning signs, perimeter lighting, guards |
| Preventive | Banks, government offices, data centers | Security locks, access control systems, biometric systems, electric fencing |
| Detective | Embassies, military bases, high-security corporate buildings | Surveillance systems, motion detectors, intrusion detection systems, virtual fencing |
| Corrective | Data centers, hospitals, large corporate establishments | Fire suppression systems, backup batteries, emergency exit systems |
| Compensatory | Airports, financial institutions, telecom facilities | Manual security checks, temporary access controls, fail-secure protocols |
| Recovery | Financial institutions, cloud
service providers, data centers |
Data recovery systems, system replications, business continuity plans |
| Environmental | Data centers, labs, server rooms | Uninterruptible power supplies (UPS), fire suppression systems, HVAC systems |
| Cyber-physical | Industrial facilities, smart buildings, airports | Security information and event management systems, network segmentation, visitor management systems, physical security management software |
| Administrative | Corporate offices, government institutions | Security policies, training programs, incident response plans |
Conclusion
Physical security threats are ever-evolving, placing greater responsibility on engineers to implement robust systems that wholesomely protect an establishment. The layered approach to physical security controls spanning deterrent, preventive, corrective, and recovery measures ensures comprehensive protection across various environments.
To enhance these efforts, integrating innovative platforms like SecuriThings can revolutionize the management of physical security controls by automating device hardening, ensuring compliance, and minimizing cyber risks. For engineers, adopting such innovative platforms is an enhancement and a necessity to future-proof infrastructure against emerging threats. Take the next step: Optimize your security systems.


