Retail Security Systems & Best Practices
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
- Chapter 13: Best Practices for Corporate Physical Security
- Chapter 14: Physical Security Best Practices
- Chapter 15: How physical security powers
- Chapter 15: Best Practices for Physical Security Devices
Over the past few decades, retail security has shifted from simple standalone systems to interconnected, technology-driven solutions. This evolution has narrowed the gap between physical security and cybersecurity, with attackers able to exploit networked devices like IP cameras and access control terminals. Ensuring robust protection now requires integrating physical and digital security measures to address the vulnerabilities introduced by these systems.
Retail environments present unique challenges for security systems. Unlike industrial or residential security applications, retail systems must prevent theft while maintaining a seamless shopping experience. As a result, a balance must be maintained between customer accessibility and resilient asset protection.
This article explores what distinguishes retail security systems from other applications, delving into their unique nuances, key components, implementation best practices, and real-world scenarios. We also address potential challenges that could arise from deploying these systems and provide approaches for risk mitigation.
Summary of key retail security system concepts
The table below summarizes the key retail security system concepts this article will cover in more detail.
| Concept | Description |
|---|---|
| Retail security system attributes | Retail systems have high traffic volumes, accessibility needs, a dynamic threat landscape, and the need to protect high-value items. As such, they are closely connected to cybersecurity. |
| Types of retail security systems | System types include access control systems for restricted areas, video surveillance with analytics for theft deterrence, intrusion detection for reporting unauthorized access, and fire safety systems for compliance and protection. |
| Integration with operations | For streamlined operations, security systems must integrate with retail operational systems, e.g., inventory and personnel management. |
| Physical security management software | Centralized platforms streamline the management of security systems across multiple outlets by providing real-time monitoring, compliance reporting, automated updates, and password management. |
| Strategies for design and implementation | These involve security risk assessment, integration opportunities assessment, system implementation, maintenance, and upgrades. |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Retail system attributes
Unlike their industrial and residential counterparts, retail security systems are designed to handle high customer traffic and transactions, making them more susceptible to a dynamic and ever-changing threat landscape.
The table below highlights how retail security systems differ from other applications:
| Feature | Retail systems | Industrial systems | Residential systems |
|---|---|---|---|
| Traffic volume | High and variable | Low to moderate | Low |
| Accessibility needs | Customer-friendly | Restricted | Open for residents and visitors |
| Threat landscape | Theft, shoplifting, emergencies | Industrial sabotage, theft | Burglary, personal safety |
| Surveillance needs | Wide-angle, high-resolution cameras | Specific-area monitoring | Limited coverage |
When designing retail security systems, consider four key factors: theft prevention, safety from hazards like fire, inventory management, access control, and emergency response:
- Loss prevention: Aim to minimize shoplifting and employee theft. Use a combination of computer vision, deep learning algorithms, and sensor fusion to track items customers take off shelves and match them to items checked out at the counters.
- Ensure safety: Implement fire detection and suppression systems. Link the detection systems to fire emergency response centers.
- Manage inventory: Monitor stock levels and prevent shrinkage. Use cameras with analytics to analyze item picking from shelves and forecast inventory levels for specific products.
- Access control: Install biometric access control systems to restrict entry to sensitive areas like storage rooms and employee-only zones.
- Facilitate emergency response: Integrate intrusion detection systems with central monitoring stations.
Relationship with cybersecurity
Retail security systems, such as IP cameras and access control devices, are no longer standalone but rather integrated into IT networks. This connectivity exposes them to vulnerabilities, including cyberattacks that can compromise sensitive data, disrupt operations, or render security features inoperative.
To address these risks, integrate physical security with cybersecurity measures. This approach ensures protection by implementing the following strategies:
- Encryption: Encrypt data streams, whether video footage from cameras or access logs from control devices, during transmission and in storage.
- Device monitoring: Use monitoring tools to track device status, firmware versions, and suspicious activities, enabling proactive responses to potential threats.
- Network segmentation: Isolate security devices on dedicated VLANs or subnets to reduce exposure to broader network risks.
- Authentication and access control: Implement strict authentication mechanisms, such as multi-factor authentication (MFA) and role-based access control (RBAC).
Customer flow management
Retail security systems must manage customer flow while maintaining security. The table below details security measures that need to be installed in retail spaces, their impact on customer convenience, and mitigations offered by retail security systems.
| Security measure | Impact on customer convenience | Mitigation strategy |
|---|---|---|
| Bag checks at entry | Potential delays | Use trained staff for quick checks, complemented by baggage scanners, metal detectors, and other screening equipment. |
| Surveillance cameras | Privacy concerns | Display clear signage about the presence of surveillance cameras. |
| Restricted Access Areas | Limited customer access | Employ proper signage and staff guidance. Install biometric access control systems. |
High-value item protection
Retail stores often carry high-value items that require additional security measures, such as display case alarms and RFID tagging. Here are some example scenarios and associated best practices.
Scenario 1: An electronics store uses RFID tags on high-value items like laptops and smartphones.
Best practice: Use RFID readers at the exit doors to trigger an alarm if someone tries to leave without paying.
Scenario 2: A jewelry store uses biometric access control in and out of the main door to restrict entry and egress only to authorized individuals.
Best practice: Use mantraps to manage access flow effectively or integrate video intercom with access control at entry points for additional verification.
Integration with retail operations
Retail operation systems, such as point-of-sale (POS) and inventory management, integrate with retail security systems to enhance efficiency. Use cameras equipped with heat map analytics features or thermal imaging cameras to track foot traffic and identify activity hotspots.
Scenario 1: A retail chain integrates its video surveillance system with the POS system. If an item is scanned at the register but not bagged, the system flags the transaction, and security staff can review the footage to investigate potential fraud.
Scenario 2: A supermarket uses thermal cameras to identify hotspots. This information is used to manage inventory, improve sales, optimize store layouts, and allocate resources.
Access control systems
Access control systems restrict entry to sensitive areas, such as storage rooms and office spaces where managers keep the store’s cash. Modern access control solutions provide an adaptable framework to safeguard critical areas and maintain business continuity in an industry where high employee turnover and external deliveries are common.
Scenario: A retail store installs a biometric access system for its storage room. Employees present their biometrics to enter, and the system logs all access attempts. During inventory restocking, delivery personnel are granted temporary access via time-bound credentials such as QR codes.
Best practices:
- Multifactor authentication: Use multifactor or multiuser authentication for high-value inventory areas. For example, have both the hotel manager and chef of the hotel restaurant authenticate with their fingerprints before the store door opens.
- Access log analysis: Regularly audit access logs for unusual activity, such as suspicious access attempts or after-hours entries. Use software platforms that automate audit trail analysis.
- Scalability: Implement scalable systems to accommodate temporary or seasonal workers. Modern access control systems enable you to define specific access periods for each user’s access level and issue temporary credentials, such as one-time QR codes.
- Use role-based access control (RBAC): Minimize the risk of unauthorized access and potential breaches by limiting access to outlet areas based on user roles.
Video surveillance systems
Video surveillance systems (also known as closed-circuit TV or CCTV systems) in retail environments are more than just security tools: They provide operational efficiency and improve customer experience. Modern video surveillance systems offer proactive monitoring, support incident investigation with ease of evidence retrieval, and provide insights by analyzing customer behavior and store traffic patterns.
Scenario: A department store deploys high-definition IP cameras with advanced analytics to monitor customer behavior. Cameras in high-risk sections, such as the electronics department and jewelry counter, send real-time alerts to security personnel when motion is detected outside business hours.
The following table provides camera placement recommendations.
| Area | Recommended camera type | Purpose |
|---|---|---|
| Entrance and exit | Wide-angle IP cameras
People counting cameras |
Monitor customer flow and prevent theft.
Track foot traffic, analyze customer behavior, and optimize store operations. |
| Cash register | Fixed-focus cameras | Record detailed footage of transactions. |
| Stockroom | PTZ cameras | Enable flexible monitoring of stock areas. |
| Retail aisles | Thermal imaging
Heat mapping |
Identify high-traffic areas. |
Here are some best practices in this area:
- API integration: Integrate cameras with point-of-sale (POS) systems to flag suspicious transactions and correlate footage with transaction data.
- Optimal camera positioning: Position cameras to eliminate blind spots and comply with privacy laws to avoid legal liabilities.
- Video management systems: Use cloud-based VMS for secure footage storage and analytics.
Intrusion detection systems
Intrusion detection systems safeguard retail spaces during non-operational hours by monitoring unauthorized entries. These systems act as sentinels, using advanced technology to detect breaches in real time and mitigate potential threats before damage occurs.
Example scenario: A jewelry store installs motion detectors and glass-break sensors linked to an alarm system. If triggered, the system alerts the store owner via a mobile app and activates the alarm.
Best practices:
- Intruder verification as a service (IVaaS): Integrate intrusion detection with surveillance and access control systems to improve response accuracy and reduce false alarms.
- Multi-technology sensors: To reduce false alarms, use tri-technology sensors (e.g., infrared, PIR, and microwave). These advanced sensors eliminate issues caused by pets or inanimate objects, as they combine multiple detection methods to cross-verify triggers and ensure accuracy.
- Firmware updates: Test and update system firmware regularly to ensure functionality. Additionally, explore platforms that offer device health monitoring, enabling the detection and execution of over-the-air (OTA) updates for control panels and peripherals.
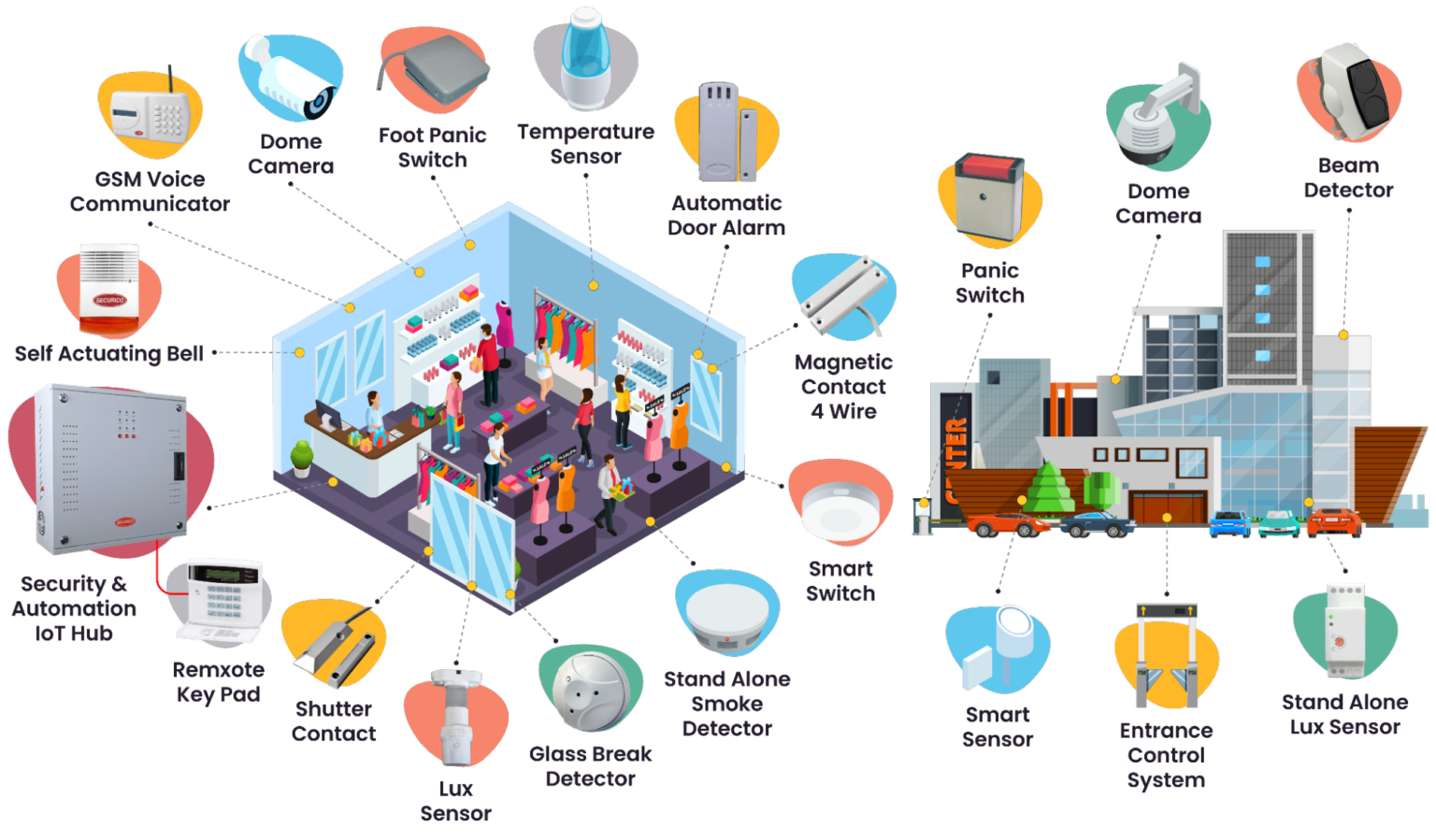
Smart intrusion detection system for retail chains
Fire safety systems
Fire safety systems are critical for protecting lives and assets, especially in environments with high customer traffic.
Scenario: Imagine a clothing store with a fire safety system integrating smoke detectors with an automatic sprinkler system. When smoke is detected in the storage room, which has a high concentration of flammable materials, the smoke detectors activate the fire alarms, notifying everyone in the store. Simultaneously, the sprinkler system is triggered, suppressing the fire until emergency responders arrive on the scene.
Follow these best practices with these systems:
- Maintenance: Conduct routine fire drills and regular system maintenance of all devices.
- Optimal sensor positioning: Place detectors in high-risk areas like kitchens or stockrooms, but use heat detectors in areas prone to smoke.
- Compliance: Ensure compliance with local fire safety regulations. This may include displaying fire system inspection certificates.
- Emergency response center reporting: Configure reporting through a communicator to relay signals for response in case of emergencies.
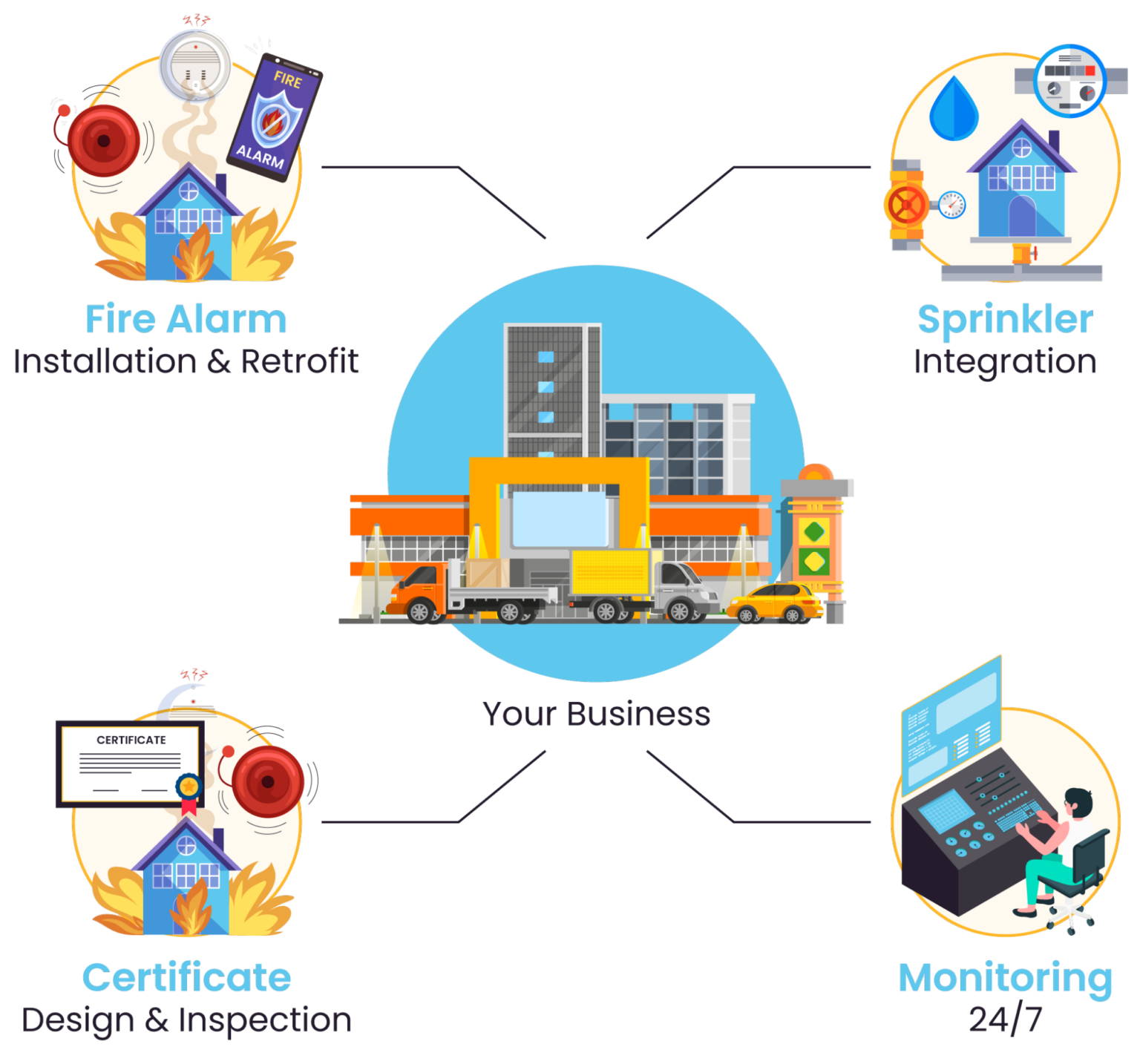
Key considerations for a fire detection and suppression system (source)
Integration with retail operations
Integrating security systems with operational tools like point-of-sales (POS) systems, analytics platforms, and inventory management software benefits retail environments.
Here is a table that details the retail security systems, the operations they can integrate with, and the approach and technologies typically used.
| Integration | Approach | Technologies | Systems |
|---|---|---|---|
| Video surveillance integration | Link CCTV cameras to point-of-sale (POS) systems to monitor transaction activity. | IP cameras, video management systems, POS software | CCTV systems, POS systems |
| Access control integration | Restrict employee access to certain areas based on role or time of day. | RFID, biometric scanners, keypad systems, and access control hardware | Access control systems, time management systems |
| Intrusion detection systems | Trigger alarms when unauthorized entry is detected in restricted areas. | Motion sensors, glass break detectors, PIR sensors, alarms | Alarm systems, building management systems |
| People counting systems | Monitor foot traffic at store entrances to optimize staffing and layout. | Infrared sensors, thermal cameras, IoT sensors | POS systems, analytics platforms |
| Heat mapping integration | Analyze customer movement patterns to optimize store layout and product placement. | Thermal cameras, data analytics software, IoT sensors | Store layout systems, analytics platforms |
| Electronic article surveillance (EAS) | Detect stolen merchandise through EAS tags at exits. | EAS tags, RFID, antenna systems | EAS systems, POS systems |
| Real-time location systems (RTLS) | Track assets, staff, and inventory across the store in real time. | RFID, Bluetooth Low Energy, ultra-wideband | Inventory management systems, staff management systems |
| Video analytics | Use AI to detect suspicious behavior or analyze customer interactions. | AI algorithms, machine learning, video analytics software | CCTV systems, AI analytics software |
| Alarm monitoring integration | Centralize all security alarms and notifications to a central monitoring station. | Alarms, monitoring software, IoT integration | Alarm monitoring stations, security operations centers |
| Mobile app integration | Enable remote access to security systems and alerts via smartphones. | Mobile apps, cloud services, IoT | Security management systems, cloud platforms |
| Incident management system integration | Log and manage security incidents automatically in a digital system. | Incident management software, cloud integration | CCTV, access control, alarm systems |
Best practices:
- API integration: Design and implement systems with seamless data sharing between security and operations via API. Most security software suppliers provide open APIs and SDKs.
- Monitoring: Monitor key performance indicators, such as shrinkage rates and customer dwell times.
Physical security management software
Retailers often operate multiple outlets, making managing security systems consistently across all locations challenging. Centralized security management software addresses these challenges by providing a unified platform for monitoring and controlling security infrastructure across sites. This centralization, however, requires connecting devices to an IP network, which introduces potential vulnerabilities that cybercriminals could exploit.
To mitigate these risks, physical security management software maintains comprehensive asset inventories, automates password rotations for devices and users, ensures the timely application of security patches, and generates compliance reports. These features improve security and streamline operational workflows, enabling retailers to focus on their core business.
The SecuriThings enterprise platform provides summarized insights into the performance of physical security tools, improving operational efficiency and minimizing downtime by offering real-time monitoring, alerts, firmware upgrades and patching, regulatory compliance reporting, and automated management of devices from various vendors.
As an example, consider a large mall that uses centralized security management software to oversee video surveillance, access control, and fire safety systems. Through a unified dashboard, security teams can monitor the status of all devices in real time, receive alerts for issues like disconnected cameras, and execute system-wide updates with minimal downtime. This approach enhances responsiveness to security events and reduces the risk of operational disruptions.
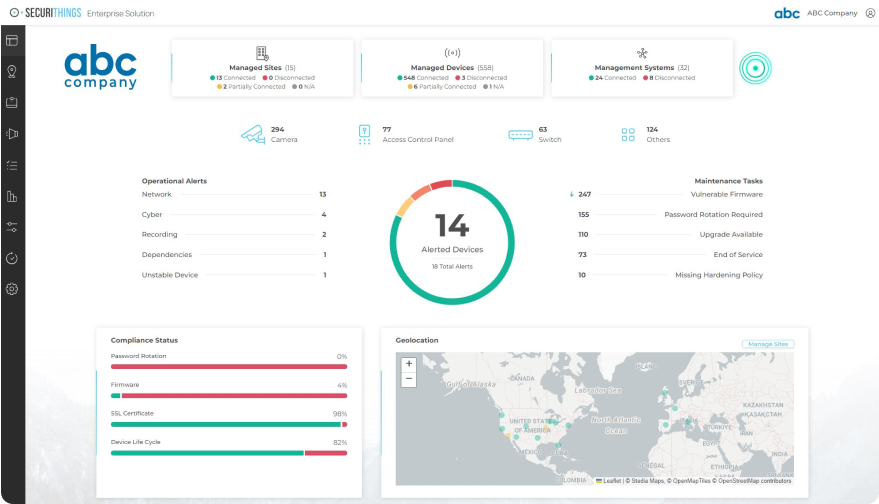
An example of a centralized platform for monitoring devices (source)
Platforms like SecuriThings enhance these capabilities by offering real-time monitoring, automated device management, and performance insights for systems from various vendors. By leveraging such solutions, retailers can maintain operational efficiency while ensuring robust security across all locations.
Strategies for design and implementation
Planning and assessment
Before implementing a security system, thoroughly assess the retail environment to identify security needs and potential vulnerabilities and to identify opportunities for leveraging data for decision-making.
Here’s a checklist for security assessment:
- Identify high-risk areas, such as entrances and exits, aisles with high-value items, storage areas, and points of sale.
- Evaluate current security measures, assessing their effectiveness, coverage, and integration within overall store operations.
- Consult with stakeholders (e.g., store managers, employees, and other key stakeholders) to understand their perspectives on security challenges.
- Identify key operational pain points that security solutions can address.
System integration
Ensure that all security systems are integrated for efficient operation and monitoring. This includes linking video surveillance with access control and intrusion detection systems.
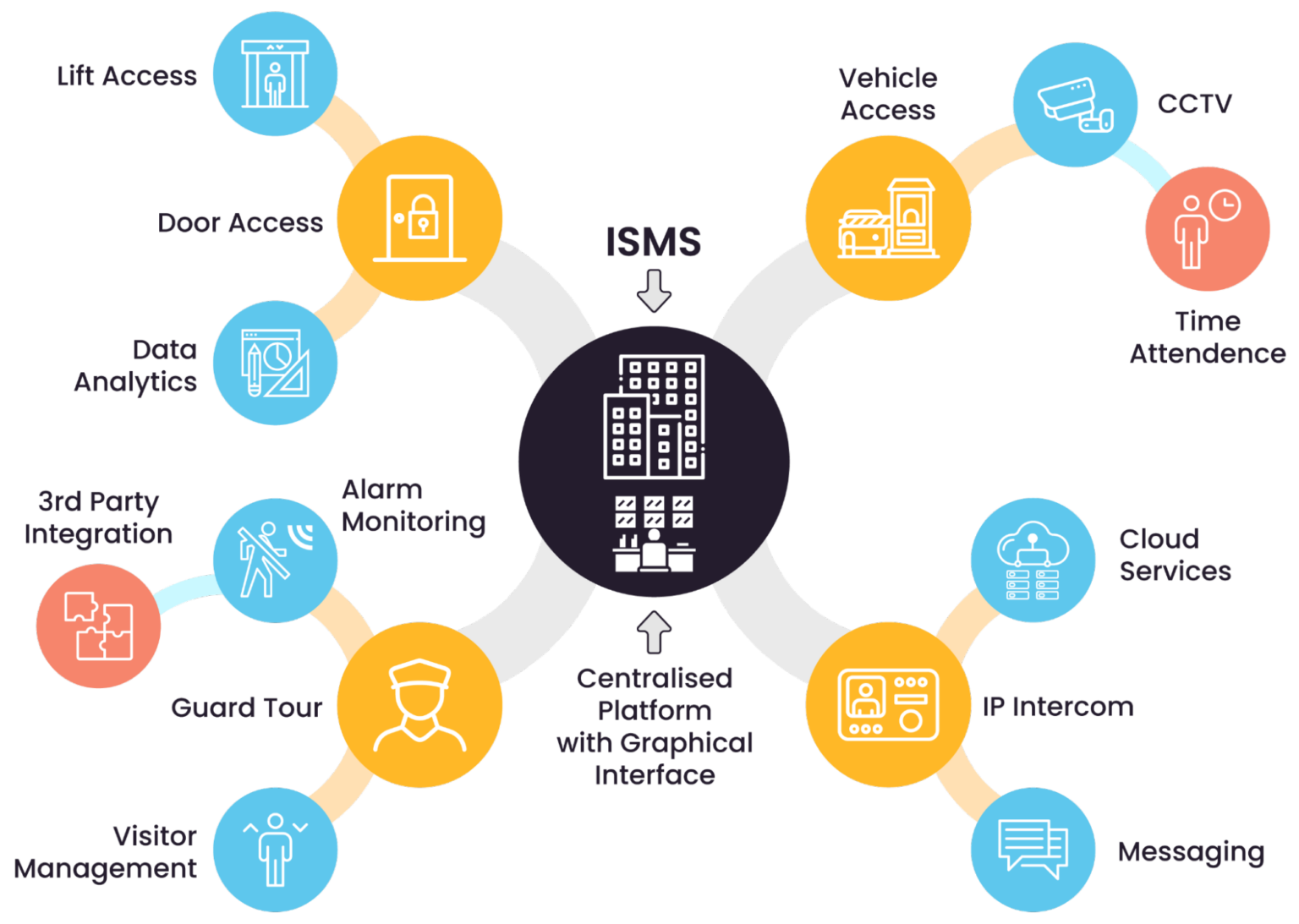
Integrated security management system architecture (source)
Regular maintenance and upgrades
Regular maintenance and updates to firmware are critical for keeping security systems effective and secure against emerging threats. Implement software updates to take advantage of new features and fixes to existing vulnerabilities
Schedule quarterly maintenance checks for surveillance cameras and intrusion detection sensors. Apply firmware updates to address vulnerabilities and enhance functionality.
Conclusion
Retail security systems must address diverse challenges, from theft prevention to customer safety and operational efficiency. In this article, we explored the unique requirements of retail security, focusing on access control, surveillance, intrusion detection, and fire safety systems. We highlighted the importance of integrating these tools with retail operations, such as POS systems and inventory management. By following best practices in design, implementation, and maintenance and using the full capabilities of physical security management software, you can build resilient systems that meet the dynamic demands of retail environments while mitigating risks.


