Critical Infrastructure Protection Program Best Practices
Power grids, communication systems, water facilities, and transportation networks form the backbone of national security, economic stability, and public safety. Any sector’s failure due to cyberattack, sabotage, cascading failure, or disaster can have severe consequences.
Understanding a critical infrastructure protection (CIP) program is more than a list of security controls. It’s a cross-functional, structured effort to align operational risk management with visibility, layered mechanism protection, access management, and compliance audit. A CIP program allows an organization to continually identify, evaluate, and mitigate risks to its critical services before those risks become incidents.
This article explores what it takes to build a mature, effective critical infrastructure protection program. It briefly highlights common challenges and offers practical actions around asset visibility, access control, and incident response. It also shows how intelligent platforms can support long-term program success.
Summary of key critical infrastructure protection program concepts
The table below summarizes four essential CIP program concepts that this article will cover in detail.
| Concept | Description |
|---|---|
| CIP program overview | High-level view of CIP, its importance, and its cyber-physical scope. |
| Common gaps in CIP programs | Key weaknesses in real-world implementations. Include visibility, access control, and coordination. |
| CIP program maturity level | Staged model showing how organizations evolve in managing infrastructure risk. |
| Best practices for building a CIP program | Practical guidance for security engineers and program managers for building a CIP program. |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Critical infrastructure protection program overview
Critical infrastructure protection programs are designed to protect the systems that support essential services such as electricity, communications, water, and transportation. These programs are not one-time compliance initiatives but ongoing efforts to manage risk across cyber and physical domains.
A mature CIP program puts asset identification, threat assessment, secure system design, access governance, and continuous monitoring under a unified strategy. It requires collaboration across operational, IT, and physical security teams to ensure that protective measures are implemented and consistently maintained.
Organizations face an ever-changing risk environment fueled by technological developments, increasingly complex attack surfaces, and growing interdependencies across systems. As a result, CIP programs must be agile, scalable, and responsive to emerging threats, with resilience and continuity as the final outcomes.
Common gaps in critical infrastructure protection programs
While many organizations have taken steps to align with critical infrastructure protection standards, a significant gap often remains between policy and execution. These gaps can appear at multiple levels, from individual assets to strategic coordination and weaken an organization’s ability to maintain resilience and compliance.
At the device level, commonly overlooked vulnerabilities include incomplete inventories, outdated firmware, expired certificates, and the continued use of default or weak credentials. These issues can be seen in physical security systems, such as access control panels and video surveillance cameras, because they are typically independent and generally always running. Also, you might have little visibility or control over physical security systems if the configurations are incorrect or they are down for an undetected period of time. This can ultimately harm your ability to comply with some basic CIP requirements.
From an operational standpoint, many organizations struggle with fragmented monitoring and reactive device management. Asset status changes or vulnerabilities can remain unnoticed for extended periods without centralized oversight or automated alerts. This increases response times and introduces inconsistencies in audit trails and evidence collection, which are critical for satisfying regulatory standards.
At the program level, gaps typically occur due to teams acting independently, inadequate coordination across teams, and poor integration of IT, physical security, and compliance. In some organizations, security teams are siloed from each other and can work in duplicate or be unaware of risk. In addition, the lack of standard processes to classify assets, assess vulnerabilities, and govern access made it impossible to consistently implement the controls across diverse systems and sites.
Strategically, many organizations lack a formal maturity model, long-term roadmap, or crisis-tested response framework to drive continuous improvement. Limited private–public collaboration, inadequate resource allocation, and reliance on static risk assumptions further reduce the agility of CIP programs. In several cases, external threat models are adopted without proper tailoring to the local infrastructure, leading to misaligned priorities and incomplete protections.
Closing these gaps requires more than fixing individual problems, it will require an operational shift towards integrated monitoring, real time risk management, and cross-functional governance, characteristics of a mature and resilient CIP program.
Critical infrastructure protection program maturity levels
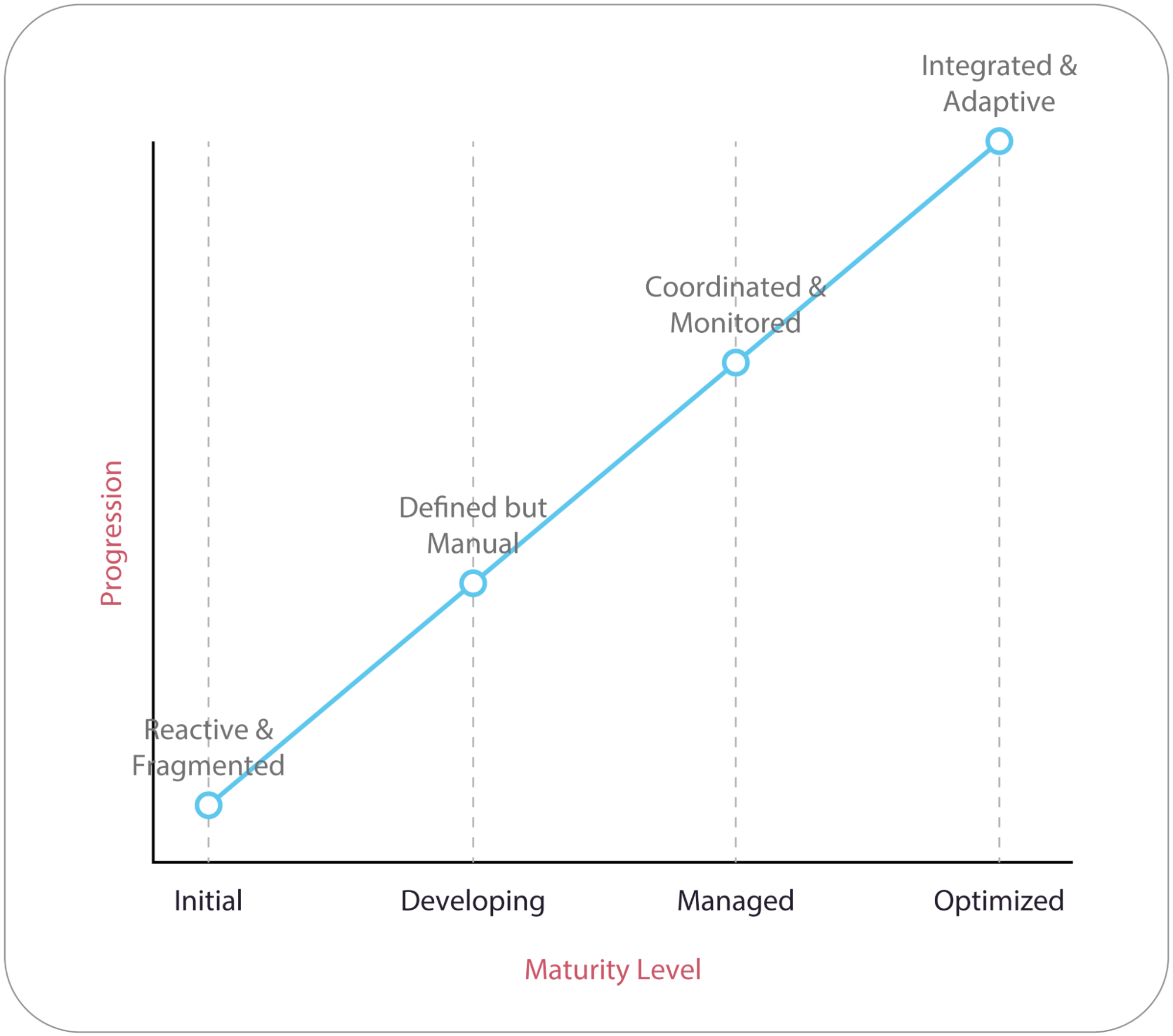
CIP Program maturity model. (Source)
CIP programs often start as broken and reactive implementations and evolve into coordinated, data-driven organizational approaches. This transition demonstrates how an organization can effectively account for, manage, control, and respond to threats to its physical and digital assets.
CIP maturity is not a fixed benchmark but rather a continuous journey. The following figure illustrates the progression of a CIP program maturity model, outlining how organizations evolve from basic, reactive practices to fully integrated and adaptive protection strategies.
The sections that follow break down each level of CIP program maturity.
Initial
At this stage, CIP is reactive mainly and fragmented. Security devices such as surveillance cameras, access control panels, or sensors may be deployed, but lack continuous oversight. Hardware and software Inventories are incomplete or outdated, and teams often rely on manual checks or remain unaware of device status. Critical issues such as expired certificates, default passwords, or firmware vulnerabilities go unnoticed until flagged during an audit or following an incident. Operational silos between IT, physical security, and compliance teams limit communication and leave critical gaps unaddressed. These challenges are often compounded by a lack of OT-specific cybersecurity expertise and an ongoing convergence of IT and OT environments without proper segmentation or strategic alignment. Compliance is approached as a one-time obligation rather than an ongoing responsibility.
Developing
In the developing stage, organizations start bringing structure to their CIP efforts. Assets are cataloged more consistently, and basic controls, like password policies or user restrictions, are introduced. But much of the work still relies on manual processes. Device health is tracked in spreadsheets or across different vendor systems, and issues like expired certificates or outdated firmware often go unnoticed until they cause problems.
There’s growing awareness of the need for better coordination, but teams still work in silos. Physical security, IT, and compliance may each have their tools and priorities, making it hard to respond quickly or apply consistent standards. The result is a program that meets baseline compliance but still lacks the visibility and agility needed for true resilience.
At this stage, introducing centralized platforms can make a big difference, helping teams catch issues earlier, reduce repetitive work, and shift from reactive to proactive
Managed
In the managed stage, CIP programs are now more uniform, coordinated, and measurable. Teams can collaborate with centralized tools that provide real-time visibility into device status, system health, and configuration changes. Organizations do not have to manually chase down issues since they have alerts, dashboards, and automated monitoring to help resolve problems before they arise, such as expiring certificates, offline devices, or firmware gaps.
This stage represents a definitive movement from reactive to proactive operations. The physical security, IT, and compliance teams now use the same data, aligning their workflows and sharing a common language. Evidence for audits is easier to gather, and policies are enforced more consistently across locations and vendors.
While not fully automated, the organization has a strong foundation for long-term resilience. The CIP program supports compliance and day-to-day operations and is positioned to keep improving.
Optimized
At the optimized stage, CIP is not only part of the organization’s culture and strategy but has become more than just a compliance or security function. Processes are automated, systems are integrated, and teams work as an ecosystem of individuals working in unison. Real-time access to data and analytics informs decisions to predict potential problems before incidents occur.
Device management is no longer a manual task; it is a continuous, intelligent process in which teams, automated routines, and ongoing vulnerability and risk assessment manage device certificate renewals, patch updates, etc. Teams are now able to take risk-based actions, more efficiently and holistically, leveraging the entire view of the infrastructure.
CIP is not just used to comply with standards but also achieves larger objectives such as operational efficiency, risk mitigation, and organizational resiliency. The organization will rapidly adapt to change, learn from events, and invest in solutions. It uses a proactive, risk-based approach to invest in protection strategically.
Best practices for building a critical infrastructure protection program
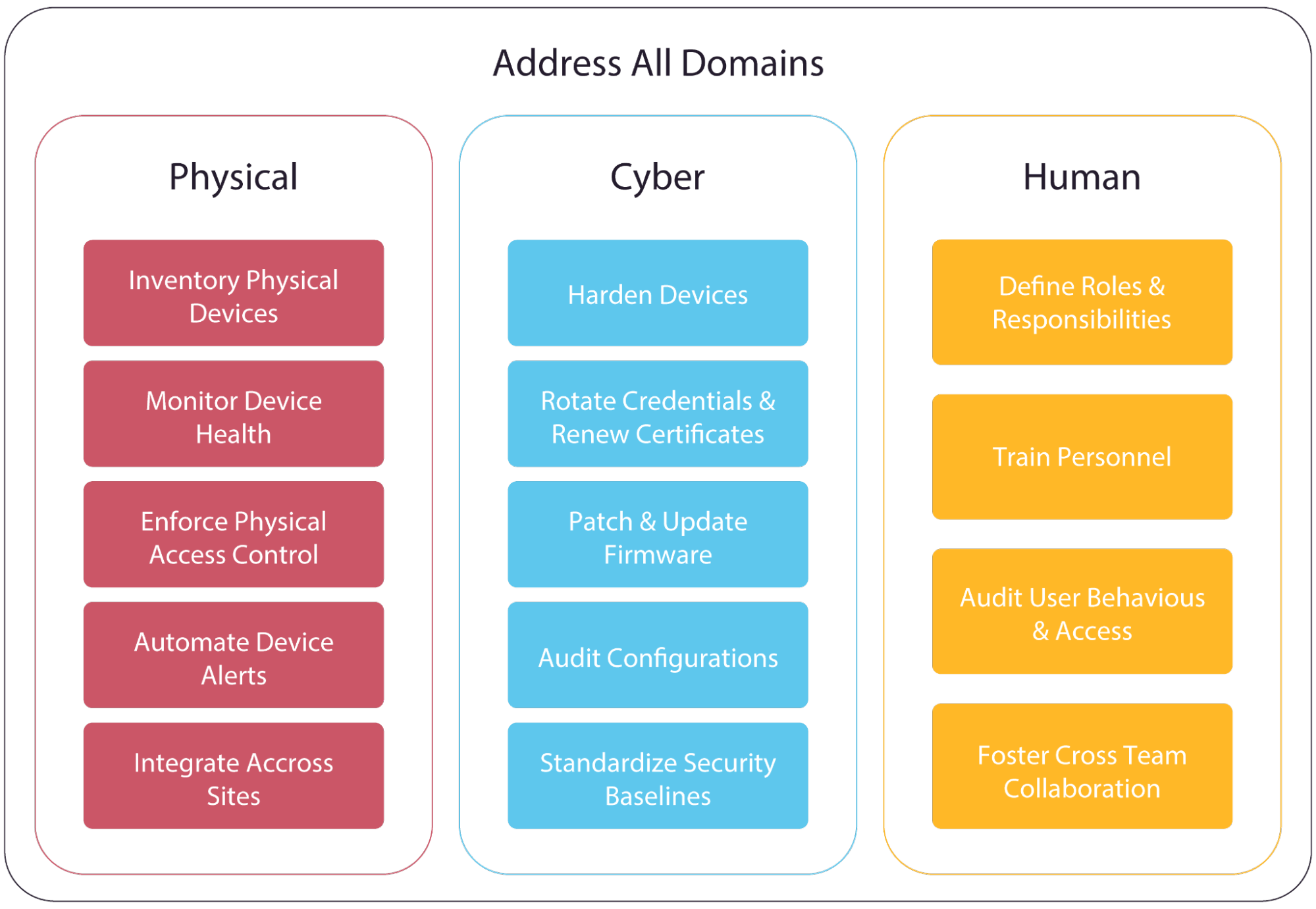
Core domains and best practices of a CIP program.
To build a truly resilient CIP program, organizations must implement safeguards across three interdependent domains: physical, cyber, and human. The graphic above illustrates the aforementioned core domains that every critical infrastructure protection program must address, along with key best practices for each domain, which will be explained in the sections that follow.
Physical domain – Secure physical infrastructure
Law 3 from the immutable laws of security states that “if a bad actor has unrestricted physical access to your computer, it’s not your computer anymore.” That fundamental cybersecurity truth sums up why physical security is the cornerstone of an effective critical infrastructure protection program. The best practices below help organizations get physical security right and reduce the risk of a threat actor accessing critical infrastructure.
Inventory physical devices
Maintain a comprehensive, real-time inventory of all connected physical and cyber devices, including cameras, badge readers, environment sensors, and programmable logic controllers (PLCs). Ensure records are continuously updated and accessible to relevant teams. Accurate inventory is not only essential for operational visibility, it also enables the detection of unauthorized or rogue devices, since an organization cannot secure what it hasn’t identified as legitimate.
Monitor device health
Continuously monitor every device for availability and operational status to identify issues such as downtime, tampering, or configuration drift. You should employ centralized dashboards and automated checks to minimize manual supervision, ensure systems stay operational, and maintain compliance.
Enforce physical/logical access control
Implement and maintain strict physical security measures to prevent unauthorized access to critical infrastructure areas. This includes the use of secure facility entry systems, badge readers, biometric controls, guards, gates, and surveillance systems. Regularly audit physical access logs and ensure only authorized personnel are permitted entry to sensitive zones.
Enforce strict access policies to define who can access the physical infrastructure. Use role-based permissions and ensure access changes, for example, revoking credentials, are implemented swiftly and consistently across all connected systems.
Automate device alerts
Implement a monitoring platform capable of continuously collecting data from physical and cyber devices. Use this system to generate automated alerts for anomalies such as device downtime, expired certificates, firmware inconsistencies, or configuration changes. Alerts should be integrated into a centralized workflow to ensure timely review and response by operations or security teams.
Integrate across sites
Establish centralized management of physical security devices across all sites and facilities. Use standard templates and configuration profiles to enforce consistency, simplify onboarding of new systems, and scale policies across regions and vendors.
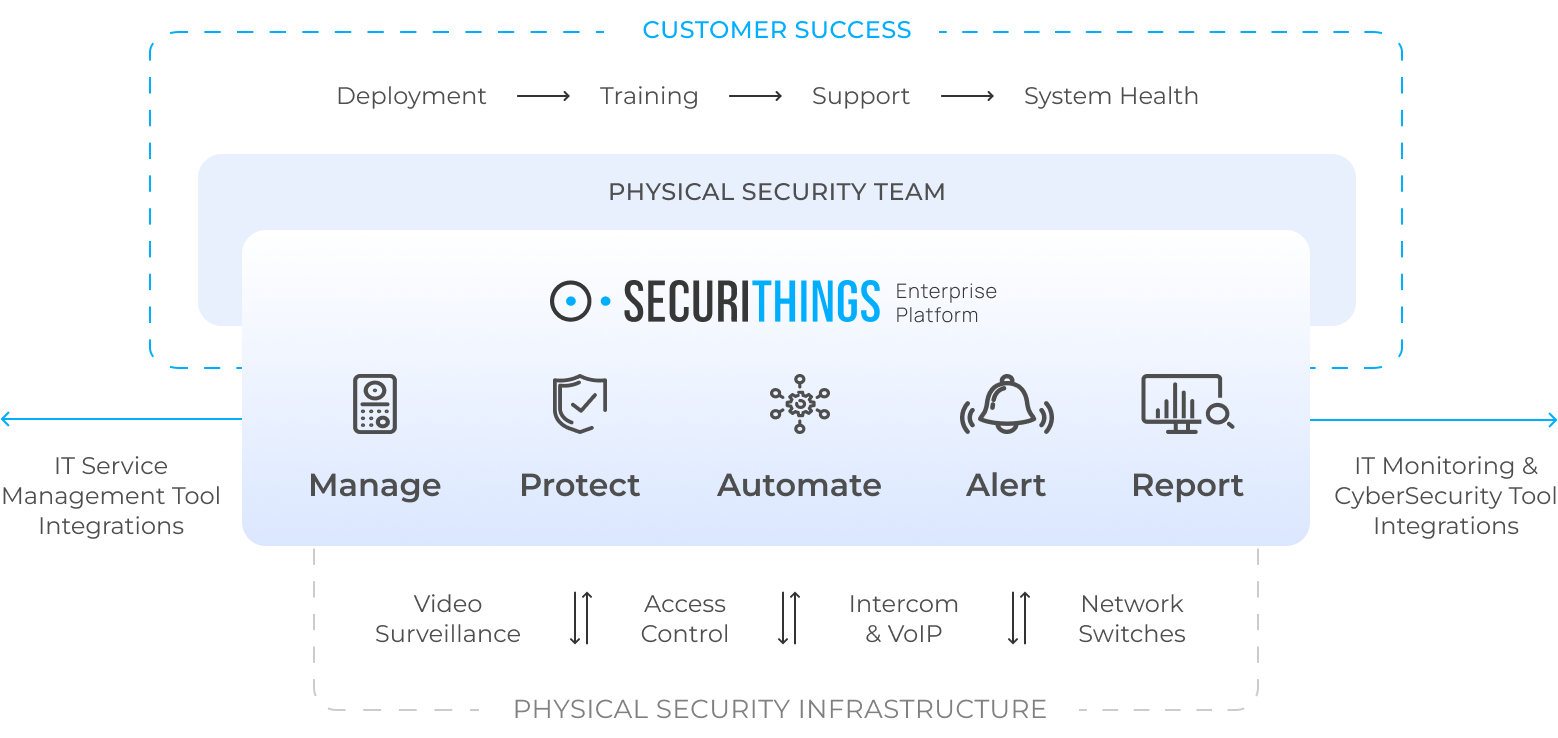
SecuriThings helps teams manage any physical security environment from one place. (Source)
Cyber domain – Strengthen cyber hygiene
This domain deals with more “traditional” software, firmware, and network-based security best practices. These practices help improve the digital components of a critical infrastructure protection program.
Harden devices
To minimize attack surfaces, disable unused services, enforce strong authentication policies, and apply secure network configurations. When possible, follow vendor-specific hardening guides to align device settings with industry best practices.
Rotate credentials and renew certificates
Ensure device credentials are regularly rotated and certificates are renewed before expiration to maintain trust and compliance. However, many OT devices have technical limitations, some may not support complex passwords or trusted certificates, particularly if they are off-network or vendor-locked. In these cases, security teams should implement compensating controls such as network segmentation, firewalls, network access control (NAC), and monitoring for unauthorized configuration changes.
Patch and update firmware
Apply firmware and software updates systematically across all devices to address known vulnerabilities. Prioritize based on risk, targeting high-severity exposures on critical assets first. Use dedicated staging or development environments to test patches before deployment, and schedule updates within approved maintenance windows to minimize operational disruption while maintaining a consistent security posture.
Audit configurations
Conduct routine checks on device settings and compare them against approved baselines to detect unauthorized or accidental changes. Use configuration monitoring tools to ensure systems remain aligned with defined security standards.
Standardize security baselines
Use uniform templates for firmware versions, access control policies, and alert thresholds across all environments. You should simplify management, reduce human error, and ensure consistency during audits or system expansions.
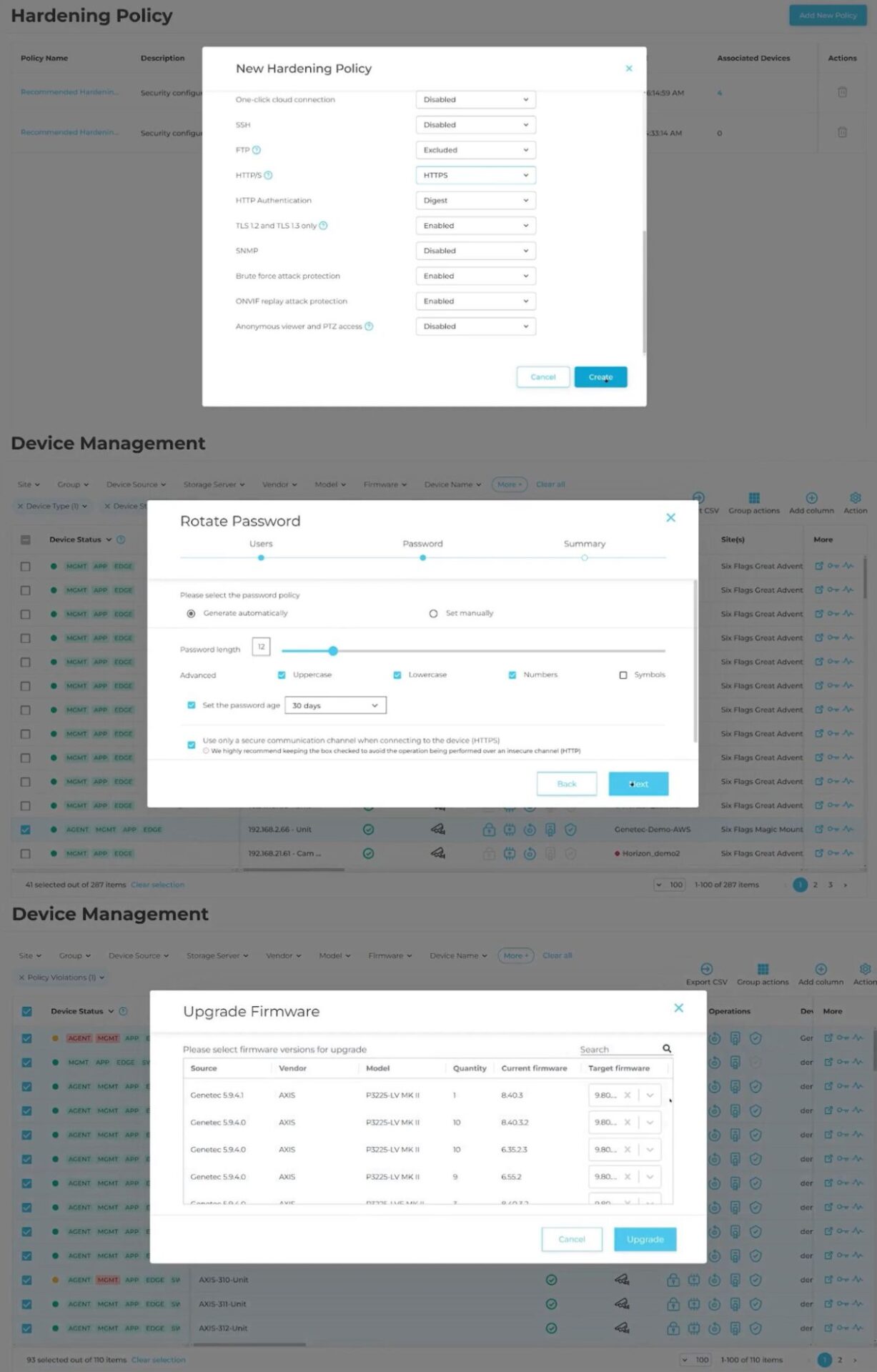
An intelligent device management platform enables key cyber hygiene practices. (Source)
Human domain – Empower and align people
People are often the weakest link in a cybersecurity chain. Social engineering regularly exploits human nature in a way that is hard to prevent with technical controls alone. The best practices below help organizations turn their employees into human firewalls that can reduce security risk.
Define roles and responsibilities
Clarify ownership across departments by assigning accountability for monitoring, response, compliance documentation, and system monitoring. You should have an unambiguous delegation of work to be actionable, yet accountable and flexible in daily practice and emergencies.
Train personnel
Deliver regular, role-specific training to staff involved in CIP, including physical security operators, IT administrators, and compliance personnel. Keep training content aligned with the latest threats, regulatory requirements, and operational tools.
Audit user behavior and access
Monitor logs and user activity to confirm individuals are operating within authorized boundaries. Investigate anomalies and adjust access levels as needed to prevent misuse or gaps in enforcement.
Promote cross-team collaboration
Use shared dashboards, alerts, and reporting tools to promote cooperation between IT, physical security, and compliance teams. Break down silos to enhance visibility and accelerate response across the organization.
Last thoughts
As threats to critical infrastructure grow in scale and complexity, the importance of a well-structured, continuously evolving CIP program has never been greater. From foundational controls like asset inventory and access management to advanced capabilities like real-time monitoring and cross-domain integration, CIP is not just about compliance but resilience, continuity, and strategic readiness.
Organizations that succeed in building mature CIP programs look beyond static checklists and embrace dynamic, data-driven operations. This means empowering teams with the tools to detect risks early, automate routine controls, and unify physical and cyber protections into a single operational picture.
Modern physical security and device management platforms that offer centralized visibility, automated alerts, and scalable policy enforcement, particularly for distributed physical security devices, can help introduce organizations to this process. Organizations can move from reactive defense to proactive protection by closing visibility gaps, reducing manual work, and encouraging cross-team collaboration.
A mature CIP program isn’t just a response to today’s requirements; it’s an investment in tomorrow’s stability. The sooner organizations align their processes, people, and platforms, the better positioned they’ll be to defend the infrastructure that underpins everything else.


