Power Grid Security Best Practices
The power grid is the backbone of a modern and evolving society, supporting everything from hospitals and water systems to data centres and public transportation. Ensuring the security of the power grid isn’t just a technical challenge but also a national security imperative. A single point of failure can cause a ripple effect across major sectors, leading to human safety risks, blackouts, and irreparable economic disruption. Recent events have demonstrated the severity of these threats, with cyberattacks targeting utilities and physical attacks on substations resulting in localized power outages. For example, the December 2022 Moore County substation attack in North Carolina left 40,000 residential and business customers without electrical power for days and caused an individual’s death.
As grid systems evolve and become more connected through smart devices, remote monitoring, and Internet of Things/ Operational Technology (IoT/OT) integration, their attack surface grows. Substations in remote areas, legacy Supervisory Control and Data Acquisition (SCADA) protocols, and unmanaged devices all create entry points that can be exploited by threat actors ranging from ransomware groups to nation-state adversaries.
This article explores strategies to enhance grid protection in an era where physical infrastructure and digital systems are increasingly interlinked. It also discusses the critical role of power grid security, exposure points, today’s threat landscape, and leading strategies and best practices to build security into every layer of our technological environment.
Summary of key power grid security concepts
The table below summarizes the power grid security concepts this article will explore in more detail.
| Concept | Description |
|---|---|
| The critical role of power grid security | Power grid security is essential for ensuring national security, economic stability, and public safety. Governments and organizations must protect against disruptions from both cyber and physical threats that could have wide-reaching, catastrophic impacts. |
| Exposure points and threat landscape | There are many risks and vulnerabilities that could compromise power grid security. The risks are both physical and digital, including evolving threats such as cyber intrusions and hybrid attacks. Threat actors can exploit unprotected attack vectors to disrupt, damage, or compromise the reliability and safety of the grid. |
| Best practices for power grid security | Governments and organizations can safeguard the modern power grid against the growing convergence of cyber and physical threats, by combining layered defenses, rapid response strategies, and a culture of security. |
Monitor the health of physical security devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports



The critical role of power grid security
The power grid underpins nearly every essential function of modern society, from hospitals and water systems to communications, transportation, and national defense. As physical and digital systems become increasingly interconnected, the consequences of security failures grow more severe. Securing the grid is not only a technical challenge but also a matter of national security, public safety, and economic stability.
While engineers and operators know the grid is critical, it is useful to highlight the main areas where security plays the largest role. The following table summarizes three key domains: national and economic stability, public safety and trust, and operational resilience, along with examples showing why grid security is essential and must be prioritized.
| Domain | Why it matters | Example |
|---|---|---|
| National & Economic Stability | Grid failures cascade across health, emergency services, transport, water, and communications. Adversaries view the grid as a strategic target. | In 2015, a Ukrainian power grid hack cut power to 230,000 people. |
| Public Safety & Trust | Outages threaten hospitals, water systems, and emergency services while eroding public confidence. Even short failures can disrupt entire communities. | A compromised substation or Remote Terminal Unit (RTU) can put thousands at risk. |
| Operational Resilience & Uptime | Downtime brings safety, compliance, and economic risks, with impacts ranging from lost productivity to humanitarian crises. | 2003 Northeast blackout ($6B loss); 2021 Texas winter storms (246 deaths, $195B damages). |
Power grid exposure points and threat landscape
The power grid has become one of the most complex systems and infrastructures ever designed. It includes an interconnected network of substations, transmission lines, control systems, and intelligent devices that work together to keep electricity flowing reliably. However, this complexity creates a wide range of exposure points, making the grid increasingly vulnerable and susceptible to a diverse and evolving set of threats. First, understanding these vulnerabilities and how they can be exploited is imperative, as this will help build more resilient infrastructure. Today, protecting the grid means recognizing how cyber threats, physical intrusions, and hybrid attacks can compromise both safety and business/service continuity.
The following image illustrates the main exposure points across the power grid, spanning the cyber, physical, and hybrid domains. It highlights critical components such as SCADA systems, RTUs, substations, control rooms, transmission lines, and communication networks, all presenting unique security challenges.
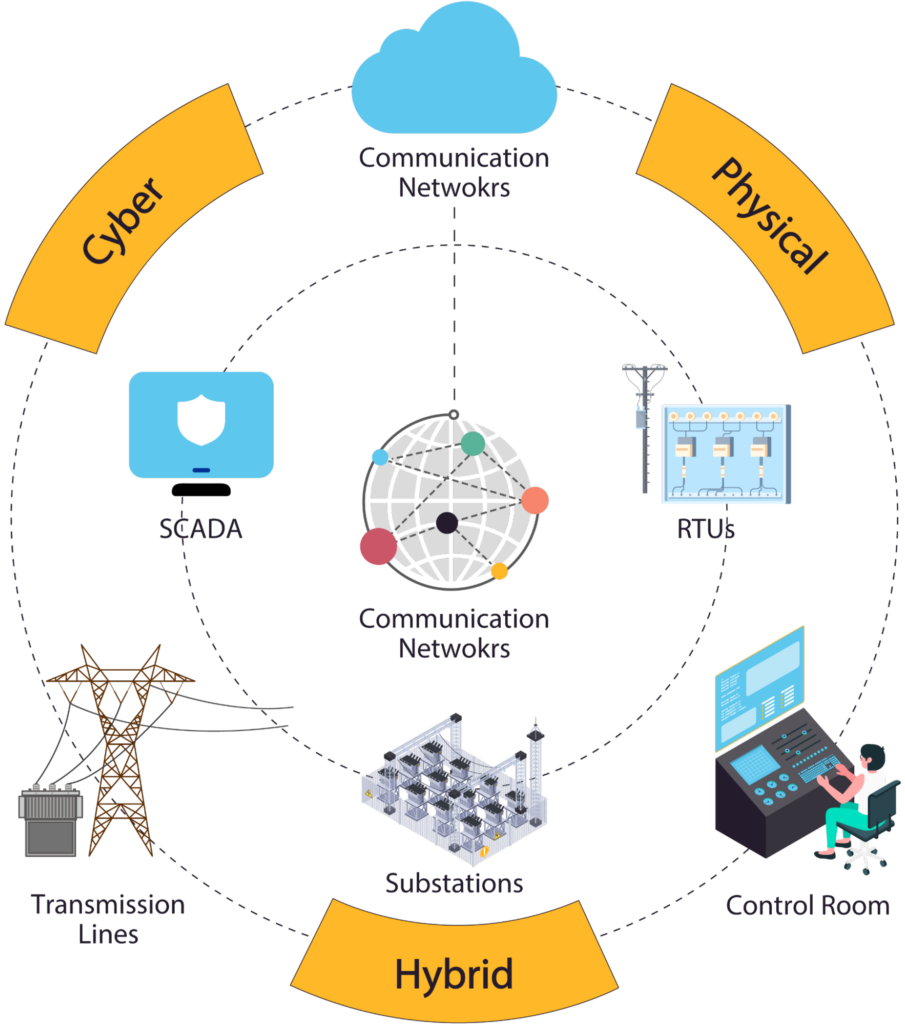
Key exposure points across cyber, physical, and hybrid domains of the power grid. (Source)
Physical and digital vulnerabilities impacting power grid security
Power grid infrastructure spans two critical domains which are physical assets (such as transformers, substations, and field devices) and digital systems (such as SCADA, Programmable Logic Controller (PLCs), RTUs, and control centers). Each presents unique security challenges.
Physical vulnerabilities occur given:
- Substations and critical equipment are often located in remote or lightly guarded areas, making them targets for vandalism, sabotage, or theft.
- Inadequate access controls, surveillance, and environmental monitoring leave physical sites exposed to tampering.
- Many legacy systems lack tamper detection or event-triggered alerts.
Examples of digital vulnerabilities include:
- Lack of encryption or secure authentication to Legacy SCADA protocols such as Modbus, DNP3.
- Operational technology (OT) environments that still rely on flat networks, where all devices are connected without clear boundaries. Poor segmentation and weak access controls allow attackers who compromise a single device to move laterally across the network, increasing the risk of reaching critical systems.
- Unpatched devices, insecure remote access such as exposed Virtual Private Network(VPNs) or Remote Desktop Protocol (RDP) ports, weak password practices, and unnecessary open ports or services listening on them
- IoT/OT convergence introduces connected sensors and smart devices, many of which are deployed without adequate visibility or lifecycle management.
As the grid modernizes, these two domains are becoming increasingly interwoven, thereby creating new hybrid exposure points.
Analyzing the power grid security threat landscape
Modern threat actors have become more strategic in targeting the grid. Attacks may focus on disruption, economic impact, espionage, or even national destabilization. It is critical to analyse the threat landscape as it relates to cyber, physical and hybrid attacks.
Cyber threats include:
- State-sponsored actors that are known to infiltrate OT networks for reconnaissance, staging attacks, or delivering malware. An example of this is Industroyer, which was used in the cyberattack on Ukraine‘s power grid on December 17, 2016.
- Ransomware groups have begun targeting critical infrastructure to extort utilities by encrypting systems or threatening public outages.
- Supply chain attacks that occur via compromised software updates or third-party vendors introduce backdoors into trusted systems.
- Insider threats, whether malicious or accidental, are a persistent risk in any environment, and weak monitoring can make them harder to detect and stop.
Physical threats include:
- Direct attacks on substations using firearm attacks or arson which can damage high-voltage equipment and cause widespread outages.
- Equipment theft that could impact or disable backup systems and compromise safety.
- Coordinated physical attacks which may be timed to coincide with digital incidents, increasing confusion and impact.
Hybrid attacks are the most dangerous scenarios involving combined cyber and physical operations. This could include:
- Using physical breach to install rogue devices or intercept network communications.
- Cyber attackers disabling security systems to aid physical intrusion.
- Simultaneous cyber-physical attacks can overwhelm response teams and cripple resilience efforts.
The Ukraine 2015 power grid attacks showcased how attackers can remotely control circuit breakers while disabling operator visibility and response capabilities.
Understanding key power grid attack vectors
Common attack vectors include:
- Remote access exploits such as insecure VPNs, exposed RDP ports, and third-party vendor connections
- Phishing & credential theft through compromised user accounts or reused passwords
- Malware & payload delivery that are custom-built targeting ICS protocols and devices
- Unpatched vulnerabilities of known exploits in firmware or software that remain unresolved (e.g., unpatched camera vulnerabilities)
- Compromised field devices such as rogue firmware, cloned devices, or outdated sensors left unmanaged
- Lateral movement via flat networks. Once inside a network, attackers can reach critical systems due to lack of segmentation
- Human error or insider misuse which could result based on unintentional misconfigurations or deliberate sabotage by trusted personnel
Each of these attack paths can originate in either the cyber or physical domain and they mostly intersect.
Best practices for securing the power grid
Securing the power grid and building resilience at the intersection of physical and digital infrastructure is a matter of national stability, public trust, and operational continuity. As the grid evolves through digitization, IoT expansion, and increased automation, so does its exposure to cyber and physical threats. From ransomware groups targeting remote substations to nation-state actors probing for weak spots in SCADA environments. There is a growing pressure to anticipate, detect, and contain threats across these complex systems.
Securing the power grid today requires a holistic approach that accounts for both physical infrastructure and digital systems working together. The convergence of IT (Information Technology) and OT (Operational Technology) has created new efficiencies but also new exposures and vulnerabilities. Engineers and operators must think in layers of visibility, access control, resilience, and coordinated response to better protect the grid.
The good news is that there are leading practices provided by modern platforms designed to help organizations secure their physical infrastructure across every layer of the power grid, from edge devices and substations to control centers and monitoring dashboards.
The sections that follow examine six of the most effective practices for ensuring power grid security in the modern threat landscape.
1. Cyber & physical defense including hybrid security measures
Ensure that surveillance and intrusion detection are installed at key sites, integrate physical security systems such as cameras, badge readers with your Security Operations Center/Network Operations Centre (SOC or NOC) and include physical breach scenarios in your incident response plans.
Key actions to consider:
- Deploying integrated cyber-physical intrusion detection systems
- Hardening substations with surveillance, strict access controls, and alarm integration
- Isolating digital control interfaces from publicly exposed networks
- Using analytics to correlate physical and cyber events for rapid situational awareness
A unified platform for monitoring digital device behavior, access logs, and physical tampering alerts can support this hybrid defense model, helping teams close the visibility gap across both planes.
2. Implementation of defense-in-depth controls
Organizations should deploy asset discovery tools to build a live inventory, use platforms that integrate with SCADA to surface device status, firmware versions, and create a layered defense.
Key areas to consider for layers of defense include:
- Network segmentation (e.g., zoning based on the Purdue Model)
- Role-based access control (RBAC) and multifactor authentication (MFA)
- OT-specific firewalls and protocol filtering
- Secure boot, patching, and vulnerability management for field devices
- Continuous configuration monitoring
SecuriThings plays a critical role in supporting DiD by automatically detecting misconfigured devices, unauthorized software, and outdated firmware allowing operators to quickly address vulnerabilities before they can be exploited.
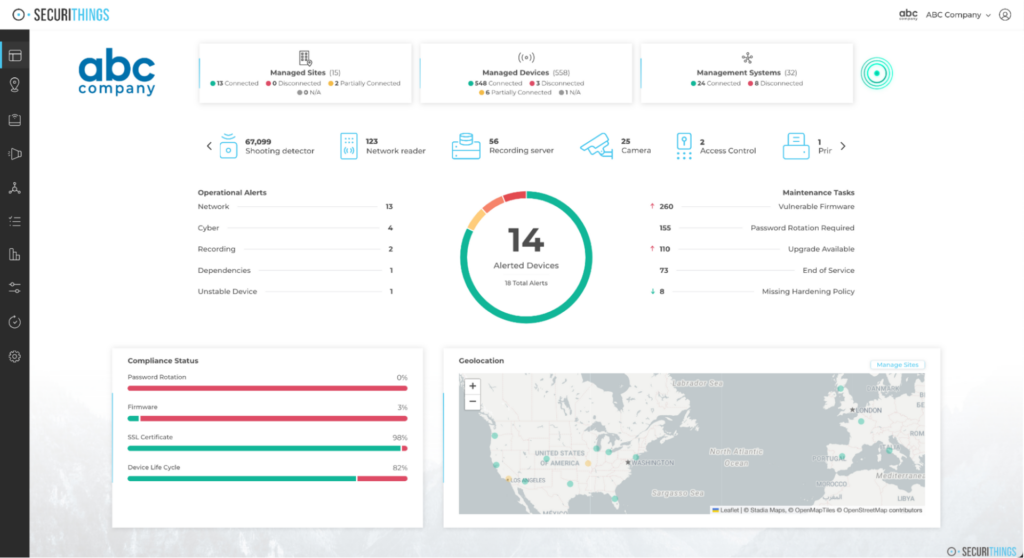
Centralized dashboards consolidate visibility across sites, devices, and compliance status, supporting a Defense-in-Depth approach to grid security. (Source)
3. Incident response for power grid security
Grid environments require OT-specific playbooks that address operational and safety implications. The incident response should include the following components:
- Clear delineation and definition between IT and OT roles in incident management
- Tailored tabletop exercises involving engineers, SCADA operators, and facility managers
- Integration of physical breach scenarios into cyber response workflows
- Logging and forensic readiness to support post-event analysis
Modern platforms can enhance IR readiness by providing device telemetry, contextual alerts, and automated root cause analysis across devices and control layers, enabling faster, more coordinated responses.
4. The role of automation, remote monitoring, and remediation
Organizations should leverage automations for continuous visibility within distributed environments and rapid detection of abnormal activity such as unauthorized access, firmware tampering, or communication anomalies.
Examples of automation include:
- AI-driven anomaly detection for SCADA and sensor data
- Centralized dashboards for monitoring geographically distributed assets
- Automated policy enforcement (e.g., locking devices with outdated firmware)
- Smart alerting with context (who, what, where, how)
Intelligent platforms empower engineering and security teams by automating remediation actions such as isolating compromised devices, revoking access credentials, or triggering alerts when compliance baselines are breached.
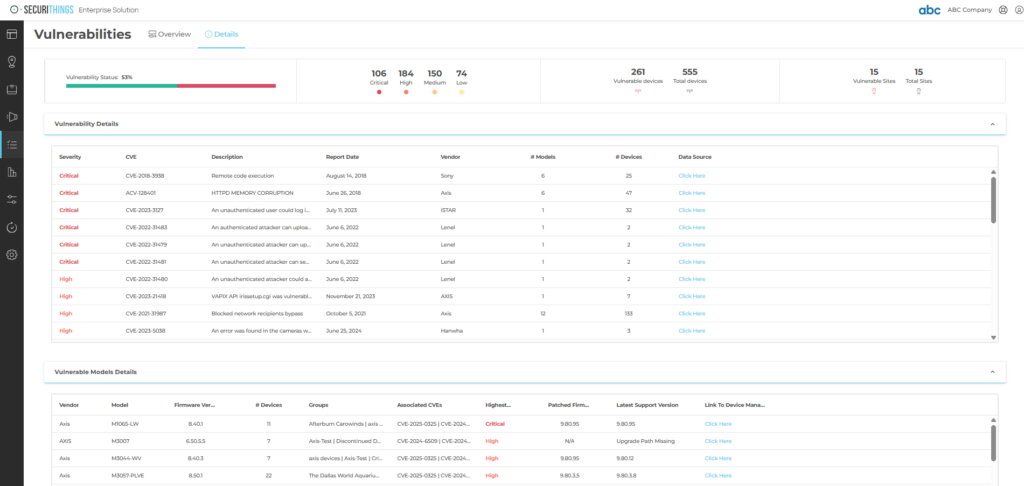
Automated monitoring dashboards provide real-time visibility into device vulnerabilities, firmware versions, and patch status, helping utilities detect risks early and streamline remediation. (Source)
5. Building a security-first culture: Awareness, training & visibility
Ensure that only vendors with secure firmware update processes are engaged. All new installations must follow network and access control standards, and engineers and field technicians must be trained to recognize signs of compromise.
Security culture building practices include:
- Routine OT security awareness training tailored to field teams.
- Real-world scenario testing such as simulating phishing attempts or access violations.
- Encouraging a “see something, say something” mindset at substations and field sites, and implementing banners that remind teams.
- Investing in dashboards that provide real-time visibility to operators and IT staff.
Centralized platforms support cultural transformation by offering visibility tools built for OT teams, presenting alerts, compliance drift, and access violations in language and context relevant to field personnel.
6. The future of power grid security: Proactive, predictive, and resilient
Security engineers should embrace a proactive stance by leveraging the following actions:
- Using machine learning to predict failures and preemptively isolate weak nodes
- Implementing security orchestration across IT/OT/physical domains
- Preparing for quantum-resistant encryption and supply chain validation
- Designing systems with “secure by design” configurations and not just bolt-on protections
Advanced platforms help organizations shift from reactive to predictive defense by delivering intelligent insights, automating risk prioritization, and supporting long-term grid modernization strategies.
Last thoughts
The security of the power grid is a matter of national resilience. As the lines between physical and digital systems continue to blur, the grid’s exposure to state-sponsored actors, ransomware groups, and hybrid attacks grows more complex and dangerous. Protecting this critical infrastructure requires a holistic approach that includes integrating physical safeguards with robust cyber defenses, deploying defense-in-depth controls, and maintaining continuous monitoring and rapid response capabilities.
While it is evident that technology alone cannot secure the grid, it must be coupled with a strong security-first culture, ongoing training, and cross-disciplinary collaboration between engineers, operators, and security teams. Modern platforms that provide unified visibility, automation, and device lifecycle management can play an important role in helping utilities proactively address vulnerabilities and embrace innovation. By combining these tools with strong processes and people, the backbone of our modern society can remain reliable, resilient, and protected regardless of how the threat landscape evolves.