NERC CIP Security Standards Best Practices
The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards form a foundational framework to protect the Bulk Electric System (BES) from both cyber and physical threats. While cyber risk continues to dominate headlines, physical security attacks pose a real and present danger to critical infrastructure, with increasing sophistication and frequency.
Electric substations, transmission stations, and control centers are vulnerable to vandalism, unauthorized access, sabotage, and terrorism. These threats can lead to large-scale service disruptions, compromise national security, and result in steep penalties for utilities that fail to maintain compliance.
This article explores the NERC CIP standards that govern physical security, offers best practices for compliance, includes real-world examples, and introduces features that utilities can implement with a technology partner or solution provider to optimize their physical security systems.
A summary of key NERC CIP security standards concepts
The table below summarizes three concepts related to NERC CIP security standards that this article will explore in more detail.
| Concept | Description |
|---|---|
| NERC CIP standards structure | There are 13 standards for CIP, structured in a series of numbered requirements. Each focuses on a specific aspect of cyber and infrastructure security:
CIP-002 – Asset Identification CIP-003 – Security Management Controls CIP-004 – Personnel & Training CIP-005 – Electronic Security Perimeters (ESP) CIP-006 – Physical Security of BES Cyber Systems CIP-007 – System Security Management CIP-008 – Incident Reporting and Response Planning CIP-009 – Recovery Plans for BES Cyber Systems CIP-010 – Configuration Change Management and Vulnerability Assessments CIP-011 – Information Protection CIP-012 – Communications Between Control Centers CIP-013 – Supply Chain Risk Management CIP-014 – Physical Security |
| Implementation challenges | Identifying facility vulnerabilities is a complex task, made more challenging by the high cost of physical security measures needed and the constantly evolving threat landscape. Security protocols require continuous updates, compliance demands exhaustive documentation, and without alignment between physical and cybersecurity, facilities risk falling short, often with costly consequences. |
| Practical implementation and best practices | To build a truly resilient physical security program, organizations must take a multifaceted approach, leveraging third-party audits to validate compliance, enforcing strong access controls like dual authentication and role-based permissions, and deploying intelligent surveillance systems backed by AI-powered analytics. On the ground, protective measures such as fencing, intrusion detection, rotating patrols, and structured drill routines help detect and deter unauthorized activity. Collaboration plays a key role too: coordinating with law enforcement, vetting and escorting visitors, and staying aligned with industry groups and regulators all help sharpen incident response and future-proof against evolving threats. Meanwhile, automation in compliance tracking, continuous staff training, and insider threat awareness ensure that both human and technical defenses remain agile and accountable. |
Monitor the health of physical security devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports



The NERC CIP standards applicable to physical security
To provide a clearer understanding of how the NERC CIP framework is structured and which standards are most relevant to physical security, the table below summarizes all CIP standards. While many of these requirements focus on cybersecurity, several directly affect physical security systems and their management.
| CIP standard | Description | Physical security relevance | Notes |
|---|---|---|---|
| CIP-002 | BES cyber system categorization | Medium | Drives the scope of physical and cyber protections based on system criticality. |
| CIP-003 | Security management control | Medium | Establishes baseline security policies, which include physical security in governance processes |
| CIP-004 | Personnel and training | Medium | Ensure personnel with access to BES cyber systems are properly trained and vetted. |
| CIP-005 | Electronic security perimeter | Low | Focuses on cyber perimeters |
| CIP-006 | Physical security | High | Core physical security standards, including access control, monitoring, and response plan |
| CIP-007 | Security system management | Low | Mostly IT-focused, it can impact patching and change procedures |
| CIP-008 | Incident reporting and response planning | Medium | Security breaches are reported in the incident report, which also contains a response protocol |
| CIP-009 | Recovery plans for BES cyber systems | Low | It includes business continuity, recovery, and backups |
| CIP-010 | Configuration change management and vulnerability assessment | Low | Ensure all system changes are properly logged and reviewed. Also, it describes how and when a vulnerability assessment is due. |
| CIP-011 | Information protection | Medium | Safeguards for sensitive data and storage |
| CIP-014 | Physical security for the critical transmission station | High | Addresses threats to transmission stations and control centers. |
NERC CIP standards related to physical security are primarily outlined in CIP-006 and CIP-014. Together, these standards ensure utilities are both proactive and reactive in their approach to physical threats, contributing to the grid’s overall resilience.
Common challenges in physical security implementation
Although advanced physical security technologies are more widely available than ever, utility providers, especially those in rural or under-resourced areas, still face persistent challenges when implementing adequate protective measures. Chief among these is the issue of limited budgets. For many utilities, funding tends to be funneled toward revenue-generating infrastructure or regulatory compliance efforts, often leaving physical security upgrades sidelined or indefinitely delayed.
Beyond financial limitations, integrating modern security systems into aging legacy infrastructure is also a considerable challenge. Many older facilities continue to rely on outdated technologies that are incompatible with today’s access control and surveillance solutions. From a technical standpoint, vulnerabilities often arise from poorly configured devices, many of which still operate with default or weak passwords. Perhaps more concerning, however, is the widespread neglect in updating device firmware, leaving systems dangerously exposed to known security threats.
Meanwhile, the threat landscape itself is evolving at an unprecedented pace. While traditional risks like unauthorized entry remain, they are compounded by more advanced threats such as drone surveillance, remote cyber intrusions, and even AI-assisted tactics. Regulatory frameworks like NERC CIP add another layer of operational pressure to complicate matters further. Many organizations still rely on manual methods for maintaining compliance records, a process that is inefficient and prone to human error, risking audit failures and potential penalties.
Practical implementation and best practices for NERC CIP security standards
Effectively addressing the physical security requirements within the NERC CIP standards requires a structured approach built around three core focus areas: securing the perimeter, managing access and identity, and implementing monitoring and detection systems.
These categories represent practical domains where utilities can strengthen their compliance posture while improving the resilience and visibility of their physical infrastructure. For each of the focus areas below, we will enumerate subcategories and explain related implementation tips and best practices.
Securing the perimeter
This focus area deals with preventing breaches of physical perimeters. Effective perimeter security includes:
- Protection against intruders: Robust perimeter protection begins with high-security fencing designed to resist cutting and climbing. These barriers should stand at least seven feet tall and be topped with barbed wire or similar deterrents to prevent unauthorized entry.
- Protection against vehicles: To defend against vehicle-based threats, utilities should install bollards and reinforced walls capable of withstanding high-speed collisions. Traffic barriers are equally important, serving to channel vehicles into controlled routes while also preventing vehicular access to critical areas.
- Adaptive lighting: Lighting systems must be smart and responsive, activating when motion is detected or when ambient light drops below safe visibility levels. In high-security zones, lights should turn on at dusk and remain active under all low-light conditions to maintain visual oversight.
Managing access and identity
This focus area deals with ensuring that only authorized personnel can access a physical location. Effective access and identity management practices include:
- Multi-factor authentication (MFA): A strong access control framework begins with multi-factor authentication, commonly achieved through card readers paired with biometrics or keypad PIN entry. In more sensitive areas, facilities should incorporate advanced biometric tools such as fingerprint, palm, retina, or facial recognition scanners.
- Time-based permissions: Limiting access based on scheduled shifts helps ensure personnel are only on-site when necessary. This method restricts unnecessary presence and supports tighter security management.
- Visitor vetting: Visitor management protocols should involve pre-registration and identity checks before arrival, with escorts required at all times. Electronic gates controlled by the access system make it easy to log and monitor all entries in real time.
- Automated alerts: Facilities must be equipped to detect and react to anomalies like denied access attempts, doors being forced open, or held ajar. Organizations should configure alerts and alarms to notify operators of any suspicious activity immediately.
- Integrated platforms: Third-party software solutions can provide centralized identity management, automatically logging all access events and pushing real-time alerts to administrators. These platforms may also handle firmware upgrades remotely, keeping devices current without manual intervention.
Monitoring and detection systems
This focus area deals with monitoring physical locations and detecting anomalies or threats. An effective monitoring and detection strategy includes:
- Intelligent camera coverage: Modern CCTV systems should include PTZ (Pan-Tilt-Zoom) cameras for flexible monitoring and zooming capabilities, as well as multi-sensor units that offer comprehensive panoramic views (180° to 360°). These enable operators to maintain situational awareness across broader areas.
- Behavioral analytics: Cameras with built-in analytics can assess behavior patterns and trigger alerts for activities that deviate from established norms. Since these capabilities are embedded directly within the camera hardware, they operate independently of recording devices, minimizing processing load.
- Vehicle tracking: License plate recognition systems enhance security by tracking vehicle movement in and out of secure zones. They support whitelist/blacklist functionality, but should be used to complement, not replace, proper access control protocols.
- Perimeter intrusion detection: Fiber-optic intrusion detection systems (IDS) offer advanced monitoring along facility boundaries. When fiber-based solutions aren’t feasible, teams can deploy alternatives like vibration, acoustic, and infrared sensors to detect unauthorized movement. Many devices support multiple detection modes in one unit.
- Thermal surveillance: Thermal cameras provide high-contrast imaging and wide-area coverage, making them ideal for low-visibility conditions or nighttime monitoring. These systems can also be linked to intelligent platforms for centralized tracking, remote access, and automated threat escalation.
How intelligent security management platforms improve physical security
Leveraging intelligent security management platforms can significantly streamline the implementation of physical security controls and compliance with NERC CIP security standards, ensuring accurate documentation and regulatory compliance while freeing up valuable internal resources. Additionally, these platforms can facilitate the day-to-day operation and maintenance of the security system, like automatically replacing the passwords of all devices, detecting and alerting devices that go offline, running automatic reports, performing firmware upgrades, and more.
For instance, using a dashboard facilitates an overview of the security systems.
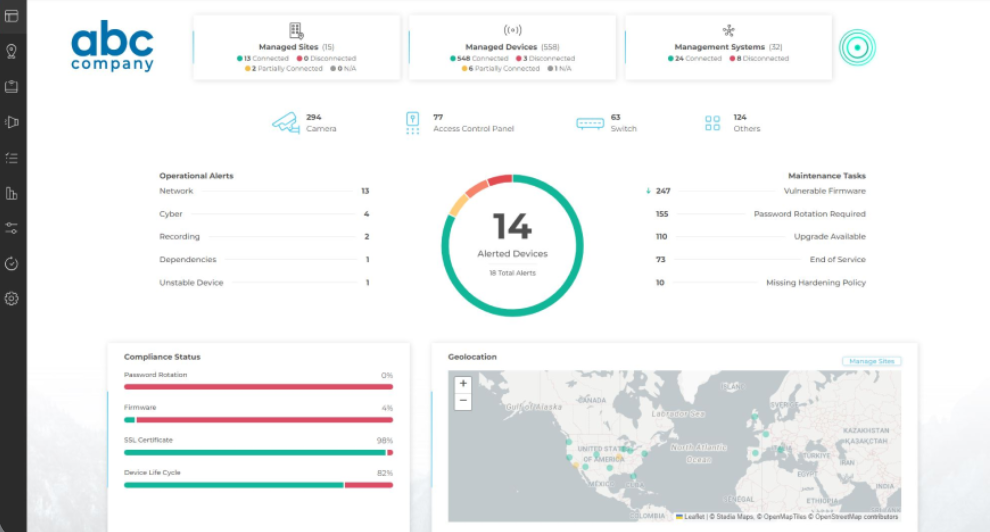
SecuriThings dashboard overview. (Source)
It is very easy to manage all of your security devices under one platform:
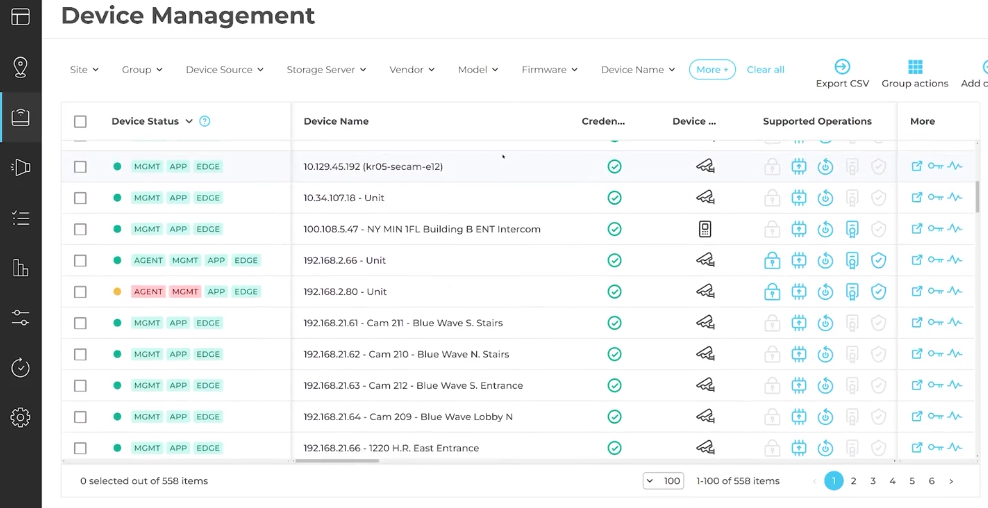
SecuriThings device management overview. (Source)
Security management platforms also detect devices that need attention:
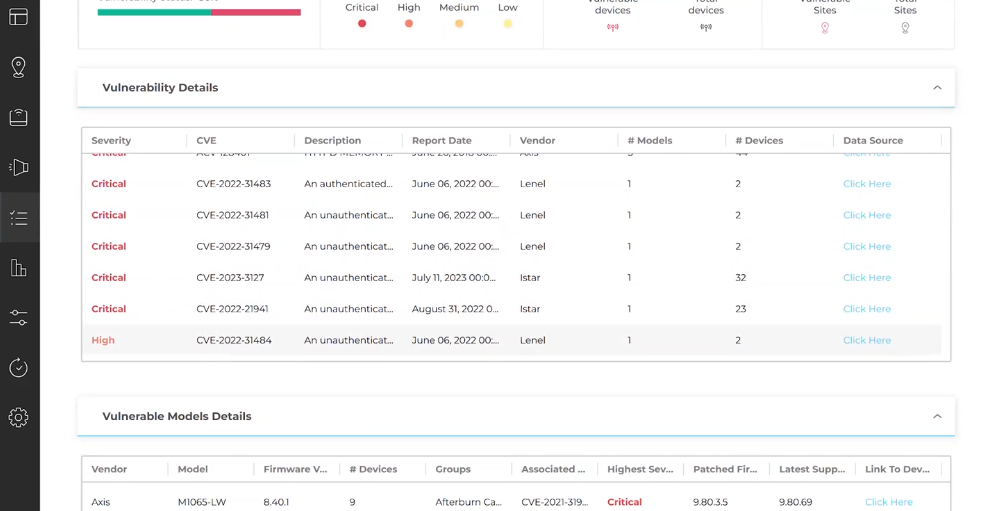
In this section, the SecuriThings platform informs the user of device vulnerabilities. (Source)
Security management platforms can run reports on the security systems:
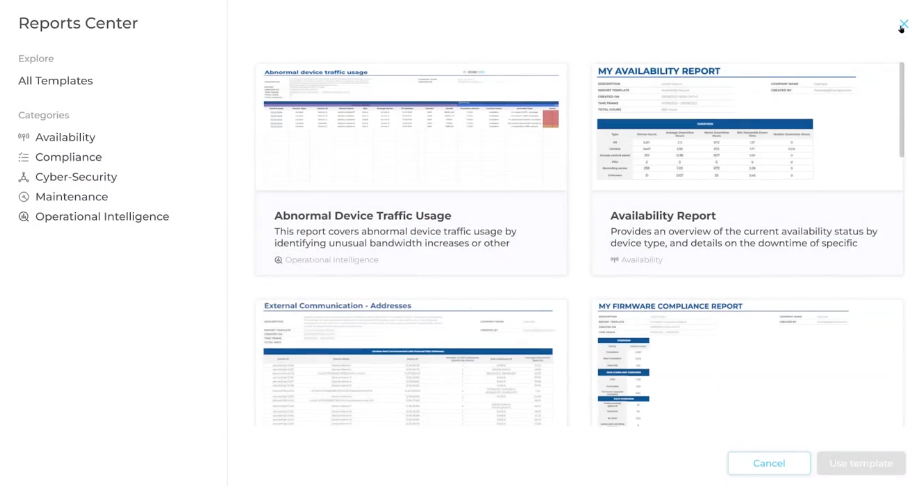
The SecuriThings report section allows users to create their own custom-made reports. (Source)
The table below outlines how modern device management platforms can help organizations meet NERC CIP standards and implement the best practices discussed above.
| CIP standard | How SecuriThings supports compliance |
|---|---|
| CIP-003 | Provides centralized visibility and policy enforcement for physical security systems, supporting governance over user access, system behavior, and audit trails. |
| CIP-005 | Automated security device management and remediation, vulnerability management for physical security devices, and automated hardening |
| CIP-006 | Comprehensive device inventory, real-time health monitoring, and remote remediation |
| CIP-007 | Automated security device management and remote remediation, automated firmware upgrades, end-of-service tracking and reporting, automated password rotations, automated SSL and 802.1x certificate management |
| CIP-008 | Smart alerts and remote remediation, vulnerability monitoring, and reports |
| CIP-010 | Automated device hardening, drift analysis, vulnerability monitoring, smart alerts with root cause analysis, reports, and integration with IT systems |
| CIP-011 | Automated security device manager and remote remediation |
| CIP-014 | Comprehensive device inventory, automated management, and remediation of physical security devices |
Case study: Modernizing substation security with technology integration
Background: A major utility in the U.S. Midwest faced repeated intrusion attempts at several remote substations. Although no damage was done, the company recognized significant risk and moved to upgrade its physical security infrastructure to comply with CIP-014.
To strengthen their physical security posture, the utility implemented a series of strategic upgrades. AI-driven video analytics were introduced to detect unusual behavior patterns in real time, while biometric scanners replaced traditional keycard access at all entry points, significantly tightening access control. Additionally, a cloud-based dashboard was deployed to enable centralized monitoring across multiple facilities, providing greater visibility and operational oversight.
These changes delivered measurable improvements. Within just six months, unauthorized access incidents dropped by 50%. The new system also streamlined audit processes by making access logs fully searchable and automatically archived. Most notably, the time required to detect potential threats was slashed—from several hours to under five minutes, enhancing both responsiveness and overall situational awareness.
This example demonstrates how integrating advanced security systems with a trusted technology partner can boost resilience and simplify compliance.
Conclusion
As threats to physical infrastructure grow in scale and sophistication, utilities must go beyond the baseline requirements of NERC CIP standards. With physical and cyber threats increasingly converging, the need for integrated, intelligent, and adaptive security systems has never been more urgent.
By partnering with experienced technological solution providers, utility companies can monitor and secure real-time remote assets, automate compliance documentation, respond rapidly to physical security breaches, and future-proof their operations through predictive analytics and intelligent integration.