NERC CIP Compliance Best Practices
Ensuring security, reliability, and resilience of North America’s Bulk Electric System (BES) requires operational excellence and a structured approach to safeguarding critical infrastructure from both cyber and physical threats. The North American Electric Reliability Corporation (NERC) developed the Critical Infrastructure Protection (CIP) Reliability Standards to give organizations such an approach. These mandatory requirements are designed to protect assets essential to the BES, addressing risks ranging from unauthorized access and data breaches to supply chain vulnerabilities and sabotage.
The NERC CIP standards apply to registered entities involved in the planning, operation, or ownership of BES facilities. This article offers a practical guide to building and maintaining a sustainable NERC CIP compliance program. It goes beyond checklists and policy documents to explore real-world implementation strategies, operational challenges, and best practices.
Summary of key NERC CIP Compliance concepts
The table below summarizes the three high-level concepts this article will explore in detail.
| Concept | Description |
|---|---|
| Background of NERC CIP and compliance requirements | This section explains the foundational purpose of NERC CIP, the evolution of the program, and why it is critical to the reliability of the Bulk Electric System (BES). Covers the regulatory structure, mandatory compliance obligations, and the overall complexity of managing cyber and physical security controls across critical infrastructure. |
| Understanding the security controls | This section provides a high-level overview of the 14 NERC CIP standards, with examples of how organizations typically comply and discusses real-world challenges and common risks. |
| Best practices for building and sustaining a NERC CIP Compliance Program | This section focuses on the governance, processes, and structures necessary to establish and maintain a successful NERC CIP compliance program. It highlights the importance of cross-functional coordination, internal accountability, evidence management, and integration with broader risk management efforts, along with guidance on assigning roles, conducting internal audits, automating tasks, managing documentation, and ensuring the program adapts to evolving threats and regulatory updates. |
Monitor the health of physical security devices and receive alerts in real-time Automate firmware upgrades, password rotations & certificate management Generate ad hoc and scheduled compliance reports



NERC CIP and compliance requirements
NERC developed the CIP standards to protect critical infrastructure necessary to ensure the reliable operation of North America’s BES from cyber and physical security threats. Enforced by NERC under the oversight of the Federal Energy Regulatory Commission (FERC), the standards are mandatory for registered entities responsible for critical aspects of BES operation. Over time, they’ve evolved from basic perimeter defense requirements into a mature framework that reflects the complexity of today’s Information Technology (IT) / Operational Technology (OT) environments.
Structure and focus of the NERC CIP standards
There are currently 13 enforced CIP standards, each organized around specific domains such as asset identification (CIP-002), physical security (CIP-006), incident response (CIP-008), and configuration management (CIP-010). Each standard includes detailed requirements and defined measures that entities must meet and demonstrate through documentation and evidence. While the standards provide structure, implementation can vary significantly depending on an organization’s architecture and maturity level.
As utilities navigate these standards, implementation often requires coordination across IT, OT, compliance, legal, and operations teams. For organizations seeking to understand the intersection between CIP and physical security, the SecuriThings Guide to NERC CIP Compliance for Physical Security offers a great overview.
The table below outlines all current NERC CIP standards along with their primary focus areas. This provides a high-level view of the regulatory landscape that compliance programs must address, from asset identification and access control to incident response and supply chain risk.
| NERC CIP Standard | Focus area |
|---|---|
| CIP-002 | Asset Identification |
| CIP-003 | Security Management Controls |
| CIP-004 | Personnel & Training |
| CIP-005 | Electronic Security Perimeters |
| CIP-006 | Physical Security of BES Cyber Systems |
| CIP-007 | Systems Security Management |
| CIP-008 | Incident Reporting & Response Planning |
| CIP-009 | Recovery Plans for BES Cyber Systems |
| CIP-010 | Configuration Change Management & Vulnerability Assessments |
| CIP-011 | Information Protection |
| CIP-012 | Communications Between Control Centers |
| CIP-013 | Supply Chain Risk Management |
| CIP-014 | Physical Security (of Transmission Stations/Substations) |
| CIP-015 | Internal Network Security Monitoring (Draft) |
Compliance is evolving, and your program should too
The NERC CIP program continues to evolve as cybersecurity risks and operational environments become more complex. New revisions to existing standards, such as CIP-003-9, CIP-005-7, CIP-010-4, and CIP-013-2, introduce stricter controls for areas like remote access, transient cyber assets, patch validation, and supply chain oversight.
In addition to these updates, NERC has introduced a new fourteenth standard: CIP-015, Cybersecurity – Internal Network Security Monitoring (INSM). While not yet enforceable, CIP-015 represents a significant shift in how utilities must approach threat detection and response. It requires continuous monitoring of internal network traffic to detect unauthorized communications, lateral movement, or other signs of compromise within Electronic Security Perimeters. Organizations that treat compliance as a fixed checklist risk falling behind. A sustainable CIP program matures, adapts to changes, and incorporates new security expectations into operations before they become regulatory mandates.
Understanding the security controls – Descriptions and real-world implementation challenges
The NERC CIP standards span 13 active domains, each designed to address a specific layer of security for BES Cyber Systems. These include asset identification, physical and electronic access control, personnel training, system configuration, vulnerability management, and incident response. While the standards provide a consistent framework, the path to implementation often requires interpretation, customization, and sustained effort across technical and organizational boundaries.
What makes CIP compliance so complex is not just the requirements themselves, but the operational realities utilities face when trying to apply them. Even with clear policies and intentions, day-to-day execution often falls short due to various technical and resource-related challenges.
Common implementation challenges
While implementation challenges vary from organization to organization, specific challenges consistently impact BES operators across the industry.
Administrative overhead
NERC CIP compliance demands a high degree of organization and attention to detail. Program managers must stay current with evolving regulatory requirements, emerging adversary tactics, techniques, and procedures (TTPs), as well as the unique risk landscape of each site. Although compliance is mandatory, the ultimate goal is not simply to check boxes; it’s to reduce the likelihood of a disruptive cyberattack and protect the reliability of the BES.
The standards require detailed documentation, formalized processes, and ongoing evidence collection across a wide range of security functions. For many utilities, particularly smaller co-ops and municipal operators, this workload often falls on a limited number of individuals who also manage IT, OT, and operations responsibilities. The absence of dedicated compliance staff means that tasks like access reviews, incident logging, and self-assessments are often handled reactively or inconsistently.
Workforce and skills shortages
A significant barrier to NERC CIP compliance is the strain it places on already limited staff. Few organizations have personnel with the combined expertise in IT, OT, cybersecurity, and regulatory compliance that the standards demand.
High turnover, a shortage of qualified professionals, and limited training pipelines make it challenging to build and retain teams capable of sustaining a mature CIP program. As a result, many organizations struggle with continuity and institutional knowledge over time.
Leadership commitment and support for a NERC CIP compliance program
Even when leadership is supportive, awareness gaps remain. Executives or boards may not fully understand the complexity of NERC CIP or the risks associated with failing to meet its requirements. Without consistent communication and visibility into compliance health, it becomes increasingly difficult to secure the funding, staff, and technology investments necessary to mature the program.
Technical implementation
In addition to organizational challenges, many entities face significant technical hurdles.
- Asset identification and inventory management, while foundational to NERC CIP compliance, remains a common weak point. Organizations often lack automated tools to discover and track assets across IT, OT, and physical security environments. Without clear visibility into what exists on their networks or the ability to map their assets, BES operators risk leaving critical systems unprotected. Although asset inventory may seem like a straightforward requirement, it is essential for effective risk management and is frequently underestimated.
- Log retention and visibility remain challenging for many organizations. Collecting and securely storing system and security logs requires the right combination of tools, trained personnel, and well-defined retention policies. This becomes especially difficult when dealing with physical security or OT devices that do not easily integrate with enterprise log management systems. Ensuring that logs are tamper-proof is crucial, as adversaries may attempt to alter or delete them to conceal their activities. These records are essential not only for real-time monitoring but also for incident detection, investigation, and forensic analysis.
- Legacy systems continue to pose compliance and security risks. Devices that cannot support encrypted communication, role-based access, or regular patching introduce vulnerabilities and complicate efforts to meet modern control expectations. Replacing them is often expensive and disruptive, but leaving them in place increases both regulatory and operational risk.
- Lack of automation remains a limiting factor across nearly every requirement. Manual patch tracking, evidence collection, access control validation, and documentation updates consume time and increase the likelihood of missed steps or outdated records. This reliance on human effort not only raises compliance risk but also contributes to staff burnout and audit fatigue.
Best practices for building and sustaining a NERC CIP compliance program
Successfully meeting NERC CIP requirements is only part of the challenge. The greater task is sustaining compliance over time, across evolving infrastructure, staffing changes, audit cycles, and regulatory updates. This section outlines best practices that help organizations move from reactive compliance to a continuous, well-managed, and security-driven program. Each area includes practical steps, organizational considerations, and, where applicable, examples of tools and strategies that support long-term resilience.
Establish governance and accountability structures
A successful CIP program begins with clear governance. Assigning a dedicated CIP compliance lead or team ensures day-to-day ownership, continuity, and accountability. Roles and responsibilities should be documented across departments, and the compliance team should be empowered to engage with IT, OT, legal, and executive leadership. Centralized dashboards or reporting platforms provide real-time visibility into compliance health and help identify emerging gaps before they become audit issues.
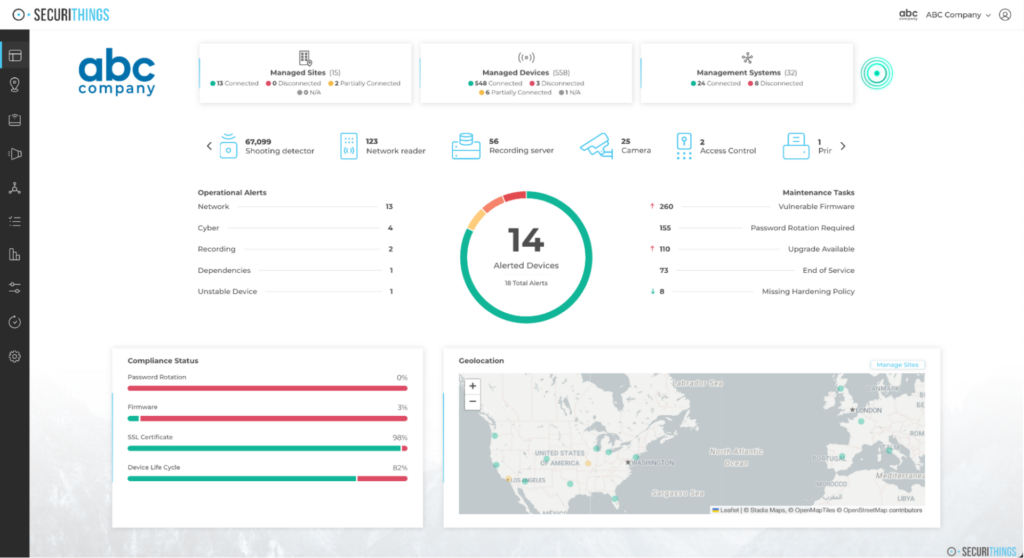
An example of a centralized dashboard for monitoring device health, compliance status, and operational alerts across sites. (Source)
Promote cross-functional collaboration across IT, OT, compliance, security, legal, and operations
Breaking down silos is essential. NERC CIP touches a wide range of operational domains, and collaboration is an absolute requirement to close policy-to-practice gaps. Creating a standing compliance working group with representatives from IT, OT, security, legal, risk management, and operations helps align efforts, share data, and streamline workflows.
Real-time monitoring of physical and cyber assets, including shared access to device health, credential status, and certificate management, enables teams to detect issues faster and coordinate effectively. As highlighted in this blog by SecuriThings, this kind of cross-team coordination is especially valuable for physical security teams working to comply with cybersecurity-driven controls.
Treat audits as continuous health checks, not one-time events
Organizations that treat audits as periodic events often struggle to maintain consistency. Instead, organizations should build CIP compliance into their normal operations. Conducting regular internal mock audits or readiness reviews helps keep documentation current, identifies recurring issues, and reduces last-minute scrambles. Tracking audit outcomes over time also allows teams to measure progress and demonstrate maturity. Automated reporting tools can further reduce the overhead of evidence preparation.
Strengthen documentation and evidence management
Strong documentation is the backbone of a defensible compliance program. Policies, procedures, logs, and other artifacts should be maintained in a centralized, version-controlled repository. Each requirement should map clearly to supporting evidence that can be accessed quickly during audits.
Automate wherever possible to reduce manual effort and risk
Manual processes not only consume staff time but also increase the likelihood of errors or missed tasks. Wherever feasible, organizations should automate routine compliance functions such as access reviews, account management, password rotations, certificate renewals, firmware updates, vulnerability scanning (where possible), and health monitoring. Automation also enables more frequent and consistent policy enforcement across devices and sites. For example, as discussed in this SecuriThings blog post, automating the management of physical security devices can significantly reduce compliance costs while improving system uptime and control.
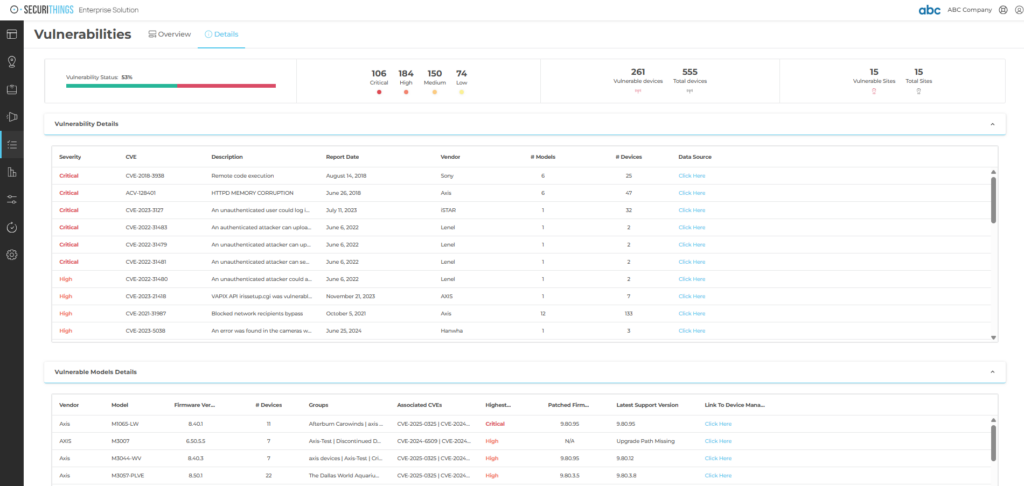
An example of automated vulnerability tracking, helping teams prioritize risks and streamline NERC CIP compliance. (Source)
Apply best practices across all standards using people, processes, and technology
Once the foundational program elements are in place, organizations should focus on operationalizing best practices across the full set of CIP requirements. This includes applying strong identity and access management, implementing network segmentation, ensuring secure remote access, maintaining reliable patch and configuration management, and performing regular vulnerability assessments. Monitoring should be continuous and integrated across systems. Technology platforms, supported by well-trained staff and repeatable processes, help ensure these controls are implemented consistently. SecuriThings, for example, helps operationalize controls across CIP-003, CIP-005, CIP-006, CIP-007, and CIP-010 by securing the cyber posture of physical security devices and providing centralized visibility.
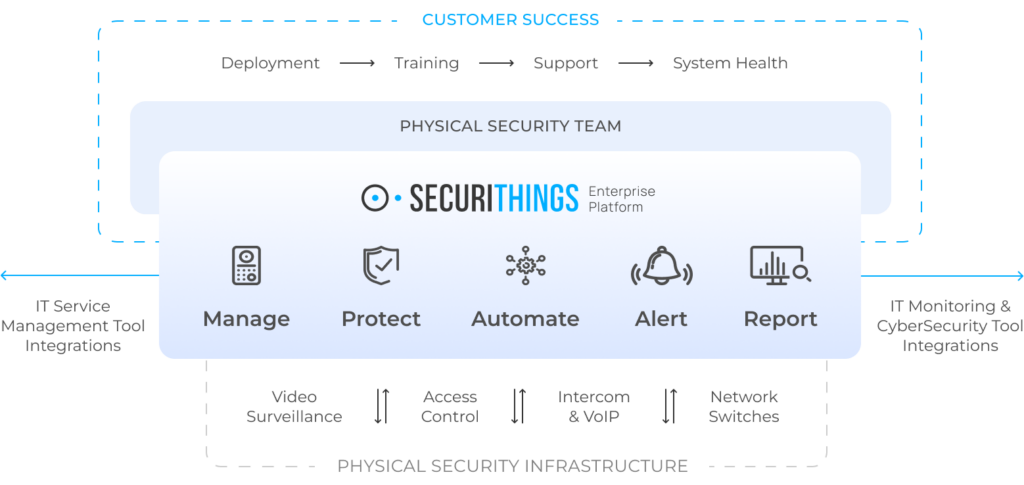
An example of a unified platform supporting device management, automation, alerting, and reporting across physical security infrastructure. (Source)
Last thoughts
A sustainable compliance program depends on a strong organizational culture. Compliance should not be seen as the sole responsibility of the security or compliance team. Every department has a role to play in protecting critical systems, supporting audit readiness, and ultimately contributing to the reliability of the Bulk Electric System and the safety of the communities served.
Leadership must consistently emphasize that compliance is integral to operational excellence. Fostering a culture of shared responsibility improves audit performance and enhances the organization’s ability to detect, respond to, and recover from cybersecurity threats.
The right platform can streamline NERC CIP compliance by automating routine tasks, enhancing device visibility, and facilitating continuous monitoring across both physical and cyber assets.