Physical Security Software
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
- Chapter 13: Best Practices for Corporate Physical Security
- Chapter 14: Physical Security Best Practices
- Chapter 15: How physical security powers
- Chapter 15: Best Practices for Physical Security Devices
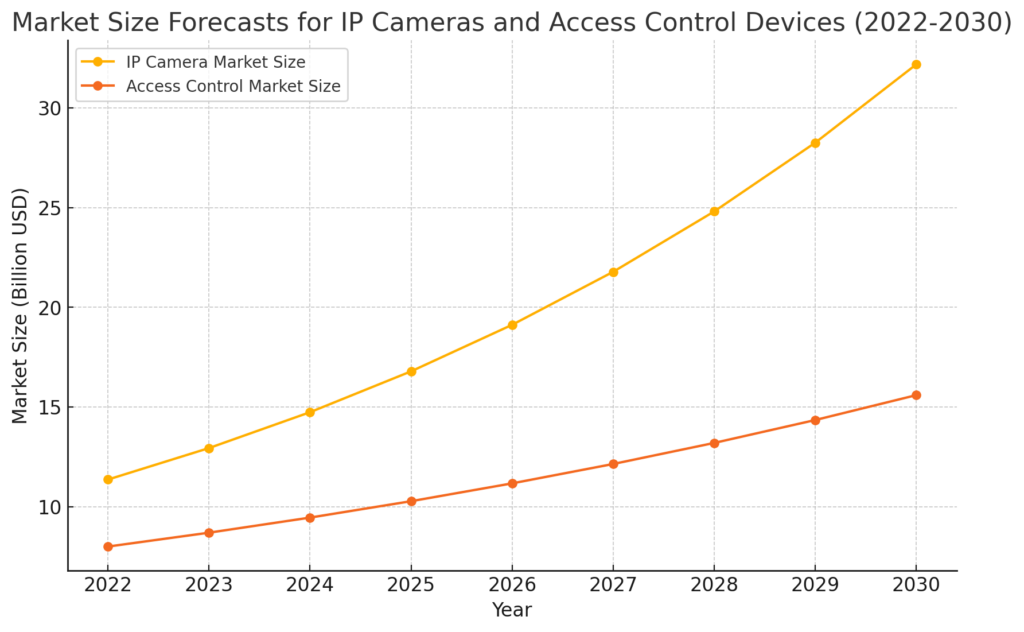
The growing presence of physical security devices has significantly challenged cybersecurity and IT professionals. For instance, the global IP camera market was valued at $11.4 billion in 2022 and is expected to expand at a compound annual growth rate (CAGR) of 13.9% from 2023 to 2030. It is also estimated that the global access control market will have a CAGR of around 8.7% during the forecast period.
This rapid expansion is fuelled by institutions seeking to enhance their physical security with advanced surveillance cameras, access control systems, intrusion detection systems, and diverse IoT devices. However, the proliferation of these devices presents several challenges. One of these challenges is growing cybersecurity risks with the rise of physical security devices. Each network-connected device is a potential cyber-attacker threat vector, making the overall security ecosystem more vulnerable to breaches. These devices often have varying levels of cyber protection. If not correctly managed and updated, they can be an easy target for cybercriminals, potentially leading to unauthorized access, operation disruptions, or the theft of sensitive information.
Advanced physical security software is essential for managing and securing these devices effectively. Choosing the right physical security software is a strategic task: Physical security and IT professionals should carefully assess the best solution that meets their expectations and fits their organization’s strategic vision. This article outlines the key features that every top-notch physical security software should have.
Summary of key physical security software features
| Desired feature | Description |
|---|---|
| Multi-vendor support technology | Ensures wide compatibility with various hardware devices from different physical device manufacturers |
| Seamless deployment | Facilitates automated asset discovery and efficient installation and configuration of the software |
| Consolidated platform | Provides a unified interface for managing all IoT (or networked) devices from a single point of control |
| Real-time monitoring and alerting | Enables timely security breach identification, resulting in more time for remedial action |
| Compliance reporting | Automates the generation of reports required to ensure compliance with leading regulatory standards like SOC 2 |
| Automated firmware upgrades and password retention | Automates firmware updates and manages password policies to ensure ongoing security and reduce the risk of breaches |
| Scalability | Supports more devices and expanded operations without requiring extensive reconfiguration of the infrastructure or huge upfront capital expenditures |
| Integration with other systems | Seamlessly integrates with other enterprise security information and event management (SIEM) systems and ticketing management software |
| User-friendly interface | Ensures that the learning curve is short for collaboration among new users such as IT engineers, security professionals, and non-technical physical plant managers |
| Customer success and technical support | Provides ongoing assistance and resources, ensuring continuous operation, quick resolution of technical issues, and professional services when required |
| Backup and restore | Ensures business continuity, protection for critical data, and resilience against hardware failures, cyberattacks, and other disasters |
Multi-vendor support technology
Multi-vendor support of physical security software ensures compatibility with diverse hardware, enhancing flexibility and scalability while reducing costs. The software should be capable of integrating with various physical security and IoT device manufacturers, allowing for cohesive security strategies. For example, you could integrate an access control system from one vendor (like Software House, LenelS2, or Honeywell) with surveillance cameras from another (such as Axis, Hanwha, or Bosch) to enable synchronized monitoring and incident responses.
This flexibility avoids vendor lock-in and lets you use the best device for each task. Accommodating a wide range of physical security and IoT device brands and technologies can help your organization optimize its physical security infrastructure needs without being tied to a single vendor.
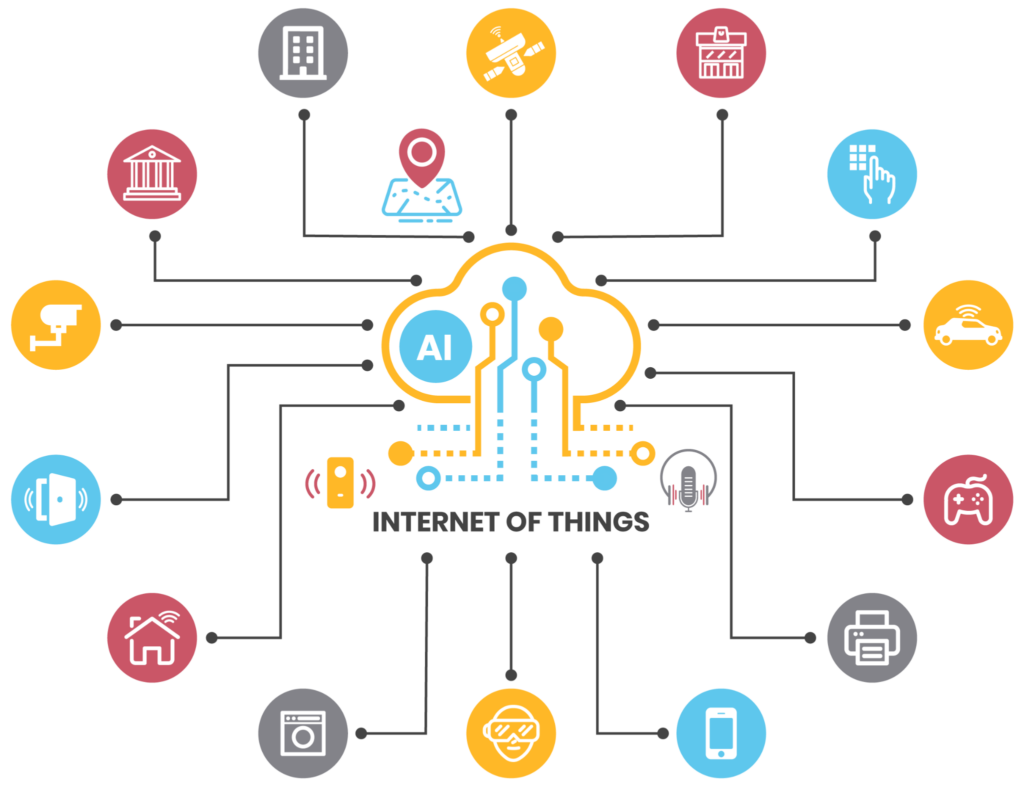
Networked physical devices managed using IoT communication protocols (source)
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Seamless deployment
Seamless deployment ensures the efficient installation and configuration of the physical security software, minimizing downtime and ensuring a smooth transition from existing systems. This feature streamlines the deployment process with preconfigured settings and automated setup routines, reducing the time and effort required to get the system up and running.
Here are the key steps for deploying physical security software:
- Planning and integration: Assess compatibility with existing systems from multiple vendors. Plan the configuration to integrate different physical security devices using SDKs or APIs, such as access control and surveillance cameras.
- Installation and configuration: Install the software and configure it to interface with different vendor systems. Set up automated asset discovery for seamless device recognition.
- Testing and validation: Verify functionality and data synchronization across integrated systems.
- Go-live and support: Implement the system with minimal disruption and ensure ongoing support for optimization and troubleshooting.
The physical security software will automatically discover all IP-based connected devices and add them to the dashboard, making them ready for mounting and control. For legacy devices, many organizations plan to gradually upgrade to modern, networked alternatives or use converters or adapters for better control and management.
For example, analog CCTV cameras can be connected to the network using multi-channel video encoders. This setup allows using existing coaxial cables while the encoder converts the video stream to a digital format. Brands like Axis provide solutions for transmitting the digital video stream over the network to the Video Management Software (VMS). Another approach is to replace analog cameras with IP-based cameras that offer better specifications while maintaining the existing coaxial cables by adding coax-to-Ethernet converters with power over Ethernet (PoE).
Both approaches serve as a middle ground instead of a complete replacement of the legacy system, saving costs and reducing the time required. They also minimize the labor and material costs of installing new cabling where existing cameras are located.
Consolidated platform
Managing physical security devices across multiple systems can be complex and inefficient, causing slower response times and difficulty in obtaining a comprehensive view of security operations. Without a consolidated platform, asset discovery is often incomplete. These gaps in asset discovery result in partial reporting and alerting, with crucial components of the security environment missing.
A consolidated platform integrates all security devices into a single management interface, enabling comprehensive asset discovery. This foundational step ensures that reporting is complete and alerts encompass the entire environment. Additionally, centralized collaboration tools within the platform help bridge the gap among IT engineers, physical security, and cybersecurity professionals, ensuring that all stakeholders are aligned and informed. This centralized approach not only reduces complexity but also improves operational efficiency.

A consolidated physical security platform (source)
Real-time monitoring and alerting
Continuous monitoring allows real-time identification and resolution of operational issues, ensuring your device inventory remains current and protected from cyber threats. Comprehensive information enables timely maintenance tasks and early detection of potential errors and security risks.
However, a balance is needed. Too much information might cause alert fatigue, which reduces efficiency and can divert attention away from vital concerns. Unreliable alerts that require manual monitoring can lead to significant problems being overlooked.
To mitigate these risks, a consolidated management approach is required. This strategy should deliver relevant information to the right stakeholders at the right time without being overwhelming or distracting. A solution that distinguishes between technical issues and integrates with your IT ticketing system is crucial for streamlining alert handling and improving collaboration with IT professionals. Like the example in the screenshot below, such a solution involves event deduplication and correlation using machine learning, artificial intelligence, and preset rules.
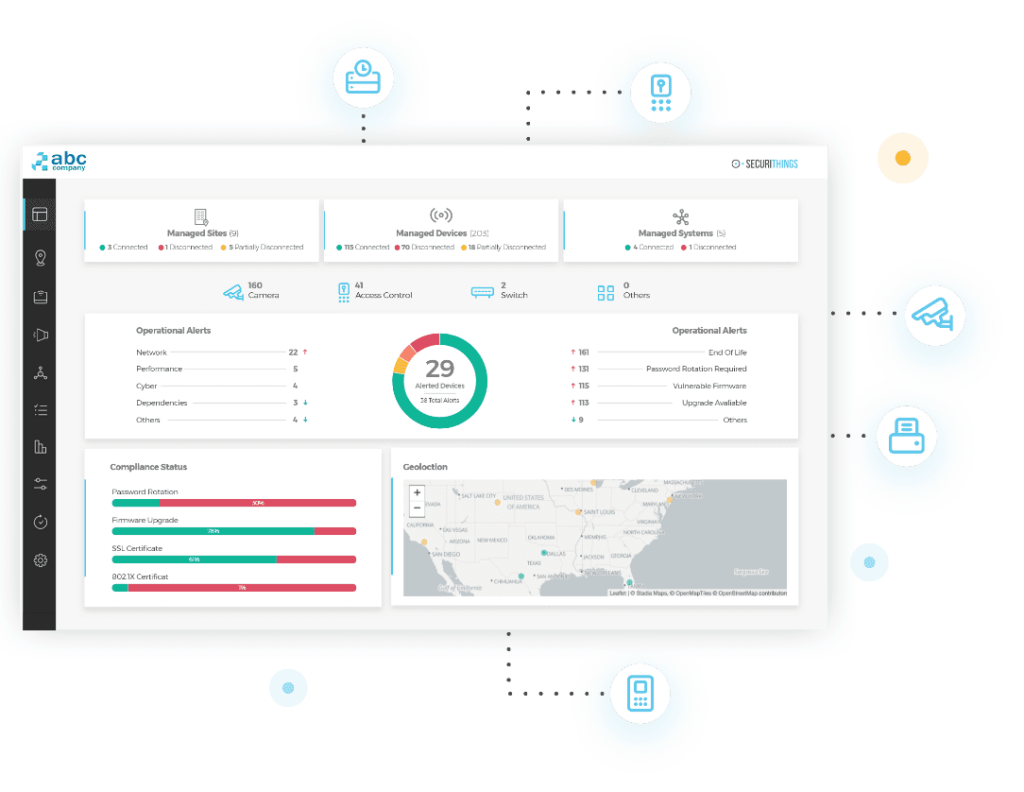
Real-time monitoring and alerting dashboard (source)
Compliance reporting
Compliance reporting helps you automate the generation of reports and ensures that the security measures meet regulatory standards. The physical security software should facilitate audit readiness and reduce the risk of penalties. This feature simplifies the audit process and enhances the organization’s credibility by documenting and verifying all security measures.
For example, ISO/IEC 27001 outlines the best practices for managing and securing information assets. To comply with this standard, the following reports are needed:
- Security incident reports: Document breaches or security incidents, including responses and mitigation steps
- Risk assessment reports: Evaluate potential threats and vulnerabilities, detailing the measures to address them
- Compliance audits: Ensure compliance with ISO 27001 standards and identify areas for improvement.
Automatic firmware upgrades and password management
Automating firmware updates and password management, including regular password rotation, ensures that devices run the latest, most secure versions and enforces strong password policies.
A manual firmware upgrade includes several steps:
- Check for new firmware releases.
- Ensure compatibility with the OS and hardware version.
- Download the firmware for each device.
- Push the firmware on each device one by one using the right device-specific tool.
- Verify the device functionality or revert to the original firmware.
This process is time-consuming and error-prone. In contrast, an automated system can handle all these steps seamlessly, ensuring that all devices run the latest, most secure versions while enforcing strong password policies effortlessly.
It goes almost without saying that passwords serve as a crucial first line of defense for physical security devices like cameras, access control systems, and intrusion detection. However, research indicates that many security breaches stem from unchanged default passwords or poor password practices. Default login/password combinations—such as support/support, admin/admin, admin/0000, user/user, and root/12345—are frequently exploited, potentially compromising up to 10% of all physical security devices. This vulnerability highlights the critical need for robust automated password management to protect against security threats.
Automating firmware updates and password rotations is an effective strategy for achieving security compliance. It allows physical security professionals to focus on more critical tasks.
Scalability
Scalable physical security software supports organizational growth by quickly adding new devices and expanding operations. It adapts to increasing demands, ensuring that security measures keep pace with organizational expansion.
Choosing physical security software as a service (SaaS) helps address scalability challenges and effectively manage both capital expenditures and operational expenses. A SaaS model eliminates the need for substantial upfront capital expenditures (CapEx) on hardware and infrastructure, such as servers and storage, because the service provider handles these aspects. Additionally, operating expenses are more predictable and can be scaled according to the organization’s needs, allowing for flexible budgeting.
This model also simplifies scaling up or down: Additional resources and features can be accessed on demand without requiring extensive hardware upgrades or new installations. By leveraging SaaS, organizations can ensure that their physical security systems remain adaptable to changing requirements without incurring the high costs and complexities associated with traditional on-premises solutions.
Integration with other systems
Seamless integration with enterprise systems enhances organizational efficiency and security. The physical security software should support open APIs and connectors for data sharing and coordinated responses, improving overall security management and integration with other enterprise security information and event management (SIEM) tools, such as Splunk, Qradar, ServiceNow, etc., and various ticketing management products, like Atlassian’s Jira.
Seamless integration ensures that physical security measures work harmoniously with other critical systems within the organization and reduces the hassle of performing customized integration development. This interconnected approach leads to better data sharing and better-coordinated incident responses.
User-friendly interface
An intuitive interface reduces the learning curve and increases productivity for security personnel. The physical security software should offer easy navigation, customizable dashboards, and quick access to essential features.
Here are some of the key benefits of a centralized dashboard and customizable reports:
- Centralized dashboard: Provides a unified view of all security operations, simplifying monitoring and management.
- Customizable reports: Let you tailor reports to meet specific needs and use cases. For instance, during installation, the physical security team can have a report to check the device inventory by region and track the deployment process. At the same time, the cybersecurity team can generate a compliance report to ensure audit readiness.
A user-friendly and configurable interface, like the example shown below, allows self-service by end-users, which reduces reliance on the IT department to answer questions and perform customization. The result? A lower total cost of ownership.
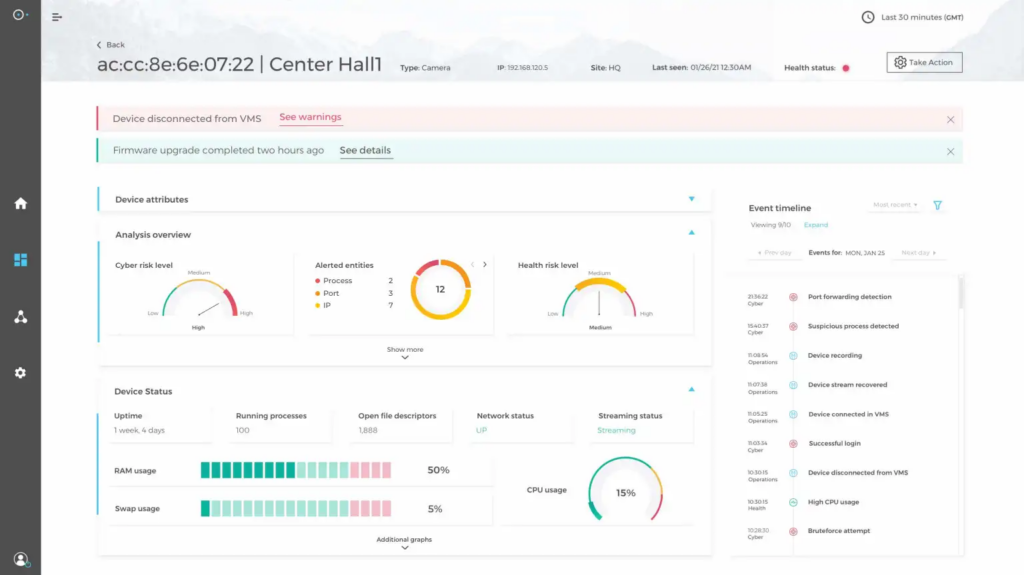
Customer success and technical support
The physical security software vendor should be able to provide 24/7 assistance, online resources, training, and regular updates to maximize the software’s effectiveness.
The physical security software vendor should also provide professional services and integrate with the client’s internal systems (such as a ticketing system, if not standard), supporting customized escalation priorities triggered by specific events.
The need for these services rules out the adoption of open-source software since they lack such a level of support.
Backup and restore
Manual backup tasks are time-consuming and prone to human error, especially if you have to log in to each device, download a backup of the latest configuration or database, and then save it in a designated folder. Restoring these backups is also slow, particularly during outages or disasters—when time is of the essence. These manual processes are inefficient and can lead to inconsistencies or missed backups.
This is where the automatic backup and restore feature truly shines. You can create backup groups and assign devices according to their sensitivity, function, or location using an automated backup process. Then, you can configure a backup schedule and select an offsite destination folder, and the system will handle the rest.
Typically, backup tasks run less frequently on edge devices and more frequently on servers or backend devices. If any backup task fails, the system should send an alert so you can implement the appropriate mitigations. While manual backups are sometimes essential before configuration changes or upgrades, completing this task with one click is key to reducing time and effort.
The backup and restore feature is also required for organizations to comply with ISO 27001:2022. All business-critical data, software, and systems should have backup facilities to ensure that they can be recovered following events such as business interruptions, system or storage media failures, data loss, or intrusions.
Last thoughts
Physical security software is essential for modern security strategies, offering advanced tools to monitor and manage assets effectively. As physical security and IT professionals, understanding these critical features will help you choose and implement the best physical security software solution.
Features like vendor-agnosticism, real-time monitoring, compliance reporting, and seamless integration with other systems strengthen your organization’s security posture, improve operational efficiency, reduce costs, and ensure regulatory compliance. A centralized dashboard offers a unified view of all security operations, consolidating critical information in one place and improving decision-making efficiency. Customizable reports further enhance this capability, allowing different teams to generate reports tailored to their needs.
SecuriThings, a trusted partner for many Fortune 500 companies, provides a comprehensive physical security platform that supports these features and services. It’s designed to manage hundreds of thousands of devices, including cameras, access control devices, and intrusion detection systems.