Best Practices for Corporate Physical Security
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
- Chapter 13: Best Practices for Corporate Physical Security
- Chapter 14: Physical Security Best Practices
- Chapter 15: How physical security powers
- Chapter 15: Best Practices for Physical Security Devices
An effective physical security program must align mitigation measures with daily operational risks. As today’s security programs increasingly rely on connected security devices, it becomes more important than ever to effectively integrate cybersecurity and resilience as key parts of a physical security program.
Meanwhile, organizations are becoming increasingly regulated, and corporate physical security programs must adapt their scope to meet the growing scrutiny. Security practitioners will need to balance industry-specific regulations without being seen as “Big Brother” looking over every employee’s shoulder or violating their privacy.
This article discusses the development, scaling, and implementation of corporate physical security and recommends best practices for a threat-based and business-focused program tailored to an organization’s risk profile.
Summary of best practices for corporate physical security
| Best practice | Description |
|---|---|
| Develop a resilient, converged corporate physical security strategy | Implement a corporate security program that focuses on resilience and cybersecurity, aligning with these functions and effectively managing risk. |
| Develop a program focused on the organization’s physical security risks | Conduct a structured assessment to understand physical security risks and quantify their impacts and needed mitigation measures. |
| Position corporate physical security as a business enabler | Align the security program to the business by providing value and through effective metrics. |
| Implement a scalable technology strategy | Use integration-friendly systems, develop an asset strategy, and embrace emerging technologies. |
| Optimize physical security compliance | Align the corporate physical security program to country-specific laws and industry regulations. |
| Foster proactive approaches to physical security | Implement preventive and change control to modify employee behavior and create a more secure environment. |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Develop a resilient, converged corporate physical security strategy
A modern and effective corporate physical security must embed resilience as a key component of its framework. The future of corporate physical security lies in a more converged program where corporate physical security, cyber, and information technology are closely aligned.
Assess opportunities for convergence and the risk of physical/cyber threats.
Corporate physical security programs should assess the opportunities and costs of developing a converged physical and cybersecurity program. A key driver should be understanding whether the organization faces a significant risk from hybrid threats, which are attacks that originate in both physical and cyberspace and impact assets in both areas.
Some preliminary questions security practitioners should think about if deciding to pursue this path are:
- What is the organization’s maturity model, and can/will leadership be supportive of this type of change?
- What are the current threats the organization faces, and are hybrid threats more or less likely to impact the organization?
- Does your organization rely heavily on the Internet of Things (IoT), Operational Technology (OT), and/or Industrial Internet of Things (IIoT)?
- How can we conduct an internal strengths, weaknesses, opportunities, and threats (SWOT) analysis to determine the possible impact of a converged program?
A gap assessment should include incorporating the NIST Cybersecurity Framework 2.0 or other relevant frameworks or standards to better identify and manage risk. For example, the voluntary adoption of NIST CSF 2.0 by critical infrastructure sectors is vital since these organizations face a higher risk of hybrid threats.
SCADA systems are particularly vulnerable to both physical and cyber threats due to their importance in complex industrial operations. As more companies start rolling out IoT devices, it will become necessary for corporate physical security programs to understand where the risks are in their systems/technologies. Security practitioners should look to device management solutions that can give them both high-level insights and also granular information to ensure that they manage and secure their physical infrastructures.
Embed resilience as a key component of physical security strategy
As corporate physical security programs shift toward more interconnected devices and digital infrastructure, resilience will need to be a key component. Successful programs now need to prioritize disaster recovery efforts (the first 12 to 24 hours). As part of the disaster recovery model, programs should focus on identifying their core services: maintaining resilience in the event of a crisis (and with limited guard force personnel) and outlining how a corporate security program will recover from an incident.
To ensure operational continuity, physical security should be integrated into the broader business continuity lifecycle. This means preparing not just for preventing incidents but also for maintaining critical operations during a disruption and enabling rapid recovery. The diagram below illustrates how corporate physical security plays a role at each phase of the lifecycle, from preparedness and response to recovery.

Corporate physical security should have programs designed to be part of the business continuity lifecycle. (source)
Develop a program focused on the organization’s physical security risks
Corporate physical security programs should be developed, scaled, and matured in a manner that meets the company’s specific needs and requirements. While security practitioners are the subject matter experts (SMEs), they must also rely on their stakeholders to understand what the risks are and to develop measures that fit the needs of the business.
Understand the organization’s business and key assets
An important but often overlooked step in developing an effective program is conducting regular interviews with key stakeholders. Ideally, these interviews should be conducted by a senior-level security practitioner who has built trust/rapport across the organization and is also capable of handling criticism of the program.
A successful corporate physical security program will need to take into account operating environments, including the types of buildings (office, manufacturing spaces, labs, and industrial facilities) and whether they are shared, leased, or owned locations. Security practitioners should do all of the following:
- Conduct regularly cadenced site assessments.
- Develop an after-action review process for those incidents and near misses that have the potential to impact the organization significantly.
- Meet regularly with site leadership for training, check-ins, and touch bases.
- Develop and maintain relationships with local law enforcement and emergency services.
An effective corporate physical security program will leverage its understanding of the business, its assets, and its associated risks to develop measures that are tailored to the organization.
Leverage data/metrics to better understand and quantify risk to stakeholders
A corporate physical security program needs to demonstrate its organizational return effectively. This should include using quantifiable metrics or impactful case studies. Whatever method is chosen, the most important consideration is that the information be presented in a manner that speaks to executive leadership.
Security practitioners should consider the following questions to assess their understanding of the company’s physical risk:
- Do we have a case management system for incidents and a device management system for logging security technology?
- Are we consistently tracking and classifying incidents and activities across our locations?
- Are we regularly assessing and benchmarking our program against government standards or by outside qualified consultancies?
Position corporate physical security as a business enabler
Here are a few considerations to keep in mind.
Speak the language of the business
Security practitioners need to understand and speak effectively in the business’s language. This does not mean using corporate jargon or prose but rather being able to communicate with business units and leaders in terms/concepts that they understand. For example, if a biotechnology company faces significant issues with unauthorized access, a security leader should be able to explain how these incidents could lead to inadvertent entry into a clean room, resulting in cleanup needs and manufacturing downtime.
Leverage security technology as a business informatics system
Security systems should be viewed not only for their ability to mitigate risk but also for how these tools can help drive business decisions. Specifically:
- Use security technology to help drive business decisions: In the post-COVID workforce, tools like physical access control systems (PACS) can be used to drive business decisions such as whether a company should move towards hot desking (i.e., desk swapping) or what type of real estate portfolio the company’s strategy should be going forward. Security technology can provide vital, often real-time information that can help business leaders make smarter decisions on how they allocate their facilities for their workforce.
- Implement device management for a holistic view of physical security infrastructure: Physical security practitioners should integrate smart device management that can provide a consolidated real-time snapshot of all their security technology infrastructure. As more connected and smart devices are added to an organization’s network, it will be increasingly necessary for the corporate physical security program to have a real-time management system that can give them details about their devices’ integrity, status, and operability.

A device management solution that can track all physical security infrastructure. Source
Be sure that the security program is visible
A corporate physical security program should not operate behind the scenes; it should be at the forefront for visibility. A “marketing strategy” for the program might entail activities like town halls where corporate physical security presents changes, posting updates and/or news on the company intranet, and regularly presenting to different business units/leaders on security topics of interest.
As a forward-facing department, corporate physical security programs can look to incorporate market research metrics to better gauge and align their services to employees’ needs. These could be accomplished through employee engagement surveys, targeted polling after an incident, or high-level discussions with executive leadership on security needs. It is important that security practitioners distill the feedback received to understand what is a subjective evaluation (e.g., “I don’t like using an ID badge”) versus an objective evaluation (e.g., “I think we should modify the door to use a pin pad versus a badge reader”).
Implement a scalable technology strategy
As security technology becomes more intertwined and connected, it is necessary for security practitioners to adjust their mindsets and move away from closed and/or proprietary systems to scalable and integration-friendly ones. Corporate physical security programs should work closely with stakeholders in information technology, cybersecurity, human resources, and facilities to develop a strategy that is optimally aligned with the business as much as possible.
Use an integration-friendly approach
This method of implementing security technology is essential for scalability; while in an ideal world security practitioners would want plug-and-play solutions, this can introduce unintended risks. An effective risk management approach strikes a balance between integrating new technologies and utilizing effective supply chain risk management principles/or adapting existing technologies to fit specific use cases. A device management system that monitors the health, performance, and security of connected devices, including but not limited to firmware and software, is key to implementing this type of open solution. Here are two practical considerations:
- Tailor device selection to meet the business’s needs: Security practitioners should select devices that meet the operational requirements of their company’s stakeholders. For example, if you work in a manufacturing plant where employees often must carry and/or move objects, consider whether a PIN pad or facial recognition is the better fit. Before implementing new solutions, try doing test runs with selected stakeholders to validate the usability and the effectiveness for the environment.
- Use predictive forecasting to manage end of life (EOL) and end of service (EOS): As security programs become more dependent on security technology, lifecycle management will be increasingly important to ensure optimal usage, limit downtime, and effectively use more limited budgets. A predictive forecasting model should consider factors like office locations, age of/types of devices being used, availability of integrators, and impacts on stakeholders when assessing lifecycle management.
Implement naming conventions and audits
A corporate physical security program, with its vast array of locations, technology, and processes, needs to develop a coherent process to manage and optimize deployments:
- Use a standardized naming convention: Security practitioners should develop a standardized process for naming their devices. This ensures that it is easier to identify and resolve issues with specific devices.
- Conduct regular audits of devices/location: As new devices are added, old devices are replaced/updated and office locations are updated. A regular cadence of virtual management combined with in-person checks can help ensure that regular inventory management is maintained.
Implement a device management system
Security teams should prioritize implementing and categorizing their devices. For enterprise organizations, device management should go beyond manual tools like spreadsheets, which are error-prone and difficult to scale, and instead rely on purpose-built platforms, whether on-premises or cloud-based, that offer real-time visibility, control, and integration. One of the benefits of a cloud-based provider is a clear platform for dashboarding, device aggregation, and firmware/hardware management.
Strategic questions to ask:
- Does my company have an ISO and/or NIST standard that I need to comply with?
- Does my company have any GDPR and/or local regulations regarding data security that I need to comply with?
- Is there existing company/enterprise software that I can leverage without adding a new vendor?
Tactical questions to ask:
- How user-friendly is the platform for non-technical users?
- How many of what types of devices will be monitored, and is my physical security technology/infrastructure consistent globally?
- How many APIs/integrations does the provider have to connect with our company systems/software?
- What type of reports can the system generate, and do these reports fit my use cases?
Embrace emerging technologies
Security practitioners should assess whether emerging technologies, such as generative AI or drones, can effectively support and enhance their corporate physical security program:
- What security needs are not being met? Security teams should think about non-critical gaps in their operations where emerging technologies might deliver an ROI. For example, this might be using generative AI for incident templates or drone technology to surveil a large industrial complex.
- Use emerging technologies as a tool: Whether it’s AI, drones, or biometrics security, practitioners should remember to remind themselves that these are tools. Their effectiveness, productivity, and output should be continually measured and assessed against the program’s needs.
- Remain compliant: New security technologies continue to blur the line between privacy and security. An essential consideration should be to ensure that all privacy and compliance considerations are examined and adhered to.
Dive deep into manual processes to see where automation can assist and reduce costs
A security team should conduct a thorough review of its entire operational portfolio to identify manual/unneeded processes and determine where automation can be leveraged to effectively reduce costs without compromising service delivery. Corporate physical security programs should be open to meaningfully understanding what their teams actually spend their time doing. Security practitioners should also spend time observing their operations, talking with members of their teams, and soliciting feedback from stakeholders. After they have done these steps, they will be better able to measure where technology can more effectively assist.
Optimize physical security compliance
Embed and audit compliance as part of the corporate physical security program
Security teams need to embed audit and compliance into their programs. With the prevalence of the EU GDPR laws and similar laws in 17 countries, it is important that corporate physical security programs understand and comply with these data regulations. Given the scope of these regulations, program managers should regularly consult with their legal and compliance teams to ensure that they are abreast of all rules.
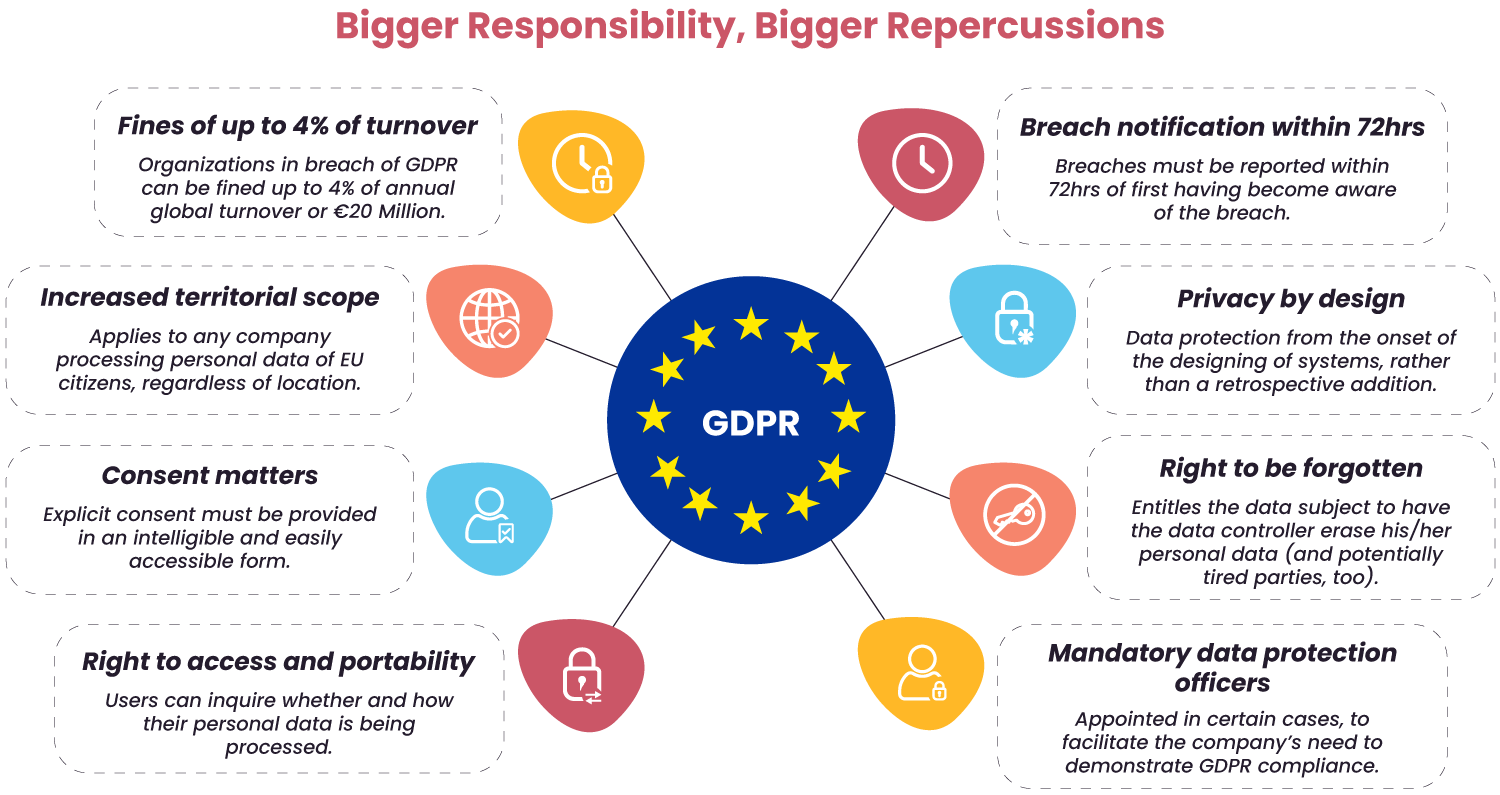
To be compliant, a company’s corporate physical security programs must understand the jurisdictional laws that apply in their region. (source)
Promote the use of physical security to enhance adherence to safety laws
Security technology should be viewed through the lens of dual-use technology. Where applicable, security devices should assist with safety, facilities, and operations management. For example, connected devices could help monitor lone workers for EU compliance, while AI smart cameras embedded with shot detection can help comply with the California OSHA law on workplace violence prevention. Security teams must actively engage across their organizations to assess where their devices can provide added value.
Foster proactive approaches to physical security
Build a security-first culture
Security practitioners should start by embedding security into the everyday culture, operations, and makeup of the company:
- Advocate for corporate physical security to have a designated timeslot at new hire orientations and/or employee onboarding.
- Add security information to the back of an employee ID access badge, making it easily visible.
- Use any employee interaction as an opportunity to remind them of the support that corporate physical security can provide.
Implement a layered approach to physical security
As design philosophy is becoming more ingrained in security operations, physical security practitioners should embrace crime prevention through environmental design (CPTED) as a core component of their programs:
- Add natural surveillance: For a corporate campus, consider an open design that allows for greater visibility and large swathes of open space that make it more visible for anyone to hide.
- Opt for discrete access control: Incorporate access control into the landscape. For a corporate campus, this might be creating a single walkway/path to the main entrance of a building.
- Use territorial reinforcement: A restricted facility might use gates and perimeter fencing, while a corporate campus could deploy signage and perimeter landscaping.
- Maintenance: Liaise with your facilities team to ensure regular upkeep and maintenance. For example, if you have outdoor power sockets and are dealing with unauthorized use, consider capping them.
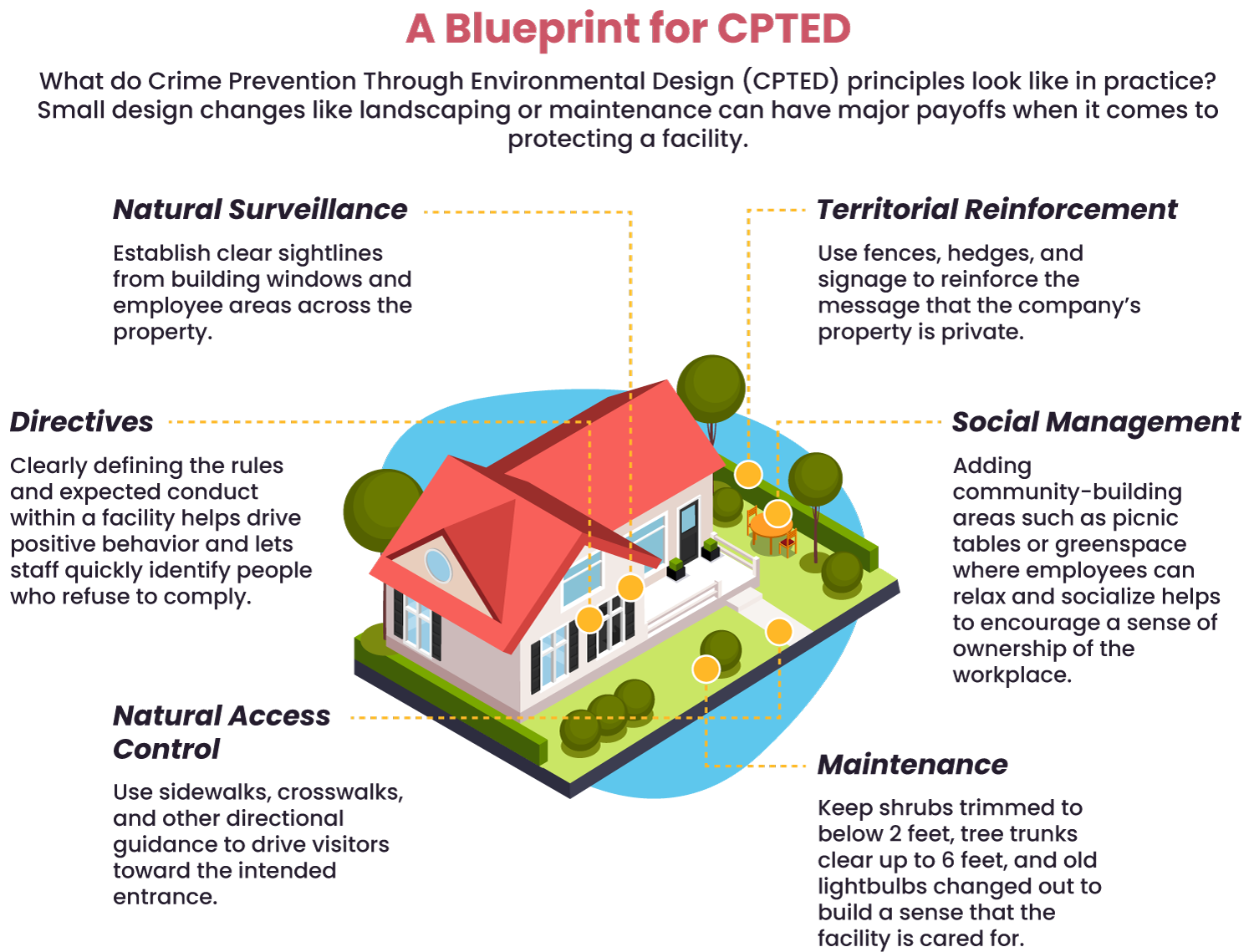
Principles of CPTED design (source)
Last thoughts
A corporate physical security program needs to be built, scaled, and matured through a business-focused and risk-based approach. A good program will leverage stakeholder relationships, technological solutions, and understanding of organizational culture to embed itself across the organization. As organizations expand their global footprint and operations, a modern corporate physical security program must innovate through technology, drive implementation through compliance, and optimize all aspects of its program to effectively mitigate risk to people, assets, and operations.


