Physical Security Systems
- Chapter 1: Tutorial & Best Practices
- Chapter 2: Commercial Building Security Systems
- Chapter 3: Physical Security Systems
- Chapter 4: Data Center Physical Security
- Chapter 5: Physical Security Cybersecurity
- Chapter 6: Physical Security Plan
- Chapter 7: Physical Security Controls
- Chapter 8: Retail Security Systems
- Chapter 9: Physical Security Tools
- Chapter 10: Physical Security Program Best Practices
- Chapter 11: Physical Security Policy Best Practices
- Chapter 12: Best Practices for Physical Security and Cybersecurity
- Chapter 13: Best Practices for Corporate Physical Security
- Chapter 14: Physical Security Best Practices
- Chapter 15: How physical security powers
- Chapter 15: Best Practices for Physical Security Devices
Traditional physical security systems can’t address many modern security threats. Protecting assets, personnel, and sensitive information in today’s world requires innovation, seamless device interoperability, and using data to enhance security and convenience. Modern physical security systems need a comprehensive approach that integrates advanced operational technologies and interconnected IT systems, rather than just performing simple installations.
This article will explore the ten essential features of aspects of physical security systems and provide insights into cutting-edge technologies, best practices to optimize security solutions, and the critical role technology companies specializing in integrating and managing physical security systems play in securing and managing IoT devices.
Summary of key features of physical security systems
The table below summarizes the key features of modern physical security systems, which this article will explore in detail.
| Feature | Description |
|---|---|
| High-definition cameras | Modern video surveillance cameras with high-resolution capabilities for clear, detailed surveillance. |
| Integrated video management | Advanced video management systems (VMS) for seamless real-time monitoring and analysis. |
| Flexible storage solutions | Options for both on-premises and cloud-based storage to ensure scalability and remote access. |
| Advanced alarm systems | Systems that use a control panel with Intelligent multitech sensors to reduce false alarms and enhance detection accuracy. |
| Perimeter detection | Use of motion detectors, electric fencing, and beam detectors to secure property boundaries effectively. |
| Access control systems | Use of specific criteria and unique identification like card, PIN, or biometrics to regulate access to physical environments |
| Enhanced intercom systems | High-quality audio and video systems used for communication between entry points and personnel in the restricted areas |
| IoT integration | Real-time data collection and automated responses through intelligent sensors and operational technology devices. |
| Intelligence and machine learning | Intelligence-driven facial recognition and behavior analysis for advanced security and predictive maintenance. |
| Cybersecurity measures | Encrypted communication and strong access controls to protect against cyber threats. |
-

Monitor the health of physical security devices and receive alerts in real-time
-

Automate firmware upgrades, password rotations & certificate management
-

Generate ad hoc and scheduled compliance reports
Ten essential features and technologies for physical security systems
The sections below will explore the ten key features and technologies for modern physical security systems.
Video surveillance systems
video surveillance systems are fundamental to physical security setups, providing more than essential surveillance. Advancements in video surveillance technology now allow for proactive monitoring, where systems can detect and alert surveillance teams to specific incidents. These capabilities have been made possible by real-time edge analytics supported by centralized analytics for more resource-intensive tasks. Additionally, machine learning (ML) has made it possible to train a model on live video footage to make it more accurate in predicting security or safety incidents.
Video surveillance technology includes several key components:
- Cameras: Ranging from basic analog to advanced IP models with high-definition resolution, colored night vision, and PTZ (Pan-Tilt-Zoom) capabilities. Modern camera systems include advanced analytics that enable capabilities such as license plate recognition (LPR), facial recognition, people counting, heat mapping, and thermal detection.
- Recording devices: Network video recorders (NVRs) for IP cameras and digital video recorders (DVRs) for analog cameras. These devices support multiple storage options.
The table below compares IP and analog camera systems across several key selection parameters.
| Feature | IP Camera System | Analog Camera System |
|---|---|---|
| Resolution | High resolution (up to 4K and beyond) | Limited resolution (up to 960H or D1) |
| Signal transmission | Digital (over TCP/IP networks) | Analog (coaxial cable) |
| Features | Advanced analytics, motion detection, remote access | Basic features, fewer analytics options |
| Power supply | Power over Ethernet (POE) capability | Separate power supply required |
| Storage | Cloud, local NVR, or hybrid options | Local DVR storage only |
| Scalability | Highly scalable, supports large, networked setups | Limited scalability, separate wiring for each camera |
- Storage solutions: video surveillance systems generate vast amounts of data, which requires reasonable storage solutions. Enterprises often choose between on-premises network-attached storage (NAS) or cloud-based solutions to ensure scalability, easy access, and long-term data retention.
- Monitoring interfaces: Utilize multiple screens, video walls, and advanced video management systems (VMS) for real-time monitoring and analysis.
Integration with other security systems
Integrating video surveillance with other systems enhances situational awareness and response capabilities. Access control can link access events to video footage for visual verification. Intrusion detection and alarm systems automate camera focus on areas where sensors detect movement. In alarm systems, infrastructure video as a service (IVaas) — which is gaining popularity in commercial building security systems — reduces false positives and ensures appropriate responses. ONVIF allows interoperability among different video surveillance brands to achieve the intended system design goal.
Cameras can also be triggered by motion detectors or other intrusion detection peripheral devices by hardwiring the dry contacts of the device to the NVR or DVR as inputs. Configurations on the NVR or DVR settings help achieve the possible triggers and automation.
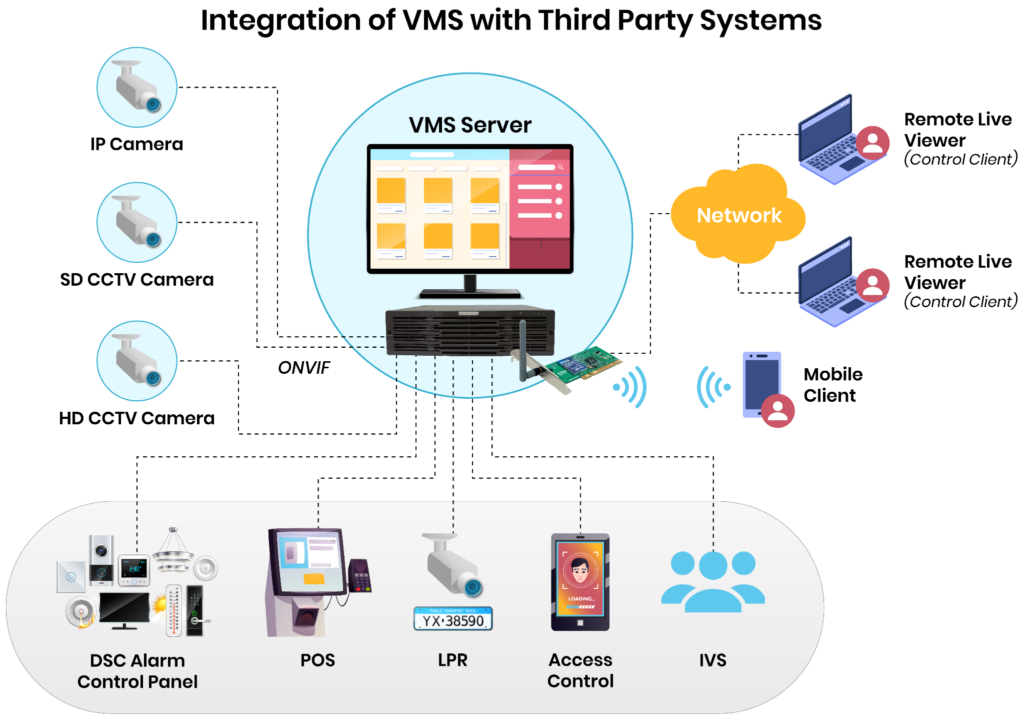
A logical view of the integration of a VMS with third-party systems.
Application recommendations and installation best practices
Different sectors demand specific video surveillance systems based on security requirements. Government facilities should deploy IP systems for high resolution and scalability, which are ideal for large, sensitive areas. Healthcare can opt for hybrid setups, integrating IP (wired and wireless cameras) for flexible coverage in patient rooms and secure areas. Data centers need IP cameras with advanced analytics and motion detection for real-time threat detection. Retail or small businesses may find analog or wireless systems more cost-effective, depending on the scale and complexity of their setup.
Prioritize strategic camera placement at installation for optimal video surveillance system performance. Regular maintenance is crucial, including routine lens cleaning, system checks, and firmware updates to maintain functionality and security. Additionally, implementing robust data management practices is essential, ensuring data retention policies comply with legal and customer requirements while optimizing storage capacity, particularly for high-resolution footage and extended recording durations.
Alarm systems
Alarm systems are vital to physical security, detecting unauthorized access and alerting security personnel for quick response. Beyond essential intrusion detection, modern systems can be tailored to detect environmental conditions, fire hazards, and gas and water leaks. Effective design ensures interoperability with existing systems, scalability for future upgrades, and reliable communication for timely response.
Below is a list of the different types of alarm systems:
- Burglar alarms: Detect unauthorized entry through door/window sensors, curtain detectors, glass break detectors, and shock or vibration sensors.
- Fire alarms: Use smoke, heat, and flame detectors to identify fire incidents. Smoke detectors are categorized into Ionization detectors, which are more effective at detecting fast-flaming fires with minimal smoke but intense flames, and photoelectric detectors, better suited for slow, smoldering fires that produce heavy smoke but fewer flames.
- Environmental alarms: Monitor conditions like temperature, humidity, gas and water leaks.
- Panic alarms: Some systems allow manual triggering of distress signals, and panic buttons can be modified and repurposed as medical alarm buttons.
Integration with monitoring systems
Modern alarm systems integrate with central monitoring stations for real-time response. Key components of the integrations include:
- Communication protocols: Alarm systems communicate with central stations using radio Frequency, cellular, Wi-Fi, or IP protocols. Peripheral devices communicate with the main panel via wired, wireless, or hybrid means.
- Central monitoring: Stations verify alarm signals before notifying responders. Alarm communicators report to the CMS via VHF, GPRS, or IP.
- Mobile integration: Alarm systems can notify end-user mobile devices for off-site responses or reporting redundancy.
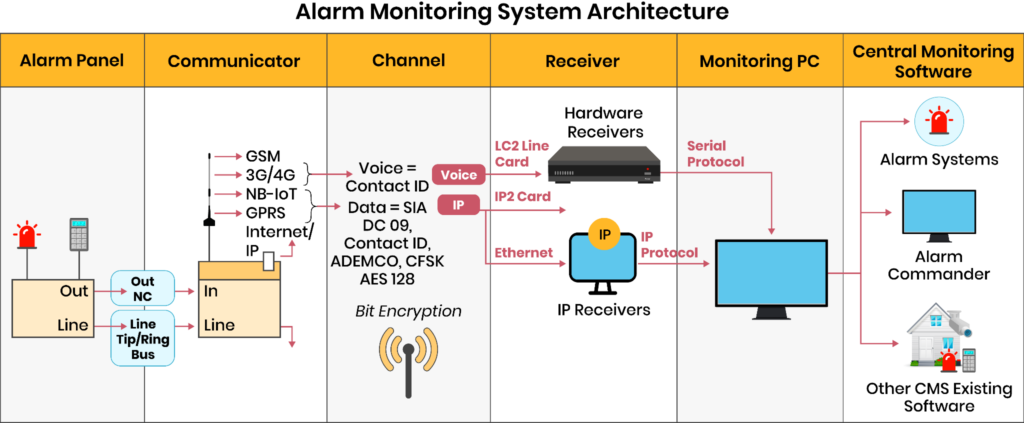
Alarm system to central station data flow diagram.
Advanced features and technologies
Modern alarm systems utilize intelligent sensors that reduce false alarms by distinguishing actual threats from false triggers. The integration of AI in these systems allows for the analysis of alarm data, helping to identify patterns and predict potential security breaches. For reliability and redundancy, alarm systems should always have backup power and use multiple communication channels.
Intrusion and perimeter detection
A perimeter detection and protection system is the first line of defense in a property’s physical security setup. The system safeguards property boundaries using various technologies and sensors such as:
- Motion detectors: These sensors use infrared, ultrasonic, or microwave technology to detect movement within a designated area. Manufacturers often combine these in dual-tech or tri-tech configurations to reduce false activations.
- Fence sensors: Detect vibrations or cuts with accelerometers or fiber-optic cables. These are dug underground and primarily used in areas less prone to false triggers, such as from pets.
- Beam detectors: Employ infrared or laser beams to create invisible boundaries that trigger alarms when crossed.
- Electric fencing: uses a high-voltage electric current to deliver a non-lethal shock through wires or conductive materials, creating a deterrent barrier on the perimeter.
Integration with video surveillance and alarms
Surveillance systems integrate motion sensors, fence detection, and beam detectors by wiring dry contact outputs to an NVR or configuring them in a VMS to automatically trigger camera recording and track intruders. Integrating these systems with the SecuriThings platform gives security teams real-time insights and automatic alerts for faster responses.
Perimeter detection devices and electric fence energizer outputs can be wired into an alarm panel as a zone, triggering automatic alarms in response to intrusion events. This synergy enhances security systems’ detection and response capabilities, providing comprehensive protection and monitoring.
Application scenarios and best practices for perimeter security
Perimeter detection systems should align with specific sector requirements. For government and data centers, dual-tech motion and beam detectors offer robust protection, while fence sensors are better suited for restricted zones. In healthcare and commercial buildings, motion detectors and beams create effective boundaries. Electric fencing is optimal for high-security sites like military bases. Retail environments can combine motion detectors, beams, and video surveillance to reduce false alarms and improve security.
Below are some of the best practices to be implemented in perimeter security:
- Layered Security: Combine multiple detection methods like motion sensors and beam detectors to create multi-layered protection.
- Regular Testing: Periodically test the system or set the system’s self-test at intervals to ensure functionality.
- Environment Consideration: Select sensors that can withstand and work in harsh environmental conditions such as bad weather, terrain, and potential interferences.
Access Control Systems
Access control systems manage, control, and log entry and exit events with the use of components such as:
- Credential readers: Devices that read RFID keycards, biometric data, or PIN codes.
- Door locks: Electromagnetic or electric strike locks and secure door control units.
- Access credentials: Items or data used for user authentication.
- Control panels: These central units process access requests and control locks. They can also implement certain security features, such as interlocking, anti-passback (APB), zone control, time and attendance tracking, etc.
- Management software: enables centralized control, monitoring, and administration of entry/exit points, user permissions, and event logs to ensure secure and efficient facility access.
Integration with other security systems
Access control systems can integrate with intrusion detection to enhance security and convenience. For instance, they can restrict access until the alarm system is disarmed. Access control systems can also integrate with intercom systems by using access control readers as multipurpose door stations for intercom, streamlining security and communication in one system.
Best practices for implementation
Scalability: Access control systems should be able to adjust to growing demands, allowing for additional entry points and users without compromising security.
User Management: Regularly auditing access credentials, updating or revoking permissions as necessary to maintain system integrity.
Intercom systems
Intercom systems allow visitors to call and communicate with the residents or security personnel to gain access. The systems entail the following components and technologies:
- Master stations: these are central units that allow communication with multiple doors or sub-stations, enabling users to monitor, communicate, and control access to a building or facility from a single point.
- Substations: include indoor and outdoor stations that act as endpoints for two-way communication.
- Communication links: Wired or wireless connections transmit audio and video signals, typically utilizing two-wire or IP-based communication protocols. The engineer’s choice of connection mode, whether wired or wireless, depends on network infrastructure, signal range, interference, security, ease of installation, power requirements, cost, and system integration. For example, in a setup with heavy vegetation or blockage from buildings, implementing a wireless gate intercom system wouldn’t suffice; a wired one would be more reliable.
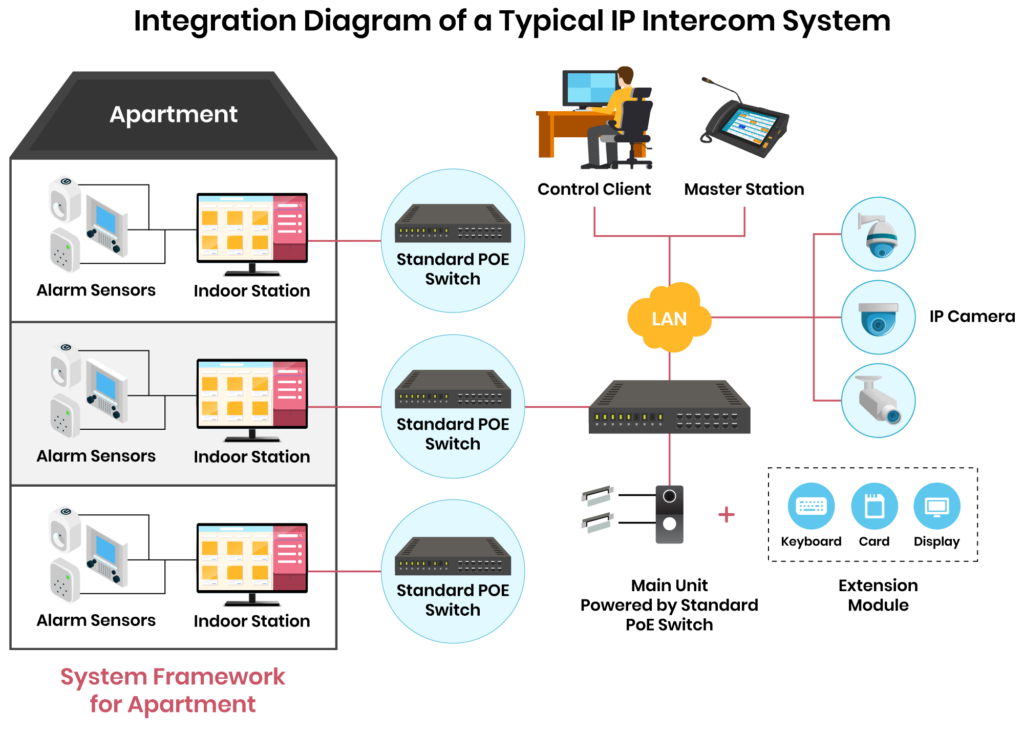
A logical view of a typical IP intercom system integration with alarm and video surveillance
Integration with access control
Remote access: Modern systems support integration with mobile devices for remote control. This is done through OEM mobile apps that allow viewing live feeds of door stations and automatic forwarding of calls from the door stations.
Gate/door automation: door stations feature an inbuilt relay with normally closed (NC) and normally open (NO) terminals. This allows hardwiring into gate or door controllers, enabling remote and local opening or closing.
Advanced security solutions
Cybersecurity is an essential aspect of modern physical security. For example, unpatched camera vulnerabilities can lead to the compromise of a video surveillance system. The sections below explore three specific categories of advanced security solutions for physical security systems.
IoT and cloud integration
IoT and cloud technologies enhance physical security by providing:
- IoT devices: Real-time data and automated threat responses.
- Cloud storage: Scalable and remote access to security data.
- Remote management: Flexible control of IoT-enabled devices.
SecuriThings provides a platform for real-time data collection from devices, remote access, and management in the context of IoT and cloud integration.
AI and machine learning in security
AI and machine learning offer advanced capabilities such as:
- Facial recognition identifies individuals and manages access or alerts.
- Behavior analysis detects unusual behavior through video analysis. This can be applied in various scenarios to achieve exception-based monitoring.
- Predictive maintenance provides intelligent analytics of devices and sensors enabling the forecasting of maintenance needs to reduce downtime.
Cybersecurity considerations
Cybersecurity is crucial for protecting assets and data in interconnected systems, especially as the threat landscape constantly evolves. Bad actors can exploit vulnerabilities in OT devices, such as physical security equipment, to access IT systems. Therefore, a well-designed physical security system should incorporate the following measures:
- Secure communication: Encrypt data transmitted between devices. Security systems should use encryption protocols (e.g., HTTPS, TLS) to reduce the risk of data leaks or sensitive data exposure.
- Access controls: Implement strong controls to prevent unauthorized access. A good example is the implementation of MFA in access control systems.
- Regular updates: Keep software and firmware updated to address vulnerabilities. This helps deny the bad actors the chance to explore any known vulnerabilities.
SecuriThings centralizes and automates device management, enhancing operational efficiency and security posture management. Through device performance monitoring, security alerting, and task automation, such as firmware updates and security patches, SecuriThings enables alignment with security standards and best practices, such as encryption, multi-factor authentication, and segmentation of security devices from IT infrastructure. Learn more by visiting this page.
Conclusion
Advancing physical security systems requires integrating diverse technologies and adhering to best practices. From video surveillance and alarm systems to advanced solutions like AI and IoT, a comprehensive approach ensures robust protection against various threats. Security professionals can safeguard assets and information by staying updated with the latest innovations and focusing on integration and interoperability.


